TeamsPhisher is a phishing tool that allows threat actors to send you messages within Microsoft Teams while posing as a member of your organisation. These typically contain phishing links or executable files that the message will encourage you to open. In this case, the executable file was the DarkGate Loader malware.
TeamsPhisher is a tool we have raised awareness of in a previous blog and delivered to stakeholders as an advisory product. Recent work by our CTI team suggests that it's still a threat.
On September 22nd 2023, Bridewell Security Operations Center (SOC) identified that one of our customer’s users had interacted with a phishing link on Microsoft Teams. As the incident unfolded, there was an increase in users clicking on the phishing link, indicating a possible relationship with our recently published research on the TeamsPhisher tool.
Our analysts immediately isolated the initial devices and began digital forensic investigation. Following this, we documented event log activity and analytics to understand the threat and its observable behaviours. We determined that no further malicious activity was observed.
Investigating the network indicators, we were able to confirm the involvement of the DarkGate Loader malware and provided our SOC with actionable detections to enhance monitoring for this malware. Additionally, to ensure limited impact to business, we provided consultation and recommended actions to our customers regarding Microsoft Teams.
If you are looking to mitigate the risk posed by TeamPhisher, and similar threats, you should limit access between internal and external tenants to prevent a similar vector of delivery being possible in the future.
Key Takeaways
- Social engineering is, so far, the observed means of distributing this malware, which is used as a beacon to receive and enact commands issued by an operator-controlled management tool.
- Early adopters of this malware are likely seeking to leverage minimal reporting on DarkGate Loader compromises to increase impact of the infection chain.
- Suspected use of the TeamsPhisher tool highlights a potential for future scenarios where phishing attacks are increasingly deployed into what is typically a ‘trusted’ environment.
- Use of a large-language model (LLM) is likely to have increased efficacy of the phishing message used in this incident.
DarkGate Loader Malware
DarkGate Loader is a multi-functional loader, advertised as comprising a long list of customisable features. It is currently being used as an initial payload toward deploying secondary payloads and enabling actions-on-objectives. The malware first debuted in 2018, where it was observed distributing via torrent files, and was at the time described to be a capable malware and authored by a developer recognised for their level of sophistication.
In May 2023, the developer behind the tool announced on the Russian-language forums, ‘Exploit[.]in’ and ‘xss[.]is’, their intention to make this available for ’rent’ for up to ten users. Since this advert was raised, DarkGate Loader has been observed in the wild (ITW), with varied means of delivery and success.
Recent reporting has linked its use to a threat group known as TA577, who were associated with the successful distribution of Qakbot malware, whose botnet was recently disrupted in an FBI operation.
Incident Analysis
The following outlines the process taken by the malware upon infection, having been delivered as a malicious link over Microsoft Teams.
- User receives Microsoft Teams message from sender, who used a Chilean university domain, purporting to have found lost items in the company’s physical office environment.
- The sender included an attachment (zip archive file), titled along the theme of lost items, requesting the user to review so they could either claim or support owner identification.
- “Lostitems_Pictures_ARCHIVE[.]zip”
- While being labelled as ‘external’ in the top of the window, the sender sign off below the message body included the target user’s company domain.
- Upon user click, a ZIP archive file is automatically downloaded from an external SharePoint site. Initial devices showed signs of attempting to beacon out to an unknown IP address.
- After initial actions were taken by Bridewell to halt malicious activity and block any further communication attempts, a second Microsoft Teams message was received (shown below).
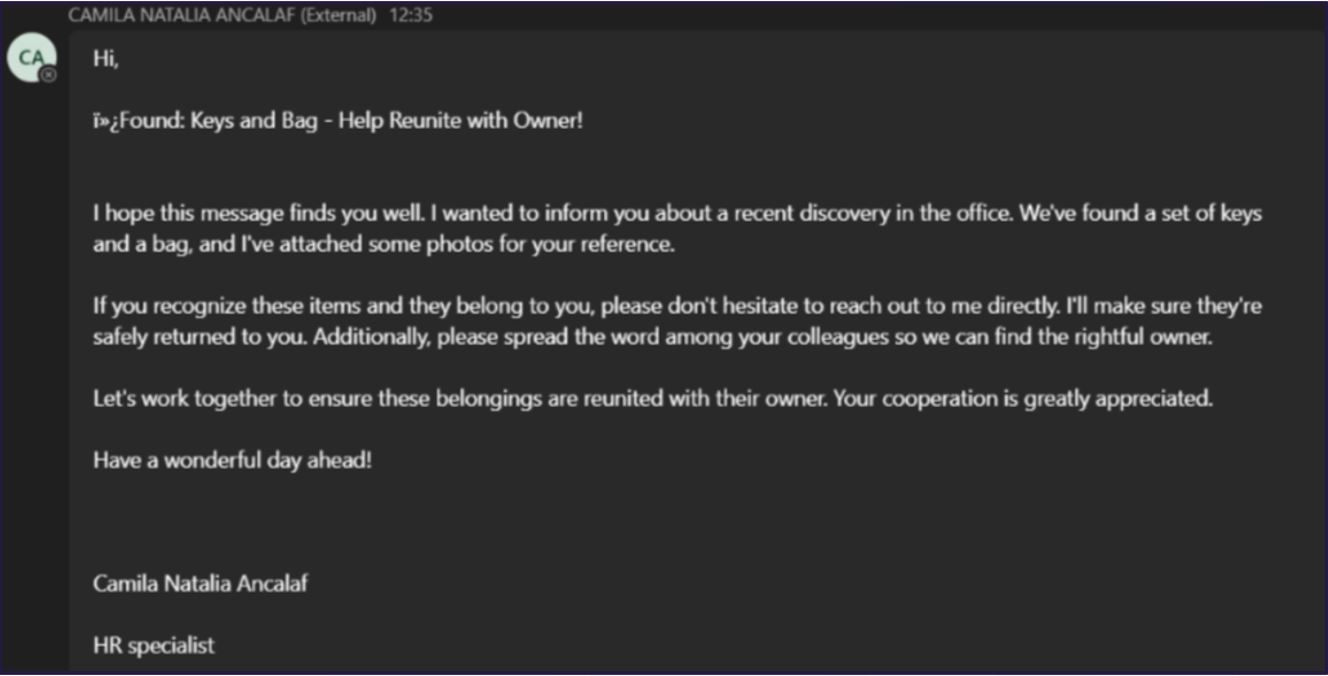
Figure 1. Teams message delivering DarkGate phishing link
- In the second message, the sender:
- Uses a different Chilean university domain
- Poses as a HR employee
- Continues to use the receiving user’s company domain in the sign-off
- Bridewell’s SOC were alerted to the arrival of this message having developed detections from the first instance, and no further beaconing traffic was successful in the second instance due to effective actions taken during the initial phase of the incident.
