Introduction
In recent times, ransomware attacks have become one of the most significant threats to cybersecurity. As part of our continuous commitment to monitoring and mitigating these threats, the Bridewell CTI team closely follows the work of other security researchers in the industry. Recently, our team came across an insightful report published by Mandiant on the AlphV ransomware. Impressed by their findings, we decided to conduct a further analysis of the infrastructure behind the ransomware to provide our audience with a wider range of indicators.
Mandiant's AlphV Ransomware Report
Mandiant's report (which you can find here) dives into the details of the AlphV ransomware targeting old vulnerabilities for initial access. The report highlights the ransomware's tactics, techniques, and procedures (TTPs), as well as some of the unique features that set it apart from other ransomware strains.
Building on Mandiant's Findings
At Bridewell CTI, we were intrigued by Mandiant's research and felt there was more to uncover about the infrastructure behind the AlphV ransomware. Our team conducted an in-depth analysis, focusing on the domains utilised, the deployment of Meterpreter and Metasploit, and the command and control (C2) servers.
Key Findings
Domains Utilised
We identified a number of domains associated with the AlphV ransomware campaign. These domains are often used for hosting the malware payloads and facilitating communication between the infected systems and the attackers. By mapping these domains, we were able to provide valuable insight into the infrastructure supporting the ransomware.
Based on the additional analysis conducted by Bridewell, 29 new domains linked to AlphV have been identified. The group has taken additional Operational Security (OpSec) measures to hide the backend infrastructure linked to these domains. When analysing them, we can see that the DNS records point to Cloudflare:
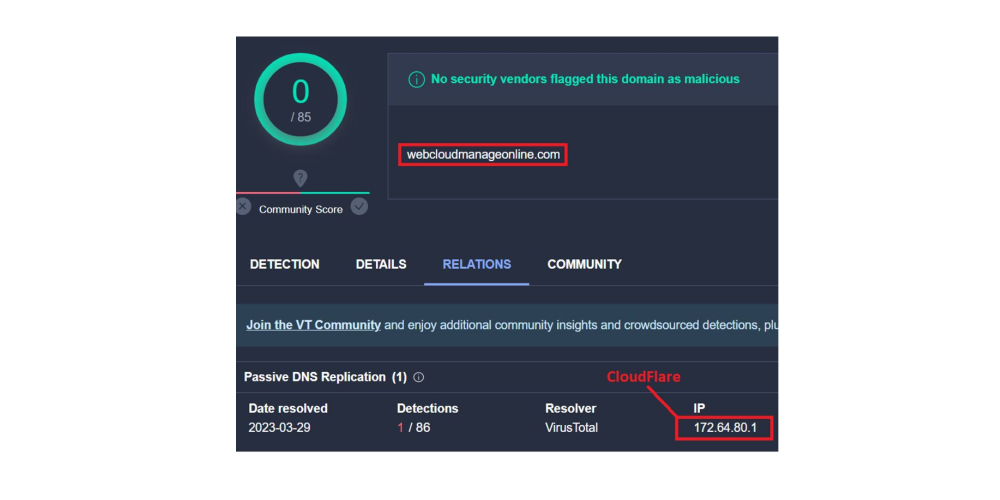
Figure 1. VT result from C2 domain pointing to Cloud Fare
