Executive Summary
Bridewell Cyber Threat Intelligence has identified a new campaign by the Hydra android banking trojan, beginning in late-January that is still ongoing, targeting users of banking applications on android by impersonating Google Chrome and the Google Play Store in Spain and Latin America. Bridewell has identified 28 Hydra Command-and-Control (C2) servers in the wild, some of which are operational whilst others are deployed and yet to be observed in any current attacks.
According to open-source reporting, Hydra malware was the most prolific banking trojan in 2022. This new wave of activity matches a historical trend by threat actors renting this malware to target banking applications. The developers of this malware continue to develop their capabilities and move C2 infrastructure to new geographical locations.
Organisations need to be aware of the threat the android malware presents to their security risk posture. Banking malware developers, like Hydra’s, are continuing to expand their capabilities and their place in the criminal ecosystem could enable it as a threat similar to infostealer malware that may fly under the radar of many organisations. Banking trojans are an effective tool for criminals to attack financial institutions, bypassing fraud detection controls due to the invasive ability to control end user devices. Criminals can intercept OTP codes, incoming messages, phones, session cookies and extract sensitive information such as call history and contact lists.
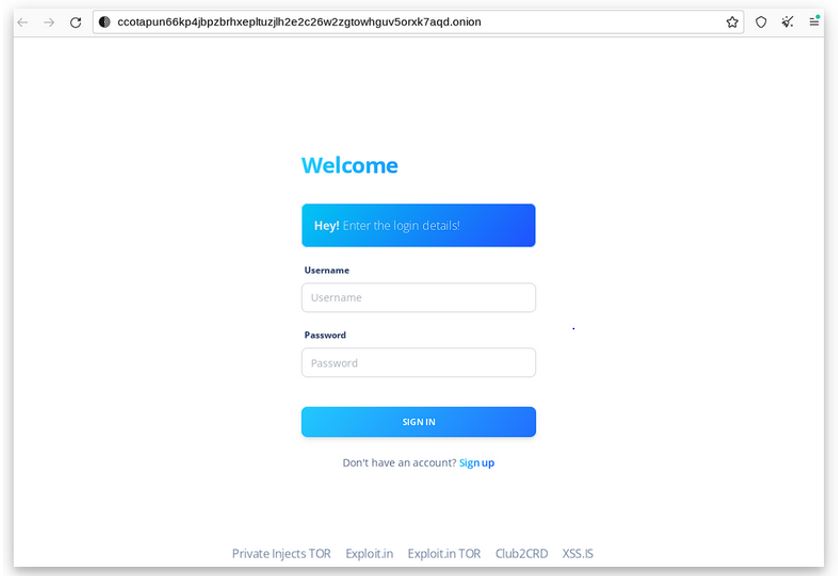
Figure 1: Marketplace login panel
Overview
Hydra, alongside other malware families such as Alien, Cerberus, Ermac, Octopus, Poison and MetaDroid, has the ability to support web injects and Bridewell has observed operators of the Hydra malware utilising web injects in their attacks against end user devices. The malware is impersonating legitimate tools such as Google Chrome or the Google Play Store, reaching out to C2 infrastructure in order to retrieve injects for targeted banking applications in order to intercept sensitive information. A "Webinject" is a customised module or package used in malware that typically inject HTML or JavaScript code into content before it's rendered on a web browser. As a result, webinjects can alter what the user sees on his/her browser, as opposed to what's in fact being sent by the server.
This area of criminal activity continues to grow rapidly, with many develops now offering similar “as-a-service” functionality for elements such as web injects. This advancement is owed to the increased maturity of developers in this space when it comes to creating convincing and successful impersonation injects that mirror the design of legitimate services. In late 2022, open source reporting documented the emergence of a new underground criminal marketplace called “InTheBox”, which was specifically designed for mobile malware. This marketplace has grown out of demand and by the success of the developers of the webinjects that are compatible with multiple stable versions of these malware families. This automated marketplace allows threat actors to create orders to receive the most up to date webinject for the malware. Whilst Bridewell has only observed webinjects related to internet banking however Hydra operators can inject pages in to any service that the end user accesses for the purposes or harvesting credentials for follow on activity. Additionally, the webinjects themselves cost between $50 and $200 per inject depending on the targeted bank.
