An intrusion that began in September 2024 has been analysed in depth, and reveals a sophisticated, multi-phase campaign highly likely to have been orchestrated by a ransomware-affiliate actor working across multiple Ransomware-as-a-Service (Raas) groups.
Despite no final ransomware deployment being observed, the attacker successfully achieved initial access, followed by network reconnaissance, collection and exfiltration of data.
Researchers at DFIR have linked this activity to several key ransomware groups including PLAY, RansomHub and DragonForce threat groups.
Our CTI team has since conducted further analysis, enrichment and pivoting using the data provided in this report, and has linked some of the attacker infrastructure to the ransomware group, Shadow Syndicate, who share links to some of the IP addresses observed in this report and with the prominent threat group, RansomHub.
Key Findings
Initial access was gained via a trojanised version of a legitimate application, leading to the deployment of SectopRAT, which then established a Command-and-Control (C2) channel. It is assessed that this payload was delivered through Drive-by Compromise, due to the origin of the downloaded initial access payload discovered by DFIR researchers.
The attacker’s tool selection included multiple distinct capabilities, including the use of SystemBC for tunnelling and proxying, Remote Desktop Protocol (RDP) access, the deployment of Betruger backdoor and the use of custom reconnaissance tool, Grixba, which is linked to the PLAY ransomware group.
Reconnaissance and lateral movement spanned domain controllers, backup and file servers alike, and the threat actor used tools such as AdFind, SharpHound, SoftPerfect Network Scanner, along with other utilities like Impacket and PsExec.
Persistence was achieved via tactics such as Windows Background Intelligent Transfer Service (BITS) transfer jobs, where the actor moved payloads and renamed executables, created auto-start shortcuts, local user accounts and assigned administrative privileges.
Data collection and exfiltration were achieved using WinRAR to archive high-value data, staging this in publicly writable locations and then exfiltrating via unencrypted use of the File Transfer Protocol (FTP) using WinSCP.
Although no ransomware execution was observed, the attacker successfully exfiltrated data and executed tools and techniques consistent with ransomware preparation. Importantly, indicators link this intrusion to at least three ransomware groups (i.e., PLAY, DragonForce and RansomHub. Our CTI team has also linked this activity to another RaaS actor, Shadow Syndicate.
Key Implications for Organisations
The convergence of tools normally associated with discrete ransomware groups, all used by a single affiliate actor, suggests that affiliates are increasingly operational across multiple RaaS ecosystems. Organisations must assume that any severe intrusion may carry full ransomware potential, even if the incident began with less obvious tools.
The use of widely available utilities (WinRAR, RDP, BITS) used in conjunction with custom-compiled malware emphasises the need for monitoring and detection not only of known malware, but of anomalous use of legitimate tools.
Data exfiltration via unencrypted or poorly secured channels remains a key phase of ransomware campaigns. Organisations must inspect outbound traffic, staging locations, archive-creation within public folders and unusual transfer to cloud or external hosts. The fine line between reconnaissance and ransomware deployment is blurring, and defenders must treat early phases of intrusion with full severity, even if no ransomware is yet visible.
Recommendations
Our CTI team recommends taking the following actions to better protect against ransomware groups such as PLAY, RansomHub and DragonForce:
- Monitor for suspicious lateral movement performed via Windows BITS jobs transferring executables into unusual locations, such as publicly accessible folders, AppData folders, temp folder and startup folders.
- Additional alerting and monitoring for unusual parent/child process chains, such as, “MSBuild.exe” being invoked with no arguments, or “rundll32.exe” calls from public writable folders.
- Monitor RDP logins to look for sequences of LogonType 3 then LogonType 10, especially where the initiating source is a previously unseen endpoint or host.
- Inspect outbound FTP traffic and archive-creation tools (WinRAR/WinZip) being used outside of normal business workflows.
Initial Access: SectopRAT
To establish a foothold and achieve initial access within the victim’s environment, the threat actor employed masquerading techniques by disguising malicious executables as legitimate software (T1036: Masquerading). The intrusion, which took place in September 2024, began with the execution of a trojanised payload impersonating EarthTime, a legitimate application developed by DeskSoft.
EarthTime is a widely available visualisation tool that displays local time, weather and geographical data for locations worldwide. In this campaign, a maliciously modified version of the EarthTime installer was downloaded from the internet (T1189: Drive-by Compromise) and used to deliver and execute a SectopRAT payload on the victim’s host.
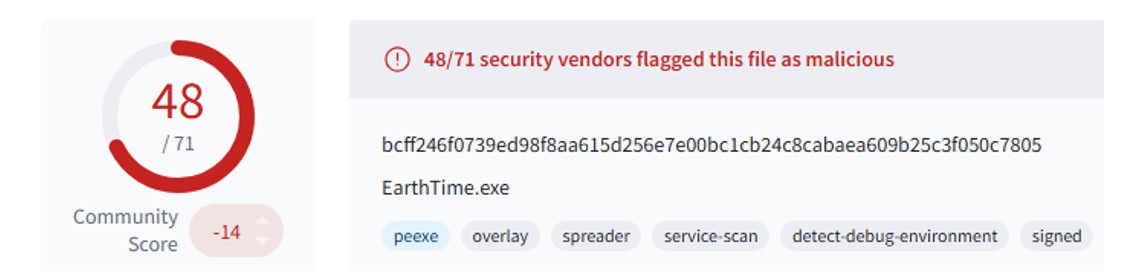
Figure 1: Actors used a legitimate version of the EarthTime application to deliver malware.
Analysis of the “EarthTime.exe” payload revealed notable characteristics of the malicious SectopRAT binary. The sample was found to be signed with a certificate issued to DeskSoft, corresponding to version 6.24.12 of the legitimate tool. However, the signer information identified the certificate as belonging to “Brave Pragmatic Network Technology Co., Ltd”, which has since been revoked.