However, pivoting from a server provided in the Mandiant report, we can identify the backend infrastructure, exclusively hosted on the UAB Cherry Servers ISP. Below is the matching domain with the backend server:
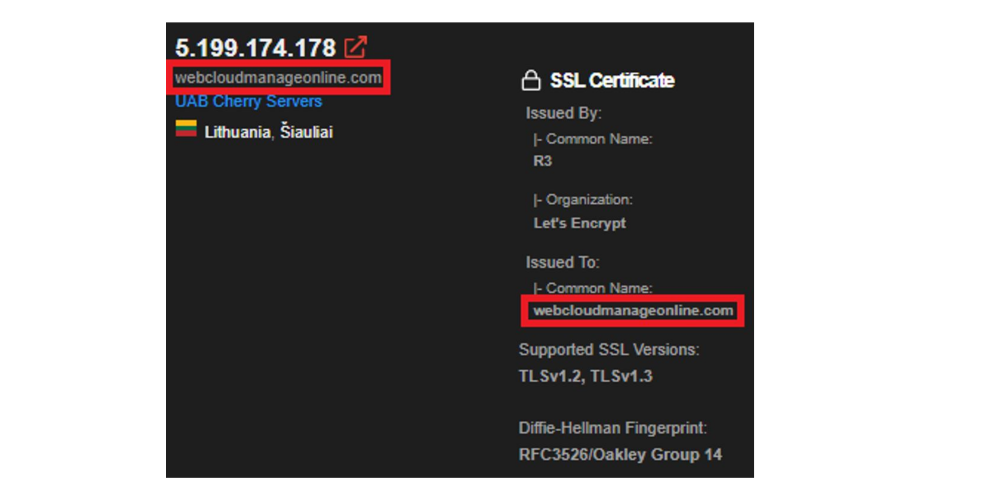
Figure 2. Shodan result for C2 server
Bridewell has identified a number of these IPs to be associated with IcedID malware which is deployed by a number of Initial Access brokers and threat actors such as those deploying Emotet and using IcedID as a follow on payload:
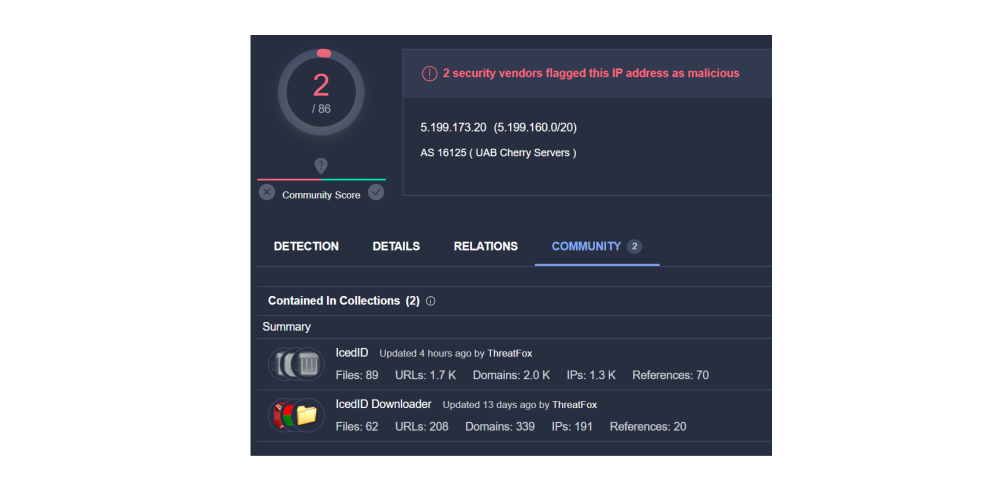
Interesting observations made by Bridewell
In September 2022, public reports by security researchers identify that the AlphV and Quantum ransomware groups are utilising Emotet infections to deploy their payloads.
Additionally, in November 2022, Proofpoint released a report highlighting that Emotet pushes a new variant of IcedID called IcedID Lite, which focuses solely on facilitating ransomware groups (removing banking and host collection functionality).
Based on this reporting and information gathered during our research, it is assessed by Bridewell that the AlphV ransomware group are likely purchasing initial access gained by IcedID deployed via Emotet or Initial Access Brokers to initiate their intrusions.
Meterpreter and Metasploit Deployment
Our analysis revealed that the threat actors behind the AlphV ransomware leveraged the Meterpreter and Metasploit frameworks for compromising victim systems. These powerful tools provide the attackers with a wide range of capabilities, allowing them to efficiently maintain control over the infected machines and carry out their malicious activities.
Pivoting from the Mandiant report, Bridewell were able to identify additional infrastructure linked to AlphV. Taking IP 45.61.138[.]109, Bridewell leveraged the historical records from Shodan to identify a previously open port on 8080 which presented a fingerprint known to be associated with Meterpreter by Bridewell.
