What is MISP
MISP is an open source threat intelligence and sharing platform primarily used for collecting, collaborating, storing and widely distributing security threat intel and indicators of compromise (IOCs). These indicators and intel include everything from file hashes, malicious website URL’s, intel of specific security groups, IP Addresses, domain names and much, much more. Users of MISP instances benefit from a vast array of security data sets which can be heavily utilised throughout security research, threat analysis and operate seamlessly as a centralised hub for security and fraud threat intel.
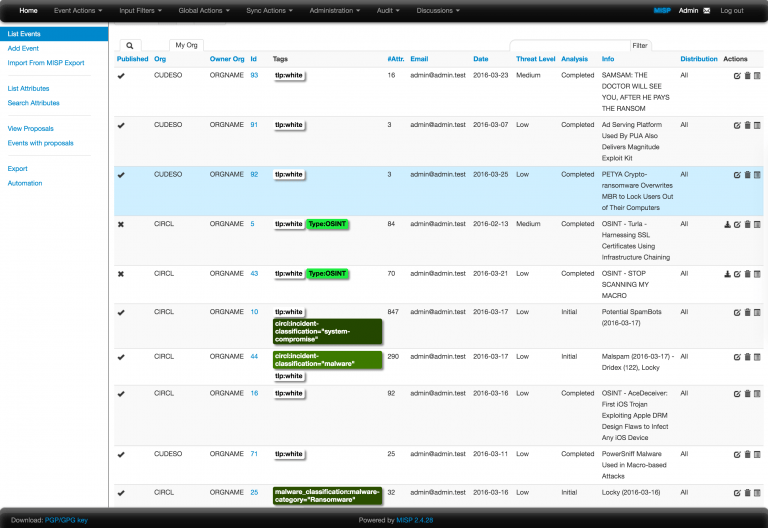
MISP Structure
- Event: An event is a singular unique threat entry created by an organisation which contains information such as the threats, last sighting, publish date, owner organisation, threat level and all associated IOCs to the threat in question.
- Feed: Once an Event has been created a user must assign the Event to a specific feed. A feed works as a centralised independent list of Events which may belong to a specific organisation, contain only a specific category of Events or any number of other grouping specifications
- Community: A community is the name given to organisations supporting MISP which form an organised collective
- Subscribers: This is essentially the user base which have selectively chosen to receive all threat pertaining to a specific feed
Data Sharing
The MISP platform is a platform which is being utilised by over 6000 independent organisations in varying industries and domains each with proprietary, public or community drive threat feeds. Once the instance has been erected, organisations are able to add Events to their own Feeds while specifying the Event’s level of explosive. These levels include:
- Viewable by your organisation only
- Viewable only within your community
- Viewable by interconnected communities
- Viewable by all communities
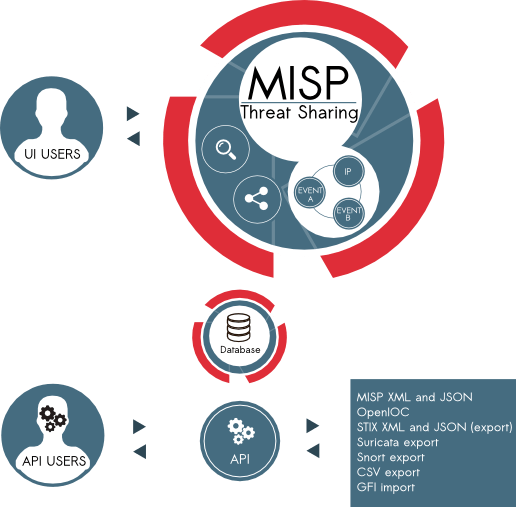
How it is accessed
- API: Users can programmatically make pull and push requests from within code to send and receive threat intel
- Web UI: MISP comes with its own dedicated Web hosted UI platform allowing users to login and interact with all data sets
How does it work
MISP is made up entirely of trusted independent users and or organisational threat submissions which are both ingested from and added to by this respective userbase. Upon joining communities, organisations can subscribe to their underlying feeds which may pertain directly to threats found only in their respective industries i.e. finance and politics as well as only receive specific categoric IOC’s of interest. Once subscribed to these feed’s organisations can begin to ingest API pull request calls, importing them into SIEM platforms, incorporating them into detection rules, adding them to firewall blacklists and much more. On the other hand, organisations are also able to contribute to the community, adding their own feeds and events which can be community shared amongst fellow community subscribers.