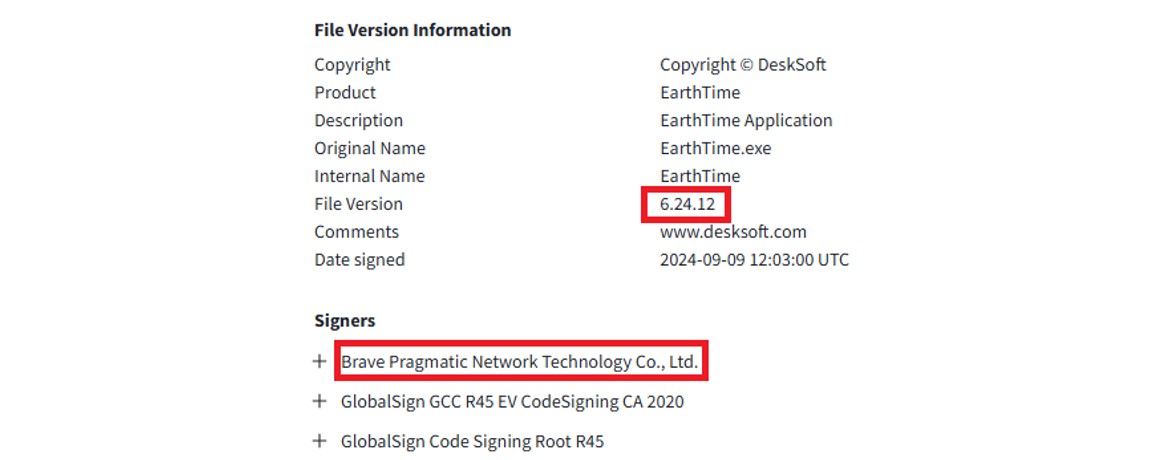
Figure 2: To obtain initial access, the actors used legitimate certificates.
This compromised certificate serves as a strong indicator of malicious activity and has also been observed in other, unrelated malware campaigns, including recent samples of LummaStealer, a widely popular information stealing malware.
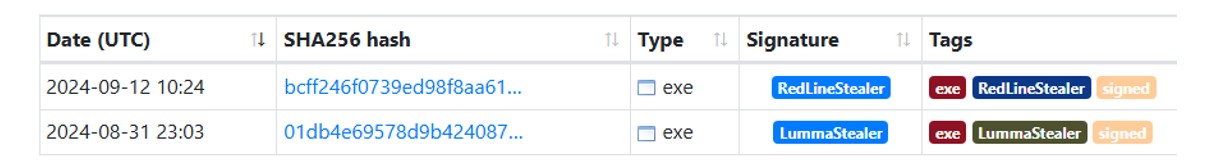
Figure 3: The code-signing certificate used in this campaign has been attributed to malware in the past.
When executed, the trojanised EarthTime binary deployed and executed SectopRAT, a well-documented Remote Access Trojan (RAT) first identified in 2019. Also known as ArechClient2, SectopRAT is typically propagated through malicious advertising, SEO poisoning and drive-by compromise techniques, reflecting its use in broad, opportunistic intrusions.
Once active, the malware establishes a remote-access tunnel to the compromised host, enabling attackers to download and execute additional payloads, issue arbitrary commands and harvest sensitive information such as credentials, browser data and system information. SectopRAT also possesses information stealing and reconnaissance capabilities, allowing it to prepare the environment before subsequent activity.
Due to its modular design and focus on persistence, SectopRAT often serves as a first-stage payload in multi-phase intrusion chains, paving the way for secondary malware such as backdoors, loaders or ransomware.
SectopRAT: Execution Behaviour and Detection
In their report, DFIR analysts noted that the SectopRAT malware was executed via Windows Explorer, from the “C:\Users\User\Downloads” folder. This suggests that the activity originated from manual user execution (T1024: User Execution), which is highly likely given the Drive-by Compromise technique used for initial access.
To further investigate this, our CTI team performed sandbox analysis of the infection chain to identify key attack behaviours and develop threat hunting queries to protect our customers from ransomware activity. Consistent with DFIR’s findings, we observed suspicious process events generated by Microsoft Defender upon execution of the EarthTime application.
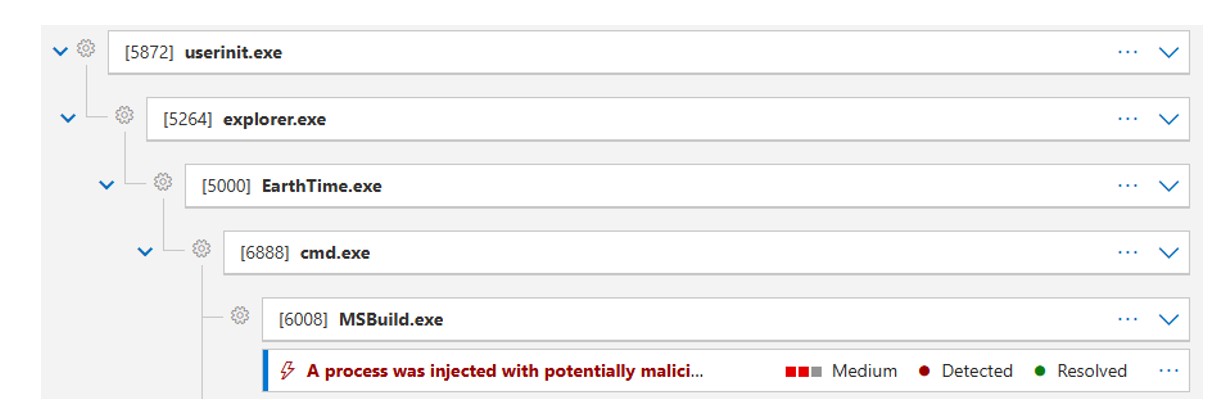
Figure 4: The EarthTime application was manually executed.
As shown above, Microsoft Defender successfully detected execution of the EarthTime application and generated a process injection alert, indicating that the malware spawned two malicious processes, a Windows command prompt (“cmd.exe”) and MsBuild (“msbuild.exe”), a legitimate Windows component used to install applications (T1055: Process Injection).
This technique is frequently used by threat actors who abuse trusted system binaries to conceal malicious behaviour and evade detection.
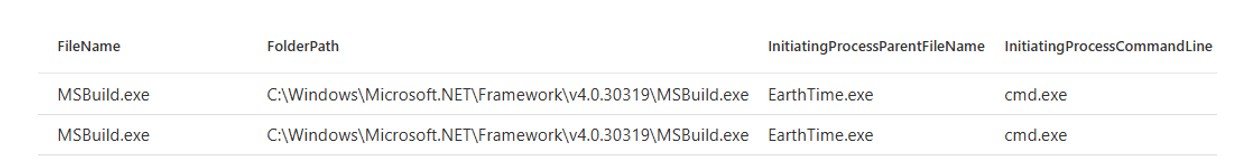
Figure 5: SectopRAT uses process injection to target legitimate Windows processes.