Evidence of the shift towards a “as-a-service” model has already been reported, showing how threat actors are moving away from individual payments, to monthly subscription services, costing around $5,000 per month and other models where threat actors get access to unlimited webinjects for a share in the profits between malware operators and developers after successful pay outs. The “InTheBox” marketplace currently has over 400 webinjects largely targeting banking applications, which are regularly updated.
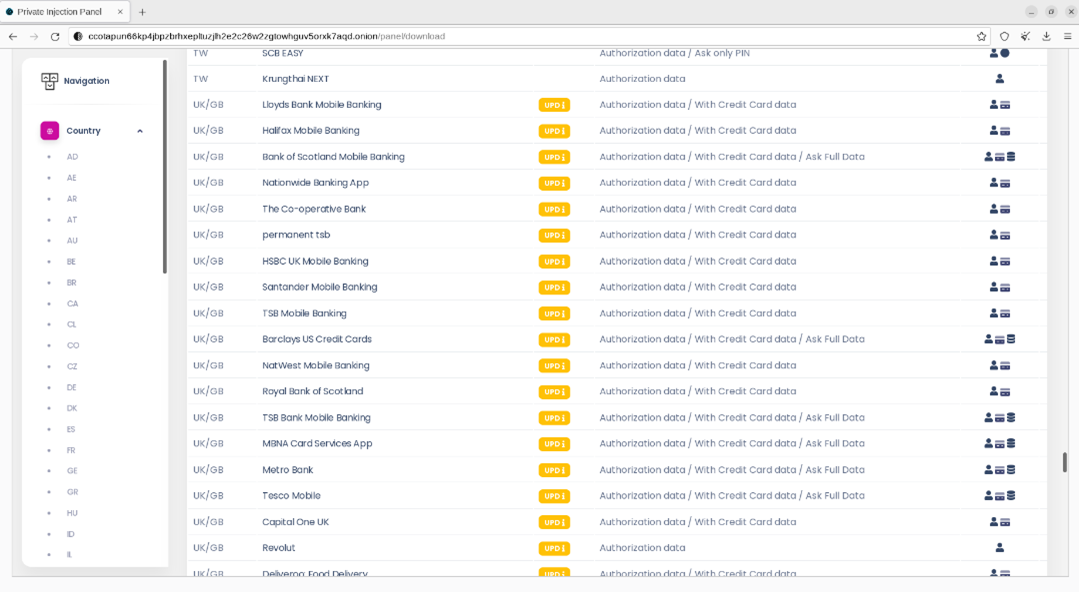
Figure 2: Marketplace listing of Webinjects
During routine research, the Bridewell Cyber Threat Intelligence team identified new infrastructure related to Hydra, some of which is being used in a new campaign. This campaign began in late-January 2023 and is still active at the time of writing this report. The developers of the malware rent this infrastructure to other threat actors and this current campaign continues to target banks. A number of Hydra malware samples appear to impersonate Google Chrome and the Google Play Store, likely distributed through third party app stores. Other files have seemingly random naming conventions. Bridewell CTI assesses that the threat actors behind the current campaign are utilising webinjects likely sold on the “InTheBox” marketplace on the Hydra C2 infrastructure to target victims in Spain and Latin America.
