As part of Bridewell Cyber Threat Intelligence’s (CTI) ongoing tracking of malicious infrastructure, we’ve identified new Meterpreter hosts and made some interesting observations:
New connections have appeared, with possible links to Black Basta affiliates.
Pivoting has uncovered additional undetected Metasploit C2 servers
The BlackBasta and Pikabot Connection
We’ve previously documented the connection between Qakbot and BlackBasta.
Prior to the FBI takedown of Qakbot infrastructure, other researchers identified a new malware called “Pikabot” that had similar distribution methods to Qakbot, also operated by TA577. We believe that Black Basta affiliates continue to utilise TA577’s Pikabot for initial access and deployment of post-exploitation frameworks such as Cobalt Strike and Metasploit, enabling utilisation of Black Basta ransomware within victim environments.
Pikabot Drops Meterpreter
We’ve tracked Pikabot C2 infrastructure and continue to validate our own detections against other security vendors and researchers. As part of this process, we identified an interesting post by Zscaler Labs and this is where our investigation begins:
https://twitter.com/Threatlabz/status/1717243502181208208
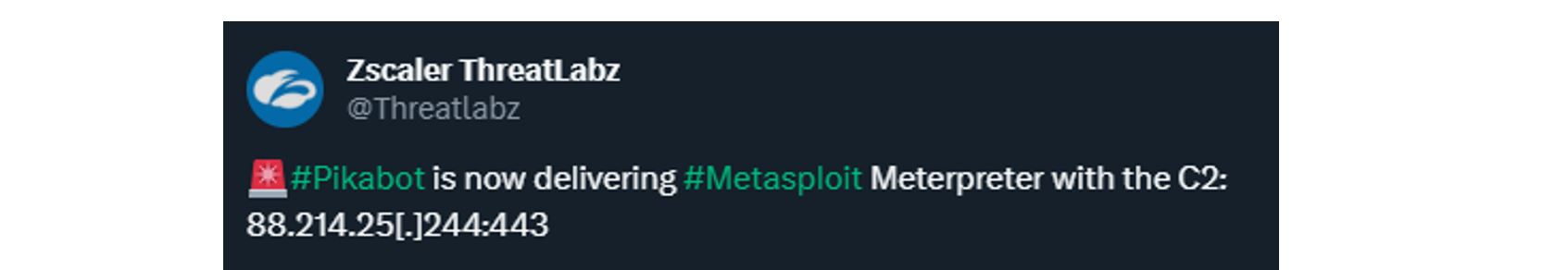
Figure 1. Zscaler tweet regarding Pikabot
Firstly, we know that Zscaler has attributed this IP address to a Meterpreter C2 being dropped by Pikabot. Results in Virus Total show lack of detections and association to Meterpreter indicating a unique fingerprint not yet identified by other security vendors and researchers. Additionally, the most recent domain draws interest.
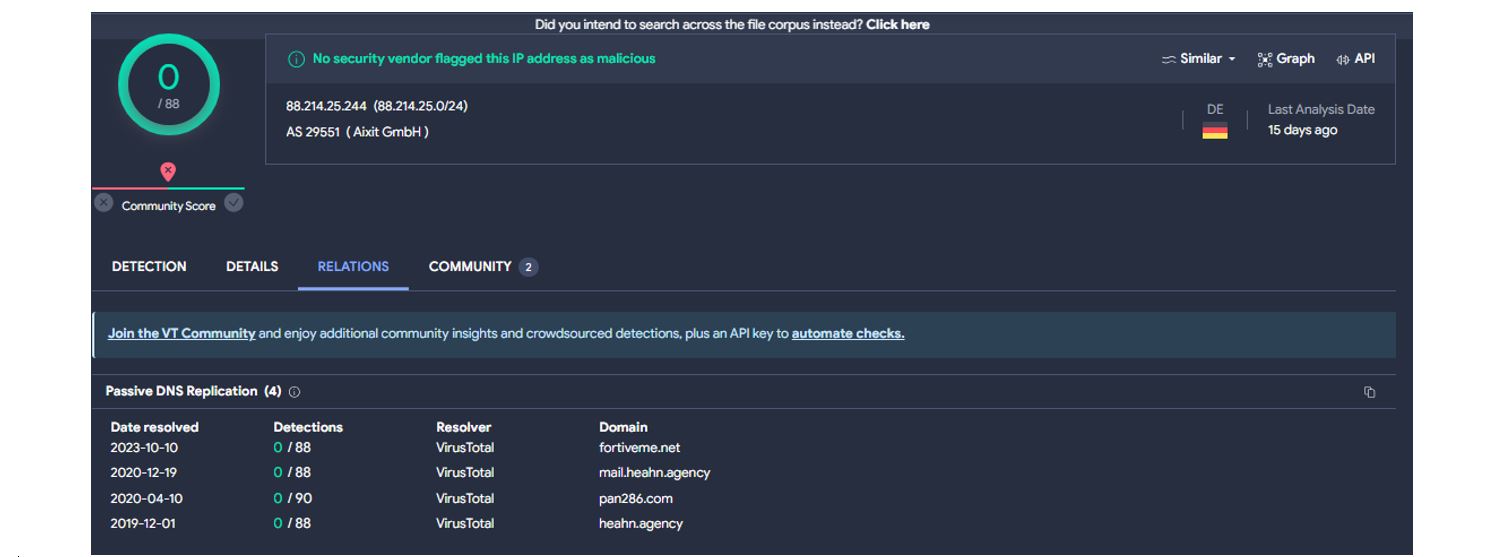
Figure 2. VT result for Meterpreter IP address listed by Zscaler
The IP address is running a small number of services on ports: 22, 80 and 8080.
