Malware is an ever-present but constantly changing threat in the cyber security world.
Much like real world infections, cyber security threats are always adapting, with new malware samples constantly being identified. These threats can vary wildly, from very simple scripts that download adware and popups, to sophisticated software with obfuscated code and modular design.
Being on top of this ever-changing threat requires businesses and security teams to always be up to date with new knowledge and findings. Having the ability to discover and analyse new malware or attacks is crucial to allow analysts to find ways to prevent and remove these threats from our networks.
Malware analysis can be a difficult, time consuming task and new techniques and tools are always being employed by attackers to slow down analysis and confuse security researchers.
In 2012, an attack was discovered under the name of Flame (or SkyWiper) and is considered by some as the most complex malware of all time. Alexander Gostev of Kaspersky Lab stated that the modular malware was almost a huge 20 MB in size upon deployment and just one of the modules contained over 3,000 lines of code.
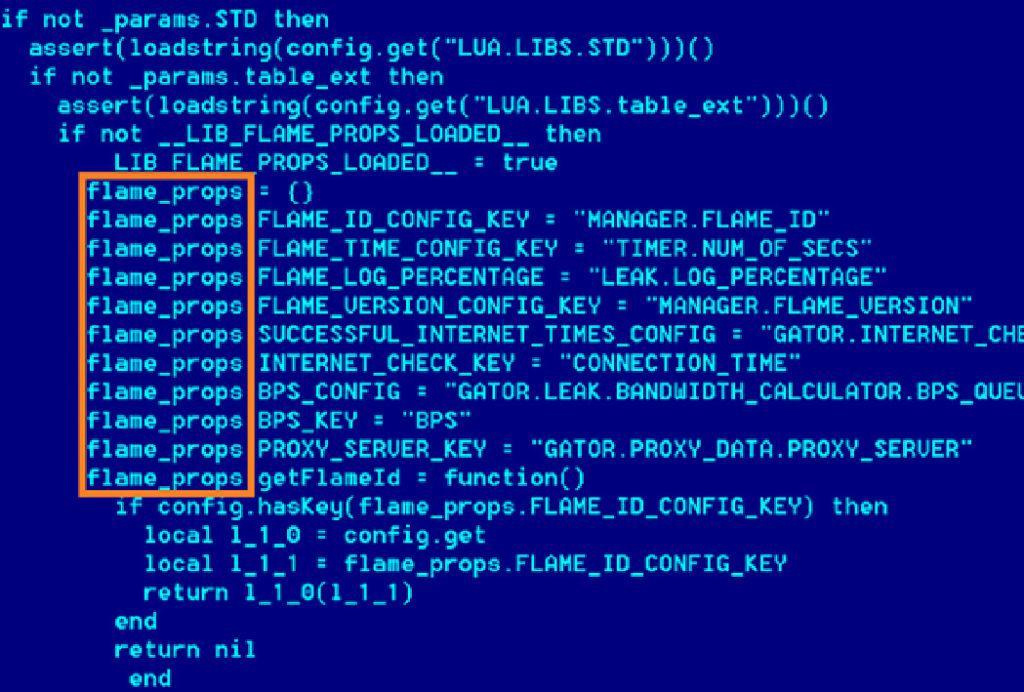
Increasing the size of the malware dramatically increases the complexity required to analyse a sample, requiring the analyst to be skilled in software development and programming languages.
Cuckoo
A very handy, open source tool known as Cuckoo was developed by Google in 2010 and has been growing ever since, with a 1.0 release in 2014. This modular tool provides a way to effectively automate the analysis of malicious code, allowing analysts to run tests on multiple suspicious files simultaneously and on different virtualized environments.
Automated malware analysis allows researchers to perform manual work at the same time, providing more information to support the overall investigation. Automation tools also provide an entry point to less experienced analysts, allowing them to carry out tasks which may have previously been above their skill level. They also enable them to learn from the collected data.