Hydra Capabilities
The Hydra malware has a number of capabilities making it an effective and lucrative banking trojan. The developers aim to steal banking credentials to either access financial information or to sell access on. The trojan will contact the C2 infrastructure to pull down the injects for applications configured by the operators, and presents them to the unsuspecting user when they open the associated banking application. Additionally, the malware abuses accessibility permissions in order to receive password and usernames via change events. In 2022, the developers added to the ability for the malware to capture session cookies, bypassing the need for, the also present ability of the malware, OTP tokens and SMS messages. The malware also makes requests to the url path “/api/mirrors/” in order to retrieve new C2 information should existing hardcoded C2 infrastructure go down. 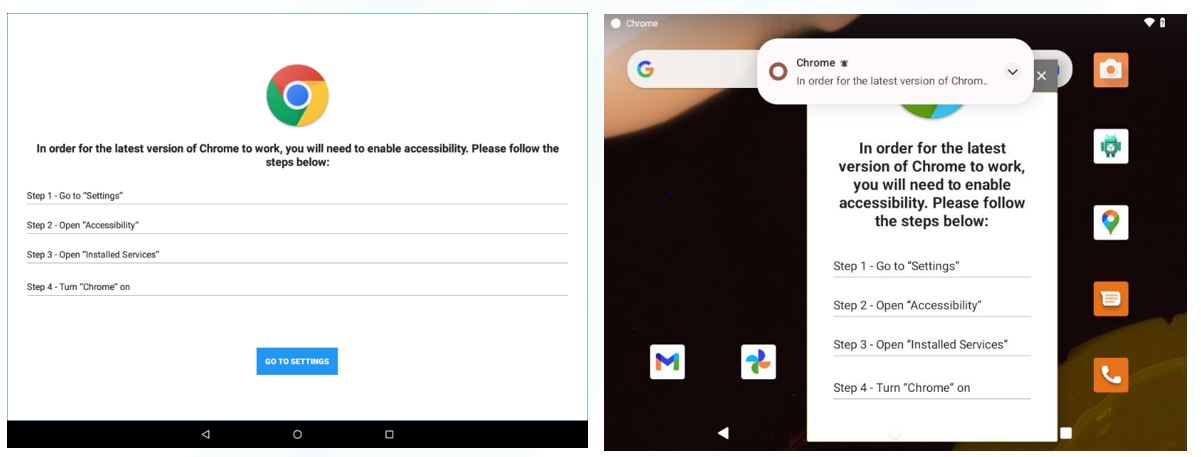
Figure 3. Screenshots of the installation of Hydra malware impersonating Google Chrome.
Infrastructure Discovery & Analysis
Bridewell CTI has uncovered 28 C2 servers for Hydra, 10 servers are currently operational and rented to active threat actors.
This new infrastructure is going largely undetected in VirusTotal by security vendors, with the highest detection rate being 5/88 for IP 80.82.76[.]16 due to its involvement in historical campaigns by Hydra in 2022. 23 C2 servers still remain in a clean state in VirusTotal, 9 of which are currently operational.
14 C2 servers remain in a pre-operational state, hosting the C2 infrastructure but currently not in use. 3 servers have been observed in use in attacks but currently remain dormant after activity as late as February 2022.
15 C2’s are currently presenting a Login Panel on port 80, interestingly, these panels have different integers following the “Admin Dashboard” string, indicating possible association to the threat actors who are currently renting the malware from the developers.