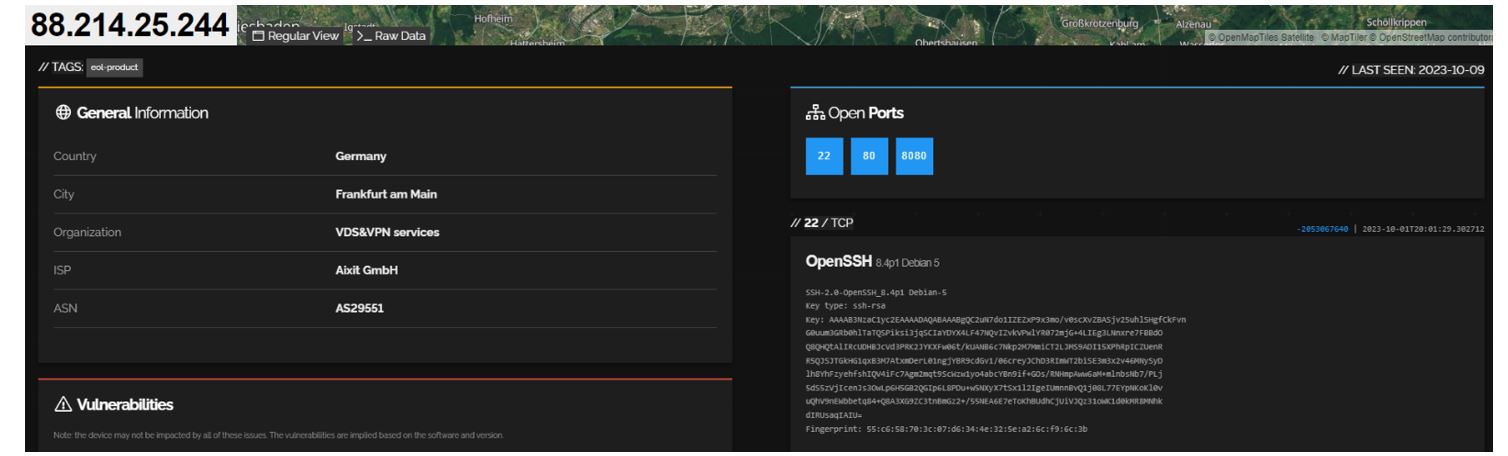
Figure 3. Shodan Result for Zscaler IP
By analysing this IP address and pivoting to uncover new infrastructure, we’ve made a number of observations below.
