Since the start of January, we have observed a resurgence in malicious activity targeting the hotel and retail sector. The primary motivation driving this incident is financial fraud, targeting two victims: hotel businesses and hotel customers, in sequential order. The threat actor(s) utilise impersonation of the Booking.com platform through two distinct phishing kits dedicated to harvesting credentials and banking information from each victim respectively.
The threat actor(s) utilised a three-stage infection chain:
- Stage 1: the initial payload delivery (email) targeting the booking.com partner (hotel),
- Stage 2: the credential harvesting of Booking.com partners, targeting service desk agents using a partner phishing kit
- Stage 3: the financial fraud activity, targeting the hotel customer's financial data using a customer phishing kit.
The final stages of the infection chain, specifically the customer phishing kit and delivery via WhatsApp, align with previous open-source reporting in the "I Paid Twice" campaign reported by Sekoia. However, the initial delivery and targeting of the retail sector using a dedicated partner phishing kit is a new approach by either the same, or new operators, of the customer phishing kit.
ATT&CK Flow
The threat actors deploy two infection chains. The first is the phishing attempt on the hotel chains, and the second is the second is the partner phishing kit, which relies on the success of the first infection chain.
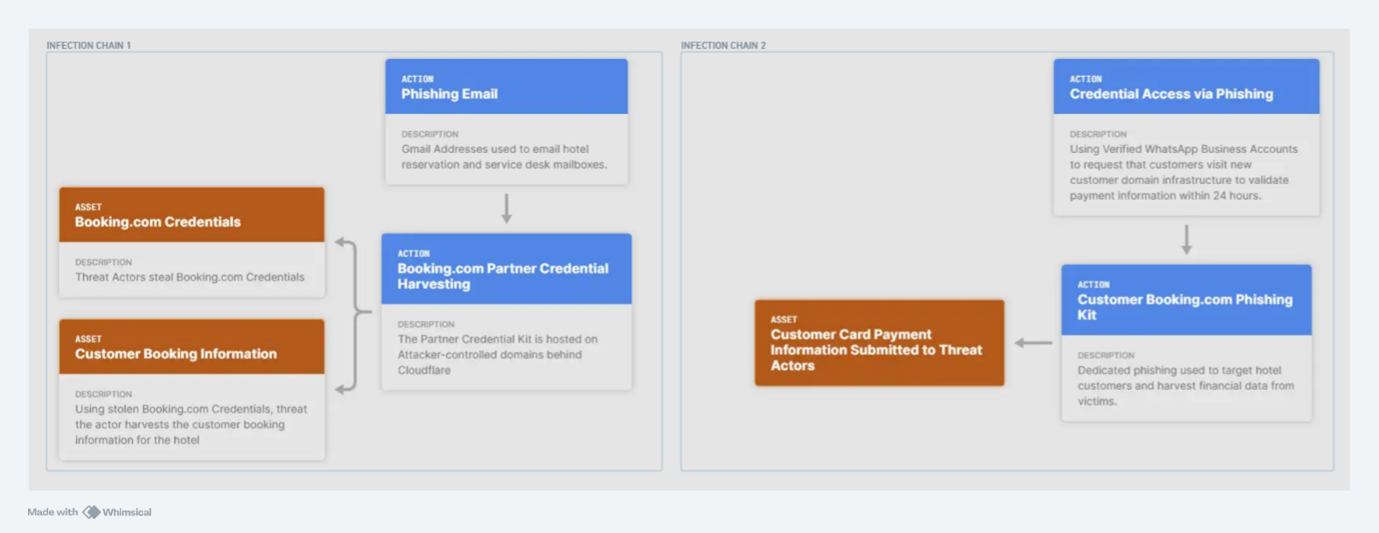
Figure 1: Infection Chain 1 - Stage 1 - Phishing Emails
The threat actors sent emails to reservation email addresses using numerous generated Gmail addresses following a similar structure, indicating automated registrations: [a-z]{7,11}[0-9]{2,3}@gmail.com. From these mailboxes, they impersonate Booking.com and refer to their targets as a "Partner" of the platform. The emails use a variety of subject lines focusing on room availability.
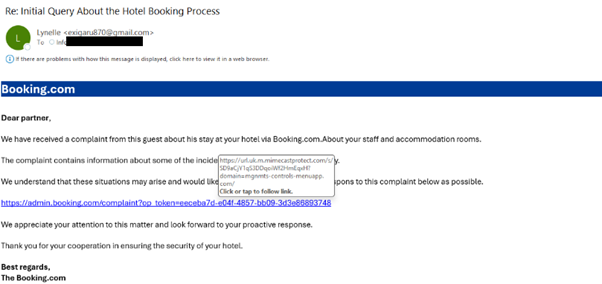
Figure 2: Initial Query
The theme of the email relates to a complaint from a guest staying at the target hotel: this is a classic conditioning technique to raise the "seriousness" of the email and lure the victim into acting upon the email instead of ignoring it. The body of the email is matched by an innocuous complaint link to the Booking.com site. However, the embedded URL redirects to the attacker-controlled infrastructure. This is another technique to appear legitimate and convincing to email gateways and the end users. The URLs also follow a consistent structure, typically containing ‘complaint?op_token=’ followed by a unique alphanumeric id value string.
Additionally, the Cyrillic small letter “о” (U+043E) was used in place of the Latin “o” (U+006F) in "booking", which is what makes it an IDN homograph. The domain visually impersonates Booking.com by substituting Cyrillic characters (e.g. Cyrillic “о”) for Latin letters, consistent with an IDN homograph technique.