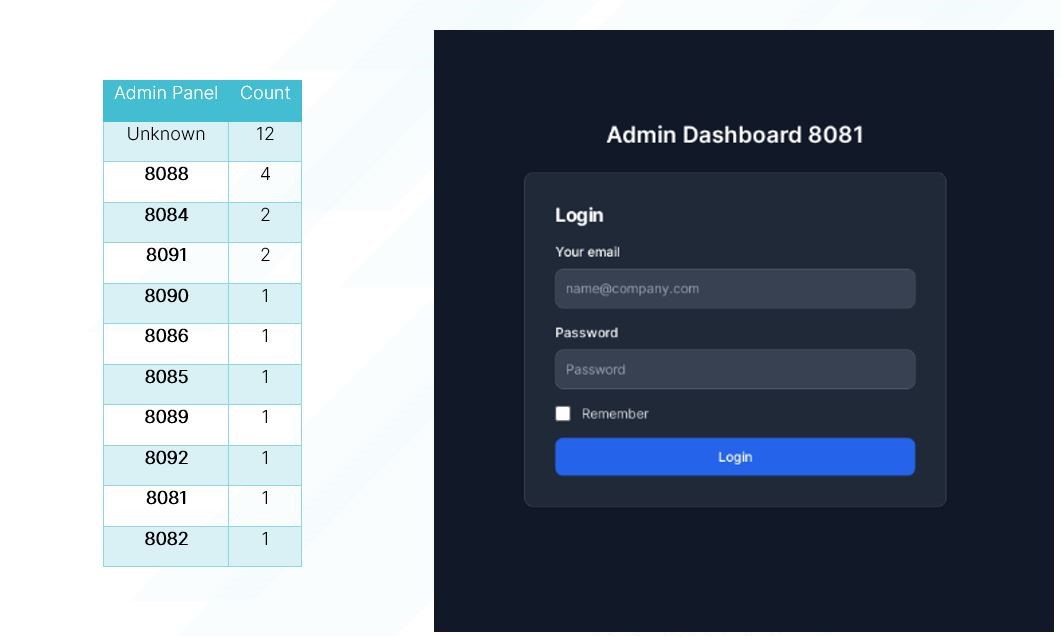
Figure 4. Count of unique strings on admin dashboard panel
Figure 5. Example of Hydra C2 Login Panel
Based on the identified C2 servers, we were able to conduct analysis based on the threat actors choice of hosting provider and country:
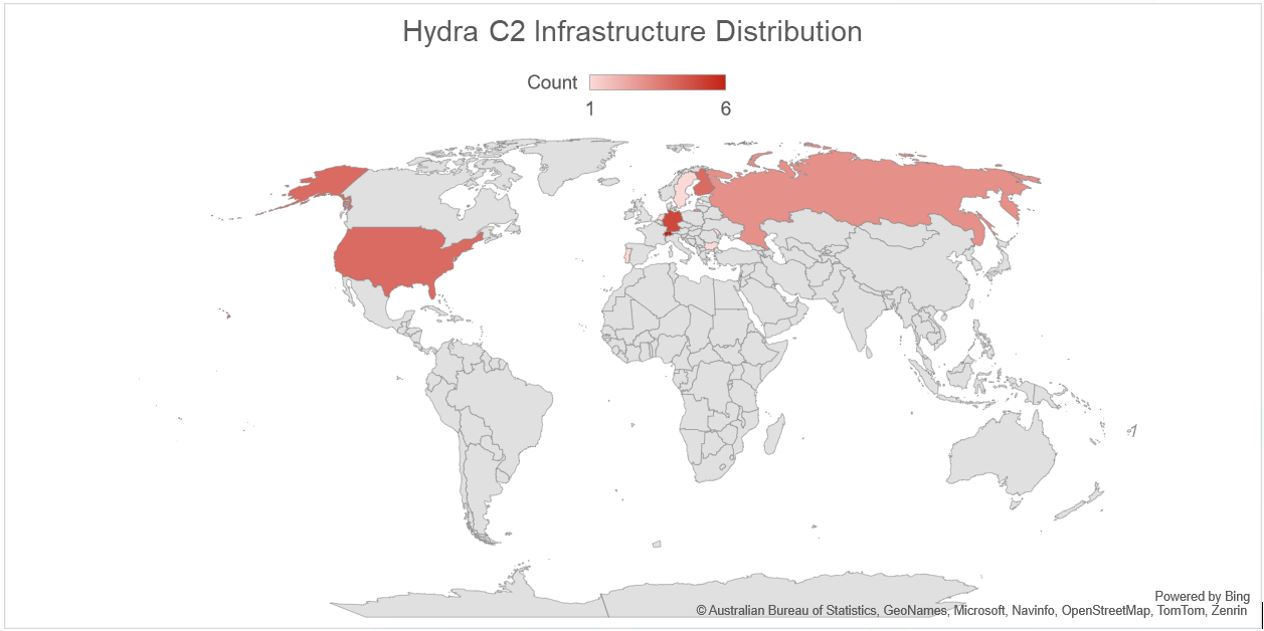
Figure 6. Hydra C2 Infrastructure Distribution
It has previously been reported that the Hydra threat actors have used infrastructure in the Netherlands, United States and Ukraine in campaigns. This new infrastructure seems to be widely distributed across cloud hosting providers in Switzerland (6), Germany(5) and Finland(4) – these providers regularly host malicious infrastructure; Private Layer INC, Delis LLC and AEZA GROUP Ltd.