Infection Behaviours
Several evasion techniques were employed by the malware, such as parent process ID spoofing, portable executable injection, and use of signed processes. This meant our SOC analysts would have to identify all activity, now suspected to be related to malware activity, associated to those processes.
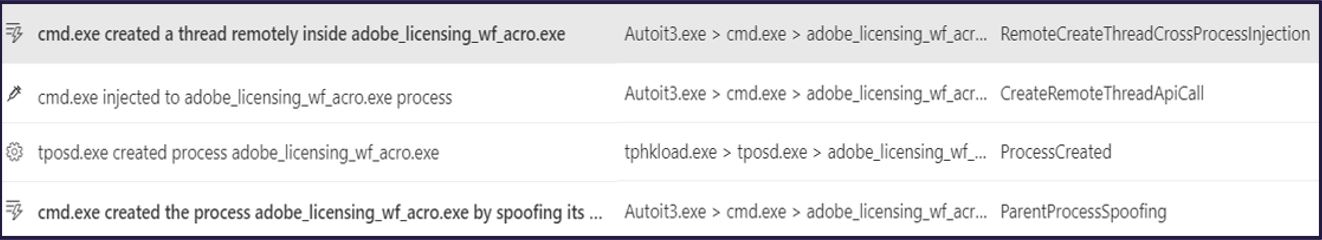
Figure 2. Observed behaviours of the DarkGate infection process
Cases of these efforts can be seen below, which ended up as tracked behaviours feeding into detection-based hunting within the customer environment to support investigations.
These behavioural indicators have been collated to form tactic, technique, and procedure (TTP) mapping to enhance customer environment coverage through rule-based detections. For example, the irregular/high-frequency execution of AutoIT scripts was a suitable behaviour, in addition to others, for fingerprinting elements of the infection.
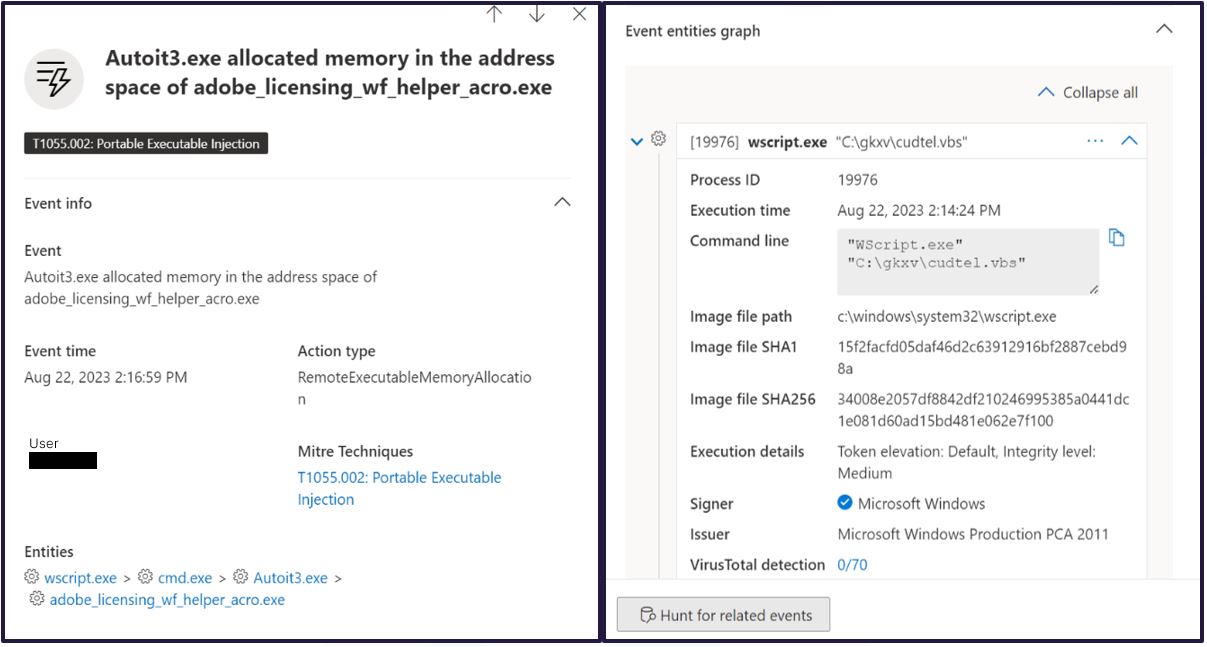
Figure 3. Behaviours identified for TTP-based detections
An observed ‘collection’ TTP of DarkGate Loader was the effort to capture keystrokes, likely to collect user inputs for items such as credentials and network assets for subsequent ingress vectors.