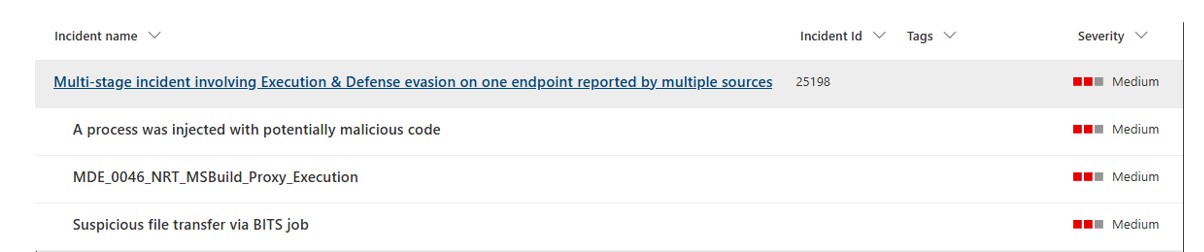
Figure 6: Alerts generated by this malicious activity in a sandbox.
Command-and-Control: SectopRAT
During sandbox analysis of the infection chain, our CTI team also identified notable characteristics of the SectopRAT payload’s C2 behaviour.
Following execution of the EarthTime.exe payload and its process injection into the legitimate MsBuild process, external HTTP traffic was observed originating from the injected process. Analysis of the payload revealed two unusual C2 URLs including https://pastebin[.]com, which is leveraged to retrieve the C2 configuration (T1071.001: Application Layer Protocol: Web Protocol).
Additionally, the payload was observed communicating with a malicious, attacker-controlled IP address using a unique URL parameter:
http://45.141.87[.]55:9000/wbinjget?q=FFB826D9252E13C4BB6EAEFFB2C1849C
The screenshot below illustrates the two C2 URLs contacted by the malicious application: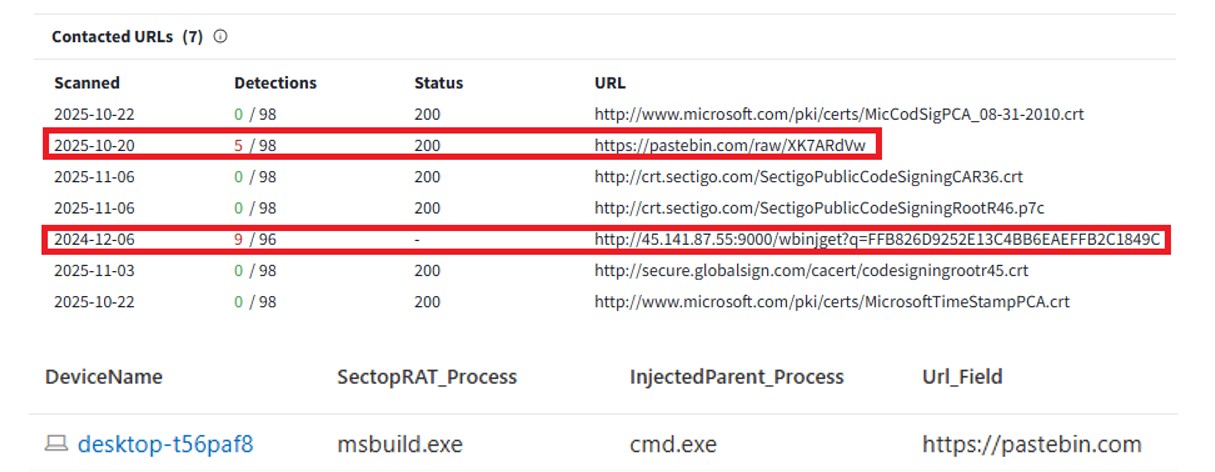
Figure 7: Process injection activity consistent with widely reported behaviour of the EarthTime application.
This C2 IP address (45.141.87[.]55) used by SectopRAT was investigated in more detail, revealing that this IP address is passively tracked by our CTI team’s C2 detection service, where it was first identified in August 2024.
This was 46 days before VirusTotal began tracking this IP address as malicious.
![]()
Figure 8: Bridewell CTI are tracking the SectopRAT C2 IP since 2024.
In total, our CTI team is currently tracking over 226 unique IP addresses attributed to SectopRAT, at an average of 18 days before VirusTotal detection.
![]()
Figure 9: Bridewell CTI is tracking over 200 SectopRAT IP addresses.
Furthermore, our CTI team conducted broader infrastructure analysis, pivoting from the indicators of compromise (IOCs) provided by DFIR researchers. Through this analysis, we identified additional payloads and IP addresses that we assess with moderate confidence to be associated with this campaign based on overlaps in unique C2 parameters and URLs and code-signing certificates observed in the original activity.
While this report includes a comprehensive list of IOCs collected during our research, this following section highlights the newly identified IP addresses and file hashes that were not present in the original report:
- 1cefb6e3871357bd629d39e4533a04c19ad3418807eae9487d5fb8c28bdfc202
- 6222e9bdf67a016e7fd7ea2b447706cba3f5796e46e70c5e9786317e551e0444
- 8bcb05ee41802733f996870feaba0863a1fe8736d49409a58178a1710a406a5f
- afc9edae65579141465dd988495aa73366f942287ac85773f0c630b5bb3e2420
- bcff246f0739ed98f8aa615d256e7e00bc1cb24c8cabaea609b25c3f050c7805
- ccb03838f324b4e1b4a598d8418dc6d277058fa6897d61599416b96138c67652
- 144.172.93[.]139
- 109.120.139[.]22
- 107.189.21[.]76
- 94.26.90[.]133
One of the newly identified IP addresses, 94.26.90[.]133, has also been attributed to the RaaS linked threat group, Shadow Syndicate. Our CTI team has previously conducted extensive research into Shadow Syndicate, a threat actor known to collaborate with and support various ransomware operations, highlighting their key tactics, techniques and procedures (TTPs) and tooling.
In January 2025, researchers at DarkTrace published an investigative report into Shadow Syndicate activity, noting a connection between Shadow Syndicate and the RansomHub group, one of three key ransomware groups highlighted in this report.
Additional Pivoting and SectopRAT Impersonation Payloads
To further understand the activity conducted within this campaign, our CTI team performed additional pivoting using the previously highlighted C2 URLs to identify further malicious content, revealing several additional payloads which we assess with high confidence to be part of this campaign due to the use of matching C2 URLs.
Our CTI team identified two further payloads which have been used to impersonate other legitimate applications, including Saint Paint Studio and BlueFin.
