A series of misconfigurations and overly trusted behaviours in the Azure Portal allowed attackers to craft malicious links that, when clicked by a user, executed unauthorised Azure Management API commands on their behalf — potentially leading to full tenant compromise.
Both vulnerabilities discussed in this post have since been responsibly disclosed and patched by the Microsoft Security Response Center (MSRC). This blog also contains a video demonstrating this vulnerability.
Background: ARM Template Deployments in Azure
Azure allows users to deploy resources via ARM (Azure Resource Manager) templates using shareable links. These links are commonly used by infrastructure teams to standardise deployments or distribute packaged solutions.
A typical deployment link looks like this:
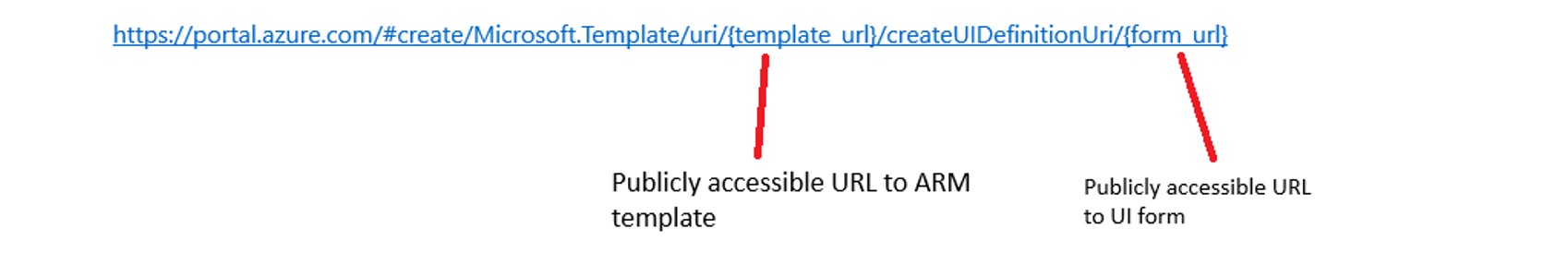
https://portal.azure.com/#create/Microsoft.Template/uri/{template_url}
When visited, the Azure Portal loads the specified ARM template from the provided URL.
However, a more powerful and undocumented variation of this URL exists:
This format is undocumented but allows the use of a custom UI definition to augment the deployment experience. These UI forms are commonly used in Azure Managed Applications to provide rich user interfaces during resource provisioning.
Understanding UI Definitions
UI Definitions enable the creation of customized deployment experiences in the Azure Portal. They support enhanced input elements like sliders, dropdowns — and more critically — the Microsoft.Solutions.ArmApiControl element.
ArmApiControl UI element
The core of this vulnerability lies in the ArmApiControl UI element. This control can issue GET and POST requests to the Azure Management API on behalf of the currently logged-in user. Importantly, these API calls are automatically triggered when the form loads — without any further user interaction.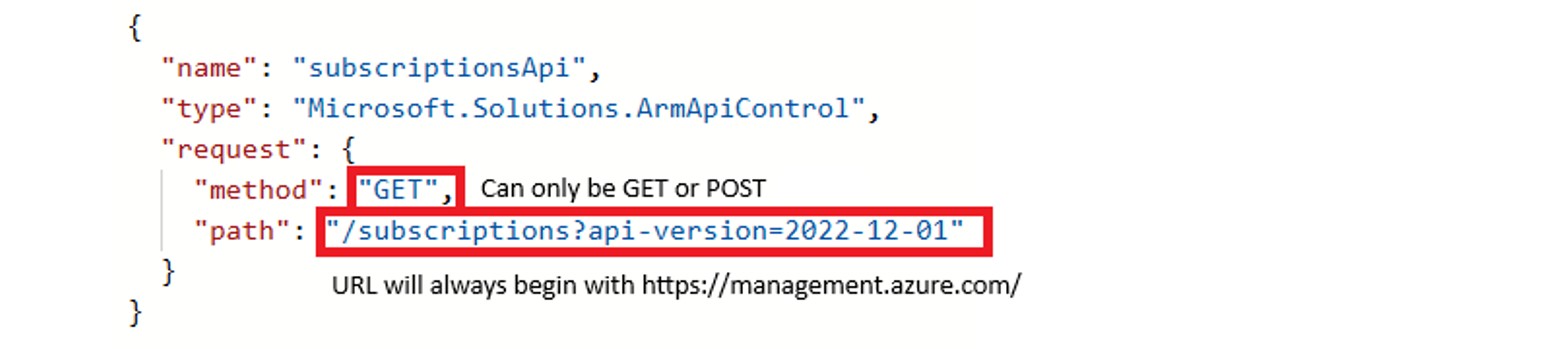
When the malicious UI form is loaded, Azure Portal bundles the API requests using its internal batch mechanism. Instead of calling the API directly from the browser, the form issues a POST request to a special Azure Batch endpoint, which wraps the intended API call inside the request body.