Timeline
Based on these identifiable attributes, we identified a timeline of email activity targeting multiple customer tenants during this campaign window:
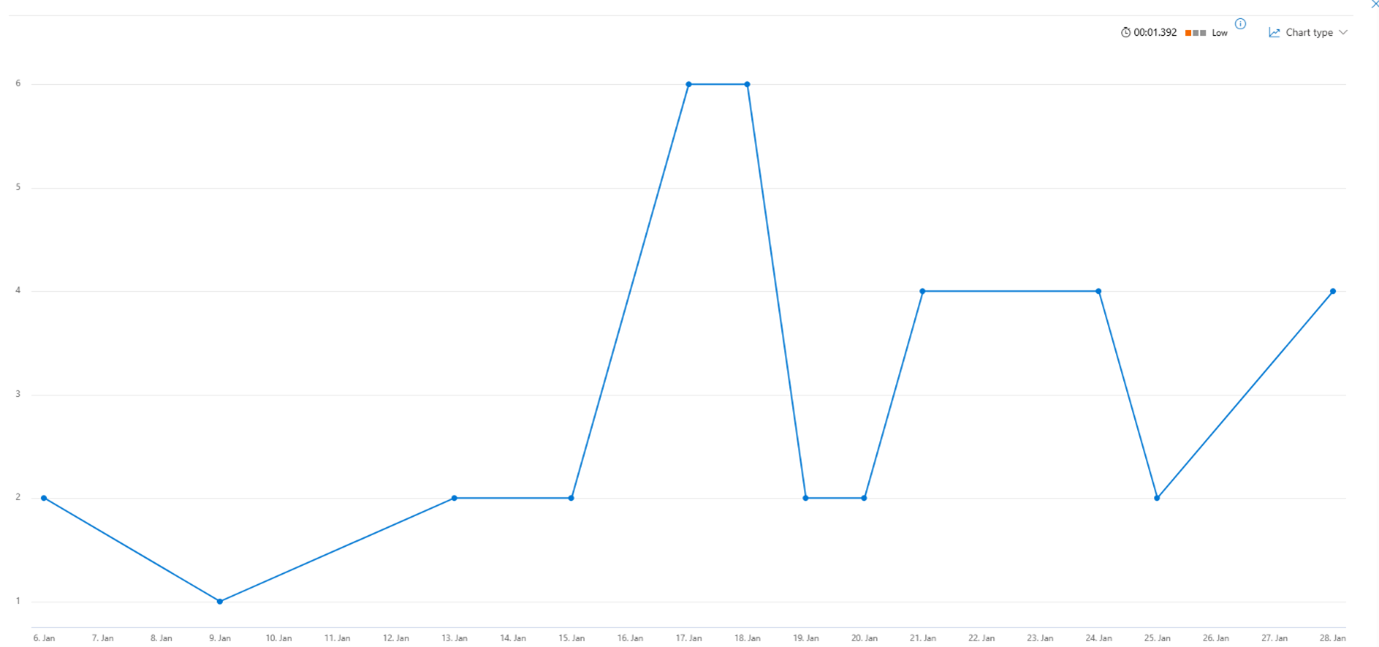
Figure 3: Tenant 1
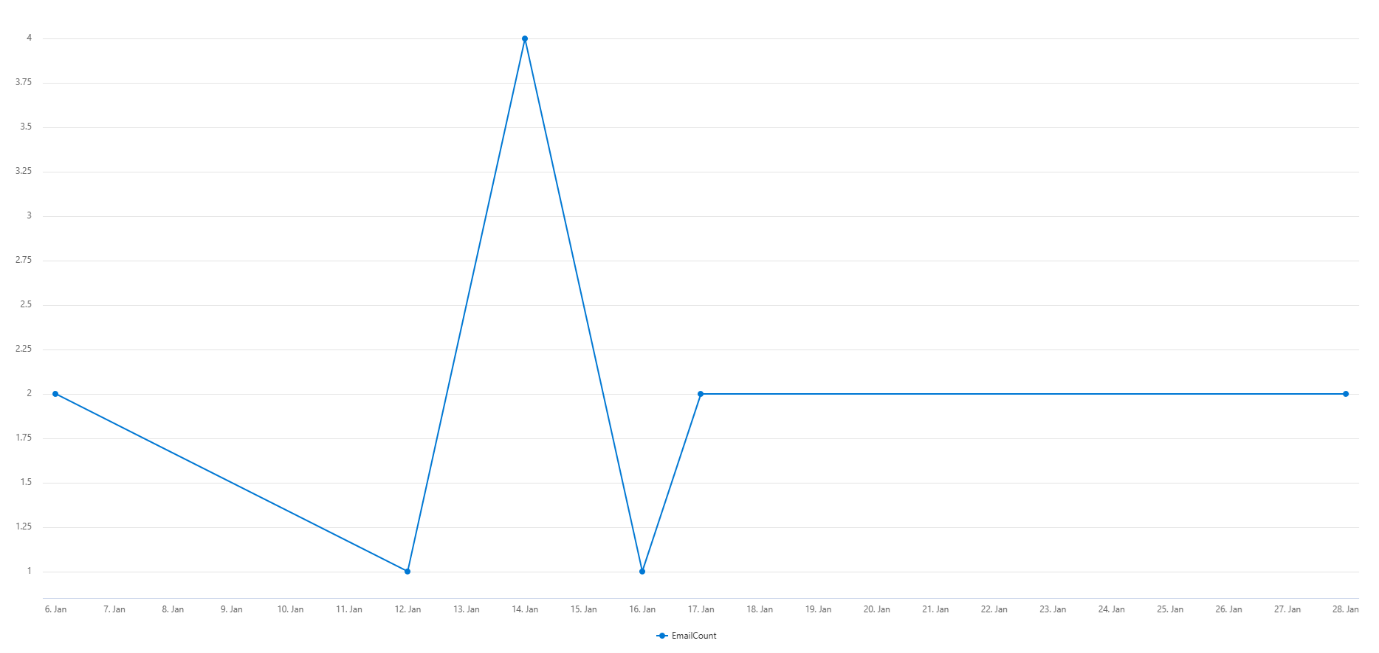
Figure 4: Tenant 2
Based on this analysis, we extracted features consistent with the phishing emails that we observed since January:
| Sender Addresses | Subject Lines | URLs |
| ovetiriqo915@gmail.com | Re: Automatic reply: Assessing Feasibility of a Stay at the Hotel | hxxps[://]xn--dmn-5cd6q[.]xn--bking-jyea[.]xn--cm-fmc/complaint?op_token=eeceba7d-e04f-4857-bb09-3d3e86893748 |
| exezuwojubi98@gmail.com | Re: Automatic reply: Inquiry About Reserving Available Hotel Rooms | hxxps[://]xn--dmn-5cd6q[.]xn--bking-jyea[.]xn--cm-fmc/complaint?op_token=eeceba7d-e04f-4857-bb09-3d3e868fd168 hxxps[://]admin[.]booking[.]com/complaint?op_token=eeceba7d-e04f-4857-bb09-3d3e868fd168 |
| mohumamix28@gmail.com | Re: Automatic reply: Automatic reply: Examining Hotel Room Options | hxxps[://]xn--bking-jyea[.]xn--cm-fmc/complint?op_token=eeceba7d-e04f-4857-bb09-3d3e647289412132 |
| aguleradux82@gmail.com | Re: Automatic reply: Examining Hotel Room Options | hxxps[://]booking[.]com/complint?op_token=eeceba7d-e04f-4857-bb09- |
| wigifudepe22@gmail.com | Re: Automatic reply: Hotel Reservation Availability Assessment | hxxps[://]xn--bking-jyea[.]xn--cm-fmc/complaint?op_token=eeceba7d-e04f-5431-ss31-3d3e423127603 |
| ijatukorepu588@gmail.com | Re: Reviewing Options for Booking a Room at the Hotel | hxxps[://]booking[.]com/complaint?op_token=eeceba7d-e04f-5431-ss31-3d3e423127603 |
| ekaxalizi593@gmail.com | Re: Automatic reply: Checking for Hotel Reservation Openings | hxxps[://]xn--dmn-5cd6q[.]xn--bking-jyea[.]xn--cm-fmc/complaint?op_token=eeceba7d-e04f-4857-bb09-3d3e8pefa119 |