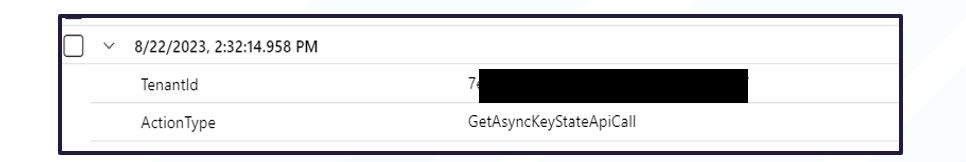
Figure 4. Identified 'Collection' behaviour
The malware has recently been observed deployed in a number of phishing-related attacks, through which a number of security researchers have identified the infection chains and their subtle differences. The infection chain variants (as presented by Telekom Security) on the right (figure 5) matches that seen by our investigations. The flow diagram demonstrates how the process initiates upon execution of a .vbs script.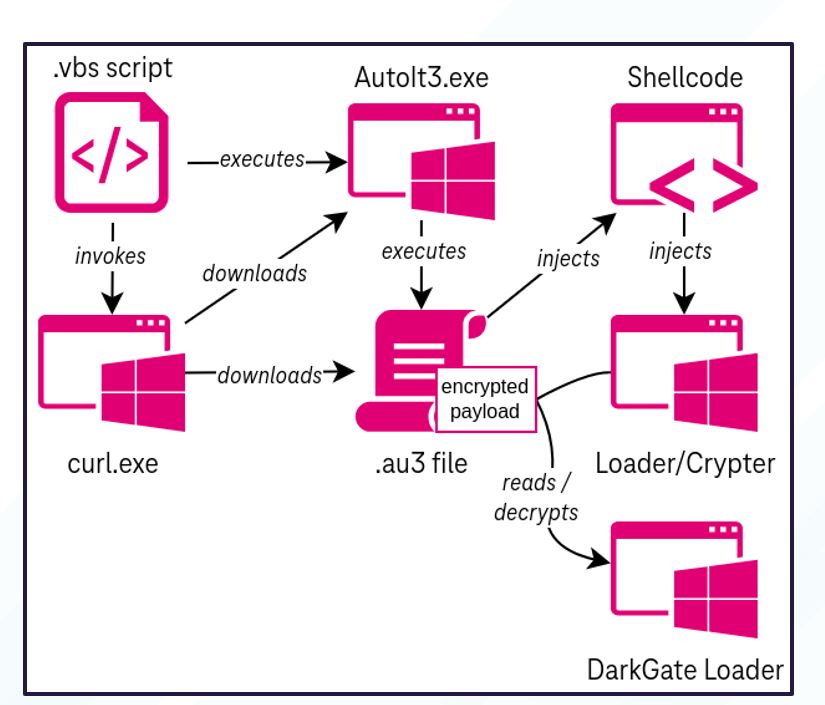
Figure 5. Infection chain reported by Telekom Security
While another variant that has been observed initiates through the download of a Microsoft Installer (.msi) file, this variant did not comprise as complete a set of behaviours like the .vbs infection chain (figure 6).
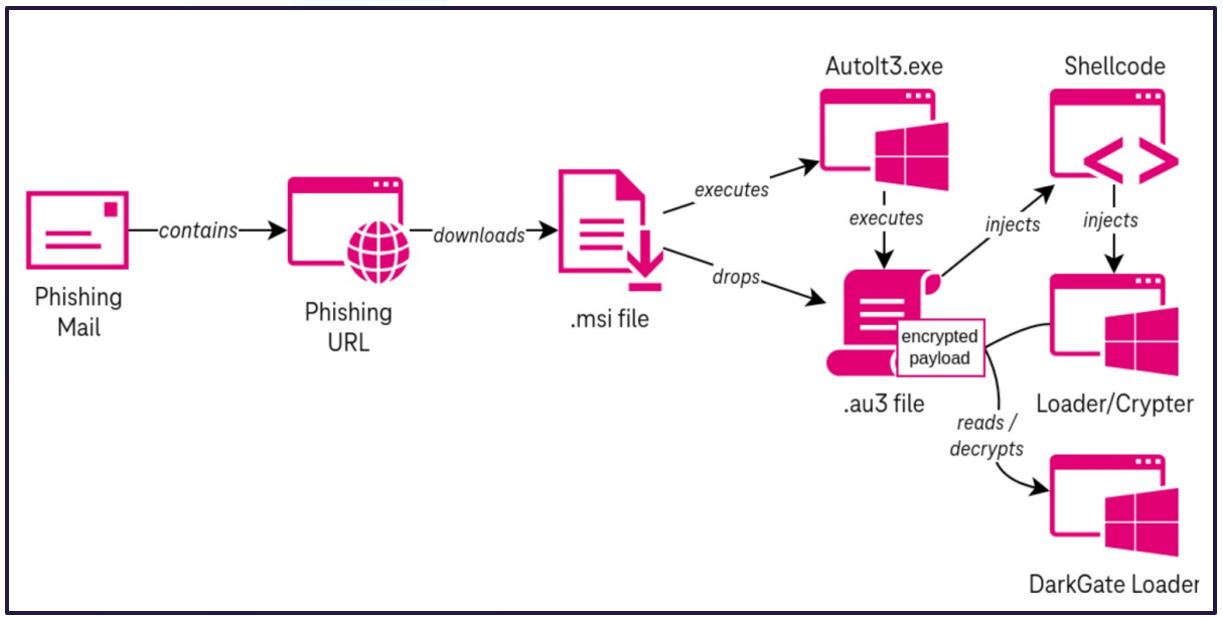
Figure 6. Alternate infection chain reported by Telekom Security
Infrastructure Investigation
Initial investigation findings identified the malicious file attempting to call out to IP Address 5.188.87[.]58 (IP-A) on port 2351 and 9999. This had zero detections on the file analysis platform VirusTotal (at the time of writing) but recorded three communicating files (“#xCF”), with one as recently as 17/08/2023. Additionally, it matched Yara rules for the DarkGate Loader malware, also with zero detections (at the time of writing).