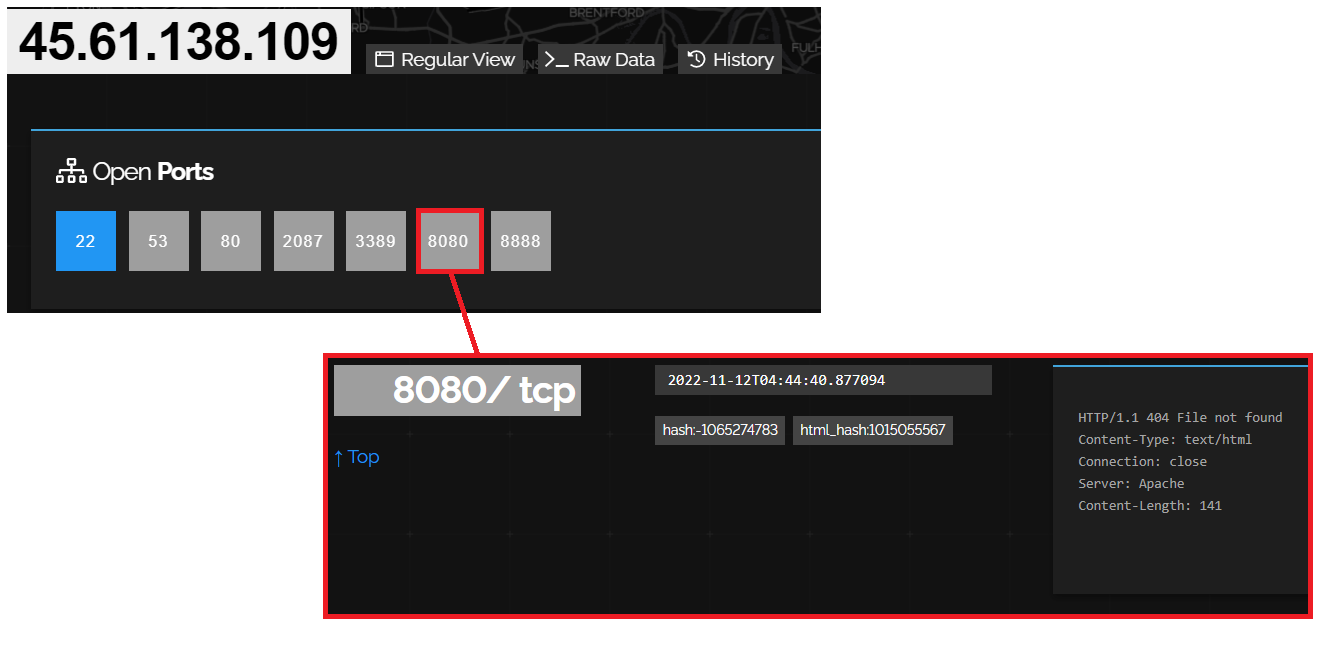
Figure 4. IOC from Mandiant Report with historical fingerprint for Meterpreter
.png?sfvrsn=4178da37_2)
Based on this fingerprint, Bridewell identified 99 Meterpreter C2 results in Shodan for currently active servers in the wild:
Figure 5. Global distribution of Metasploit C2 and hosting providers
Mitigating the AlphV Ransomware
Based on our research and Mandiant's findings, we recommend the following steps to help protect against the AlphV ransomware:
- Action the identified Indicators of Compromise (IoCs), such as malicious domains and IP addresses to prevent communication with the attackers' infrastructure.
- Maintain regular backups of critical data and ensure that they are stored offline.
- Keep all software up-to-date and apply security patches promptly.
- Implement a robust incident response plan to minimise damage in case of a breach.
Conclusion
The AlphV ransomware is a sophisticated and potent threat that can have devastating consequences for its victims. By building on Mandiant's findings, Bridewell CTI's analysis provides a more comprehensive understanding of the infrastructure behind this malware. We hope that our research will help organisations take proactive measures to protect themselves from such threats and contribute to the broader cybersecurity community's efforts in combating ransomware.
