Last October, the ISO published ISO 27001:2022. This latest version of the standard – which hadn’t been updated since ISO 27001:2013 - brought about several major changes. The majority of these changes were focused on the Annex A controls, alongside several smaller changes to clauses 4-10. In this blog, we will see how these changes have impacted organisations and share what organisations need to know when it comes to ISO 27001 certification or recertification.
In a previous blog, we discussed the main changes in the 2022 version of ISO 27001, looking at how the mandatory clauses have changed. For organisations’ with mature Information Security Management Systems (ISMS) that effectively implement the 2013 standard, these changes don’t seem to have had too much of an impact.
Most of the clauses remain fairly similar, and those that have changed have not been drastic enough to warrant a complete re-write of the ISMS documentation. At most, it seems that a few small amendments are needed to factor in updated wording or new requirements, with the biggest and most obvious change being the Statement of Applicability.
Perhaps the biggest change with the recent iteration of ISO 27001 comes from a completely rewritten Annex A, and supporting ISO 27002 guidance, which has exposed poor implementations of the 2013 version. If you’d like to learn more about the key changes for organisations transitioning from the 2013 version of the standard to the 2022, register to watch our webinar on demand: ISO 27001 Changes – What We’ve Learned from the 2022 Update.
What Has Changed with Annex A?
The original 14 control clauses have been reduced to four control “themes”. In addition to this, the 35 previous control categories have been removed completely. Annex A has also seen a decrease in the number of controls listed. 55 of the previous controls have been merged, one control has been split and then merged with other controls and 11 new controls have been introduced, resulting in a reduction of the 114 original controls to 93.
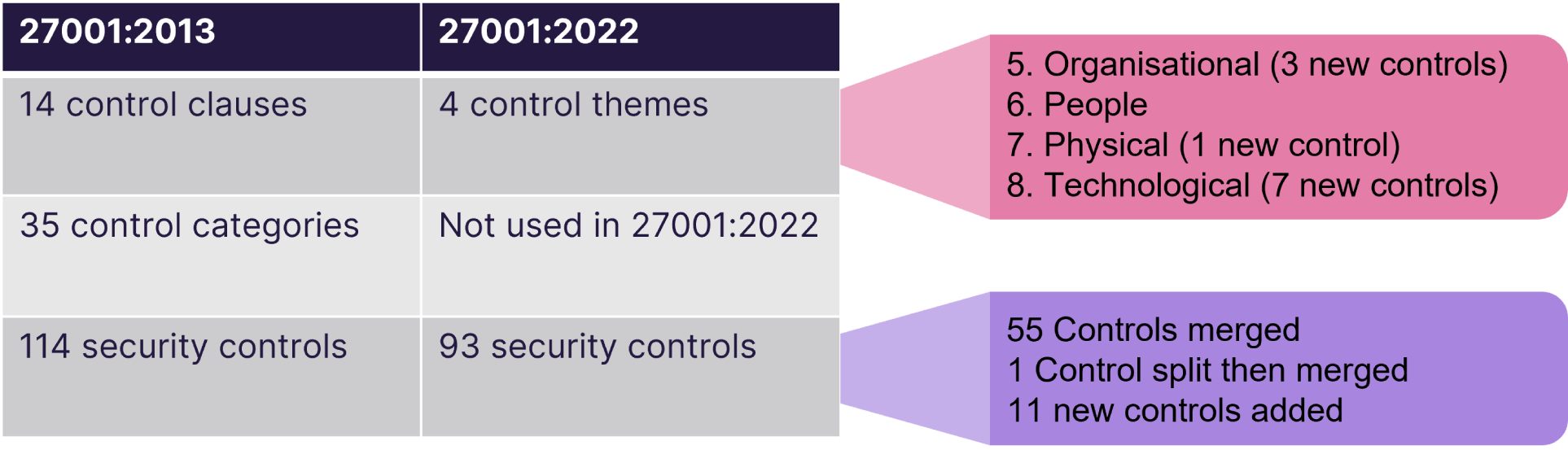
On the surface, it seems that Annex A should be easier to manage with these changes. However, this has come with increased complexity around planning and executing the dreaded internal audit.