| facufatudob41@gmail.com | Re: Corporate Booking Inquiry | hxxps[://]xn--bking-jyea[.]xn--cm-fmc/complaint?op_token=eeceba7d-e04f-4017-bo09-3d3e08912343211 |
| libovuzib49@gmail.com | Re: Availability Request | hxxps[://]xn--bking-jyea[.]xn--cm-fmc/reserv?op_token=eeceba7d-e04f-22-4371-3d8q7316314352 |
| tuwecos626@gmail.com | Re: Checking Hotel Accommodation Availability | hxxps[://]booking[.]com/reserv?op_token=eeceba7d-e04f-22-4371-3d8q7316314352 |
| cibosud987@gmail.com | Re: Inquiry About Room Availability at Hotel | hxxps[://]xn--bking-jyea[.]xn--cm-fmc/complaint?op_token=eeceba7d-e04f-4857-bb09-3d3e678931243 |
| ovetiriqo915@gmail.com | Re: Hotel Availability Inquiry | hxxps[://]booking[.]com/complaint?op_token=eeceba7d-e04f-4857-bb09- |
exezuwojubi98@gmail.com mohumamix28@gmail.com aguleradux82@gmail.com wigifudepe22@gmail.com ijatukorepu588@gmail.com ekaxalizi593@gmail.com facufatudob41@gmail.com libovuzib49@gmail.com tuwecos626@gmail.com cibosud987@gmail.com | hxxps[://]xn--dmn-5cd6q[.]xn--bking-jyea[.]xn--cm-fmc/complaint?op_token=eeceba7d-e04f-4857-bb09-3d3e86893119 |
Infection Chain 1 - Stage 2 - Partner Phishing Kit
The threat actors utilise a dedicated phishing kit with the sole purpose of capturing credentials for Booking.com partners. The phishing kit is utilising similar frameworks, such as Ajax, as the customer phishing kit, and deploys several defense evasion techniques which are responsible for the low detection rate of many security products. The image below shows how the phishing kit is set up to impersonate the partner login portal for Booking.com.
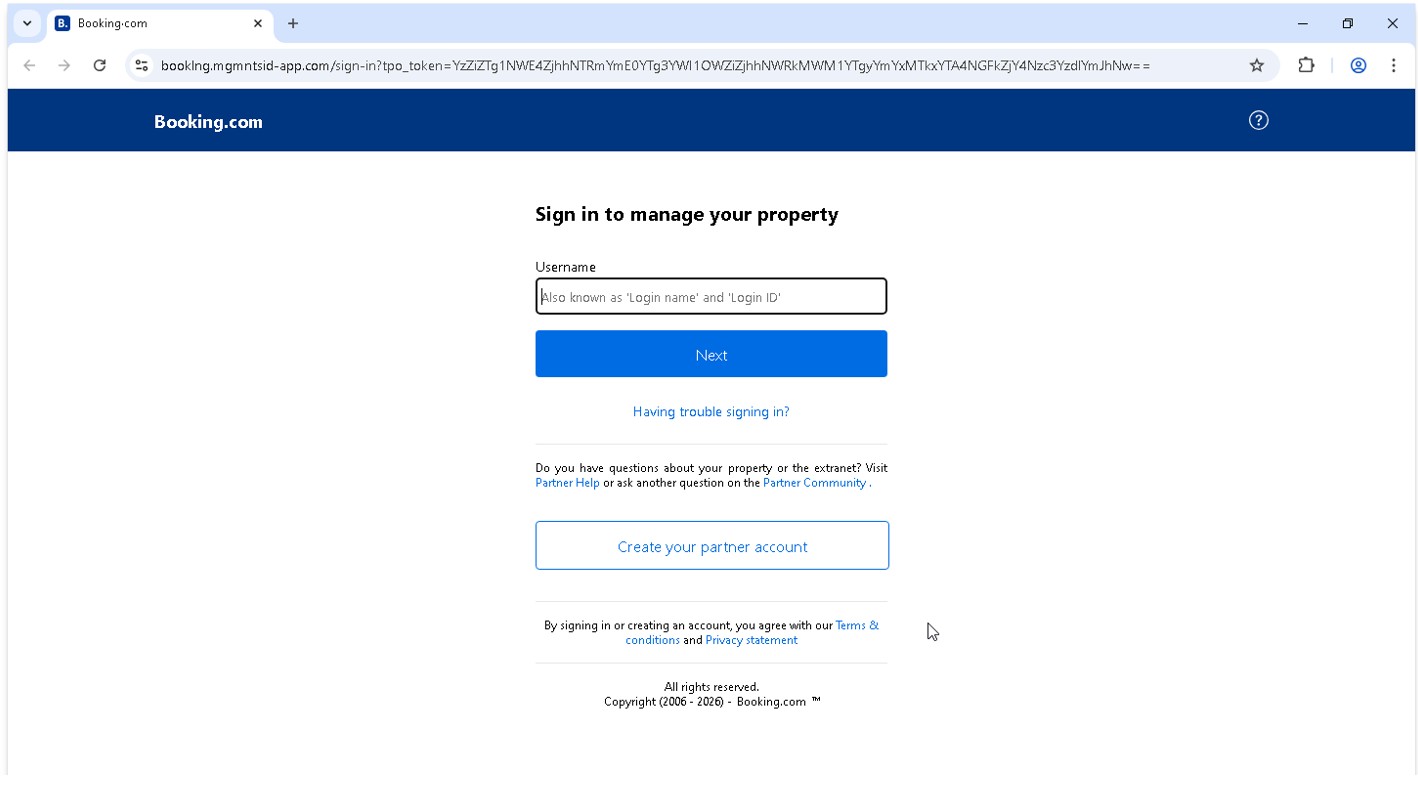
Figure 5 - How the phishing kit is set up to impersonate the partner login portal for Booking.com
All the phishing pages are constructed in the same way, utilising identifiable techniques such as the use of "<span>" HTML tags for each letter of "Booking.com" in reverse.