The total distribution of C2 servers by ASN:
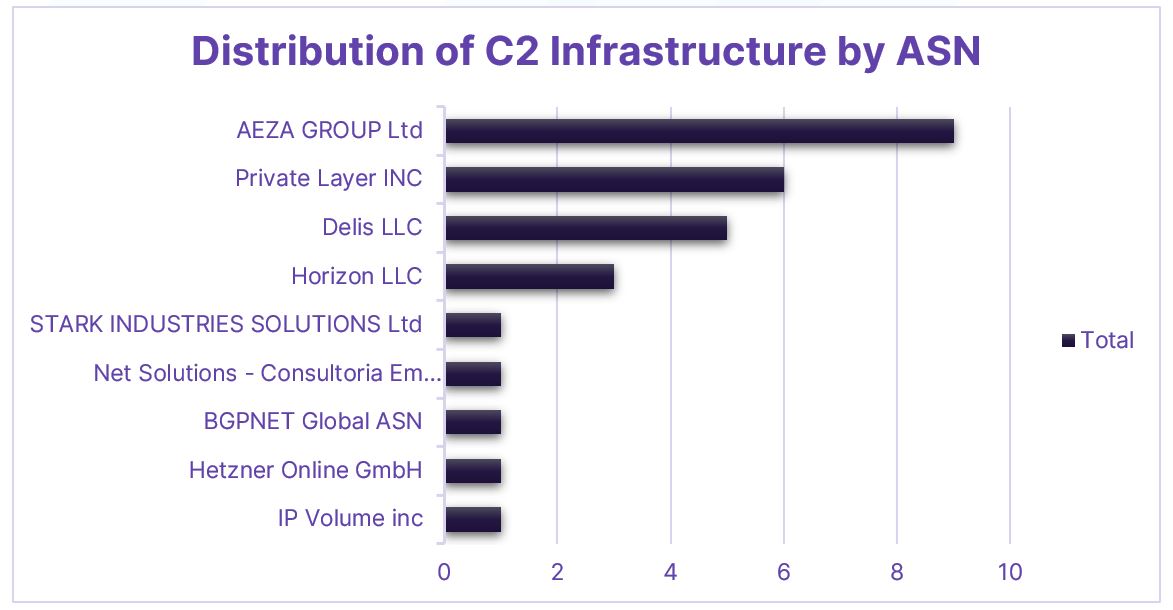
Figure 7. Distribution of C2 Infrastructure by ASN
Domain Names
The operators behind the Hydra malware are using multiple new “Domain Generated Algorithm” (DGA) domains, that are created in an automated fashion, likely for the purposes of high level redundancy and fast flux capabilities to avoid detection. A full list of the domains found through passive DNS can be found in the Appendix to this report. However, these domains are updated on a regular basis by the threat actors.
