Introducing you to the AWS Security Hub, Find out more!
If you use Amazon Web Services (AWS), then you may have seen that they recently announced the AWS Security Hub service.
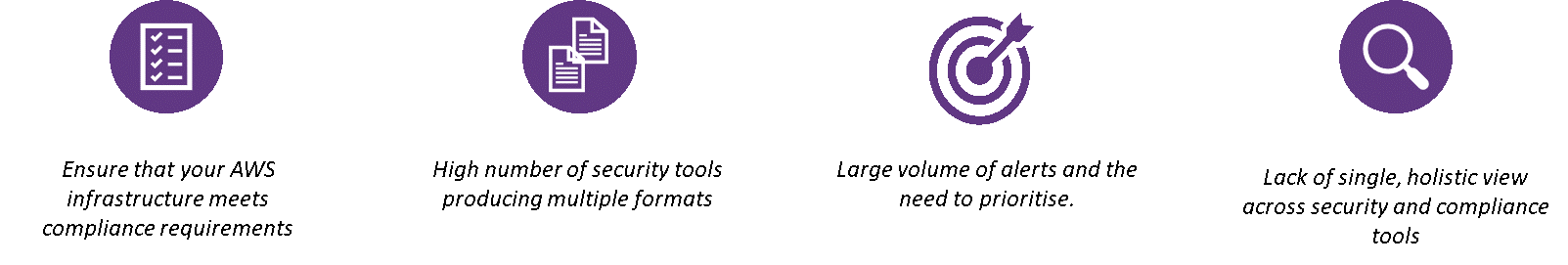
AWS have built a centralised security console that helps you monitor your AWS infrastructure from a single pane of glass, and leverage industry frameworks to assess the configuration of your infrastructure within AWS. The problem statement for the solution is displayed below:
Data Usage
AWS Security Hub ingests data from various native AWS services such as Macie, Guard Duty and Inspector, as well as integrating with offerings from the AWS ecosystem. This includes products from Splunk, Qualys and CrowdStrike.
High Visibility and Scalable Deployment
AWS Security Hub is available in both single and multi-account deployments and can be configured using cross account access, linking member accounts to a master account. Master accounts can monitor across all linked accounts, whilst individual member accounts can only view their own AWS Security Hub related information. This provides a highly scalable deployment capability, whilst still allowing localised management of a specific AWS account.
Compliance Checking
Compliance checks are made possible using pre-configured templates, 43 in total, including AWS Foundations from the CIS benchmarks. This enables development and operations teams to self-assess and remediate any findings. In addition, it adds a level of visibility and assurance to security teams, providing an autonomous method of addressing security within your AWS environment, in keeping with the DevOps mantra. This allows security teams to have a central consolidated view of all security related findings across the most complex of AWS multi account architectures.
Correlate and Automate Response
Lightweight correlation rules are also made available in the form of insights. For example, insights can be used to identify findings across the AWS estate such as:
- Active findings by created date, provider or severity
- Top S3 buckets by finding severity
- Top EC2 instances by severity
- Top AMIs by severity
- Top usernames by severity
- Top accounts by severity or type
AWS Security Hub also provides organisations with the ability to automate the detection and response loop, by providing the capability to take actions against discovered findings. This is facilitated using rules that can trigger actions within native AWS services such as CloudWatch, Lambda and Step Functions. This also provides the capability to leverage partner solutions such as Slack or AWS Aero.
Summary
If your organisation is utilising AWS, then we would encourage you to take advantage of this new capability. If you are unsure on how to progress improving your AWS environments, then Bridewell can support you on this journey. We are also certified by the National Cyber Security Centre (NCSC) and the Council for Registered Ethical Security Testers (CREST), and provide services across cyber security, information security and assurance (including implementing ISO standards), penetration testing and data privacy.
If you’d like to know more about AWS Security Hub or any of our new services, then please get in touch.
Author
Gavin Knapp
Cyber Defence Technical Lead



 Blogs
Blogs