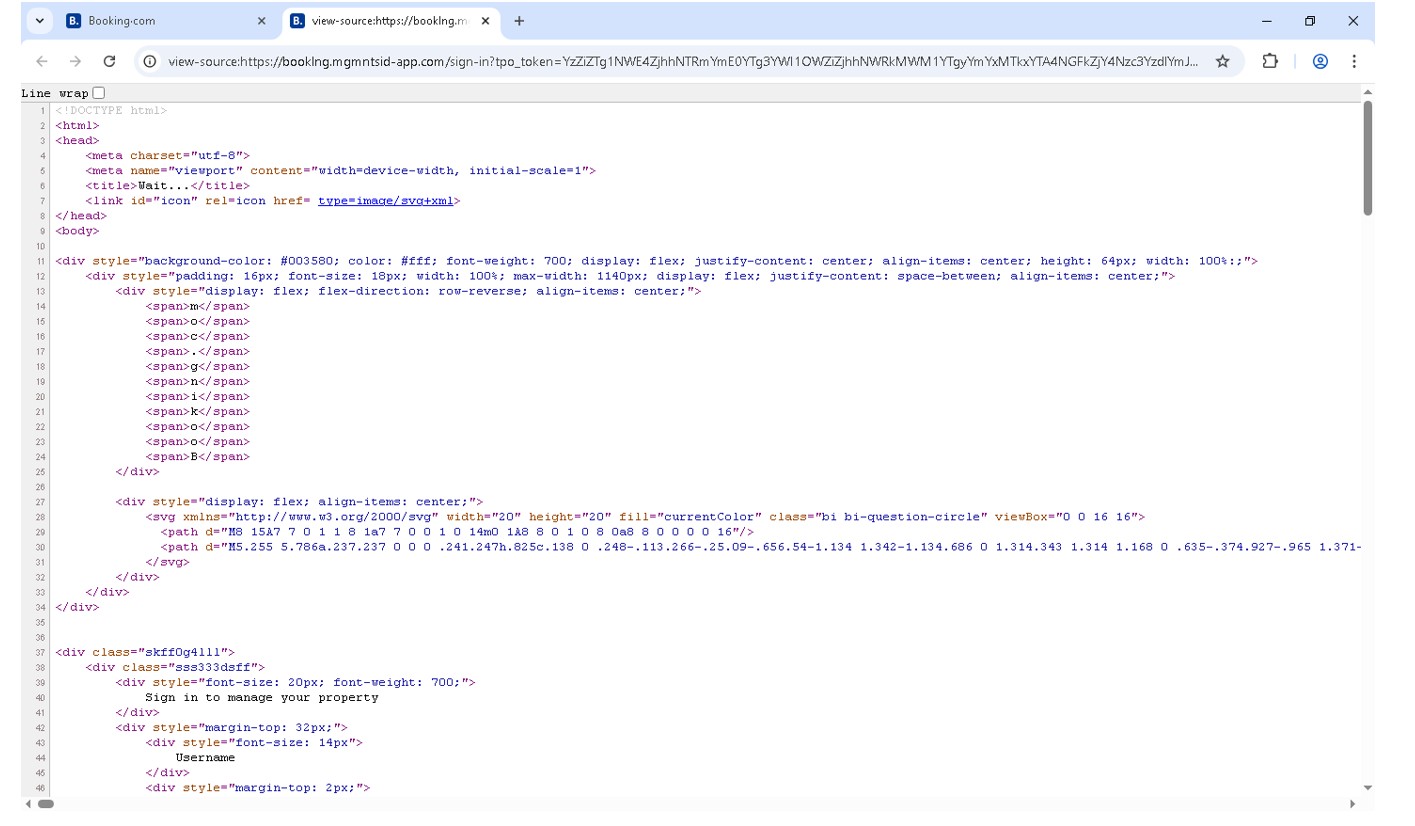
Figure 6 - Inspecting Source of Page
Domains
The threat actors are registering dedicated domain infrastructure for this campaign with very little time between registration and operationalisation. All of the domains we analysed were under 30 days old at the time of this analysis. Additionally, they are all registered with a Registrar called "Hello Internet Corp" and use the ".com" TLD. They utilise Typosquatting (intentional misspellings) and Combo-squatting (combining legitimate brand keywords with generic terms) to deceive users.