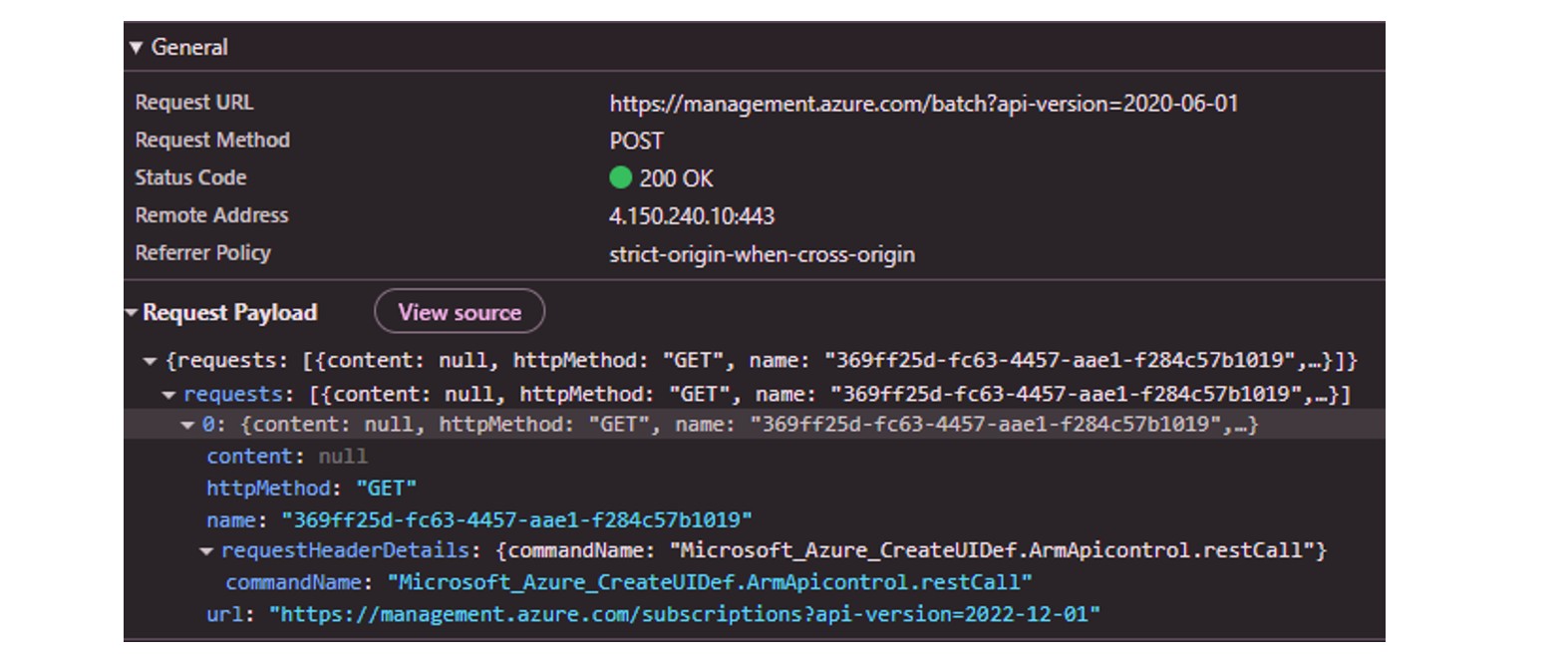
Limitations of ArmApiControl
While powerful, ArmApiControl is limited to only GET and POST methods. Many sensitive or privileged operations in Azure — such as resource creation, role assignments, or policy modifications — require the PUT or PATCH method, rendering direct privilege escalation impossible… at first glance.