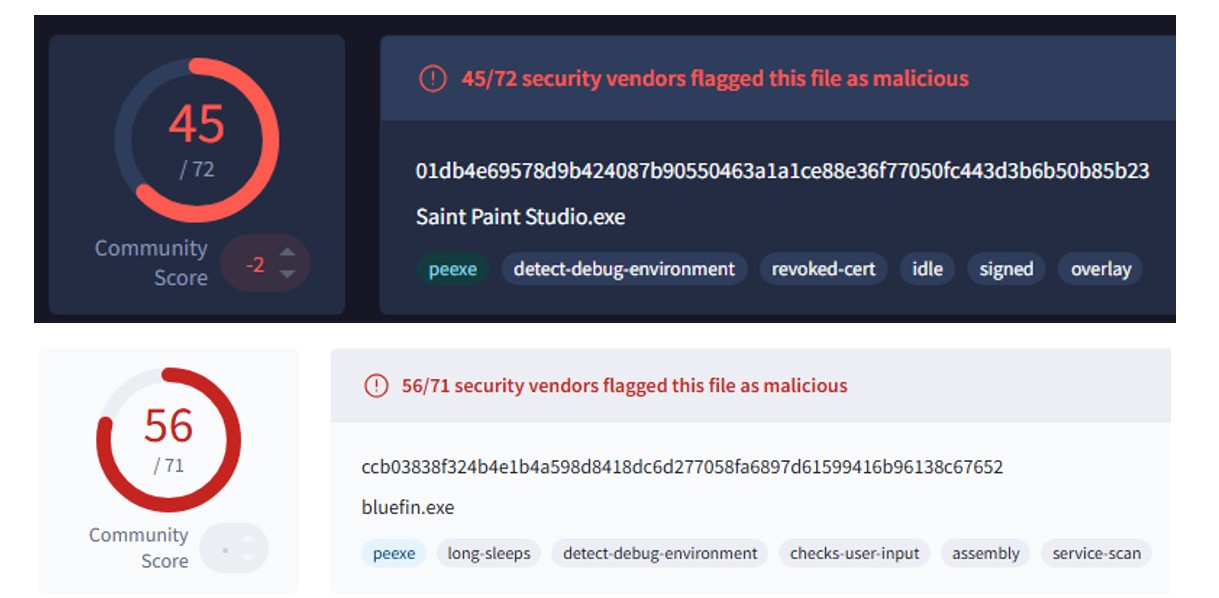
Figure 10: Further malicious payloads indicate that the actor may have impersonated more than the EarthTime application.
Analysis of the “Saint Paint Studio.exe” payload reveals identical code-signing information seen within other malicious payloads linked to this campaign:
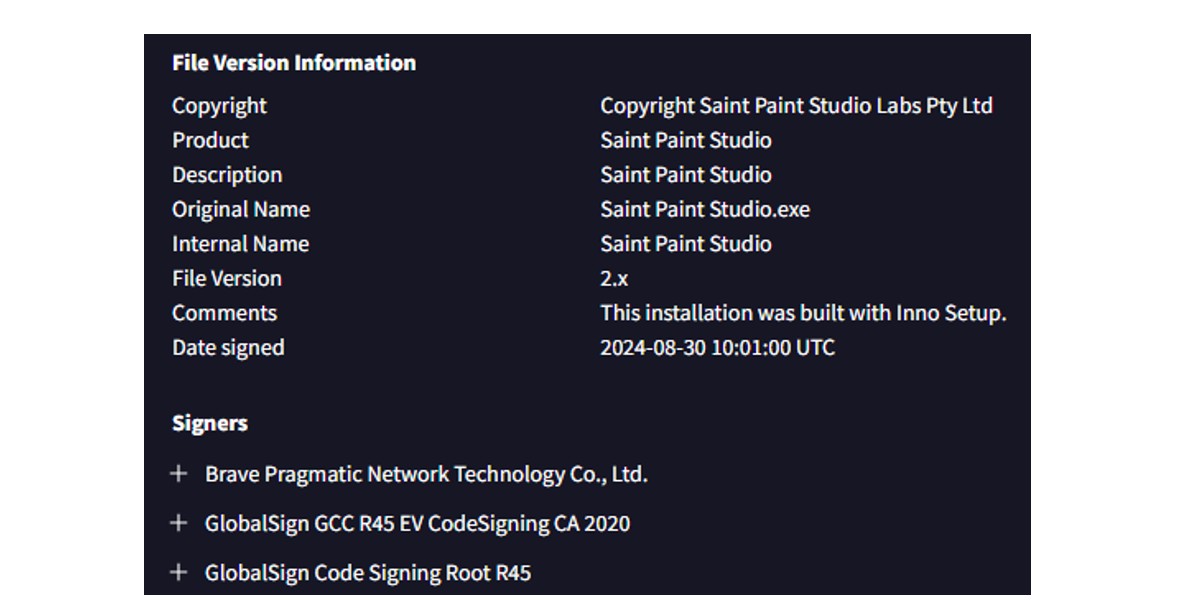
Figure 11: Additional payloads sharing identical code-signing details.
Based on these findings, our CTI team assess that these payloads suggest a broader effort to mimic additional software as part of the threat actor’s evasion strategy.
Persistence & Additional Techniques: SectopRAT
Following initial access and execution, the threat actor established persistence by leveraging the Windows BITS to transfer payloads to secondary locations on the compromised host (T1197: BITS Jobs).
The malware was copied to the user’s AppData directory (“C:\Users\User\AppData\Roaming\QuickAgent2”) and afterwards, renamed to “ChromeAlt_Dbg.exe”, to masquerade as a legitimate component of the Google Chrome browser.
To complement this, the actor created a Windows shortcut (“.lnk”) file referencing the original SectopRAT payload, which was placed in the Windows startup folder (“C:\Users\User\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup”) to ensure automatic execution on boot (T1547.001: Registry Run Keys / Startup Folder).