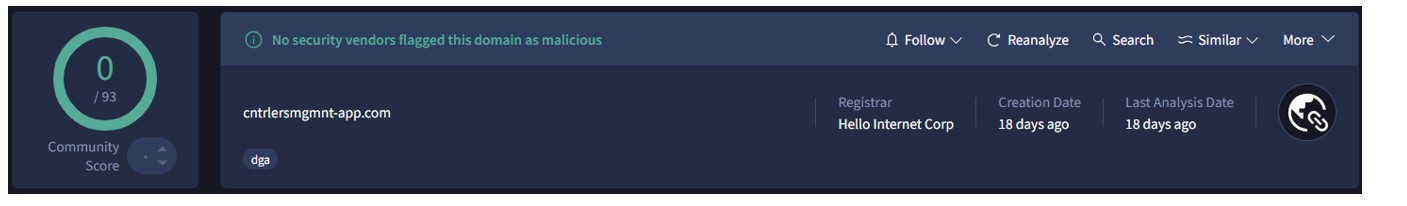
Figure 7 - Domain Analysis
Structural Analysis of Partner Phishing Kit Domains
The domains can be grouped into several "themes" designed to impersonate specific administrative and security functions:
1. Impersonation of "Portal" Services
These domains attempt to mimic corporate portals and internal IT resources:
- extrapp-menus-controls-portal[.]com
- extrapps-poratlcenter[.]com
- extrapp-goctrlenter[.]com
- controlshubportal[.]com
- dashapp-mgmnts[.]com
- mgmnshelp-console[.]com
- gocontrolscore[.]com
2. Identity & Management
A large cluster focuses on "Management IDs" and "Identity Centers,":
- mgmnts-ids-center[.]com
- bbjenbooklng.mgmnts-ids-center[.]com
- mgmntsid-app.com / mgmnts-idapp[.]com
- status-identity[.]com
3. Property & Hotel Management Lures
A subset of the domains target hospitality or real estate sectors specifically:
- app-htl-manage[.]com
- hotels-managers[.]com
- propr-mgmt[.]com
- app-propty-mngmt[.]com
Common Red Flags Identified
The threat actor domains offer several consistent "Low-Reputation" indicators:
| Technique | Example from your list |
| Transposition Errors | poratl instead of portal, mneu instead of menu |
| Character Omission / Garbled Terms | mgmmtsmnntrolsportal[.]com, cntrlersmgmnt-app.com, selmgmnsts-app.com |
| Hyphenation Overuse | go-app-controls-poratl.com |
Defense Evasion
The threat actor infrastructure hosting the partner phishing kit conduct a form of user fingerprinting at the root domain level. This likely applies inspection of source traffic, filtering and redirecting traffic originating from VPN IP subnets. We have repeatedly observed the same level of fingerprinting by threat actors that deploy web pages in front of phishing/MitM kits such as Evilginx. We can assess that the phishing kit is using one or more techniques such as WebGL, Navigator, screen or iFrame checks.
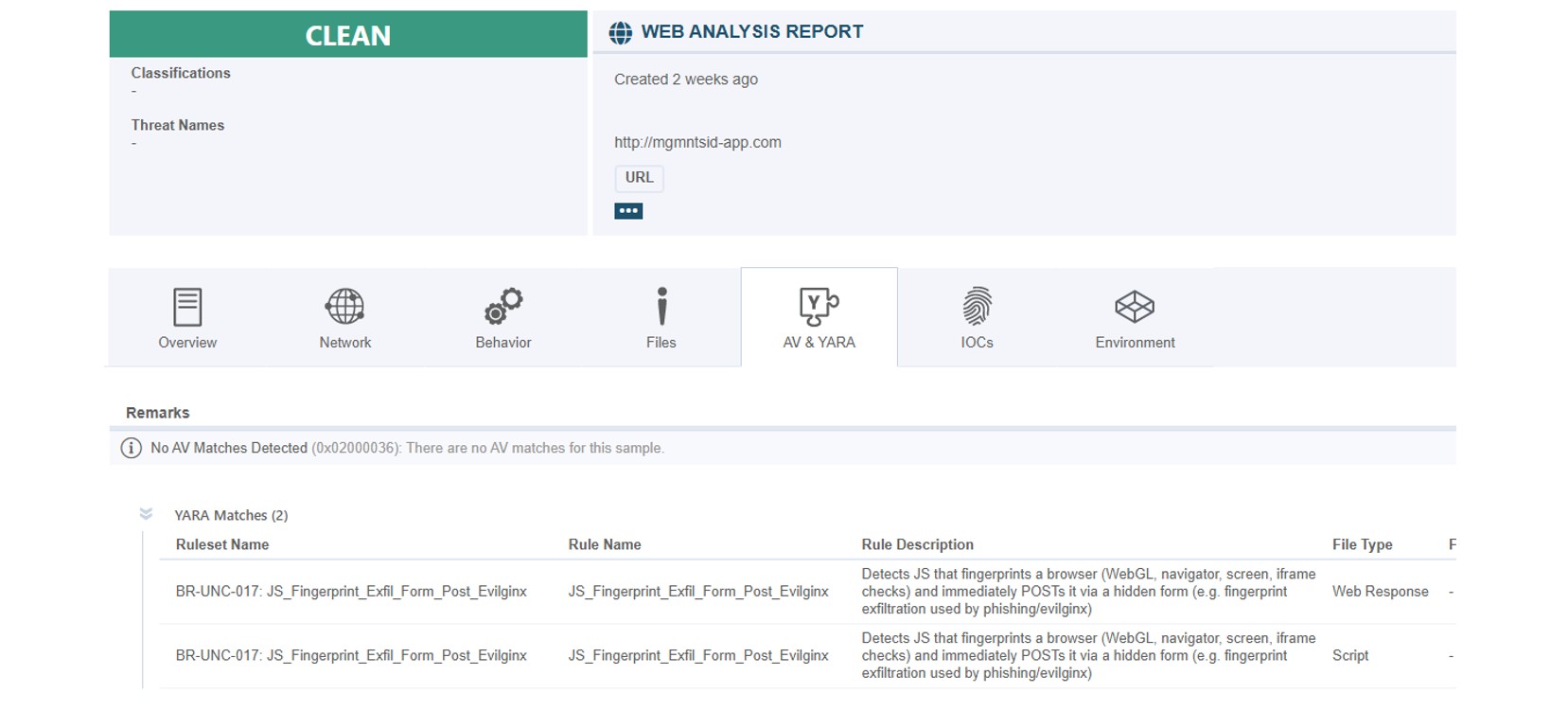
Figure 8 - Web Analysis Report
If the client fails the root domain fingerprinting checks, the phishing kit does not redirect the browser to another domain but merely presents a benign looking web page for fake cleaning companies for hospitality services. During our research we identified at least four fake webpages likely built from web template resources:
- Pristinaarax | Hotel Cleaning & Hospitality Hygiene Services
- Cleanzor | Expert Hotel & Accommodation Cleaning Services
- Shinster | Elite Hotel Cleaning Services for Top Platforms
- DustifyDoti | Premier Hotel Cleaning for Top Airbnb & Booking.com Stays
Figure 8 - Elite Hotel Cleaning Services
Figure 10 - Premier Hotel Housekeeping & Linen Management
Lastly, if the browser passes the phishing kit checks, the end user is redirected to the fake Booking.com partner login portal which is hosted on a consistent subdomain: "bookling", with the letter "L" replacing the "I" in "booking". Additionally, all URL paths contain the string "sign-in/?tpo_token=" followed by a unique UUID.
