Eclipsing drug trafficking and growing 15% year on year, cyber crime is expected to reach an annual global cost of $10.4 trillion USD by 2025. As more and more people enter the trade on both sides, you have to ensure you’re keeping one step ahead of the competition. So how do you continue to be proactive and develop new capabilities that help distract, evade and detect cyber threats?
Military strategy has a basic premise of "a moving target is harder to attack than a stationary one". So, as your own cyber wars and battles go on day after day, how do you:
- Use the same strategy to strengthen your defences
- Introduce the right capabilities into the enterprise, cloud and Operational Technology (OT) cyber defence models?
One of the fastest to implement that delivers a quick return on investment is the introduction of active defence through the use of deception technologies. These technologies - honeypots, tokens and canaries - are not new. In fact, Bridewell has been using them within our Managed Security Services (MSS) such as Extended Detection and Response (XDR) in IT and OT environments for several years.
However, the natural evolution of deception technologies is to automate their creation, destruction, changes and configuration to misdirect, attract and detect threats that exist within the environment. This new capability is being termed Automated Moving Target Defence (AMTD) by technology vendors.
What Are Deception Techniques?
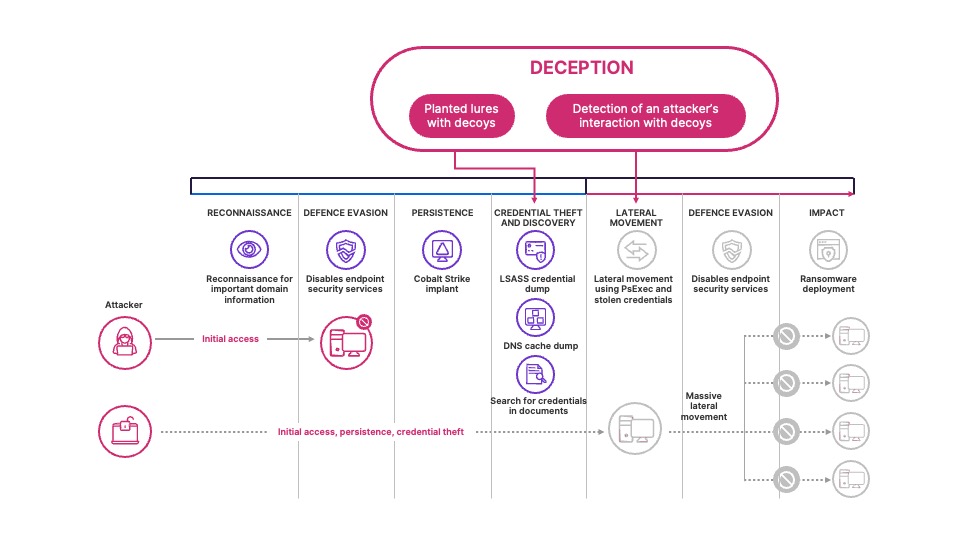
Deception techniques are a type of cyber security strategy that aims to misdirect attackers who have successfully breached your network. Instead of successful attacks providing attackers with access to your valuable or sensitive assets, they will be lead to deliberately planted assets that allow you to collect intelligence on them. This could include the methods they used in their attack, their behaviours and clues to who they are. This information can then be used to enhance your cyber defence by applying ‘lessons learned' from the attack.
Enterprise Deception
To apply deception techniques, you need to take the position of assumed breach; assume the attacker has credentialed access to your network. If your detection at initial access, persistence, and command and control isn’t sufficient, you can use deception to detect credential theft, discovery and lateral movement.
Such deceptions normally come in the form of fake devices, accounts, and network services that appear to belong to your network. The content can be a document, a configuration file, cached credentials, or anything that an attacker can read, steal, or interact with. The decoy will imitate important company information, settings, or credentials.
There are generally two types of lures available.
- Basic lures such as planted documents and link files, that have no (or minimal) interaction with the customer environment.
- Advanced lures such as planted content, cached credentials and interceptions that respond or interact with the customer environment. For example, attackers might interact with decoy credentials that were injected responses to Active Directory queries, which can be used to sign in.
The key to the best deception is to ensure that these decoys or lures look and feel just like real enterprise assets. This will likely lead to it being interacted with by an attacker. For example, XDR vendors have built the capability to leverage machine learning that can suggest decoy, lure and deception techniques for your organisation. These lures are tailored to your network and ways of working and are automatically deployed to your devices for you.
Cloud Deception
The concept of deception in the cloud is closely aligned with that of the enterprise; you're still trying to distract, lure and detect malicious activity within the environment. However, it is applied slightly differently, whether it is through the use of web bugs, decoy credentials and certificates, kubeconfigs (for containers) or by integrating decoy infrastructure into an existing infrastructure as code (IaC) environment.
In a cloud environment, deployed through IaC in your CI/CD pipeline, deception systems can be used to mimic complete windows or linux systems, serving network services such as file, proxy and database services. By deploying them within production zones, alongside production systems, an open service becomes an attractive system for attackers to interact with to see what other assets they can discover. Combining deception technologies such as decoy file shares, stored AWS credentials and Azure certificates increases the fidelity of alarms and gives your defence teams a prioritised active incident to rapidly respond to, reducing the dwell time of the attack.
Get Started Quickly
It doesn’t have to be difficult or costly to integrate these deception technologies into your environment. In fact, certain services such as canarytokens exist for you to quickly start to create decoy assets within your environment, such as documents and credentials.
At Ignite in November 2023, Microsoft announced the release of Deception within Defender for Endpoint. Deception provides many of the use cases defined above and is tightly integrated into the Defender XDR stack for customers with Microsoft Defender for Endpoint Plan 2, Microsoft Security E5, Microsoft 365 E5 at no additional cost.
By enabling deception and AMTD more widely and integrating it into your detection and response capabilities, you're able to mature your cyber defensive posture to reduce the risk and impact of the ever evolving and moving cyber threat landscape.