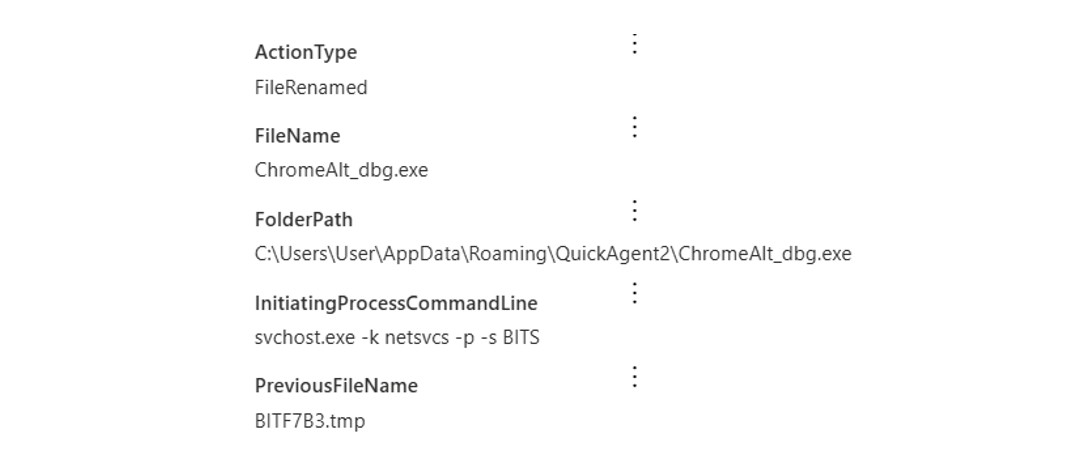
Figure 12: The SectopRAT payload copied to establish persistence on the infected host.
It was also determined that the threat actor employed additional persistence techniques by leveraging legitimate Windows utilities to create new local user accounts on compromised systems. Specifically, the actor used the “Net.exe” and “Net1.exe” command-line utilities to create a local account named “admon”, which was then added to the “Administrators” group (T1136.001: Create Account: Local Account, T1098.007: Account Manipulation: Additional Local or Domain Groups).
This action granted elevated privileges, enabling the threat actor to maintain continued access for later stages of the intrusion.
Betruger Backdoor & Grixba Internal Reconnaissance
During the subsequent stages of this intrusion, analysts identified the deployment of several families of malware, including the Betruger backdoor, SystemBC and Grixba, known to be used by several threat actors including PLAY and RansomHub specifically.
Betruger Backdoor
The Betruger backdoor, which has been attributed to RansomHub affiliates in the past, contains functionality to perform several actions that may serve as a precursor to ransomware activity, including the ability to screenshot and perform keylogging, conducting command-and-control and uploading and downloading payloads (T1056.001: Input Capture: Keylogging, T1113: Screen Capture, T1105: Ingress Tool Transfer).
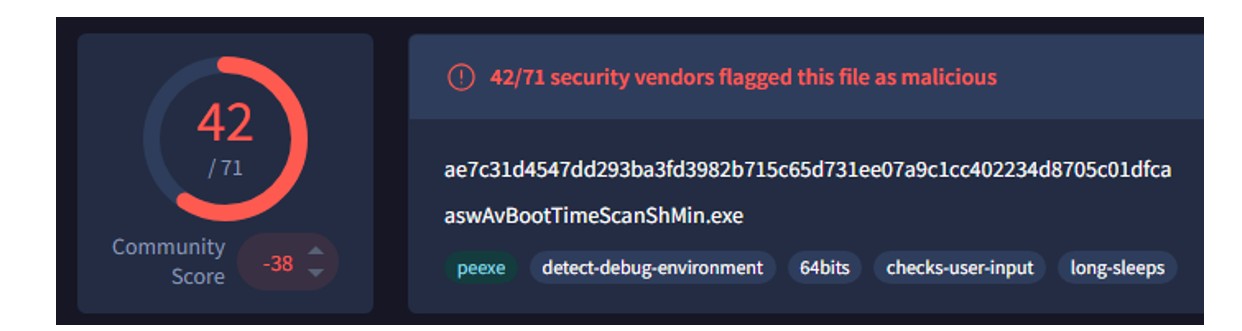
Figure 13: The Betruger payload used within this incident.
Our CTI team has executed this file within a sandbox environment to observe its behaviour. We identified alerts that had been generated by Microsoft Defender, linking this payload to emerging ransomware activity.
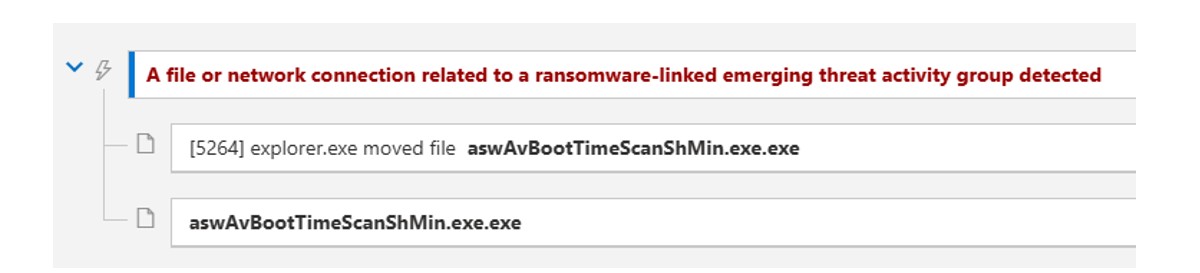
Figure 14: This file is linked to emerging ransomware activity.
Further analysis of the Betruger payload revealed distinctive code-signing characteristics suggesting that the threat actor attempted to masquerade the file as the legitimate anti-virus vendor, Avast, to evade detection.
This technique highlights a remarkably similar methodology of attack to impersonation techniques used by the SectopRAT payload in the initial access vector of this intrusion.
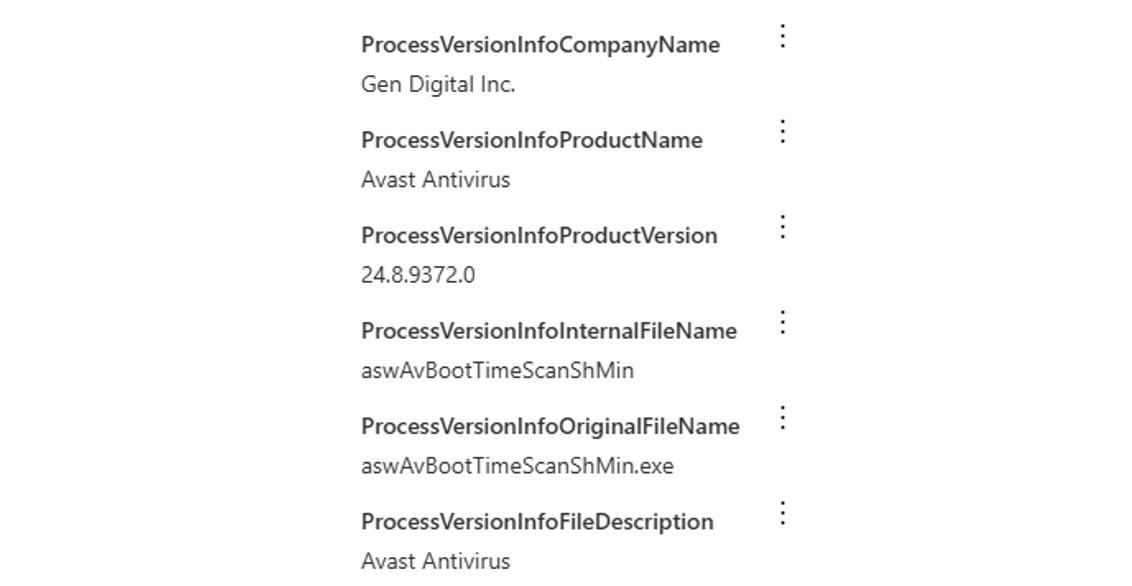
Figure 15: The Betruger payload contains signature information linked to Avast Anti-Virus software.