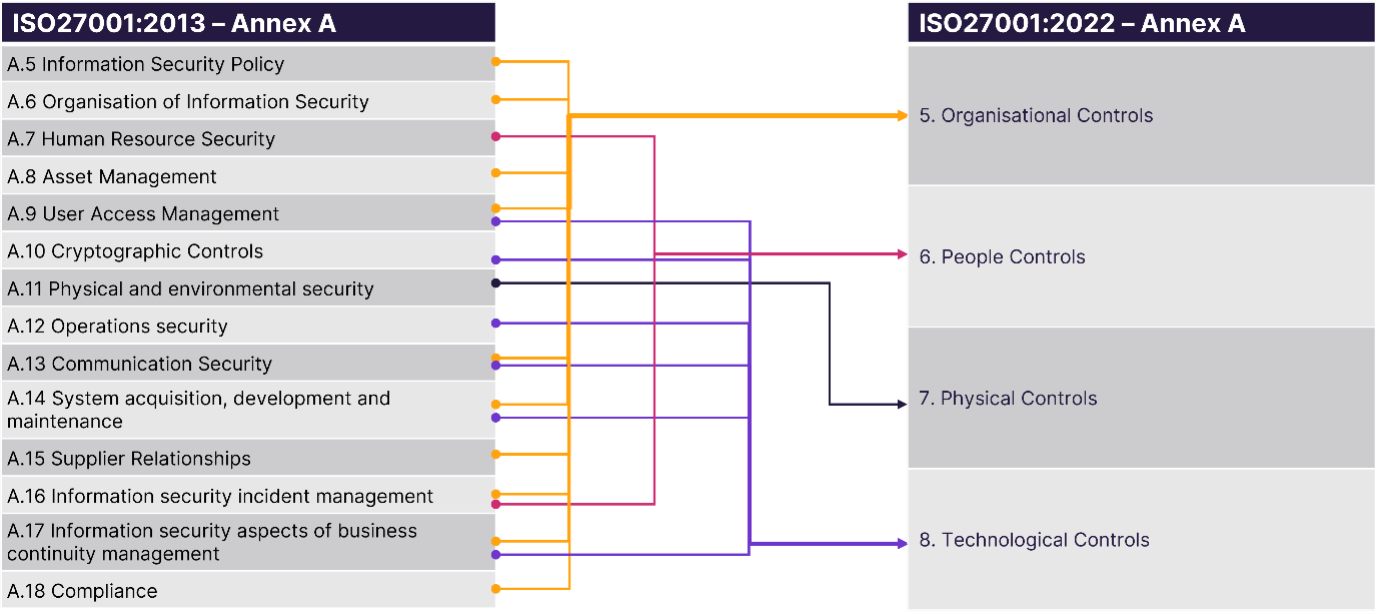
By comparison, 27001:2013 made it easy with each control bundled in with similar controls and all contained within their own neatly packaged category. This made it easy to plan the audit and select the appropriate stakeholders. 27001:2022 has made the audit process slightly more complex with most of the original categories being split between the new control themes. There are also no sub-categories, meaning that you will now need to select controls to audit individually or risk having hours-long meetings for each of the themes instead.
For example, if you wanted to audit Security Incident Response (A.16) you will now need to audit five controls from the ‘Organisational Control’ theme and one from the ‘People Control’ theme.
The same goes for some of the technical control categories, such as User Access Management (A.9), Operations security (A.12), Communication Security (A.13), System acquisition, development and maintenance (A.14) and Information Security Aspects of Business Continuity Management (A.17), which have all been split across the ‘Organisational’ and ‘Technological Control’ themes.
One way that we’ve tackled this at Bridewell is by keeping the old 2013 control clauses mapped to the new 2022 controls. Instead of having four large and varied sessions that become difficult to plan, we can continue to operate as before with 14 smaller, more distinct sessions more akin to the 2013 control categories.
You can find a visual representation of the new mappings below:
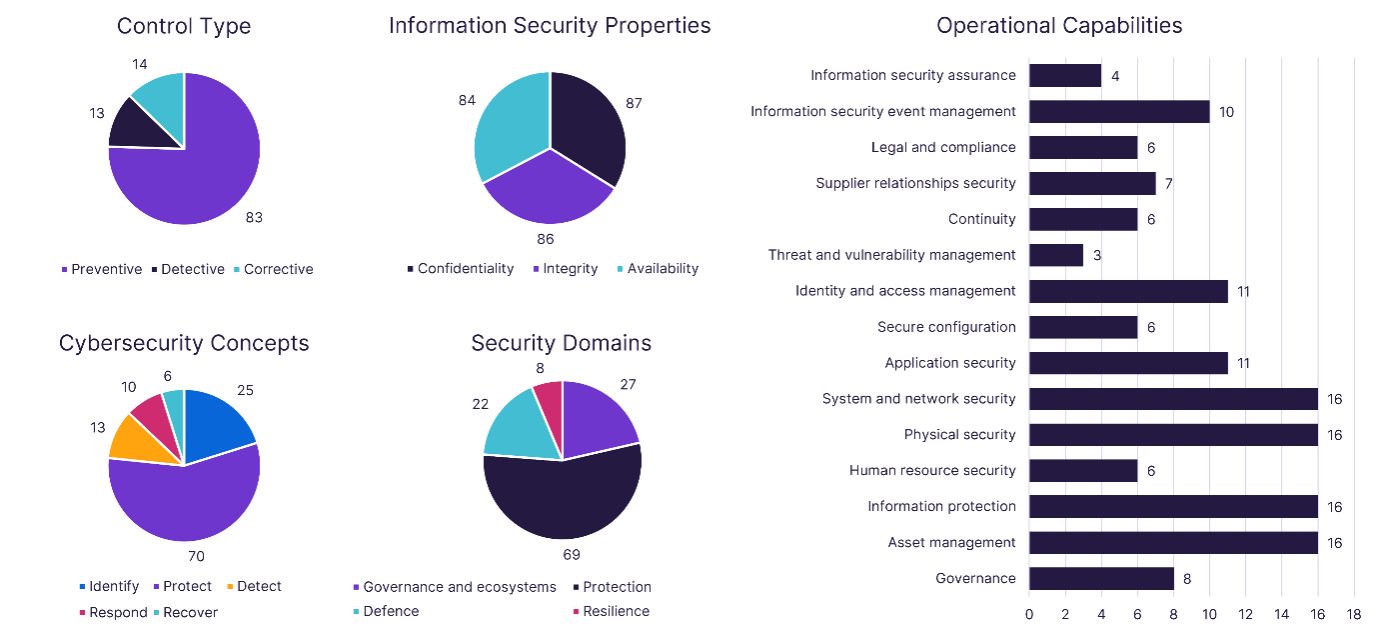
One of the most beneficial changes that has been introduced in ISO 27002 however is the attributes. Each control is given one or more attribute from the following categories:
- Control type
- Information Security Properties
- Cybersecurity Concepts (aligned with NIST CSF)
- Security Domains
- Operational capabilities
With the right analysis, this data can provide a whole new insight into the security capabilities of the organisation.
