When the September 11 attacks took place, terror groups had a minimal online presence. Changes in technology allowed these groups to embrace the anonymity the internet can provide to further their activity. Read this article to understand the technological advances twenty years on.
9/11/2001 – a most tragic date everyone remembers for the large-scale terrorist attack that was carried out in the US with an extreme high loss of life. In those days there were no smartphones to initiate a video call with loved ones. The active mobile service was down after the Twin Towers were hit in New York City, which made it almost impossible to reach family and friends. Similar occurrences happened in the series of related terrorist events in Virginia and Pennsylvania. No one knew then, just how dramatically technology and the world would change following these terrorist attacks.
Recruitment
With the increase in social media and the anonymity that is provided online, terrorist groups have frequently used online messaging to promote ideologies and to recruit. Messaging apps such as telegram are frequently used by groups such as ISIS, and online publications on the dark web are aimed at legitimising their activity.
Attack Planning
As terror groups have successfully used an online presence to radicalise people, the threat from lone-wolf style attacks have increased. These can be hard to detect and hard to predict due to a lack of online signature such as traditional indicators of Compromise (IOCs). Through our Security Operations Centre at Bridewell, we can monitor the surface, deep and dark web for threats against organisations in both cyberspace and the physical aspect.
Threats from cyberspace
The advances in technology offer a wide range of attacks available to threat actors, and these can be utilised having very little technical knowledge. Services such as RaaS allow unsophisticated actors to launch damaging attacks with minimal infrastructure and risk to themselves. An unskilled individual or organisation can leverage a more sophisticated threat actor to conduct ransomware attacks on their behalf with the ransomware owner being paid a percentage of the ransom as their fee. Many cyber criminal groups establish access to an organisation with no intent of conducting further activity against the target. They will then advertise the initial foothold onto the network for sale on the dark web.
Ransomware
Ransomware has seen an increase in the frequency of reports of successful attacks. In the twenty years since the attacks, a terrorist organisation can hold a government organisation to ransom without setting foot in the target country.
As the Ransomware attacks have increased, so too has the number of companies willing to pay a ransom to minimise disruption to operations. This has led ransomware operators to view this type of attack as one that is likely to succeed and one that will continue to fund their continuing operations.
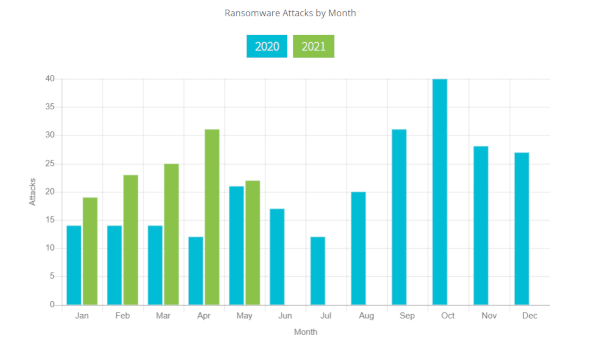
Traditionally ransomware attacks would encrypt data until a ransom was paid and a decrypt key would be given. Recently, reports have shown that ransomware actors are threatening organisations with data disclosure. The cost to an organisation from fines due to data breaches is often higher than the ransom demand and this incites the company to pay the ransom. The reputational damage to the organisation can also make paying the ransom a more financially beneficial option for an organisation. Active monitoring and defence have been shown to reduce the risk to organisations from ransomware attacks. The early detection, quarantine and mitigation of a threat can seriously improve an organisation’s chance of recovery at minimal cost, both financially and reputationally.
Credential theft
Recent reporting has shown an increase in spear phishing attacks. Cyber threat actors are getting more sophisticated in the way an organisation is targeted and the increase in detection of widespread phishing makes a targeted spear phishing attack likely to succeed. Attacks have been seen to include URLs usually masquerading as a location that is of significant interest to the individual. Alternatively, attachments are used, and these are likely to be labelled as something of interest to the recipient and may include their name. Once a user clicks on the URL or opens the attachment, they are asked to enter additional credentials, normally these are O365 credentials. Once a user does so, they are normally presented with a blank screen giving the impression the login has failed.