Tracking opportunities
- Title/favicon of benign cleaning webpages
- "booklng" subdomain patterns
- URL path patterns matching "sign-in/?tpo_token="
- Gmail email addresses sending complaint links to service desk/reservation mailboxes
If the threat actors are successful, they will have captured the Booking.com login credentials in order to harvest customer booking information.
Infection Chain 2 - Stage 1 - Customer Phishing
Once the threat actors have compromised the hotel users and gathered the partner Booking.com credentials, they steal the booking information for the target hotel by logging into the Booking.com platform and exfiltrating the data, including customer names and booking information. We assess it is possible that they use "Ghost paired" business accounts on WhatsApp, likely to leverage the blue verified status to boost the trustworthiness of the lures.
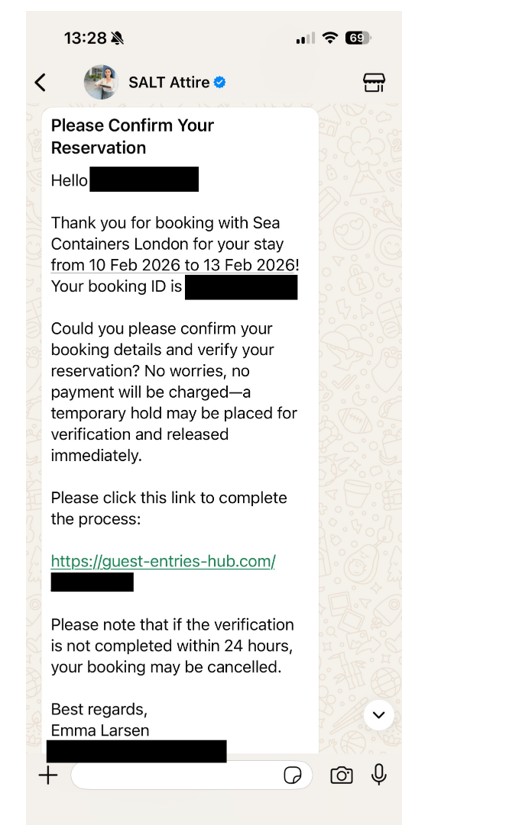
Figure 11 - Whatsapp message from a different account
This WhatsApp message, despite coming from a completely different account and where the user is unlikely to expect a WhatsApp message from the hotel, is very convincing, with accurate booking information (E.g. date and booking reference ID), this would give the customer an inherent level of trust to the message, paired with the sense of urgency that within 24 hours they will lose their booking. The URLs appear to have similar structural properties, using similar words and hyphens as the partner domains. These are followed by a capitalised alphanumeric 8-character string as the URL path.
The threat actors continue to utilise the previously reported phishing kit in the "I Paid Twice" campaign, which uses the same Ajax framework and auto populates the stolen booking details. The phishing kit also sits behind a Cloudflare captcha page and uses domains that, from those analysed, are registered with the registrar, Dynadot:

Figure 11 - Cloudflare Captcha Page
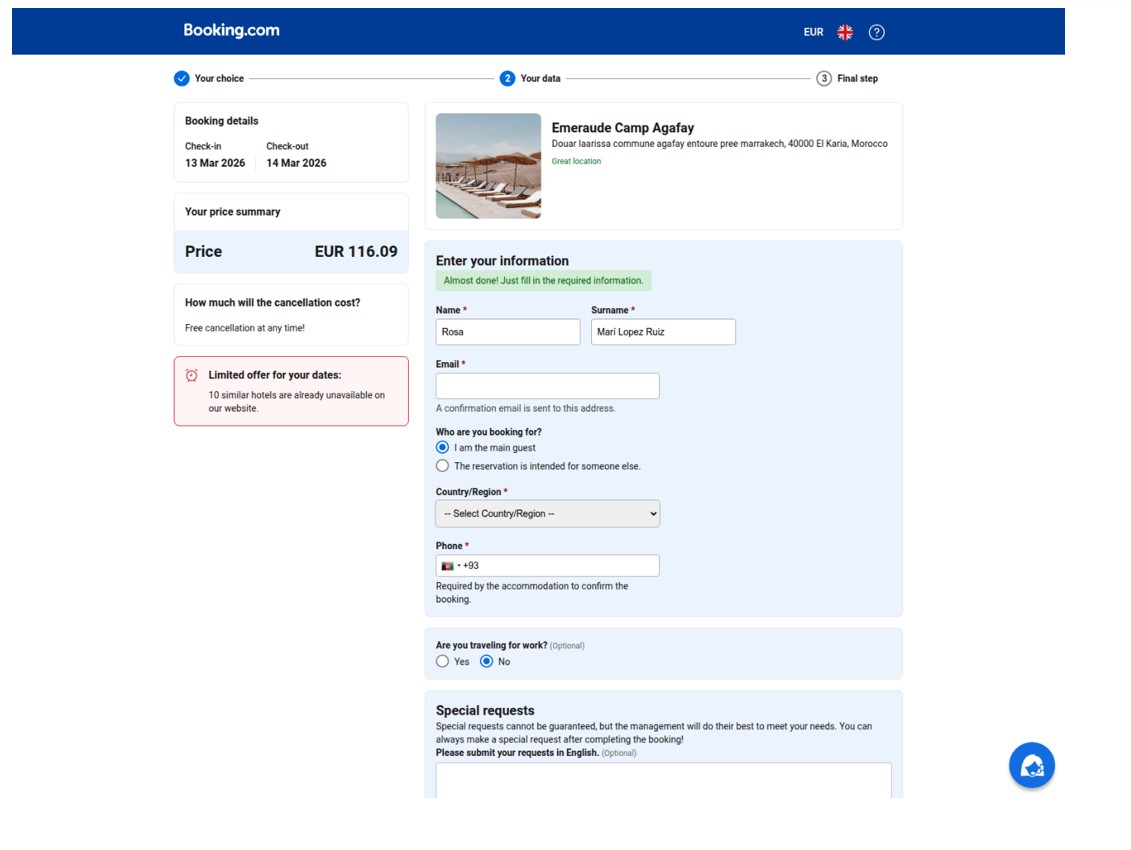
Figure 12 - Mimic of Booking.com brand
The impact of this campaign ultimately sits with the public, customers of the hotels that have had their Booking.com credentials stolen. Unless robust detections are in place to detect early attack activity, organisations may not know they are compromised until it is reported by the customers themselves. The threat actors are financially motivated, looking to take advantage of the elevated trust and reputation of the hotels and booking platforms, and aiming to steal money using two dedicated phishing kits designed to mimic the Booking.com brand.