Registrars
The operators have been using a variety of registrars for this campaign but there is a clear focus on the utilisation of Google LLC and NICENIC INTERNATIONAL GROUP CO., LIMITED. However, Bridewell has observed multiple other Registrars utilised on a smaller scale, e.g. LEXSYNERGY LIMITED, Alibaba.com, GoDaddy.com, Hostinger UAB and NAMECHEAP INC. The first domain was registered on 17-01-2023 and the latest domain in this campaign was registered on 4-03-2023, indicating that the operators are continuing to generate live undetectable domains in support of operations during this campaign.
Name Servers
Where Google LLC has been the registrar for most if the domains in this campaign, the Google DNS Nameservers have also been utilised, also associated with the Hydra samples that are named as Chrome. This may be an attempt by the developers to blend in to legitimate traffic of legitimate Google Chrome applications. The Nameservers used:
ns-cloud-d4.googledomains.com
ns-cloud-d3.googledomains.com
ns-cloud-d2.googledomains.com
ns-cloud-d1.googledomains.com
Nearly all of the domains registered under NICENIC INTERNATIONAL GROUP CO., LIMITED have utilised the same name server providers for DNS resolutions to their C2 infrastructure:
dnspod.com
my-ndns.com
Targeting
Based on the identified active C2 infrastructure used by Hydra, the following webinjects have been identified:
| Bank | Inject | Found on Marketplace | Income | No. of Customers |
|---|---|---|---|---|
| CaixiaBank | es.lacaixa.mobile.android.newwapicon | Yes | €11million | 15.8million |
| Bankia | storage/injects/inj/com.bankia.wallet | No | N/A | Merged with CaixaBank in 2021 |
| Unicaja | storage/injects/inj/es.univia.unicajamovil | No | €260million | 4million |
| Banco Santander | storage/injects/inj/es.bancosantander.apps | Yes | €9.04Billion | 14.3million |
| Banca Móvil BCP | storage/injects/inj/com.bcp.bank.bcp | Yes | €207.5million | Unknown |
| Scotiabank Colpatria | storage/injects/inj/eu.netinfo.colpatria.system | Yes | €1.9billion | 5million |
The inject naming convention aligns to the language of the inject, for example “es” indicating that the malicious code is written in Spanish or targeting Spanish speaking regions that utilise these banks. Additionally, a number of these injects appear on the “InTheBox” marketplace. This information provides a good indication that the threat actors are targeting individuals of Spanish and Latin-American banks, as reported in a previous campaign by NCC group in 2022, utilising injects from “InTheBox” marketplace.
Conclusion
There is increasingly more reporting of cybercrime activity of prominent banking malware such as Hydra in recent years. The operations continue to grow more efficient, aligning to other commercial models observed by other areas of the cybercrime ecosystem, such as infostealers and ransomware. Hydra continue to deploy new infrastructure in support of the rental operations to threat actors using web injects from growing marketplaces such as “InTheBox”. The threat from Android malware is likely to continue to increase in the coming months in 2023. Bridewell Cyber Threat Intelligence continue to fingerprint and identify new C2 infrastructure for Android trojans as they are used and before they are used in attacks against their customers.
Mitigations
There are good rules to follow to help detect and prevent a web inject attack. We recommend the following mitigation strategies:
- Keep devices up to date: Make sure that all Android devices used in the enterprise are running the latest version of the operating system and security patches are installed regularly. This helps to prevent known vulnerabilities from being exploited by malware.
- Use mobile device management (MDM) software: MDM software allows IT administrators to monitor and manage mobile devices remotely, including enforcing security policies, configuring devices, and controlling access to enterprise resources.
- Implement a strong password policy: Require all employees to use strong passwords that include a combination of letters, numbers, and special characters. Passwords should be changed regularly and never reused.
- Educate employees on safe mobile device usage: Provide regular training to employees on how to identify and avoid Android malware, such as phishing scams and malicious apps. Emphasize the importance of not downloading apps from unknown sources.
- Use app vetting and whitelisting: Only allow employees to install apps that have been vetted and approved by the IT department. Implement a whitelist of approved apps and block the installation of any unapproved apps.