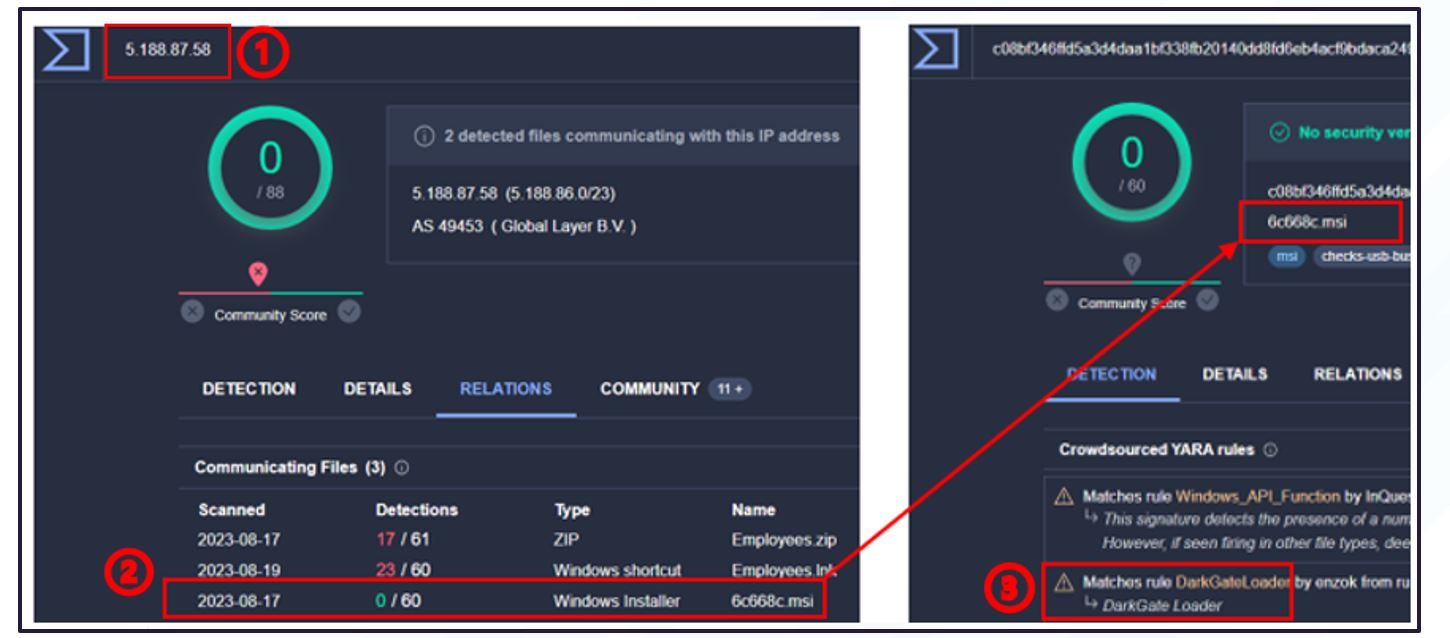
Figure 7. Initial investigation into IP-A results linking to DarkGate malware
- Outbound network traffic calling to IP-A, which had zero detections across VirusTotal.
- IP-A seen hosting a clean, communicating “.msi” file.
- Crowdsourced Yara rule highlighted to match with DarkGate Loader malware.
While this indicator was used as an initial attributing identifier, the .msi file shown in the image was not identified in the customer environment.
Throughout analysis and investigation of the incident, the IP address shown above has seen an increase in the number of communicating files. These all follow a theme of corporate updates and notifications. (See image below).
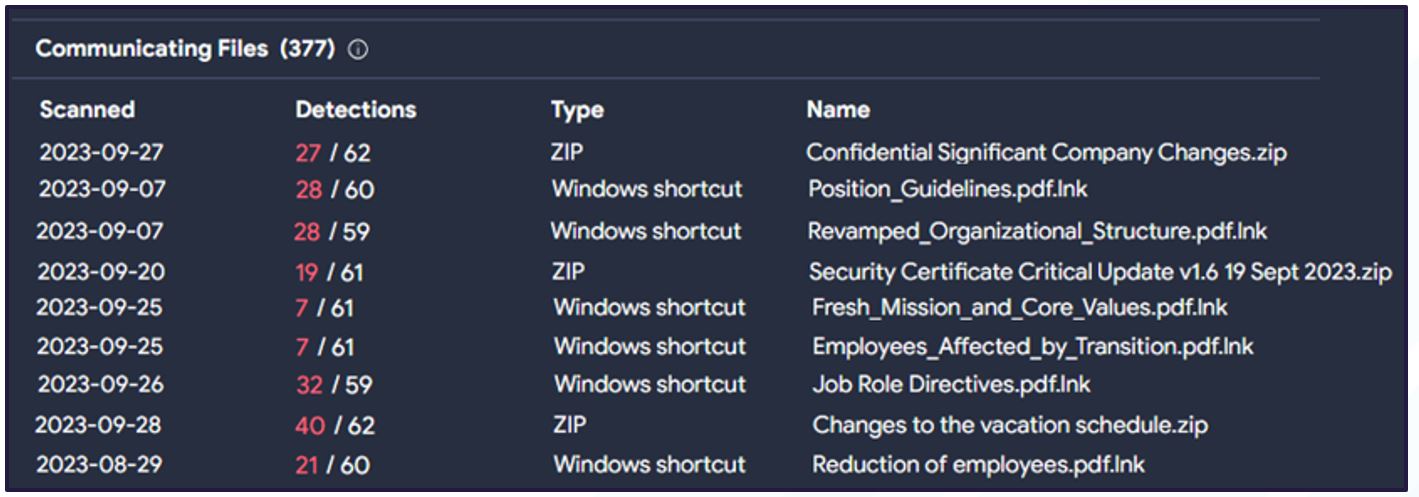
Figure 8. Examples of 'official' file-naming convention
Open-source reporting on DarkGate Loader uncovered separate delivery mechanisms and malware analysis, but little commentary was found on C2 communications. This is in line with Bridewell CTI investigations into the infrastructure observed in this incident.