Assessment and Attribution
This is a long running campaign targeting Booking.com, it's hotel partners and their customers. We did not observe the previously reported activity of threat actors using ClickFix as the initial access vector into enterprise networks to steal credentials; instead, they leverage newly generated Gmail addresses and domains to deploy a dedicated partner phishing kit, which appears to be successful in its delivery and execution.
We have deployed several detection analytics to identify early lure activity from the threat actors, through to the decoy pages and phishing pages for the partner and customer Booking.com portals. We have allocated this intrusion set, BR-UNC-030, to track activity associated with the partner phishing kit that we've observed targeting hotels since early January 2026.
Infrastructure associated with previous "I Paid Twice" activity, such as the commercial TDS, appear to have subsided and it's possible that the same threat actors have moved to the dedicated phishing kit instead. Additionally, within the customer phishing kit, we identified the "Russian" word for "Error" within the code comments: //console.error("Ошибка: " + textStatus + ", " + errorThrown); suggesting that the developer of the customer phishing kit is of Russian origin.
Detections
Detection Rules |
| YARA: Booking.com Partner Phishing Kit |
| UrlScan_Jan26_Booking.com_Customer_Phishing_Kit |
| YARA_Jan26_Customer_Phishing_Kit |
| Infra_Jan26_Partner_Booking_Domains |
| VT_Jan26_Partner_Booking_Domains |
| KQL_MDE_Partner_Booking_Subdomains |
worldweb-mgmnts-app[.]com
webhome-mngr[.]com
webgo-appmgmntt[.]com
status-identity[.]com
st-mgmnts-apply[.]com
reviwres-reportes[.]com
property-vrf[.]com
portallgate-mgmnts[.]com
partner-hubs[.]com
partner-controlapp[.]com
mngmntsapplyacontrol[.]com
mngmnts-apps-cntr[.]com
mgnmts-controls-menuapp[.]com
mgmtsapps-controls[.]com
mgmts-portallsapp[.]com
mgmtns-controls-poratl[.]com
mgmntswebhome-app[.]com
mgmntsweb-home[.]com
mgmntss-apps-control[.]com
mgmntsho-controlapp-menu[.]com
mgmntsgocontrolscenter[.]com
mgmntsgate-console[.]com
mgmntsgate-apps[.]com
mgmntsfconfitol-app[.]com
mgmntscoreportal[.]com
mgmntscorecontrols[.]com
mgmntscontrolshub[.]com
mgmntscontrol-app[.]com
mgmntscons-meapp[.]com
mgmntscntorlsportal[.]com
mgmntsapps-gate[.]com
mgmntsapplyyfy-menu[.]com
mgmntsapplymenu[.]com
mgmntsappcontrol-info[.]com
mgmntsappciontols[.]com
mgmntsapp-console[.]com
mgmntsadmcontrol[.]com
mgmnts-webhome[.]com
mgmnts-web-control[.]com
mgmnts-shieldapp[.]com
mgmnts-sec-app[.]com
mgmnts-portal-app[.]com
mgmnts-mneu-controls-portal[.]com
mgmnts-menus-poratl-apps[.]com
mgmnts-menuapp-centers[.]com
mgmnts-menu-contrlos-go[.]com
mgmnts-ids-portal[.]com
mgmnts-ids-menu[.]com
mgmnts-ids-controls[.]com
mgmnts-ids-center[.]com
mgmnts-idapp[.]com
mgmnts-hostify-app[.]com
mgmnts-homeaccses[.]com
mgmnts-gocontrol-app[.]com
mgmnts-ctrlos-menu[.]com
mgmnts-controls-app[.]com
mgmnts-controlgo-app[.]com
mgmnts-contorls-center[.]com
mgmnts-contlrols-apps[.]com
mgmnts-cntrls-app[.]com
mgmnts-appshield[.]com
mgmnts-apps-mneu-portal[.]com
mgmnts-appme-control[.]com
mgmnts-apply-con[.]com
mgmnts-applportalme[.]com
mgmnts-appjoin[.]com
mgmnts-appid[.]com
mgmnts-appcontrolme[.]com
mgmnts-appcentralsap[.]com
mgmnts-appcenterme[.]com
mgmntranet-app[.]com
mgmnt-appliteme[.]com
mgmnstcontrols-app[.]com
mgmnshelp-console[.]com
mgmns-tsmenusportal[.]com
mgmmtsprodesk[.]com
mgmmts-mneu-controls-center[.]com
mgmmts-controls-mneu-portal[.]com
mgmmts-controls-menu-go[.]com
mgmmts-contrlos-portals[.]com
mgmmts-apps-controls-poratl[.]com
mggmnts-portalgate[.]com
menusprodesk[.]com
menus-contrlosctergo[.]com
menumgmnts-items[.]com
menucoreportal[.]com
menuapp-mggmnts[.]com
menu-mgmnts-apply[.]com
menu-mgmnts-appl[.]com
managmntscenter[.]com
litemgmnts-app[.]com
liteapp-mgmntsgo[.]com
id-manageapp[.]com
homemmgmnts-control[.]com
homemgmnts-center[.]com
homemgmmnts-app[.]com
home-mgmntsapp[.]com
home-controlmgmnts[.]com
gomgnts-appcontrols-menu[.]com
gomgmnts-appso[.]com
gomgmnts-applyfy[.]com
goconsole-mgmnts-app[.]com
go-menus-controls-center[.]com
go-menu-controls-cetner[.]com
go-controls-poratl-center[.]com
go-contrlos-menu-portal[.]com
go-apps-mneu-portals[.]com
go-app-controls-poratl[.]com