Annex A
C2 Domains:
all-app-inc[.]com
allautotechnow[.]com
allcompanygroup[.]com
allincservices[.]com
allllcgroup[.]com
alllocalcompany[.]com
allonlinebusinessservices[.]com
auto-tech-llc[.]com
bestonlinebusinessgroup[.]com
getautoappnow[.]com
getautotechnow[.]com
gethighappinc[.]com
gethightechinc[.]com
my-online-company[.]com
myonlinecompanysolutions[.]com
one-business-group[.]com
online-company-group[.]com
online-company-solutions[.]com
onlinecoservices[.]com
onlinecousa[.]com
the-online-company[.]com
theonlinecoinc[.]com
theonlinecompanyinc[.]com
webcloudmanageonline[.]com
your-llc[.]com
yourcompanystudio[.]com
yourcosolutions[.]com
yourincstudio[.]com
youronlinebusinessshop[.]com
Cherry Server IPs:
5[.]199[.]162[.]99
5[.]199[.]173[.]3
5[.]199[.]174[.]178
5[.]199[.]162[.]216
5[.]199[.]173[.]9
5[.]199[.]169[.]239
5[.]199[.]161[.]65
5[.]199[.]173[.]41
5[.]199[.]174[.]175
5[.]199[.]173[.]20
5[.]199[.]168[.]81
5[.]199[.]169[.]234
5[.]199[.]161[.]48
5[.]199[.]173[.]24
5[.]199[.]161[.]18
5[.]199[.]168[.]171
5[.]199[.]169[.]193
5[.]199[.]169[.]251
5[.]199[.]169[.]209
5[.]199[.]173[.]8
5[.]199[.]161[.]88
5[.]199[.]162[.]241
5[.]199[.]169[.]254
5[.]199[.]162[.]145
5[.]199[.]174[.]176
5[.]199[.]162[.]166
5[.]199[.]162[.]165
5[.]199[.]168[.]107
5[.]199[.]168[.]216
5[.]199[.]169[.]224
5[.]199[.]169[.]242
5[.]199[.]162[.]149
5[.]199[.]168[.]213
5[.]199[.]173[.]40
5[.]199[.]161[.]67
5[.]199[.]162[.]1
Generic Meterpreter IPs:
3[.]20[.]143[.]240
101[.]33[.]248[.]33
118[.]193[.]36[.]116
146[.]190[.]92[.]159
128[.]199[.]99[.]111
24[.]137[.]215[.]168
20[.]62[.]176[.]30
167[.]172[.]92[.]124
43[.]242[.]213[.]182
192[.]81[.]128[.]146
125[.]124[.]138[.]141
3[.]83[.]39[.]238
23[.]94[.]131[.]51
107[.]191[.]61[.]199
2[.]56[.]10[.]15
66[.]152[.]160[.]97
20[.]246[.]81[.]83
101[.]34[.]90[.]47
116[.]204[.]211[.]130
176[.]58[.]110[.]151
107[.]148[.]131[.]222
150[.]158[.]142[.]12
195[.]238[.]126[.]224
103[.]234[.]72[.]170
175[.]178[.]213[.]24
20[.]81[.]187[.]27
24[.]199[.]90[.]224
157[.]245[.]40[.]62
23[.]23[.]172[.]96
167[.]99[.]154[.]113
103[.]96[.]129[.]116
185[.]159[.]130[.]125
193[.]169[.]245[.]120
185[.]73[.]124[.]154
85[.]10[.]138[.]222
146[.]190[.]98[.]97
152[.]136[.]130[.]140
8[.]219[.]128[.]144
72[.]142[.]102[.]168
82[.]156[.]55[.]208
47[.]94[.]137[.]101
104[.]233[.]162[.]169
146[.]190[.]107[.]14
134[.]195[.]91[.]199
158[.]247[.]236[.]239
74[.]119[.]194[.]239
159[.]223[.]81[.]217
81[.]68[.]247[.]107
42[.]192[.]59[.]199
13[.]77[.]104[.]147
116[.]205[.]244[.]33
43[.]143[.]230[.]92
18[.]116[.]77[.]125
1[.]117[.]183[.]85
89[.]1[.]88[.]251
206[.]188[.]197[.]227
209[.]97[.]172[.]32
43[.]143[.]114[.]30
183[.]134[.]99[.]183
103[.]244[.]148[.]36
89[.]1[.]88[.]253
93[.]95[.]224[.]189
149[.]127[.]215[.]86
47[.]92[.]243[.]108
158[.]247[.]196[.]148
202[.]79[.]171[.]27
5[.]34[.]177[.]25
43[.]138[.]47[.]22
194[.]33[.]39[.]89
154[.]40[.]46[.]31
185[.]67[.]204[.]98
81[.]68[.]152[.]129
45[.]56[.]162[.]71
141[.]95[.]139[.]226
74[.]234[.]95[.]8
45[.]82[.]79[.]48
212[.]118[.]8[.]147
193[.]124[.]33[.]251
195[.]128[.]248[.]10
192[.]30[.]242[.]155
45[.]79[.]144[.]196
47[.]96[.]190[.]247
118[.]193[.]78[.]234
81[.]68[.]91[.]194
43[.]139[.]146[.]77
20[.]238[.]43[.]254
81[.]19[.]136[.]238
194[.]49[.]94[.]165
50[.]255[.]107[.]170
185[.]14[.]28[.]134
141[.]164[.]49[.]54
172[.]104[.]33[.]31
89[.]1[.]88[.]250
175[.]178[.]153[.]101
139[.]155[.]90[.]81
185[.]223[.]235[.]122
206[.]25[.]68[.]46
Register for instant alerts to Bridewell threat advisories or to speak with a member of our Cyber Threat Intelligence team.