Scripted analysis also allows testing to be performed on multiple machines at once to record results from multiple operating systems and software configurations. This means the same suspicious file can be tested on an Linux machine and a Windows machine at the same time. It may even be possible to test two machines with the same operating system but with different installed software packages or even differing network configurations, one with a VPN, one without. The possibilities are endless.
To learn more about Cuckoo, visit the website directly here.
How does Cuckoo work?
Cuckoo can be set up on Windows, Linux and Mac and can utilise nested virtualisation (the preferred method) or even physical machines to carry out its analysis. The benefit of using virtualised instances is that the analyst can quickly create or remove virtual machines (VM’s) and Cuckoo will automate the process of starting and reverting machines from predefined snapshots.
To create a demonstration for this blog, we configured Cuckoo on a virtualized Ubuntu desktop using Virtualbox and configured a Windows XP VM inside the Ubuntu desktop for use as the malware testing sandbox. This Windows XP machine was configured with a baseline snapshot to use and revert to each time the process runs.
Once the configuration of Cuckoo and virtual machines has been completed, a suspicious file can be fed into Cuckoo and the tool will automatically use the Windows XP VM snapshot and analyse the suspicious file inside it. When the analysis is complete, Cuckoo will turn off the Windows XP VM, revert to the initial snapshot for future testing and provide a formatted, easy to read report containing the findings.
Cuckoo can be configured to run in command line interface (CLI) mode or using the optional Web graphical user interface (GUI) which will be demonstrated in this blog.
Optional modules
One of the main benefits of Cuckoo is that it is open source and modular, meaning that it has the capability to provide extra testing methods depending on which modules or extra features are installed.
These extra features include integration with Volatility to provide memory analysis and categorisation with YARA signatures, network traffic packet capture using tcpdump, and it even provides the ability to screenshot the analysis VM or connect to VirusTotal to provide information using the hash values of the suspicious file. A full list of optional modules can be found here.
The Analysis Stage
As a demonstration, now that we have set up our Cuckoo environment and associated sandbox virtual machines, we are going to use it to test a well-known piece of malware known as WannaCry. In 2017 WannaCry ransomware caused significant impact to businesses across multiple industries, taking advantage of a former NSA zero-day exploit named “Eternal Blue” that was leaked to the public by the infamous “The Shadow Brokers” group.
Firstly, we upload the infected file to the Cuckoo web interface to begin processing.
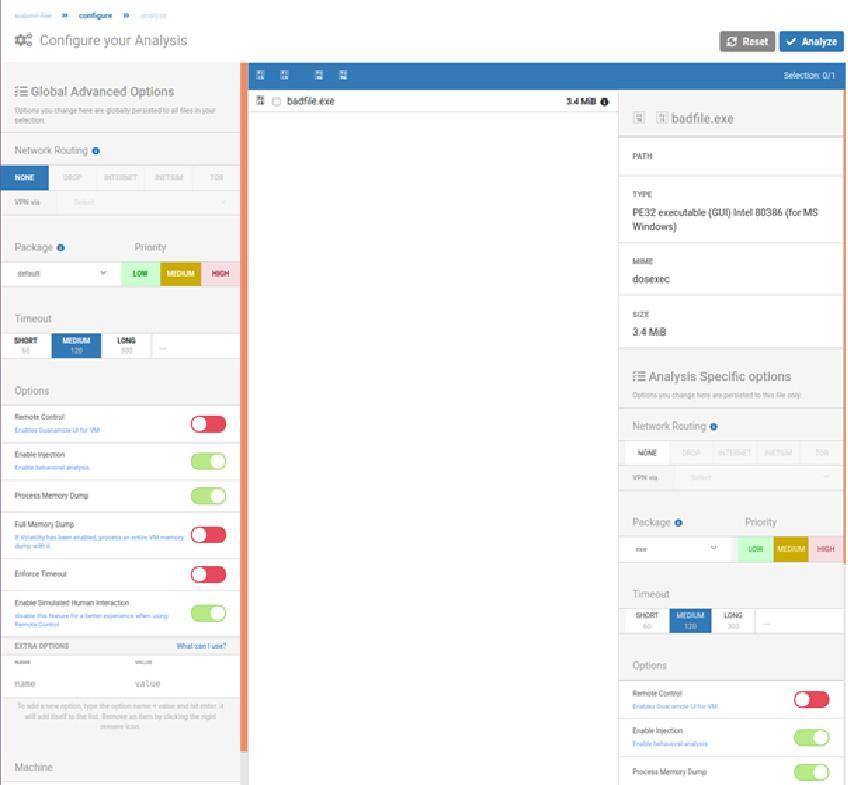
There are many different options available for configuration regarding the parameters and options to change how the file is analysed. For example, there is an option to enable or disable collection of a full memory dump or an option to simulate human interaction within the VM to prevent the malware from being able to detect that it is being analysed.