Broader reporting also indicates that during this incident, the malicious Betruger payload was placed in a public directory at “C:\Users\Public\Music\css.exe” and was observed interacting with the Windows LSASS process.
Additional research on the Betruger malware, including analysis performed by Symantec, confirms that this malware has credential access capabilities, enabling it to extract authentication data from compromised systems (T1003.001: OS Credential Dumping: LSASS Memory). Additional evidence of collection and discovery activity was also identified, in which the Betruger payload was observed spawning suspicious processes on the infected host.
The Betruger payload was observed conducting internal reconnaissance by spawning unusual, suspicious processes on the victim’s host. DFIR researchers highlighted that suspicious living-off-the-land processes that were abused during this attack. These included legitimate Windows processes, such as, “whoami.exe”, “net.exe”, “ping.exe” and “nltest.exe” (T1033: System Owner/User Discovery, T1082: System Information Discovery, T1059.003: Windows Command Shell).
Grixba – The PLAY Ransomware Reconnaissance Tool of Choice
Grixba, a reconnaissance and internal-scanning tool frequently used by PLAY affiliates, was deployed during this incident. The tool leverages the Windows Management Instrumentation (WMI) service to enumerate and gather information across networks (T1047: Windows Management Instrumentation). Two distinct builds were recovered, including “GT_NET.exe” and GRB_NET.exe”, both of which were executed on hosts and domain controllers in the compromised environment.
These two builds of malware were executed using similar file-masquerading techniques, in which the actor tampered with the metadata of the Grixba payload, rewriting it to impersonate legitimate security vendor, Sentinel Labs, Inc.
Grixba is capable of remote-access operations and can also function as an information-stealing tool. The below screenshot illustrates Grixba’s execution, which was performed using the command-line (“cmd.exe”).
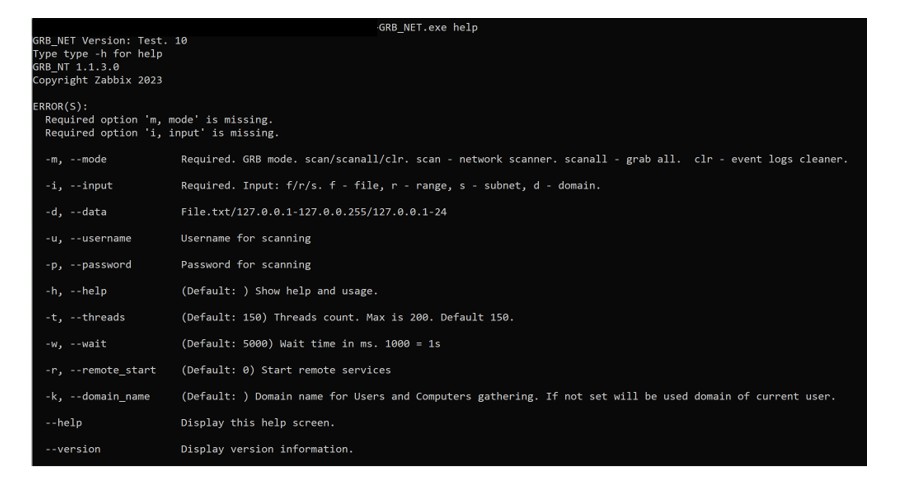
Figure 16: Grixba command-line functionality.
The above screenshot demonstrates Grixba’s functionality, offering the ability to select between different modes of operation, accept external scanning target lists and adjust runtime behaviour (such as imposing time delays, remote execution, or immediate execution) depending on the threat actor’s requirements.
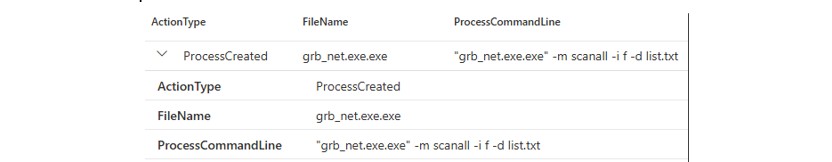
Figure 17: Grixba execution as captured within Defender logs.
Lateral Movement Through RDP & Impacket
Although no ransomware payloads were successfully deployed during this incident, DFIR researchers assess that data exfiltration and extortion were the primary objectives of the attack. After the threat actor gained access to the environment, additional post-exploitation activities were observed.
Lateral movement within the compromised environment was achieved primarily via Windows RDP (T1021.001: Remote Services: Remote Desktop Protocol). Examination of Windows event logs showed a recurring pattern in which network logons (type 3) were quicky followed by remote interactive logons (type 10).
DFIR researchers suggest that this activity was facilitated by SystemBC malware, which was used to proxy network traffic through compromised machines. (T1090: Command-and-Control: Proxy)
It is also important to note that the event log, indicates that the threat actor may have attempted to achieve lateral movement to the target user account “Admon”, referencing an attacker-controlled account that was created during the intrusion. The following unique RDP machine names were seen during this incident, including:- DESCTOP-QPITRY
- DESKTOP-A1HRTMJ
- DESKTOP-PGD76HT
- WIN-FLGU1CC210K
The threat actor also leveraged Impacket’s WmiExec module, a popular set of open-source Python tools used to manipulate network protocols, to facilitate additional lateral movement. During the incident, DFIR researchers observed suspicious WMI (“WmiPrvSE.exe”) command-line activity which suggests that the adversary was attempting to enumerate user account information, within the network.