Whether the deployment of the malware is strictly limited in its use or managed by a single, controlling operator, or the developer themselves, the operational security surrounding it is evident in this case as well as others that have come before it.
The C2 communicating ports used by the malware were masked by the adversary to prevent network scanners such as Shodan, Censys, Fofa, and others, from scanning them. As such, profiling the C2 infrastructure to achieve a level of confidence in attribution continues to prove a shifting challenge.
While standard, free-to-use open-source scanning platforms were unable to successfully probe the 5.188.87[.]58 IP, a commercial platform containing netflow enabled Bridewell CTI to find the below results showing a list of potential compromised victim networks communicating outward to the [.]58 IP.
We assessed that, based on past behaviours, network traffic on port 2351 is to notify the operators of successful infection, with the subsequent communication on port 9999 being the C2 operator activity.
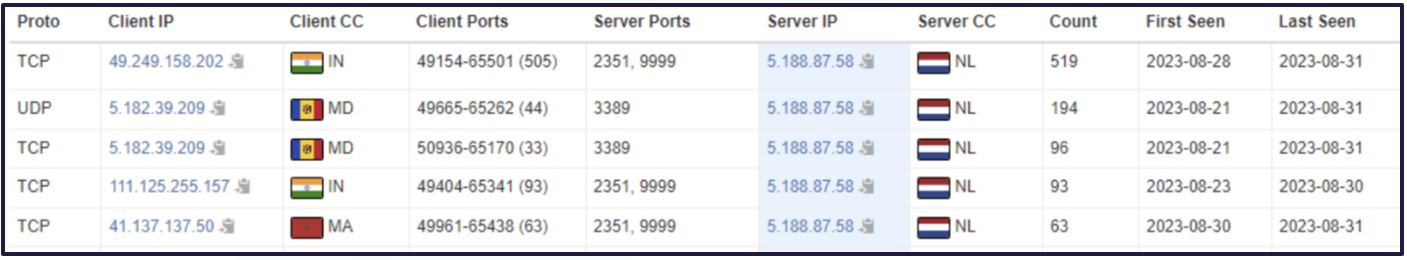
Figure 9. Observed outbound traffic toward suspect server IP
The following list of IPs show potential buyers/operators of DarkGate Loader using port 3389 and the Remote Desktop Protocol (RDP) service to interact with remote management applications.