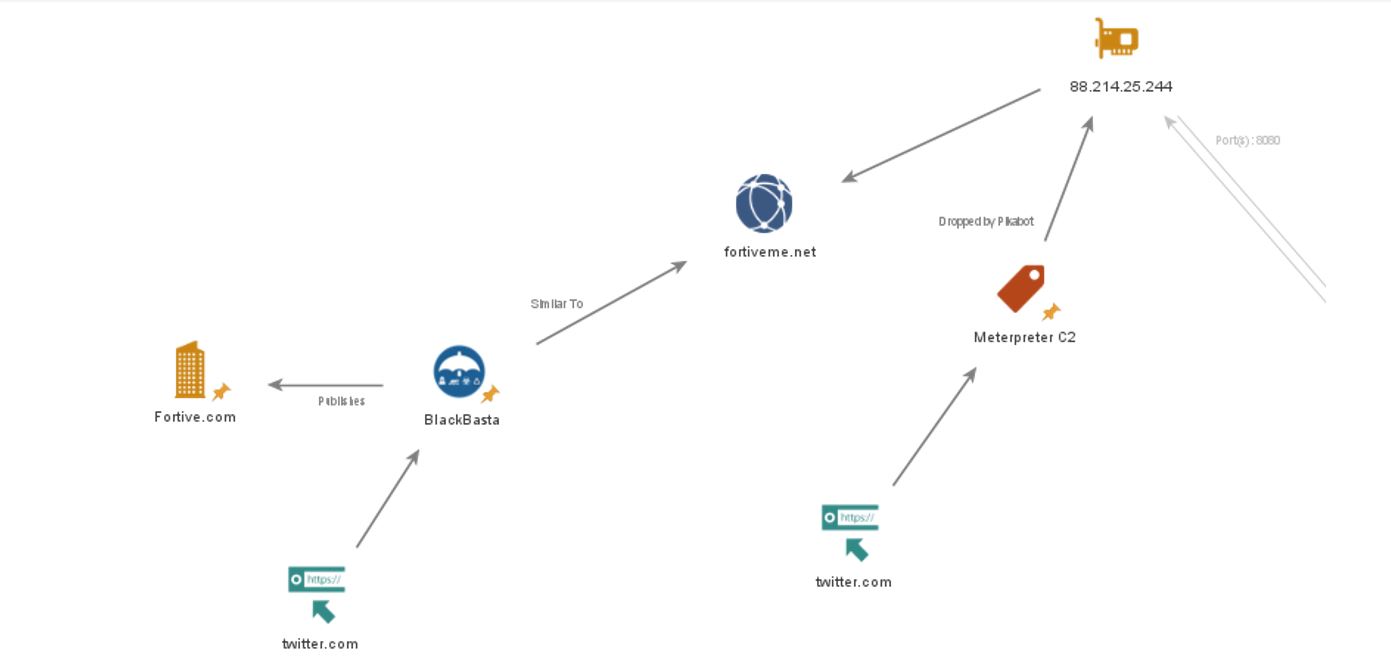
Figure 4. Maltego Graph for Zscaler IP
First Observation
The hostname: fortiveme[.]net.
This domain was created on 10th October 2023. 16 days later, on 25th October 2023, the company “Fortive” is posted as victim of Black Basta, appearing on their Data Leak Site. As announced by FalconFeeds.io on X:
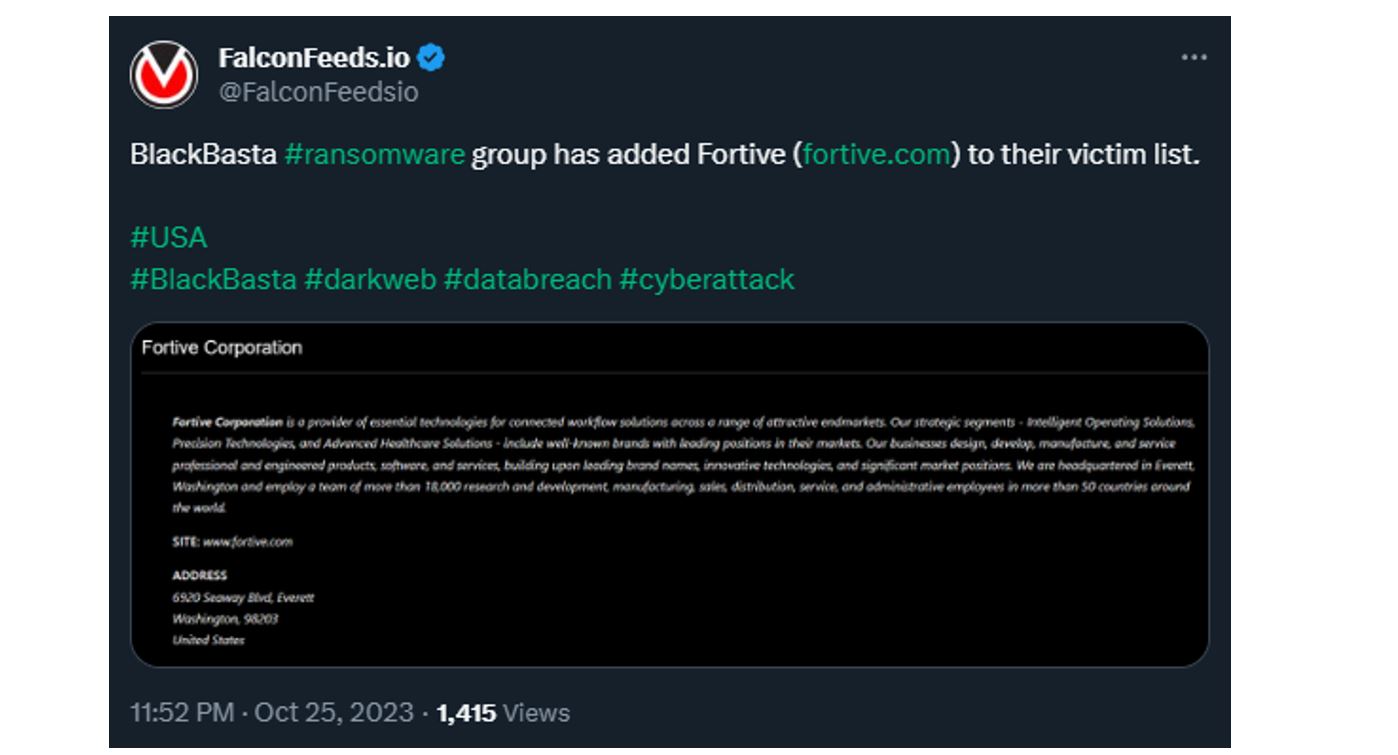
Figure 5. FalconFeeds.io posting Fortive on BlackBasta DLS
We don’t know if this infrastructure was used in an attack against Fortive, however, it is an interesting observation from which we could imply a connection to BlackBasta. We can hypothesise that the reason for using an impersonation domain is an attempt to evade detection. Additionally, knowing that Black Basta also has ties to Pikabot makes for an interesting connection.
Second Observation
The Meterpreter C2 Shares an SSH hash with a cluster of IP addresses previously linked with a Cl0P affiliate.
