This blog is the first in a series covering Microsoft Threat Protection (MTP). It provides a basic introduction to MTP without detailing all of the MTP services. Subsequent blogs will provide a more in-depth overview of the MTP services and how they all fit together.
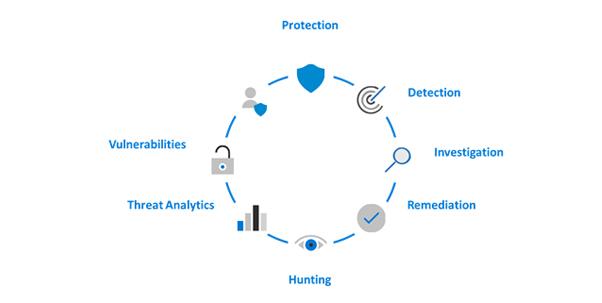
Figure 1 – Microsoft Threat Protection
What is Microsoft Threat Protection?
In recent years Microsoft has become a big player in the enterprise security space. MTP is their new security capability that leverages several existing security services, consolidating them into a central console called the Microsoft 365 security center. It can be used by IT, security and compliance professionals and is an important addition to security operations. MTP helps protect, detect and respond to a wide range of threats targeting the business.
Figure 2 – Microsoft 365 Security Center
A key feature of MTP is its ability to aggregate and correlate alerts from across different Microsoft services to generate high fidelity actionable incidents. Previously there was a lot of effort involved in traversing the various security services individually, so this is a massive improvement. Another key feature is the introduction of self-healing using automation that can detect threats and apply automated actions to prevent further impact to the business.
In addition to the inbuilt automation there are numerous integrations with Microsoft Flow and Azure Logic Apps that can be used to build remediation flows. These include triggering an antivirus scan on a device based off alerts triggered by other Microsoft security products.
With regard to impossible travel (a user appearing to be in two different geographical locations in a short time frame), alerts can be used to trigger an authorisation flow enabling managers to confirm whether the affected team member is on holiday or on a legitimate business trip. This reduces the time and effort required by security professionals to effectively triage and respond to alerts.
What’s included in Microsoft Threat Protection?
MTP is comprised of the following technologies:
- Microsoft Defender Advanced Threat Protection (ATP)
A cloud-based endpoint detection and response (EDR) product. It provides increased endpoint protection through attack surface reduction mitigations, application controls and network protection. Advanced hunting, network isolation and real-time response across enrolled devices is also possible.
- Office 365 Advanced Threat Protection (ATP)
Cloud based email and Office 365 productivity suite protection that can guard against phishing, SPAM, malicious attachments and links. Has rich reporting and data exploration features and provides an attack simulation capability that can be used to test users and detection capabilities.
- Azure Advanced Threat Protection (ATP)
A cloud-based monitoring solution for both Azure, on-premises or hybrid Active Directories. It uses behavioral analytics and built-in detections to discover attacks across the cyber kill chain, including user enumeration, pass the hash, kerberoasting and DC shadow attacks.
Azure Advanced Threat Protection also includes Azure AD Identity Protection which includes the ability to investigate user and sign-in risk, and to automate responses to potential and actual identity compromises. Advanced threat protection is also present within the Azure Security Center and is used to protect resources within the cloud.
- Microsoft Cloud App Security (MCAS)
A cloud access security broker (CASB) that helps discover shadow IT, can assess the compliance posture of cloud applications, enforce policies that protect information and help to protect against threats such as malware.
[4] https://docs.microsoft.com/en-us/defender-cloud-apps/what-is-defender-for-cloud-apps
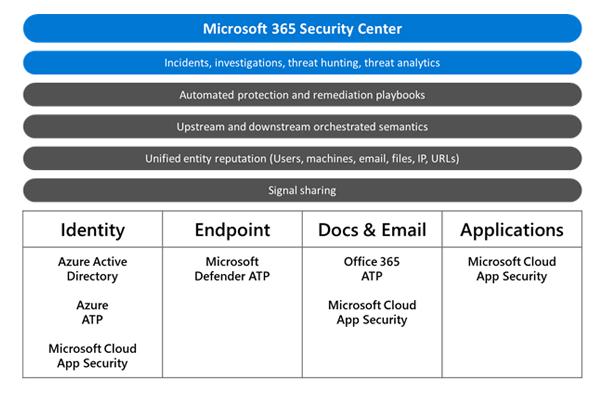
Figure 3 – MTP sub products
As mentioned above, MTP comes into play before, during and in post-breach scenarios. It can significantly reduce the time that attacks go undetected in your environment, accelerating detection and response efforts which ultimately reduces the risk posed to the business.
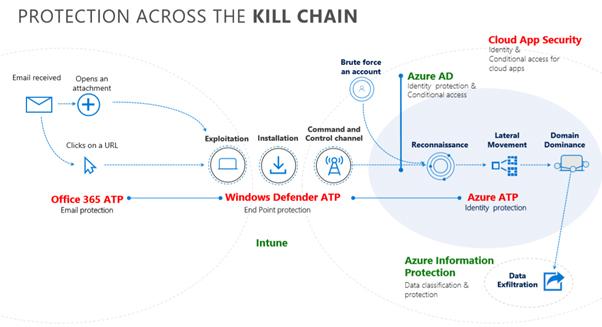
Figure 4 – MTP Protection across the cyber kill chain
Why do I need Microsoft Threat Protection?
Attacks against organisations are increasing over time whilst the barrier to entry to perform these attacks is rapidly diminishing. Microsoft state that “Cyberattacks will likely cost $6 trillion worldwide by 2021.”
Cloud services have accelerated the ability for business to exploit opportunities across the globe but conversely the cloud can accelerate the compromise of key assets and information without appropriate investment in security. Modern ways of working have extended the corporate network into people’s homes and other untrusted locations. The corporate perimeter no longer ends at the firewall and identity has now become the new perimeter.
With that in mind it is essential you maintain visibility of identities across on premise and cloud environments. MTP provides this visibility and reduces the barrier to entry for a security professional to effectively perform security monitoring, incident response and management reporting relating to the threats and attacks against your business.
This all sounds good but what do I need to use Microsoft Threat Protection?
Microsoft licensing can be a pain to navigate. However, MTP is included within the following single license subscriptions:
- Microsoft 365 E5 or A5
- Microsoft 365 E5 Security or A5 Security
Alternatively, it can be acquired by bundling existing Office 365, Enterprise Security and Mobility (EMS) and Windows subscriptions together. As long the complete bundle includes the following licenses:
- Office 365 E5 or A5
- Enterprise Mobility + Security (EMS) E5 or A5
- Windows E5 or A5