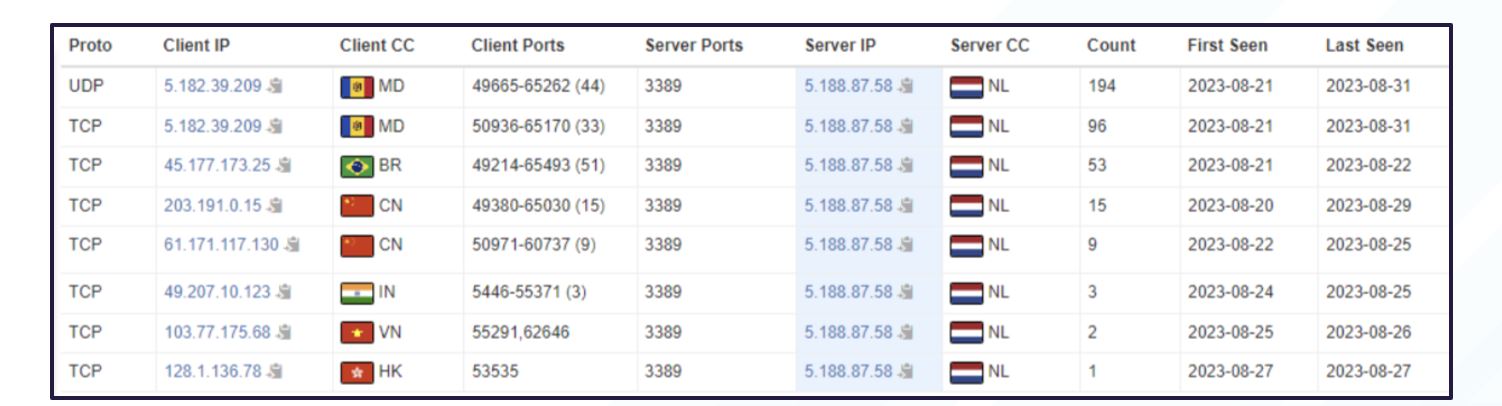
Figure 10. Potential DarkGate affiliates communicating through RDP service
Potential ‘TeamsPhisher’ Involvement
What does TeamsPhisher look like?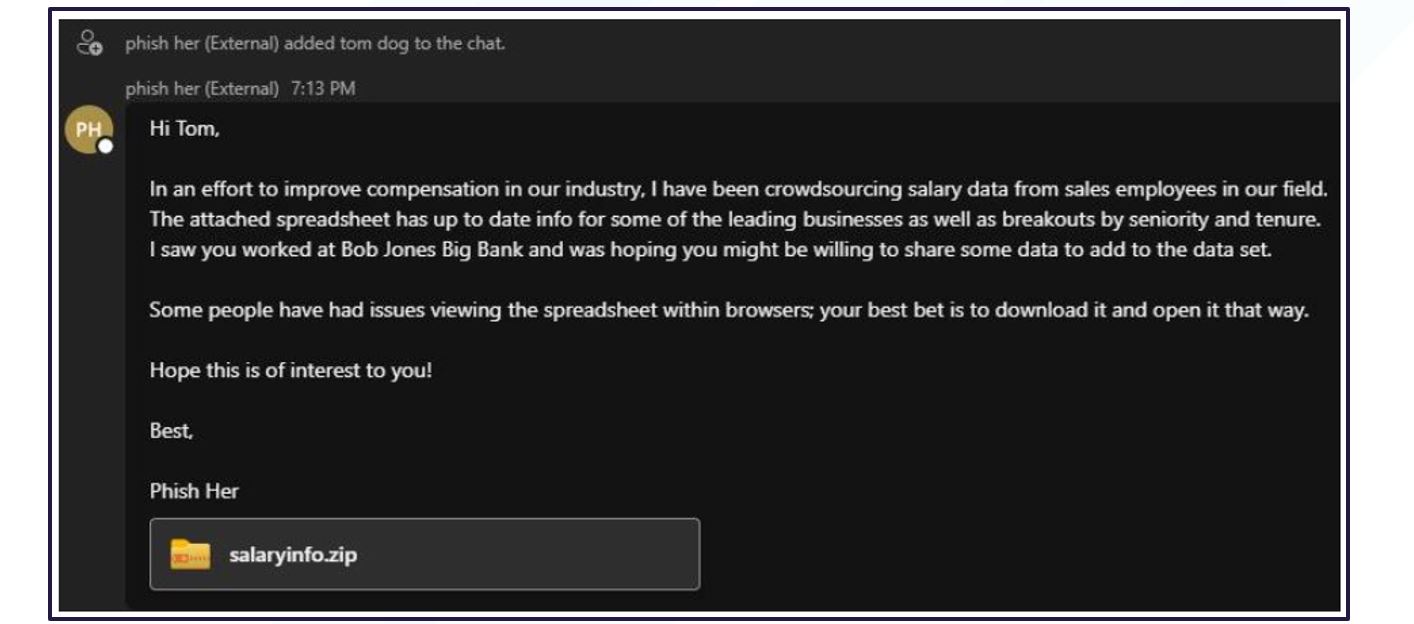
Figure 11. Example of TeamsPhisher message from user perspective
The TeamsPhisher tool, created by a red teamer, is designed to automate attachment delivery from an external tenant to an organisations’ internal employees by switching the internal and external recipient ID on the POST request (not visible to a receiving user).
This would present as a new chat to a targeted user, appearing to come from an individual within their organisation. Additionally, TeamsPhisher has a configuration option that allows an attacker to turn on authentication requirement from the recipient – a setting that may disarm initial scepticism.
See below for a screenshot of the Microsoft Teams message received that included an attached file leading to DarkGate Loader infection.
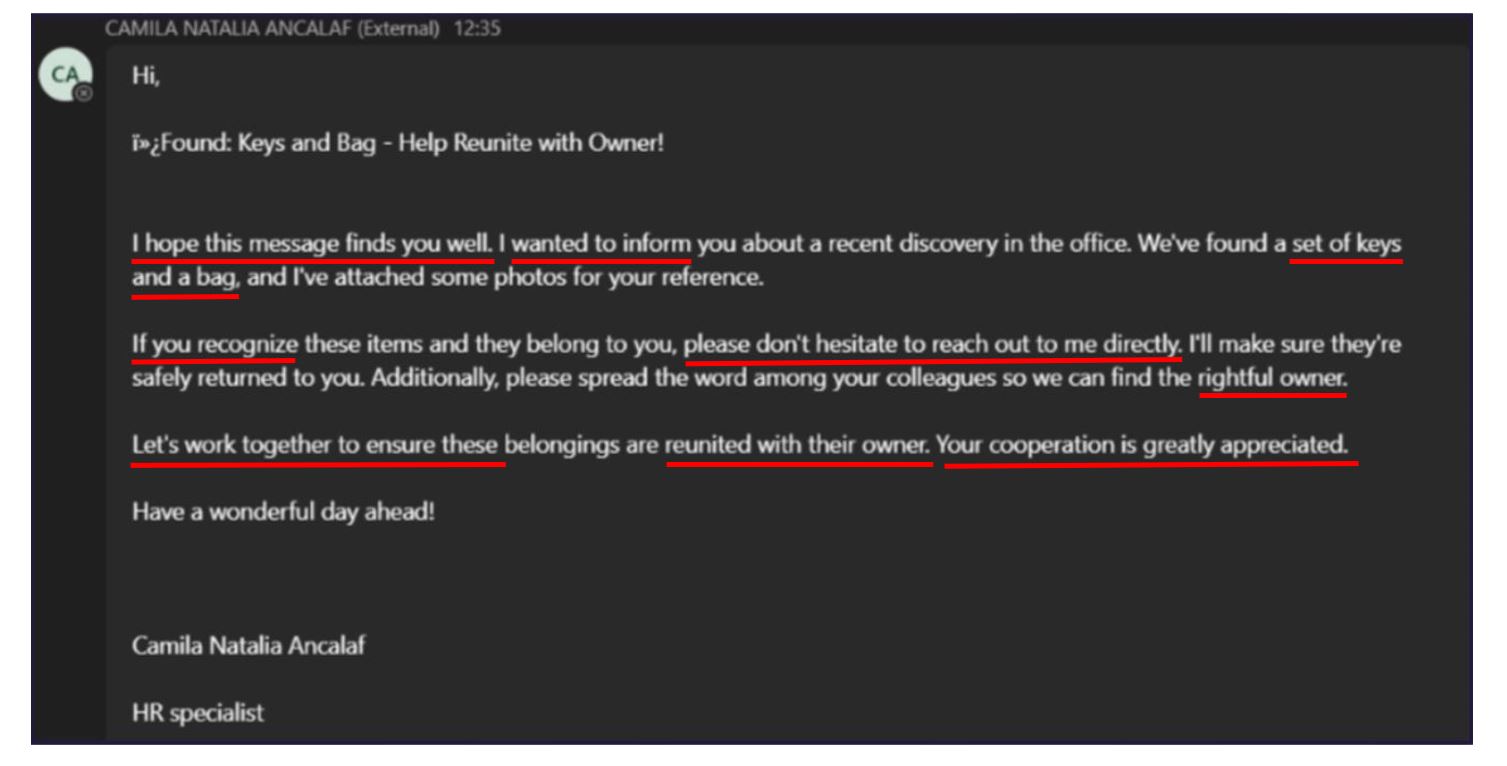
Figure 12. Message received by users in recent incident
Points to note for awareness and education opportunities:
- Formality. It is very formal for a Teams message and does not include the recipient’s name, which you would need to start a new chat with someone in the company.