There are also options available to configure networking, enabling different testing scenarios such as routing through VPN technology to simulate different countries or geolocations. The advantage to this being that we can test if the malicious code acts differently depending on its perceived location. You can find the networking documentation for Cuckoo here.
Once the file has been submitted for processing, it will appear as a scheduled task. At this stage, Cuckoo will initiate the selected test VM and execute the suspicious file inside the sandbox. This process can take a varying amount of time depending on the file and will produce a report containing all the collected information once this is complete.
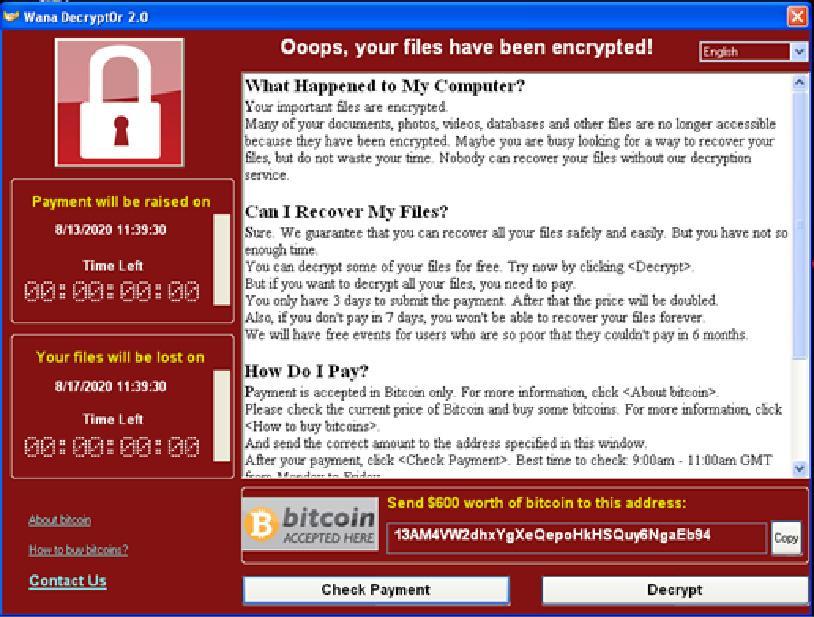
The WannaCry Ransomware
Ransomware is a specific type of malware which aims to encrypt a user’s files, rendering them useless until a ransom or sum of money is paid. If the victim is lucky a key will be provided enabling the files to be decrypted.
Common attack vectors are phishing or by tricking a user into downloading the malware. However, such malware can sometimes be found embedded in seemingly innocuous documents such as Office Word or Excel documents or even via “drive by download” attacks where a compromised site can target visitors using exploit kits to deliver malware. Other methods of malware delivery include credential compromise and/or exploitation of vulnerabilities in remote desktop protocols (RDP) used to obtain access and subsequently infect machines.
WannaCry is a piece of malicious software used to carry out crypto ransomware attacks in which the user’s files are encrypted with a key provided in the initial malware dropper. Once the user’s files have been encrypted, the infamous ransomware message appears, asking the user to pay a sum in Bitcoin to release their files.
Once analysis has been completed, we can view this from the web GUI in a handy, readable format. The summary section shows an overview of the findings with information on the file size, type, hash information and includes a score relating to how dangerous the file appears to be.