The SSH fingerprint used on this host has previously been tracked and linked to Cl0P. This SSH fingerprint was listed in our joint research into the group named Shadow Syndicate.
SSH Hash: ssh:"55:c6:58:70:3c:07:d6:34:4e:32:5e:a2:6c:f9:6c:3b"
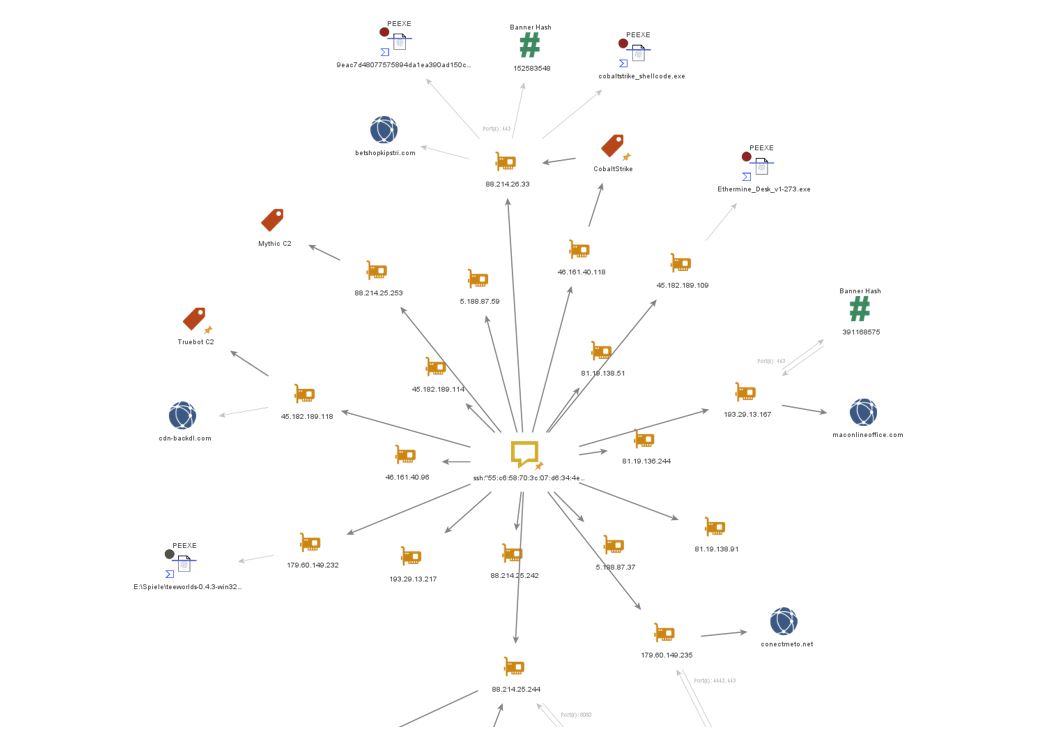
Figure 6. SSH Fingerprint shared with multiple IPs including initial Zscaler IP
We’ve previously linked this SSH to a cluster of hashes linked to Cl0P due to each cluster of IP addresses owning at least one Truebot C2 address. As we can observe from known Bridewell detections, a number of post-exploitation frameworks such as Cobalt Strike and Mythic are currently running with the same SSH hash, including a Truebot C2. A number of files and headers within this cluster make for good pivoting points for further research. However, we are able to link this Meterpreter C2 to within this SSH cluster.