Recent credential theft emails analysis by our Cyber Threat Intelligence team has highlighted the level of planning a threat actor puts into making the emails appear legitimate. The emails analysed had the recipients email pre-populated and a company logo in the spoof O365 login page. This is likely the result of conducting Open-Source intelligence (OSINT) which adds to the authentic look of the document increasing the chances of the recipient falling for a phishing email. Once an actor has gained legitimate credentials, they are likely to be used to launch an attack against the organisation such as ransomware. To finance operations, threat actors may also advertise these credentials for sale.
Threat Actors
With services such as RaaS being easily available to low-level unsophisticated threat actors and stolen credentials for sale, the type of actors an organisation will face is vast. Most cyber threat actors look to gain something from an attack. This is normally financially motivated through ransomware attacks or information compromise. Commercial espionage is often seen as highly valuable by nation states, and this can often go unnoticed within an organisation’s environment.
Most terrorist groups are able to maintain an online presence. Whilst this is predominantly used to promote ideologies and for recruitment, the ability to conduct disruptive cyber-attacks remain. A terrorist group may seek to gain control of an organisations website to promote its ideology or to spread an anti-western narrative.
Supply chain attack
Recently the world has seen large scale supply chain attacks from sophisticated threat actors that have had global consequences. Attacks such as Solarwinds and Kaseya show that an organisation can be vulnerable through trusted relationships with minimal human interaction. At Bridewell, we can conduct CTI led threat hunting to determine if a compromise has occurred before an actor is able to cause extensive damage to a companies’ network.
The Physical Threat
Insider threat
Criminal organisations have historically looked to coerce people on the inside of the organisation to carry out activity on their behalf. The threat actors may carry out blackmail to gain information or to have an employee plant malware onto a network. The criminal groups may use insiders to gain access to physical locations. This may also be targeted using employee complacency such as allowing people to tailgate into restricted areas.
Employees may also be subject to accidental disclosure, and in certain industries, journalists will be keen to learn what mitigations are in place to prevent a repeat of the September 11th attacks or an attack with equally devastating consequences. The journalists may seek to target employees of the organisation to provide information and may offer incentives such as financial rewards. In these circumstances employees may give away more information than they are authorised to do so.
Top tips to avoid becoming a victim
Invest in your staff
One of the biggest vulnerabilities an organisation can face, is poorly trained staff. Do those you rely on for the day to day running of the business know what a suspicious email looks like? Would they know what to do if they received one? Phishing simulations are a great way of understanding your businesses vulnerabilities. Users should also have an awareness of what they post online in their personal lives as this could leave them vulnerable to social engineering.
Protect the boundary
Boundary firewalls and internet gateway management are a key tool to protecting the network. Whether you adopt a whitelisting or blacklisting policy, understanding the threats to your organisation can be the difference between an attack being successful and failing. Cyber Threat Intelligence has become vital to understanding the threat landscape and allowing network defenders to be proactive in defence. Penetration testing can identify areas of vulnerability to an organisation allowing them to secure the perimeter from threats breaching this.
Appropriate User Access
It is important that users are given appropriate privileges according to their role. Any unnecessary permissions can make it easier for a threat actor with access to elevate their foothold. Restricting areas that employees do not need access to, can help prevent lateral movement within a network should a malicious actor breach your network.
System monitoring
Early warning can make stopping an attack much easier. A managed security solution can take away the burden of an organisation having to develop and mature their own model. As well as bringing a wealth of experience. Security Operations Centre’s (SOC) can ensure that an organisations estate is monitored 24/7 to detect and respond to alerts.
Patching
As far as is practicable, an organisation should ensure that their software is fully patched to the latest versions. Where this is not possible active monitoring of the affected systems can mitigate the risk of compromise. Organisations should look to patch as early as possible to prevent their network being compromised.