- Irregular Symbols. Strange symbols not commonly used between colleagues in Teams messages should draw attention and further scrutiny. If nothing malicious, it may indicate a software issue that should be raised with the Microsoft Teams admin personnel.
- Internal/External Tag. At the top of a new Teams message, a tag will be displayed indicating that the sender is “External to Your Organisation”. In this example, the sender signs-off with an internal domain, which contradicts the ‘External’ tag. This should draw attention and scrutiny.
- Language/Phrasing. In the wake of recent large-language model (LLM) developments, it has become known that threat actors will likely use them to construct realistic content to be used in social engineering attacks. These can be convincing, and colleague awareness, education, and training is the best means of combatting this vector of attack.
See below for a screenshot of a message generated by Bridewell CTI, where red boxes have been used to highlight matching wording/phrases/terminology as that seen in the malicious Microsoft Teams message.
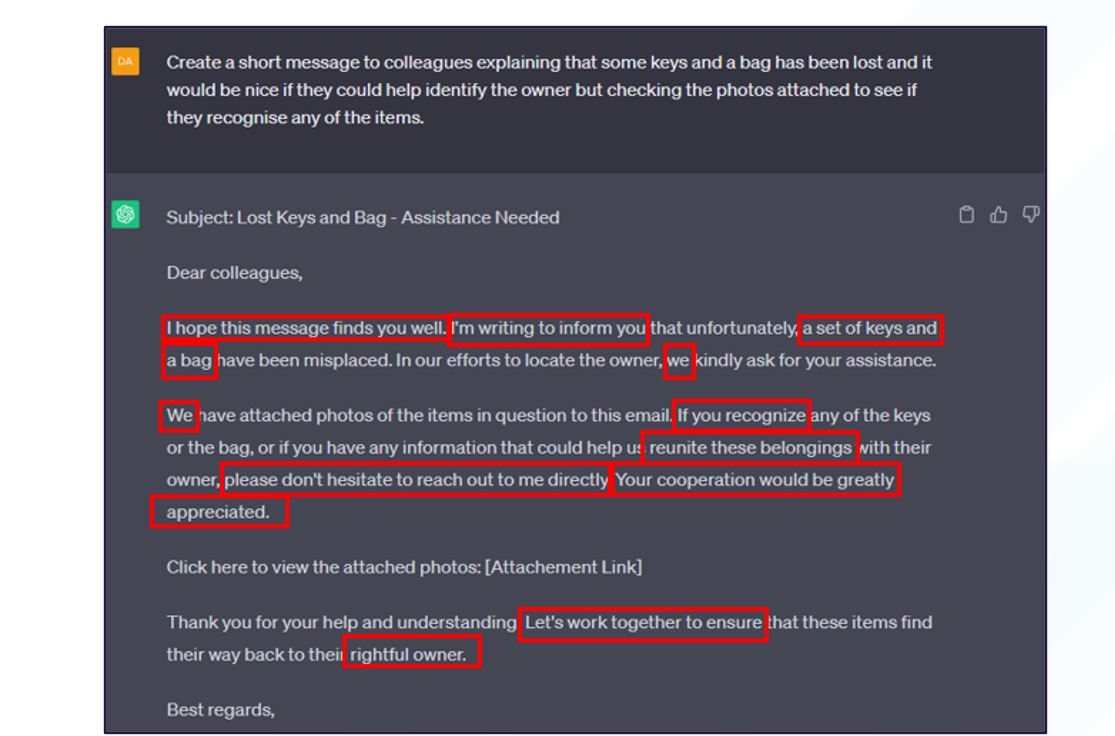
Figure 13. Bridewell CTI-generated message related to theme seen in incident message
Comparing the received message with what we generated using ChatGPT, plus its involvement in what appears to be a group distribution phishing attack, we assess with moderate-to-high confidence that the content used in this incident was generated using an LLM platform.
The use of a generative AI tool to construct the realistic message leverages social engineering and psychology (reciprocity and helpfulness) to result in a message any recipient could engage with irrespective of department/location/experience/etc. All that was being asked was to look at an image and conclude yes/no.
It is a line of query that can be applicable to a large number of users: 'Do I recognise this thing?’; if yes, ‘simply respond and be helpful’. At that point, they would have clicked the link to reach a yes/no answer.
Concluding Remarks
Why is Teams seeing a rise in use by threat actors to distribute malicious links?
The recent advertising of DarkGate comes only a few weeks after the release of the TeamsPhisher tool research publication. The apparent unreported use of Teams to deliver phishing links, plus the recently available DarkGate Loader malware, present as a new opportunity and capability respectively.
In this instance, the use of Microsoft Teams as a delivery mechanism poses greater reliability for user interaction as email phishing has wider education and awareness versus a compromise via Teams, which by comparison has less coverage. Use of the ‘TeamsPhisher’ tool is unconfirmed, however this incident does present similarly to how TeamsPhisher would typically be viewed by the recipient. Specifically, that a fake, external sender using a legitimate form of Microsoft account to deliver a malicious link, while posing as an internal sender to bypass Microsoft Teams’ security mechanisms.