We believe this indicates that a CL0P affiliate may also be working with Black Basta.
Third Observation
The Meterpreter C2 server hosts a number of unique fingerprints.
Revisiting the open ports, specifically port 8080, we can uncover additional servers that we can connect with this configuration of Meterpreter. Let’s look at the server response headers in Shodan
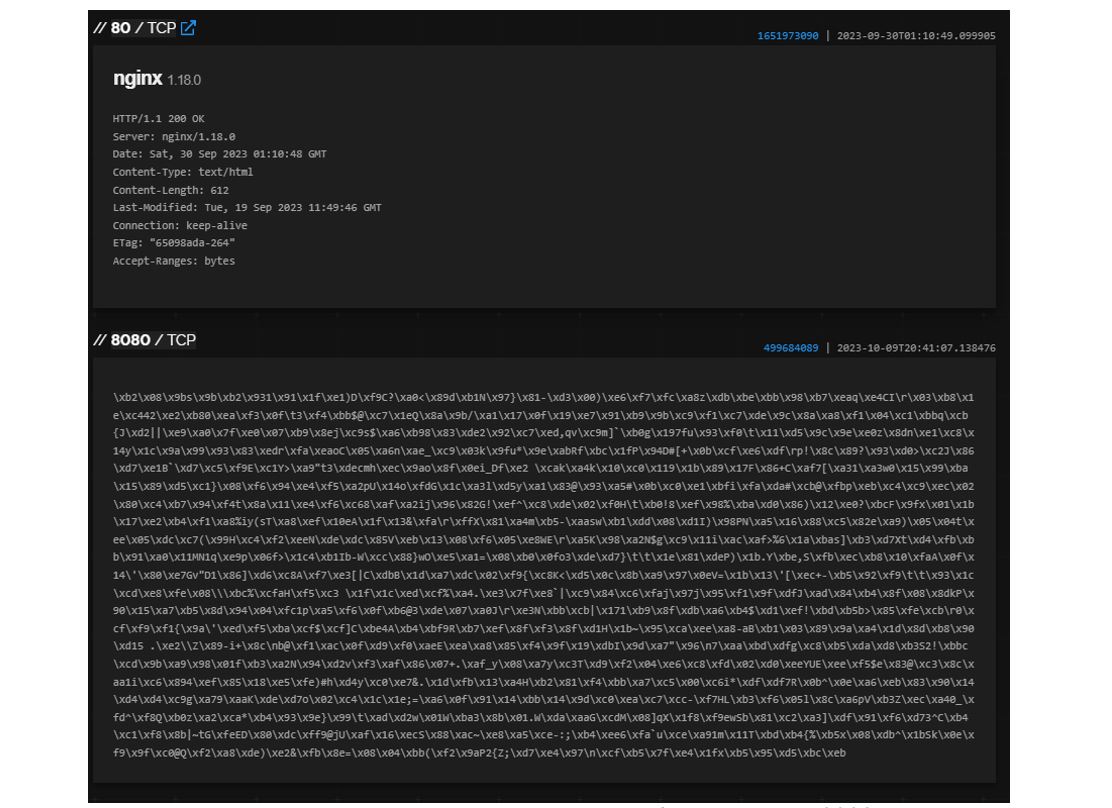
Figure 7. Meterpreter Response Header in Shodan on port 8080.
As you can see from the above screenshot, that banner is unusual on port 8080. This is a unique configuration to what we normally identify as a Meterpreter C2.