Additionally, this tagging of cyber security concepts has made cross framework mapping a somewhat more appealing task. (You can learn more about this topic in our webinar).
New Annex A Controls
Along with the changes to the current controls, there has been an addition of 11 new controls. It seems that the new controls have been devised to combat threats that have emerged, or increased, in the 10 years since the last iteration. For example, the introduction of cloud services requirements and improvements in data management and monitoring processes.
Here’s a breakdown of what you can expect when implementing these new controls:
5.7 Threat Intelligence
Information relating to information security threats shall be collected and analysed to produce threat intelligence.
For most organisations this control is relatively simple to implement since you’re already doing some of this through your risk and vulnerability management processes. However, this control also takes into account threats at the strategic, operational and tactical levels to produce a more thorough assessment of the changing threat landscape.
5.23 Information security for use of cloud services
Processes for acquisition, use, management and exit from cloud services shall be established in accordance with the organization’s information security requirements.
This control expands on some of the existing controls already in place for system acquisition, development and maintenance and supplier management to cover the use of cloud services much more explicitly.
Most organisations who have transitioned to the cloud will have already considered additional requirements but ensuring that these requirements are clearly documented remains a pain point for some.
5.30 ICT readiness for business continuity
ICT readiness shall be planned, implemented, maintained and tested based on business continuity objectives and ICT continuity requirements.
Much like the old Annex A.17 controls, this control assumes that an organisation already has a business continuity programme in place. However, this control specifically addresses the response and recovery of ICT assets to ensure the availability of the information and associated assets.
7.4 Physical security monitoring
Premises shall be continuously monitored for unauthorized physical access.
Previously showing that you had CCTV, pass card systems and physical barriers in place might have been enough to satisfy the requirements of A.11, however, that’s where many organisations stop. This control requires that you actively monitor the physical environment to identify unauthorised access, rather than just assuming that the controls in place are working.
8.9 Configuration management
Configurations, including security configurations, of hardware, software, services and networks shall be established, documented, implemented, monitored and reviewed.
This is another control that previously might have been managed, at least in part, through the requirements of system acquisition, development and maintenance. This control requires that you ensure consistency in configuration by formally documenting, monitoring and reviewing accepted configurations.
8.10 Information deletion
Information stored in information systems, devices or in any other storage media shall be deleted when no longer required.
8.11 Data masking
Data masking shall be used in accordance with the organization’s topic-specific policy on access control and other related topic-specific policies, and business requirements, taking applicable legislation into consideration.
8.12 Data leakage prevention
Data leakage prevention measures shall be applied to systems, networks and any other devices that process, store or transmit sensitive information.
These three controls all support the strengthening of the protection and privacy of data, ensuring that data is protected at rest and in transit, masked where necessary and deleted when no longer needed. Effectively implementing these controls will reduce your exposure and make it harder for data to be stolen.
8.16 Monitoring activities
Networks, systems and applications shall be monitored for anomalous behaviour and appropriate actions taken to evaluate potential information security incidents.
This new control expands on the existing capabilities that should be in place if you have implemented A.12.4 effectively with the introduction of monitoring for networks, systems, and applications to identify unusual activity and initiate incident response procedures where necessary.
8.23 Web filtering
Access to external websites shall be managed to reduce exposure to malicious content.
This control will most likely be seen by many as a welcome addition to the standard, web filtering that allows you to control who accesses what and to reduce the likelihood of users accidentally browsing to malicious websites.
8.28 Secure coding
Secure coding principles shall be applied to software development.
This control requires that you establish secure coding principles, alongside existing secure architecture and engineering principles, and apply them to your software development processes to ensure that vulnerabilities are not introduced through poor practice.





