Hearing the news of the accidental leak of sensitive information by the Police Service of Northern Ireland (PSNI) was concerning for obvious reasons. While the PSNI have understandably come into serious criticism for allowing this to happen and it would be easy to apportion blame to the individual responsible for the leak, many organisations could just as easily have leaked information in a similar way.
Lots of us have accidentally attached the wrong file to an email or included someone on an email trail that we didn’t intend to. This is seemingly what happened to the PSNI when a spreadsheet containing details of some 10,000 police officers and civilian staff was inadvertently published online. While this is an easy mistake to make, it is a risk that can be effectively mitigated through a combination of security awareness, processes and technical controls. Clearly, in the case of the PSNI, there should have been a process in place where content was reviewed before it was published on the internet.
In this instance, the data breach could have been avoided through some simple security controls which are included within Microsoft Office licenses – sensitivity labels. While this may make it seem like an obvious oversight, knowing to utilise this feature requires an organisation to have sufficient security awareness and mature processes.
All organisations need to look closely at their security controls to ensure that accidental data leaks do not take place. These controls include security awareness training, processes, procedures and technological controls. Given that the last week has seen major breaches affecting both the PSNI and Electoral Commission, which impacted over 40 million individuals, companies should also ensure these controls provide appropriate protection against data breaches.
Where Did the PSNI Go Wrong?
It’s all too easy to store large volumes of confidential data in a single spreadsheet or database, and it’s just as easy to give authorised users access to more data than they actually need for the task in hand. As this latest incident highlights, these practices allow hackers to access confidential information by simply getting their hands on a file. It’s worth noting that, based on what’s been reported in the media, that this wasn’t a data breach as no hacker or malicious software was involved. The incident is a result of someone accidentally publishing a file. Such a mistake can be avoided through implementing basic document control technologies, which most organisations already have access to but may not be aware of.
There are many document control technologies, including document management systems, which ensure that strict processes are followed. Authorised users ‘check out’ and ‘check in’ the data that they need, and there is additional oversight to sign off these activities.
For instance, this article has been written in Microsoft Word on an iPad Pro (though it could have been written on a PC or a Mac and the same protection would have been provided). At Bridewell, we make the most of a powerful capability of Microsoft Word which is present in all of the Office Suite including Excel, PowerPoint and Outlook. This capability, once configured, requires everyone who creates documents to choose a level of sensitivity before sharing it.
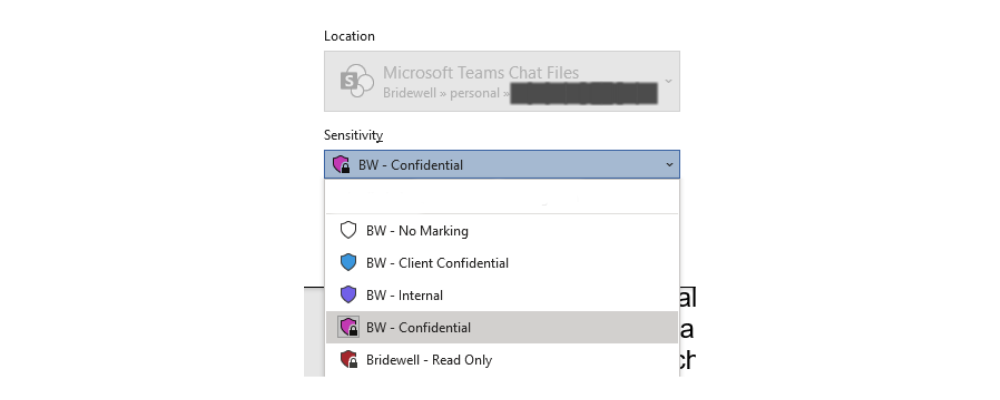
This document has been labelled “BW – Confidential” – the highest level of sensitivity. As such, it was automatically encrypted based on the template selected and a series of centrally defined controls were applied. This template restricts which group(s) of users can read, edit, print and forward the document. Many other controls are available too.
The document will remain encrypted all of the time, other than when it’s displayed on the screen of a user who has been authorised to access it (based on their Active Directory Group membership). If it’s accidentally published on the Internet, attached to an email or stored on a laptop (which is subsequently stolen), it will remain encrypted and therefore safe from prying eyes.
The magic of the system is that almost everything happens automatically behind the scenes. The only sign to the users that the content is encrypted is where the author selects the appropriate level of sensitivity from a menu when creating the document. A notification on screen reflects this for authorised users who subsequently access it. The encryption keys are automatically stored centrally, and the document access policies are managed centrally too.
Additional controls include the ability to ensure that only computers that are managed by the organisation can access the unencrypted data and offline use can be allowed for a chosen period of time. For the most sensitive data, the organisation may choose to require the device to be online in order to access the data. The benefit being that access can be removed immediately if a user reports that their sign in credentials have been compromised or if they have left the organisation.
Balancing Security and Agility
Given the ongoing tensions within Northern Ireland and the fact that dissident Republicans are known to be in possession of the list, such a data leak has caused serious consequences to those whose data has been made available. The incident has highlighted how every organisation must take the security of their data seriously, and review whether they have the right security controls, processes and capabilities in place to avoid falling victim to these types of accidental data leak.
Organisations should be aware that there are many security features available to them that they may not be using to their full extent. However, to understand what they are and how they can be most effectively implemented, they must recognise the importance of achieving appropriate security awareness and processes.
Getting the right balance of security and privacy controls while ensuring that the organisation remains as agile as possible, requires expertise and that is not always available in-house. Not having the privacy controls in place at all can be highly dangerous as the case of the PSNI has shown.
.tmb-6_col_resi.jpg?sfvrsn=c42886e0_1)