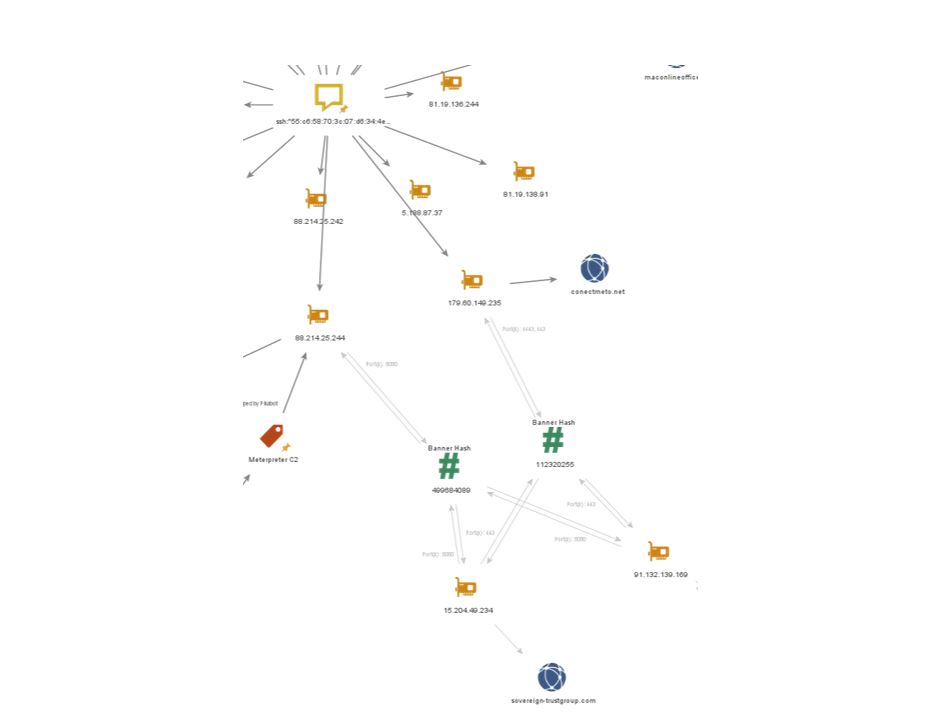
Figure 8. Maltego Graph showing relationship of IPs by Banner Hashes
Interestingly, a small cluster of four IP addresses appear to share two different banner hashes in Shodan, returning similar response headers on a number of ports (4443, 443, 8080).
By pivoting from our initial IP on port 8080 using hash: 499684089, we uncover two new IP addresses:
- 15.204.49[.]234
- 91.132.139[.]169
These IP addresses share the hash with our initial IP address, but utilising the hash: 112320255 on port 443 we can pivot back to our SSH hash to uncover IP:
- 179.60.149[.]235
Based on these findings, we can assess that these IP addresses are likely running a similar configuration of Meterpreter and are not yet tagged as such.
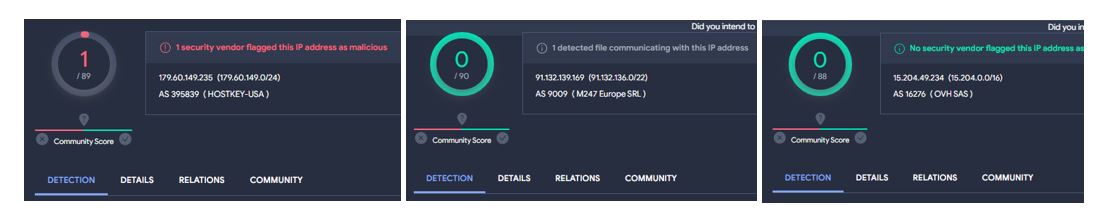
Figure 9. VT Results for newly identified Meterpreter C2s
Conclusion
As a result of Zscaler’s post regarding Pikabot dropping Meterpreter, we are able to make some assumptions about the threat groups behind some of this infrastructure as well as uncover new infrastructure that could be utilised in upcoming campaigns.
We continue to monitor and track activity relating to hosts associated with tools such as Meterpreter and groups such as Cl0p, Black Basta and Shadow Syndicate, as we continue to piece together their activity. By validating other research against our analytics, we are able to enhance our detection capabilities for Bridewell customers and share findings that may lead to further collaboration and research amongst the security community.

.jpg?sfvrsn=4c6fcb96_1)



