As part of ongoing research and monitoring activities into prominent ransomware groups, Bridewell Cyber Threat Intelligence (CTI) identified an exposed server hosted in Russia that appeared to host stolen data belonging to victims of the ransomware group BlackByte.
The server contained 38 subdirectories named after organisations across the globe. A number of these organisations had not been posted to the BlackByte data leak site indicating that they have either paid a ransom or are not yet aware of a possible compromise. We worked alongside Group-IB to retrieve the datasets and notify possible victims.
Who is BlackByte?
Figure 1. Black Byte Data Leak Site
Findings
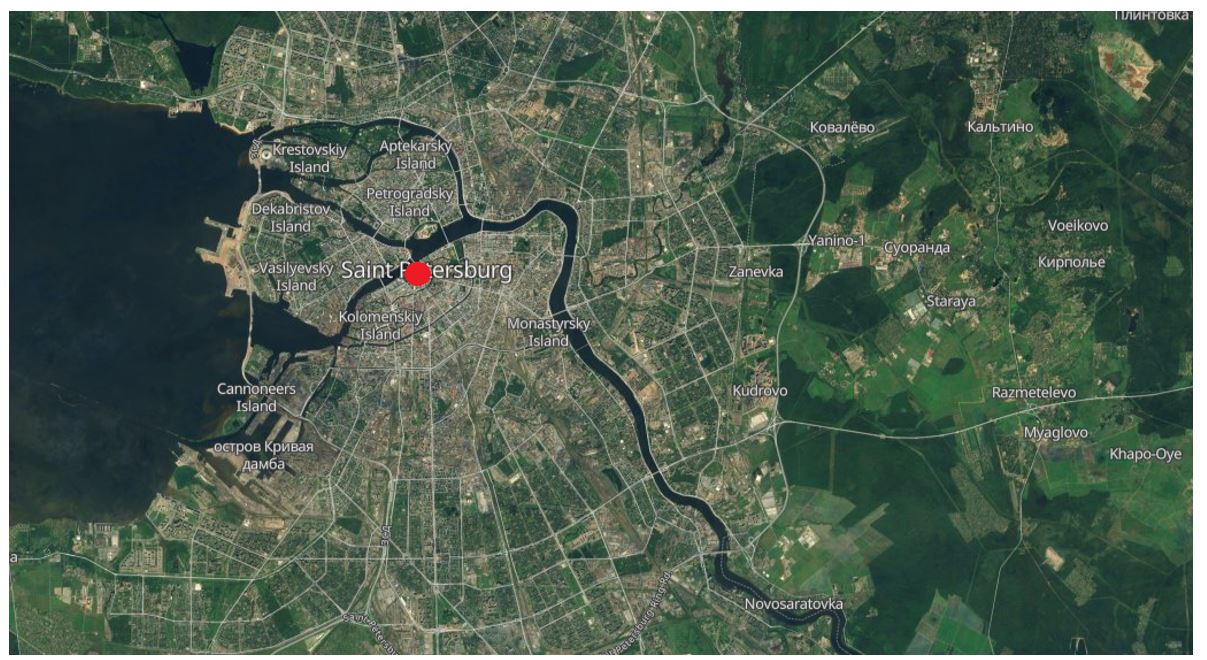
Figure 2. Location of exposed server
We assessed that this is likely an operational security failure by the owner/ operators of the server. The directory names were named after what appeared to be organisations around the globe. After analysing these directories, Bridewell and Group-IB were able to link a large portion of the organisations to the Data Leak Site for the ransomware group BlackByte. The open server contained 37 directories, with 19 named after organisations posted to the BlackByte data leak site between January and September 2023. 15 subdirectories were named after organisations not posted. The organisations are located in the US, Turkey, Germany and Denmark. It is currently assessed with moderate confidence that these organisations could be victims of the BlackByte ransomware group and either paid the ransom or are potentially unaware of any compromise.
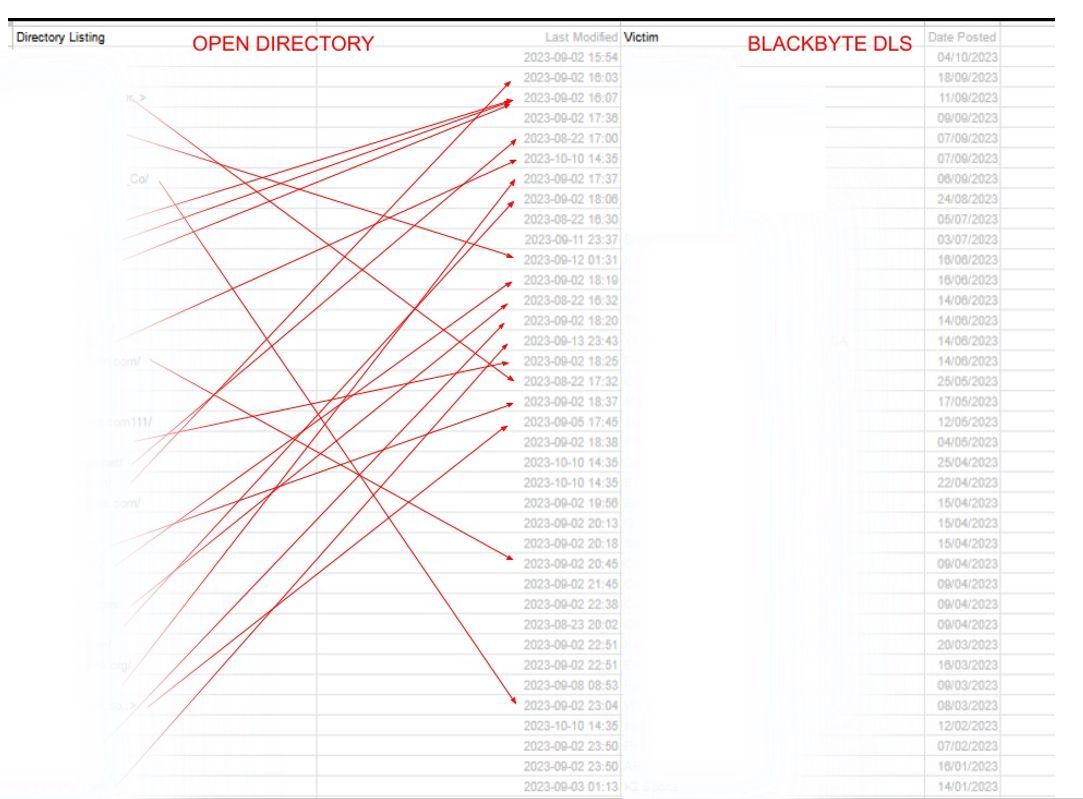
Figure 3. Open Directory mapping to BlackByte Data Leak Site.
Dataset
- Total number of files: 140,135.
Total Directory size: 1.2TB
Action Taken
We have withheld the IP address of the server hosting the open directory including additional potentially related infrastructure due to the sensitivities and confidential nature of the information. We do not wish to draw further attention to the dataset. Additional findings can be shared with other security professionals through trusted channels.
Current Status of BlackByte
.tmb-6_col_resi.jpg?sfvrsn=6c869a01_1)
.jpg?sfvrsn=4c6fcb96_1)