What actions were taken?
All network elements associated to the two DarkGate Loader links’ activities were blocked, rendering subsequent interactions with them unable to function as intended. Bridewell’s digital forensics capability was also deployed to analyse and recover compromised devices to ensure isolation protocols had been effective and would allow employees to resume routine working securely.
We put forward the recommendation to disable communications from unapproved external accounts and apply controlled accesses to select Microsoft tenants known to them. It was also recommended that the recipients of the phishing link be entitled to informative updates on the associated risks of engaging with links and the appropriate considerations that should be taken. In addition to supporting the provision of employee awareness and training, we have also committed to facilitating the review of incident response protocols and how phishing simulation exercises could best be employed to develop robust defensive culture for the wider employee-base.
Appendix
5.1 TTPs associated with DarkGate Loader deployment
| Tactic & Technique/Sub-Technique | Observed Activity |
|---|---|
| Initial Access | |
| T1566.002 – Phishing: Spearphishing Link | Tagged by Teams as external, but signed off in message, posing as internal employee e.g., HR |
| T1566.003 – Phishing: Spearphishing via Service | Delivered to users via Microsoft teams |
| Execution | |
| T1059.005 – Command and Scripting Interpreter: Visual Basic | cmd[.]exe created file dilddt[.]vbs |
| Persistence | |
| T1547.001 – Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | [.]lnk was created by adobe_licensing_wf_helper_acro[.]exe under the user startup folder “C:\Users\REDACTED\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\[.]lnk” |
| Privilege Escalation | |
| T1055.002 – Process Injection: Portable Executable Injection | ssvagent[.]exe injected to jp2launcher[.]exe process ssvagent[.]exe changed the thread context remotely to inject code into notepad[.]exe |
| Defence Evasion | |
| T1070 – Indicator Removal | cmd[.]exe deleted Autoit3[.]exe cmd[.]exe deleted bvfv[.]exe Explorer[.]exe deleted LostItems_Pictures_ARCHIVE[.]zip |
| T1134.004 – Access Token Manipulation: Parent PID Spoofing | Autoit3[.]exe created the process adobe_licensing_wf_helper_acro[.]exe by spoofing its parent process to ping[.]exe Autoit3[.]exe created process AcroCEF[.]exe by spoofing its parent process to WTabletServiceISD[.]exe |
| Credential Access | |
| T1539 – Steal Web Session Cookie | cmd[.]exe attempted to decrypt credentials – cmd[.]exe /cookiesfile C:\Users\REDACTED\AppData\Local\Microsoft\Edge\User Data\Default\Network\Cookies cmd[.]exe accessed the browser cookies file Cookies |
| T1555 – Credentials from Password Stores | Notepad[.]exe enumerated vault credentials from the Credential Manager Notepad[.]exe accessed browser web data file ‘Web Data’ Notepad[.]exe accessed browser saved passwords file ‘Login Data’ |
| Collection | |
| T1056.001 – Input Capture: Keylogging | Event of type [GetAsyncKeyStateApiCall] observed on device – seen 7-9 times per second. |
| Command-and-Control | |
| T1571 – Non-Standard Port | Wscript[.]exe established connection with 5.188.87[.]58:2351 adobe_licensing_wf_helper_acro[.]exe failed to establish connection with 5.188.87[.]58:9999 ssvagent[.]exe established an outbound application layer protocol communication with 5.188.87[.]58:2351 |
Table 1. TTPs observed during the DarkGate intrusion.
Indicators of Compromise
| Indicators | Action | Type |
|---|---|---|
| 5.188.87[.]58:2351 | C2 | IP |
| 5.188.87[.]58:9999 | C2 | IP |
| 237d1bca6e056df5bb16a1216a434634109478f882d3b1d58344c801d184f95d | AutoIT | SHA256 |
| fa23e577bf553bb9ad98a94ff33731d257ec35c9f1fbf5b31cb6280e54cd3652 | Lost Items zip | SHA256 |
Table 2. Captured IOCs during DarkGate intrusion
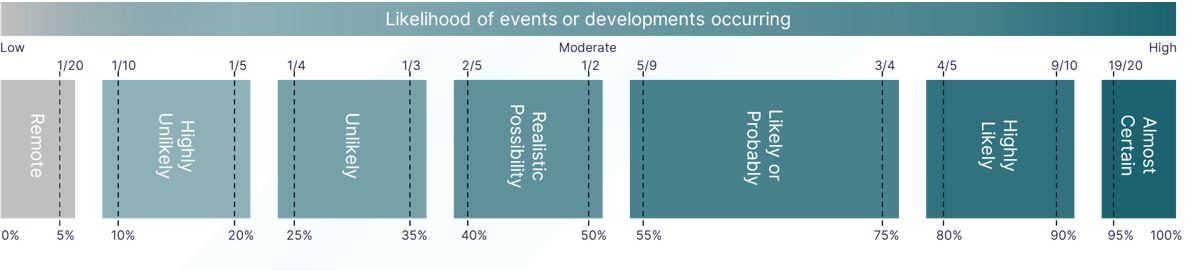
Probability Yardstick
Threat assessments and reporting will provide some indication as to the likelihood of a threat actor attempting to target you, your organisation or sector, or the tactics, techniques, and procedures used to perform an attack. Such assessments will often use probabilistic language. The yardstick, as below, gives general probabilities associated with the language used. This provides a central professional standard for government intelligence assessment to reduce uncertainty around the use of probabilistic language.
Traffic Light Protocol
Traffic Light Protocol (TLP) ver. 2.0 ensures that intelligence is shared with those who it will have the most impact with. There are five levels to the TLP. They work in similar ways to a document marking scheme.

.tmb-6_col_resi.jpg?sfvrsn=bee199ba_1)