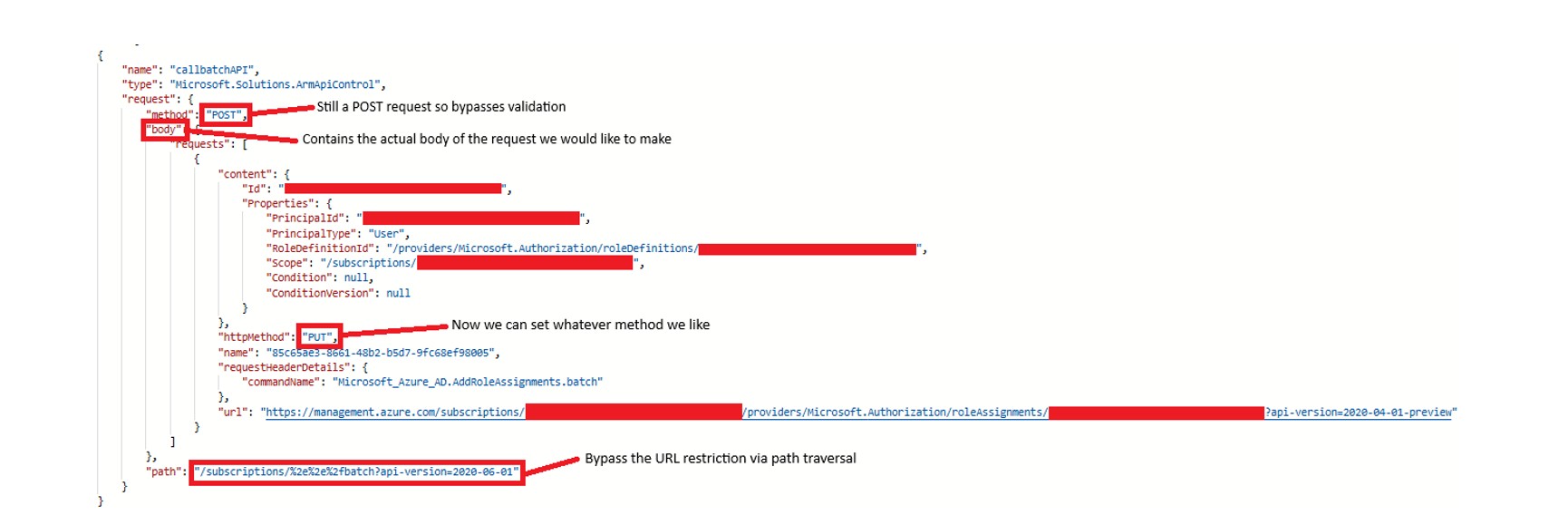
Bypassing HTTP Method Restrictions via Path Traversal
To escalate further, the attacker’s goal would be persistence — such as creating a managed identity or resource with privileged access.
While POST can be used to retrieve secrets (like keys for Azure Storage or App Services) and exfiltrate them via Kusto (KQL) queries calling out to external endpoints, true persistence typically requires PUT.
This led to an idea: since the Azure Portal batches API calls by posting to /batch, what happens if we target that directly?
Initial attempts included:
- Posting directly to /batch?api-version=2020-06-01
- Posting to /subscriptions/../batch
These were blocked with an error stating that the URI must start with /subscriptions, /providers, etc. However, a final attempt using double-encoded path traversal proved successful:
/subscriptions/%2e%2e%2fbatch?api-version=2020-06-01
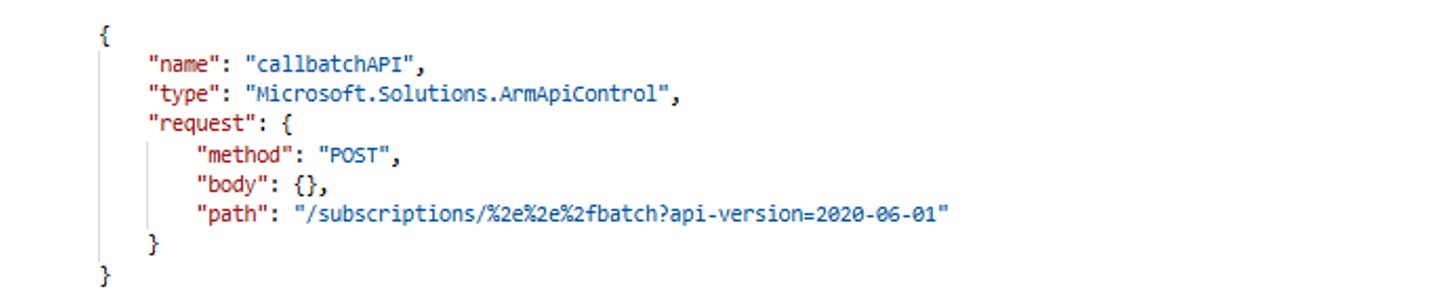
The sequence %2e%2e%2f is a double-encoded version of ../, commonly used to bypass path normalization filters.
This time, the request was processed — and returned an error indicating a malformed body, not a forbidden endpoint, which confirmed that the request was accepted and evaluated by the backend.
A final test confirmed functionality: a crafted batch payload using this bypass successfully performed a role assignment — achieving full privilege escalation
Impact
This vulnerability allowed an attacker to:
- Craft a single malicious Azure Portal link
- Have a legitimate user unknowingly execute privileged API calls
- Create or modify privileged resources (via method bypass)
- Achieve persistence within an Azure tenant
- Exfiltrate sensitive keys or secrets
This chain required no user interaction beyond visiting a link — no clicks, no button presses.
Disclosure and Resolution
This vulnerability was responsibly disclosed to the Microsoft Security Response Center (MSRC) and has since been fully patched. Microsoft has remediated both the abuse of the ArmApiControl element and the batch API path traversal technique.
Conclusion
This finding highlights the complexity and potential risk of overly flexible components like ArmApiControl, especially when security boundaries rely heavily on client-side enforcement and obscurity.
Security researchers and developers alike should remain wary of undocumented or under-documented features — particularly in privileged environments such as cloud management portals.
Watch the Video
This video shows whereby clicking a link an Azure storage account keys exfiltrated to an attacker and a file is automatically uploaded to the compromised storage account.