- Enable app sandboxing: Implement app sandboxing to isolate apps from each other and the underlying operating system. This can prevent malware from spreading to other apps or compromising the device.
- Monitor network traffic: Use network monitoring tools to detect and block suspicious network traffic from Android devices. This can help to prevent malware from communicating with its command and control servers.
- Implement remote wipe capabilities: In the event that an Android device is lost or stolen, the ability to remotely wipe the device can prevent sensitive data from falling into the wrong hands.
By implementing these mitigation strategies, an enterprise can significantly reduce the risk of Android malware infections and protect sensitive data and resources from cyber threats.
References
https://www.resecurity.com/blog/article/in-the-box-mobile-malware-webinjects-marketplace
https://research.nccgroup.com/2023/02/17/threat-spotlight-hydra/
Appendix
| IP Address | ASN | Status | VT Detection |
|---|---|---|---|
| 179.43.142[.]100 | Private Layer INC | Operational | 0/88 |
| 89.185.85[.]173 | AEZA GROUP Ltd | Pre-operational | 1/88 |
| 179.43.142[.]99 | Private Layer INC | Operational | 0/87 |
| 171.22.30[.]208 | Delis LLC | Pre-operational | 0/88 |
| 45.12.253[.]200 | Delis LLC | Pre-operational | 0/87 |
| 84.54.50[.]241 | Delis LLC | Pre-operational | 0/87 |
| 80.85.241[.]36 | AEZA GROUP Ltd | Operational | 0/87 |
| 185.38.142[.]205 | Net Solutions - Consultoria Em Tecnologias De Informacao, Sociedade Unipessoal LDA | Dormant | 0/88 |
| 62.204.41[.]219 | Horizon LLC | Operational | 0/87 |
| 85.192.63[.]83 | AEZA GROUP Ltd | Operational | 0/87 |
| 212.87.204[.]58 | Delis LLC | Pre-operational | 0/87 |
| 62.204.41[.]108 | Horizon LLC | Operational | 2/88 |
| 79.137.206[.]105 | AEZA GROUP Ltd | Operational | 0/87 |
| 79.110.62[.]232 | Delis LLC | Pre-operational | 0/87 |
| 79.137.206[.]52 | AEZA GROUP Ltd | Pre-operational | 0/87 |
| 79.137.207[.]174 | AEZA GROUP Ltd | Operational | 0/87 |
| 179.43.142[.]119 | Private Layer INC | Operational | 0/87 |
| 77.91.84[.]33 | AEZA GROUP Ltd | Dormant | 0/87 |
| 79.137.248[.]171 | AEZA GROUP Ltd | Operational | 0/87 |
| 80.82.76[.]16 | IP Volume inc | Pre-operational | 5/88 |
| 62.204.41[.]210 | Horizon LLC | Operational | 0/88 |
| 179.43.176[.]19 | Private Layer INC | Pre-operational | 2/88 |
| 85.192.63[.]118 | AEZA GROUP Ltd | Dormant | 0/88 |
| 116.203.136[.]196 | Hetzner Online GmbH | Pre-operational | 0/87 |
| 179.43.154[.]232 | Private Layer INC | Pre-operational | 0/87 |
| 134.122.133[.]18 | BGPNET Global ASN | Pre-operational | 0/88 |
| 45.150.67[.]23 | STARK INDUSTRIES SOLUTIONS Ltd | Pre-operational | 9/89 |
| 179.43.142[.]120 | Private Layer INC | Pre-operational | 0/88 |