Collection and Exfiltration
During the intrusion, the threat actor used WinRAR to collect data for exfiltration (T1560.001: Archive Collected Data: Archive via Utility).
The installation file for this tool was observed within the public Music folder, seen previously, where it was executed and used to install the WinRAR application to disk, inside the Program Files folder (“C:\Program Files\WinRAR\WinRAR.exe”).
The threat actors used this application to collect and archive sensitive victim data on the internal file sharing system before exfiltration. It was reported by DFIR analysts that over six directories of sensitive, high-value data were compressed, preparing them for exfiltration out of the environment, with the following command: (T1074: Data Staged).
"C:\Program Files\WinRAR\WinRAR.exe" a -ep1 -scul -r0 -iext -imon1 -- . F:\Shares\REDACTED\REDACTED
Exfiltration was performed using the File Transfer Protocol (FTP) and the WinSCP application, which was transferred into the victim’s environment inside a RAR file during the collection phase of the attack (T1048.003: Exfiltration Over Unencrypted Non-C2 Protocol)
DFIR researchers discovered a unique “WinSCP.ini” configuration file that was used by the threat actors to configure a custom filter, targeting a specific range of file types, including:
- Web Files, including HTML, PHP, JS, CSS.
- Configuration Files, including CFG, INI, HTACCESS
- Scripts and Code, including SH, PL, C, CPP
The nature of the files targeted within this attack suggest that the threat actor was attempting to gather and exfiltrate sensitive data, particularly code and scripts which have a higher likelihood of containing sensitive credentials, tokens, or source code.
After sensitive data was collected and staged, the threat actor used the WinSCP application to exfiltrate the data from the network. DFIR researchers observed outbound network traffic to 144.202.61[.]209 via FTP and the WinSCP application.
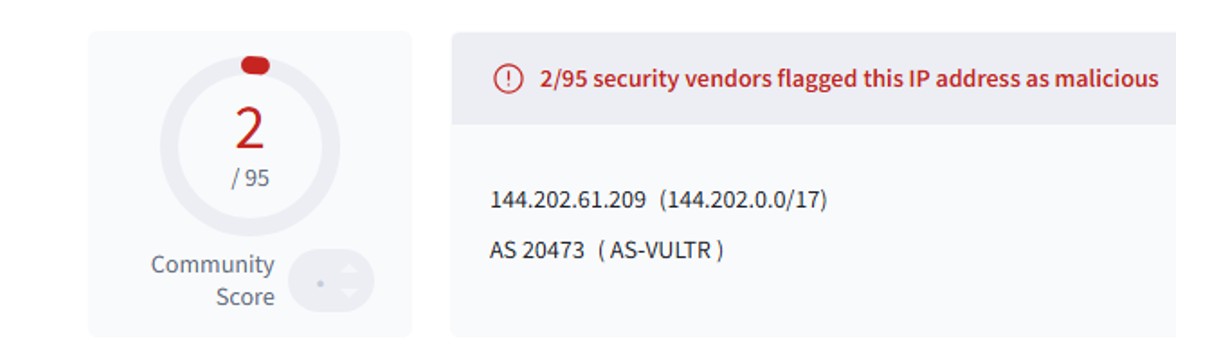
Figure 18: Threat actors exfiltrated sensitive data to this IP address via FTP.
Our CTI team recommends that customers ensure any suspicious outbound connections, particularly those using protocols such as RDP, FTP, WinSCP are monitored to prevent unauthorised (or even inadvertent) transfer of sensitive data.
Tools, TTPs and the Wider Ransomware Ecosystem
During this incident, no ransomware payloads were deployed, however, exfiltration of sensitive data was achieved. Based on the activity observed in the intrusion, DFIR researchers have stated with a high level of confidence that this attack was performed by a ransomware affiliate, with a high chance of this affiliate being connected to various RaaS operations, including PLAY and RansomHub.
Additionally, our CTI team has also identified a connection to another ransomware group, Shadow Syndicate, based on the infrastructure analysis conducted in the SectopRAT Command-and-Control section of this report. Shadow Syndicate are a ransomware group who are known to have further connections to the RansomHub group.
A full list of the tools used by the threat actor in this intrusion, as reported by DFIR, can be seen in the table below:
| Tools | Group | Description |
| Grixba | PLAY | A reconnaissance tool with information stealer capabilities, used exclusively by PLAY. |
| SectopRAT | Play & RansomHub & DragonForce & Shadow Syndicate | Remote access trojan used to facilitate initial access. |
| Betruger | RansomHub | Multifunctional backdoor, believed to be developed specifically to facilitate ransomware attacks. |
| Windows Background Intelligent Transfer Service (BITS) | RansomHub | Legitimate Windows binary used to perform file transfer functionality. |
| SystemBC | Play & DragonForce | Remote access malware which can be used to establish proxies. |
| Impacket (WmiExec) | Play & RansomHub | A suite of red teaming tools used to manipulate network traffic. |
| NetScan, AdFind, WinRAR, WinSCP, PsExec | Play & DragonForce & RansomHub | Various other post-exploitation tools used to facilitate discovery, collection, lateral movement and exfiltration. |
MITRE ATT&CK Mapping
| Phase | Technique Description | Technique ID |
| Initial Access | Drive by Compromise | T1189 |
| Execution | User Execution | T1204 |
| Execution | User Execution: Malicious File | T1204.002 |
| Execution | Process Injection | T1055 |
| Execution | Command and Scripting Interpreter | T1059 |
| Execution | Command and Scripting Interpreter: Windows Command Shell | T1059.003 |
| Execution | Windows Management Instrumentation (WMI) | T1047 |
| Persistence | Boot or Autostart Execution | T1547 |
| Persistence | Boot or Autostart Execution: Registry Run Keys/Startup Folder | T1547.001 |
| Persistence | Create Account | T1136 |
| Persistence | Create Account: Local Account | T1136. |
| Persistence | Account Manipulation | T1098 |
| Privilege Escalation | Account Manipulation: Additional Local or Domain Groups | T1098.001 |
| Defence Evasion | Masquerading | T1036 |
| Defence Evasion | Masquerading: Invalid Code Signature | T1036.001 |
| Defence Evasion | System Binary Proxy Execution | T1218 |
| Defence Evasion | System Binary Proxy Execution: Msiexec | T1218.007 |