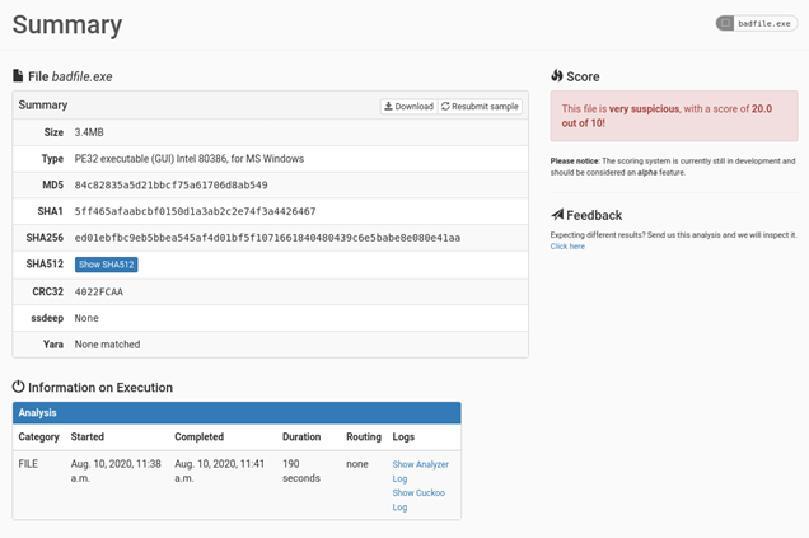
The report details a list of signatures triggered during the analysis which can be used to detail the specific operation of the malware in question. It is possible to write your own signatures to tailor it to your own specific needs, or alternatively, use community created signatures instead which you can find here.
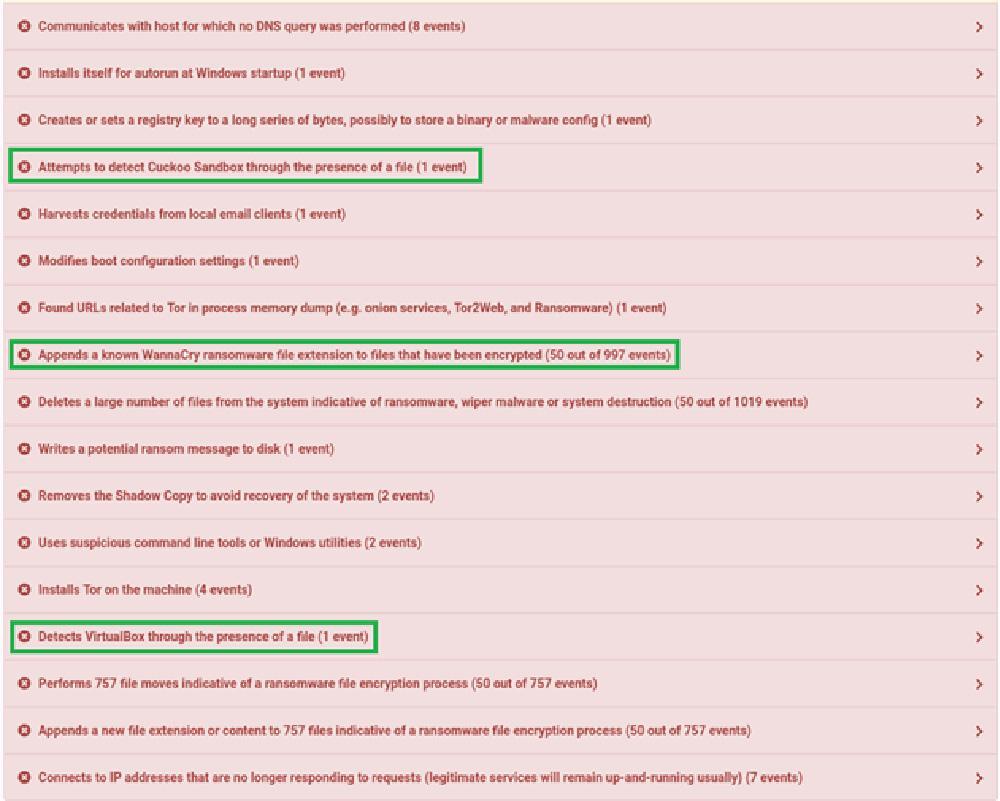
A few interesting signatures have been triggered during this analysis, including the fact that Cuckoo has detected that the malware has attempted to perform sandbox evasion techniques and that Cuckoo has correctly identified this file as being infected with the WannaCry ransomware variant specifically.