gatesmgmntts-apps[.]com
gateapps-mgmnts[.]com
extrapps-poratlcenter[.]com
extrappprodesk[.]com
extrappcolosporatl[.]com
extrapp-mneuporcontrols[.]com
extrapp-mneu-controls-center[.]com
extrapp-menus-controls-portal[.]com
extrapp-go-controls-center[.]com
extrapp-controls-poratl[.]com
extrapp-contrlos-portal[.]com
dashmenu-mgmnts[.]com
dashapp-mgmnts[.]com
controlssyscenter[.]com
controlsmgmntss-app[.]com
controlsmgmnts-apply[.]com
controlsmenucore[.]com
controlsmenu-mgmts[.]com
controlsdeskportal[.]com
controls-mneuportalcntr[.]com
controlersapp-mgnnts[.]com
controlapply-mgmnts[.]com
control-mgmnt-apps[.]com
contrcentermneuportal[.]com
console-mgmnts-app[.]com
consmgmnts-appme[.]com
cntrlsmgmnts-app[.]com
cntrlersmgmnt-app[.]com
centergate-mgmnts[.]com
center-cntrlmgmts[.]com
booklng[.]mgmntsgate-console[.]com
appst-mgmnts-controls[.]com
appsgates-mgmnts[.]com
apps-mgmntsgate[.]com
applyfy-mgmnts-menu[.]com
app-partners-portal[.]com
app-mgmnts-menu[.]com
app-helpers-mgmnts[.]com
admcontrol-mgmts[.]com
adm-mgmtsapp[.]com
zone-mgmnt-app[.]com
xweb-mgmnt-app[.]com
worldwebs-mgmnt-app[.]com
worldmgmntportal[.]com
world-mgmnts-control[.]com
wmgmnt-web-gate[.]com
wmgmns-portal-app[.]com
wegso-mgmntsapps[.]com
webmgmnt-portal-app[.]com
webhome-mgmnts[.]com
webbmgmnt-portal[.]com
webbmgmnt-app[.]com
web-mgmnt-zone[.]com
sweb-mgmtn-app[.]com
shst-mgmnt-app[.]com
propty-managments[.]com
post2mgmnt-app[.]com
portalapp-mgmnt-acc[.]com
mngtnysmenu-wapp[.]com
mgmtsapply-control[.]com
mgmtns-pportalapp[.]com
mgmntts-apph-portal[.]com
mgmntts-apph-center[.]com
mgmntt-webhost-center[.]com
mgmntstranets-app[.]com
mgmntsss-web-center[.]com
mgmntsscontrolers-app[.]com
mgmntssapp-controll[.]com
mgmntss-appcenter[.]com
mgmntss-access-web[.]com
mgmntshosapp-menu[.]com
mgmntshome-center[.]com
mgmntscontrolers-menu[.]com
mgmntscenter-portla[.]com
mgmntsappportal[.]com
mgmntsappmenu-info[.]com
mgmntsapphome-center[.]com
mgmnts-web-gate[.]com
mgmnts-hostt-portal[.]com
mgmnts-host-center[.]com
mgmnts-gate-portal[.]com
mgmnts-contolhst-app[.]com
mgmnts-applyweb[.]com
mgmnts-apply-app[.]com
mgmnts-appcontorlers[.]com
mgmnts-app-center[.]com
mgmnt2host-app[.]com
mgmnt-wwwgate[.]com
mgmnt-wwwcenter[.]com
mgmnt-wwwapp[.]com
mgmnt-wwwaccess[.]com
mgmnt-today-portal[.]com
mgmnt-hosthgate-app[.]com
mgmnt-host-portal[.]com
mgmnt-acesc-app[.]com
mgmnt-accept-portal[.]com
mgmmts-app-controls-cetner[.]com
menu-mgmnts-controls[.]com
me-mgmnts-portal[.]com
mamgmnt-web-portal[.]com
lweb-mgntm-app[.]com
lweb-mgmnt-app[.]com
lets-mgmnts-center[.]com
let-mgmnts-app[.]com
humgmnts-worldapp[.]com
hostgate-mgmnt-app[.]com
host2mgmnt-center[.]com
hmgmntcs-appcount[.]com
gw-mgmnt-acceptapp[.]com
goweb-access-mgmnt[.]com
go-mamgmnt-center-app[.]com
go-access-mgmnt[.]com
ghst-mgmnt-app[.]com
gate-mgmntt-portal[.]com
gate-mgmnt-center[.]com
controls-appmgmnts[.]com
controlersapp-mgmnts[.]com
control-mgmnts-cecontrol[.]com
control-app-mgmntss[.]com
clappl-mgmnts-control[.]com
center2mgmnt-app[.]com
center-mgmnt-gate[.]com
booklng[.]worldwebs-mgmnt-app[.]com
booklng[.]mgmnt-host-portal[.]com
booklng[.]goweb-access-mgmnt[.]com
asmgmnts-controlsapp[.]com
arcmgmnt-center-app[.]com
applyfy-mgmnts-world[.]com
appfile-mgmnts-portal[.]com
appcl-mgmnts-control[.]com
appcenter-mgmgmnts[.]com
app-proprtyhub[.]com
app-partner-portel[.]com
app-mgmntts-contorl[.]com
app-mgmnts-portal[.]com
app-mgmnts-center[.]com
app-mgmnts-access[.]com
admapp-mgmnts[.]com
accept-mgmnt-center[.]com
contrlogo-appsportal[.]com
goportalhub[.]com
ctrlosenu-poratlgo[.]com
bbjenbooklng[.]mgmnts-ids-center[.]com
controlscoreportal[.]com
mgmmtsmen-poratlapps[.]com
mgmmtsmnntrolsportal[.]com
mgmntsprocenter[.]com
controlshubportal[.]com
extrapp-goctrlenter[.]com
menuappportalcore[.]com
menusapp-porantrols[.]com
controls-poratlnus[.]com
mgmntsid-app[.]com
selmgmnsts-app[.]com
app-mgmntsre[.]com
gocontrolscore[.]com
mgmntsapsgate[.]com
web-mgmnt-portal[.]com
parnter-portals[.]com
gweb-point-mgmnt[.]com
prpty-portal[.]com
webcenter-mgntm[.]com
web-mgnmnt-app[.]com
app-propty-mngmt[.]com
webmgmnt-portal[.]com
app-htl-manage[.]com
hotels-managers[.]com
secapp-mgmt[.]com
propr-mgmt[.]com
hotl-app[.]com
ctrlosenu-poratlgo[.]com
extrapp-contrlos-portal[.]com
References

.jpg?sfvrsn=4c6fcb96_1)