| Hydra C2 Domains | VT Detections |
|---|---|
| lopaugolpeoionline[.]com lopaugolpeoi[.]net flocumentoscovizios[.]net prunalopauea[.]com cimportunescol[.]top poajurevoeorp[.]org calponutuirioe[.]net paprangeruspasio[.]net claumarspopovicos[.]net topolacpolotunc[.]com rangetopolcunos[.]com hugomarcontumico[.]net kokalarmacolpaturcompo[.]com fulgimontusoporcheton[.]com sokolpogolsopaor[.]com chirpolocalpontuios[.]net folpoconturn[.]com chikomankolputinos[.]com orgkaokolpolcon[.]com adfdwfvwsv[.]online seguronote[.]top seguromax[.]top segurofull[.]top zeminbereks[.]net faygerforgerdos[.]net binkismick[.]net borabanlixenon[.]net canlidexusuz[.]net taewssas2s[.]com[.]de taewcfas2s[.]com[.]de web[.]next-cloud-dev[.]xyz golpoglobutine[.]org franpacines[.]online pictorcamongolpendu[.]com topolacpolotunc[.]com fulmionpoltuiorecoverstun[.]org rangetopolcunos[.]com claumarspopovicos[.]net www[.]shzzoaioisjehhh[.]xyz jhrrrrronine[.]xyz jhrrroorronine[.]com www[.]firrpxxxcjnnskk[.]xyz s2g0c009gyto6znh7phsh8s6z[.]top s2g0c009gyto6znh7phsh8s6z[.]online 79n49w3v4yiwvbmgs3hx5sbv5[.]top vbzwe94a0eaxm1z77cqb9i2i6[.]online vbzwe94a0eaxm1z77cqb9i2i6[.]top dgfchgfdfbxdgfdhfg[.]top dgfchgfdfbngvhmvn[.]top www[.]milion[.]website milion[.]website milion[.]store hbbvhhgvg[.]xyz bhjhkjgkhjggy[.]xyz snakknska[.]xyz win-rar[.]laojiav7[.]com vlc-media-player[.]jieboluntan[.]com foxit-pdf-reader[.]lkax[.]com www[.]foxit-pdf-reader[.]lkax[.]com haygolesdomesdos[.]net fardesnordesfoles[.]net haygocedsosgeyses[.]net dimnesdomkusnes[.]net banconesdomines[.]net findyfindtoto[.]com www[.]tekyurektekmillet[.]com tekeoynasdes[.]net faygerforgerdos[.]net canlidexusuz[.]net selmacamdesnos[.]net ondoraboslukke[.]net aybikosloledos[.]net gayretsisgelesis[.]net folpoconturn[.]com topolacpolotunc[.]com paprangeruspasio[.]net hugomarcontumico[.]net aybikosloledos[.]net gayretsosgelesos[.]net ferdialacamgelme[.]net ahbedsoshahles[.]net halkoltoydos[.]net ferdololednes[.]net ayadomedholhal[.]net aygodborysus[.]net haphoplolkok[.]net hiphopdupdip[.]net vahbekocdeltosyes[.]net hteam88[.]com australiaaz[.]com sendreporter[.]com findyfindtoto[.]com | 4/89 5/89 2/89 9/89 4/89 2/89 10/89 5/89 8/89 1/89 0/89 0/89 5/88 11/88 14/88 0/88 6/88 8/88 10/88 0/88 0/87 0/87 0/87 0/88 1/88 0/88 0/88 3/88 5/88 6/88 0/87 0/88 11/88 1/88 1/88 3/88 0/88 8/88 1/88 0/87 0/87 10/88 0/87 0/87 0/87 0/87 0/87 0/87 0/87 1/88 1/88 0/89 0/87 0/87 0/87 0/87 0/87 0/87 0/87 0/88 0/88 0/88 0/88 1/88 10/88 6/88 0/87 7/88 3/88 0/88 1/88 11/88 6/88 6/88 1/88 5/88 5/88 11/88 1/88 10/88 8/88 9/88 10/88 8/88 5/88 11/88 10/88 8/88 0/87 0/87 0/87 10/89 |
Tags: Mobile, Malware, Dark Web, Webinjects, Financial Institutions and Cybercrime

.jpg?sfvrsn=4c6fcb96_1)