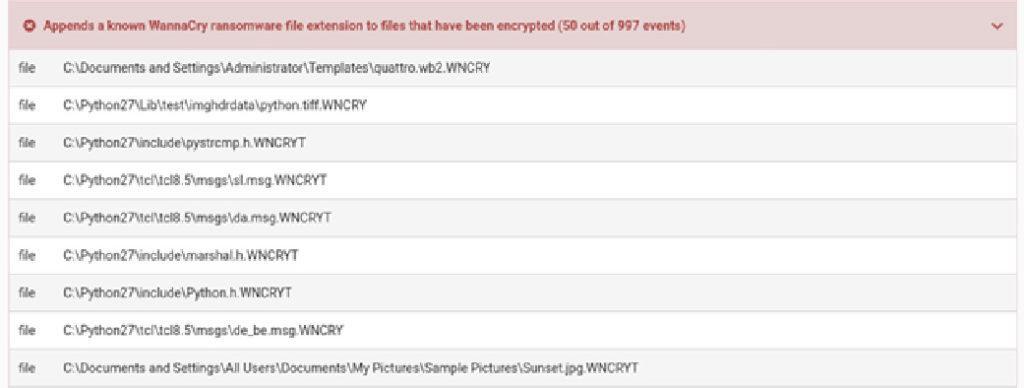
In this case, the WannaCry malware will append the “.WNCRY” extension to encrypted files and the report has highlighted the files which have been modified. This can be used to identify which files have been encrypted and provides us with an indicator on detecting this malicious code in the future.
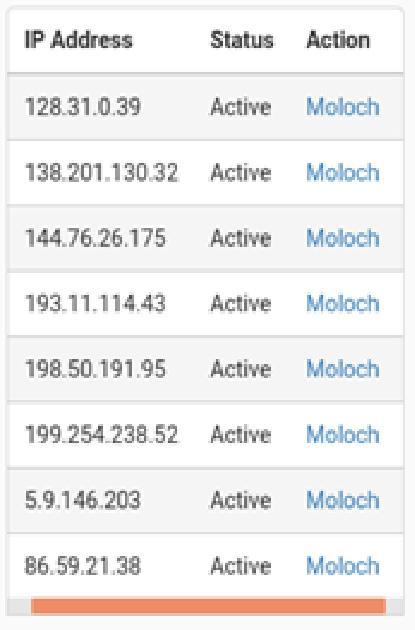
One other piece of interesting information uncovered by this report is that during the analysis of the WannaCry malware, communication has been attempted to several different IP addresses. This communication has been flagged within the report and could indicate a few different possibilities including potential command and control communication or even data exfiltration.
This report has also uncovered communication to several suspicious IP addresses. This could be further investigated and is potentially an indicator of command and control activity or even data exfiltration. One of the optional modules we could use here is Moloch to provide additional network traffic or PCAP information relating to the activity against these IP addresses. Moloch is a tool that can store and index network traffic in standard PCAP format.
More information around the report content can be found here.
Conclusion
Cuckoo Sandbox is a useful tool for any Security Operations Centre (SOC), it allows analysts of all experience levels to produce automated reports detailing the operation of malware in a quick, structured and easy to read manner. Outputs of the analysis including indicators of compromise can be used by incident responders, SOC analysts and the Cyber Threat Intelligence (CTI) team to detect and respond to previously unknown threats within the environment.
Using Cuckoo to create these automated processes gives analysts more time and freedom to supplement the reports with manual malware research methods giving a clear and concise view of security threats.