| Defence Evasion | BITS Jobs | T1197 |
| Credential Access | Input Capture | T1056 |
| Credential Access | Input Capture: Keylogging | T1056.001 |
| Credential Access | Screen Capture | T1113 |
| Credential Access | Ingress Tool Transfer | T1105 |
| Credential Access | OS Credential Dumping | T1003 |
| Credential Access | OS Credential Dumping: LSASS Memory | T1003.001 |
| Discovery | System Owner/User Discovery | T1033 |
| Discovery | System Information Discovery | T1082 |
| Lateral Movement | Valid Accounts | T1078 |
| Lateral Movement | Remote Services | T1021 |
| Lateral Movement | Remote Services: Remote Desktop Protocol | T1021.001 |
| Collection | Data Staged | T1074 |
| Collection | Data Staged: Local Data Staging | T1074.001 |
| Collection | Archive Collected Data | T1560 |
| Collection | Archive Collected Data: Archive via Utility | T1560.001 |
| Command and Control | Command and Control: Proxy | T1090 |
| Command and Control | Application Layer Protocols | T1071 |
| Command and Control | Application Layer Protocols: Web Protocols | T1071.001 |
| Command and Control | Application Layer Protocols: File Transfer Protocol | T1071.002 |
Appendix
References
https://thedfirreport.com/2025/09/08/blurring-the-lines-intrusion-shows-connection-with-three-major-ransomware-gangs/
https://www.security.com/threat-intelligence/ransomhub-betruger-backdoor
https://fieldeffect.com/blog/grixba-play-ransomware-impersonates-sentinelone
Indicators of Compromise (IOCs)
| Name | Type | Comment |
| EarthTime.exe | File Name | SectopRAT payload impersonating legitimate application, Earth Time. |
| css.exe | File Name | Betruger backdoor file name. |
| WakeWordEngine.dll | File Name | SystemBC payload file name. |
| Gt_net.exe | File Name | Grixba Recon Tool File Name. |
| Grb_net.exe | File Name | Grixba Recon Tool File Name. |
| Netscan.exe | File Name | Advanced IP Scanner Payload File Name. |
| bcff246f0739ed98f8aa615d256e7e00bc1cb24c8cabaea609b25c3f050c7805 | Hash | SectopRAT payload impersonating legitimate application, Earth Time. |
| 1cefb6e3871357bd629d39e4533a04c19ad3418807eae9487d5fb8c28bdfc202 | Hash | SectopRAT payload impersonating legitimate application, Earth Time. |
| 6222e9bdf67a016e7fd7ea2b447706cba3f5796e46e70c5e9786317e551e0444 | Hash | SectopRAT payload impersonating legitimate application, Earth Time. |
| 8bcb05ee41802733f996870feaba0863a1fe8736d49409a58178a1710a406a5f | Hash | SectopRAT payload impersonating legitimate application, Earth Time. |
| afc9edae65579141465dd988495aa73366f942287ac85773f0c630b5bb3e2420 | Hash | SectopRAT payload impersonating legitimate application, Earth Time. |
| bcff246f0739ed98f8aa615d256e7e00bc1cb24c8cabaea609b25c3f050c7805 | Hash | SectopRAT payload impersonating legitimate application, Earth Time. |
| ccb03838f324b4e1b4a598d8418dc6d277058fa6897d61599416b96138c6765 | Hash | SectopRAT payload impersonating legitimate application, Earth Time. |
| 6f9326224e6047458e692cd27aeb1054b9381c67aaf2fe238dbebfbc916c4b33 | Hash | SystemBC payload. |
| ae7c31d4547dd293ba3fd3982b715c65d731ee07a9c1cc402234d8705c01dfca | Hash | Betruger backdoor payload. |
| e1521e077079032df974c7ae39e4737cdb4f05c6ded677ed5446167466eeb899 | Hash | Fs64.exe payload referenced in DFIR Report. |
| aeaf7cc7364a44b381af9f317fe6f78c2717217800b93bee8839ab3e56233254 | Hash | Grixba Recon Tool Hash. |
| f8810179ab033a9b79cd7006c1a74fbcde6ed0451c92fbb8c7ce15b52499353a | Hash | Grixba Recon Tool Hash. |
| c92c158d7c37fea795114fa6491fe5f145ad2f8c08776b18ae79db811e8e36a3 | Hash | AdFind.exe Payload. |
| a7240d8a7aee872c08b915a58976a1ddee2ff5a8a679f78ec1c7cf528f40deed | Hash | Sh.exe Payload. |
| 18f0898d595ec054d13b02915fb7d3636f65b8e53c0c66b3c7ee3b6fc37d3566 | Hash | Netscan.exe Payload. |
| 01db4e69578d9b424087b90550463a1a1ce88e36f77050fc443d3b6b50b85b23 | Hash | Saint Paint Studio.exe Payload. |
| 0bb9e107a5f5f9ad838173ebf222107d37cc1f378fa10f46ad5b2914f19f8e72 | Hash | BlueFin.exe Payload. |
| Brave Pragmatic Network Technology Co., Ltd | Certificate Info | Code signing details used by SectopRAT. |
| 45.141.87[.]55 | IP Address | SectopRAT C2 IP. |
| 149.28.101[.]219 | IP Address | SystemBC C2 IP. |
| 144.172.93[.]139 | IP Address | Additional SectopRAT C2 IPs. |
| 109.120.139[.]22 | IP Address | Additional SectopRAT C2 IPs. |
| 107.189.21[.]76 | IP Address | Additional SectopRAT C2 IPs. |
| 94.26.90[.]133 | IP Address | Additional SectopRAT C2 IPs. |
| 80.78.28[.]149 | IP Address | Betruger Backdoor C2 IP. |
| 144.202.61[.]209 | IP Address | FTP Server Used for Exfiltration |
| www.radarmap[.]site | Domain | SystemBC C2 Domain. |
| www.radarfuture[.]site | Domain | SystemBC C2 Domain. |
| radarmap.site radarfuture[.]site | Domain | SystemBC C2 Domain. |
| www.radarweatherdata[.]site | Domain | SystemBC C2 Domain. |
| radarweatherdata[.]site | Domain | SystemBC C2 Domain. |
| www.radarstormtracker[.]site | Domain | SystemBC C2 Domain. |
| radarstormtracker[.]site | Domain | SystemBC C2 Domain. |
| 504e1c95.host.njalla[.]net | Domain | Betruger Backdoor C2 Domain. |
| net user Admon Qwerty12345! /add | Command | SectopRAT Discovery and User Creation Commands. |
| net localgroup Administrators admon /add | Command | SectopRAT Discovery and User Creation Commands. |




