“Threat-informed defense is the systematic application of a deep understanding of adversary tradecraft and technology to improve defences.” ( MITRE Engenuity – Center for Threat-Informed Defense)
To delve a little deeper into this, we consider a threat-informed defence strategy to go all the way from the board and risk management, through to security operations. MITRE Engenuity focus on the uses within detection engineering and security operations, but we apply the concept to inform strategic decision making as well as ensuring actionable intelligence is delivered in near real-time (or at least timely) to drive continuous improvement and validation of capabilities.
Fundamentally, is a holistic approach to risk management and security operations that builds a solid foundation informed by real threat actors and their tradecraft. In this blog, we’ll dive further into how a threat informed defence strategy differs from conventional approaches, how to implement it, and how it benefits your organisation.
For more on what a threat-informed defence strategy is – and a real-world example of how to implement it – see our Q&A with Mazars.
How Does Threat Informed Defence Compare to Traditional Approaches?
If we look at conventional security operations, they are often inspired by an IT helpdesk philosophy. They treat security incidents and events as rare and abnormal, purely relying on SIEM platforms to detect threats. Threat intelligence is sometimes consumed – though it often isn’t at all – and it isn’t used to inform the organisations’ defensive strategy. This approach fundamentally limits the “value” of security operations at simply triaging events and performing a limited amount of investigation afterwards; it is reactive rather than proactive.
We have seen more organisations moving towards this proactive approach in recent years. In our 2024 research amongst UK CNI, 87% of respondents reported that they have implemented, or will implement within the next 24 months, threat hunting and cyber threat intelligence. Referring to the ‘maturity scale’ shown in the diagram below, this should put most organisations closer towards the automation or threat informed side of the spectrum.
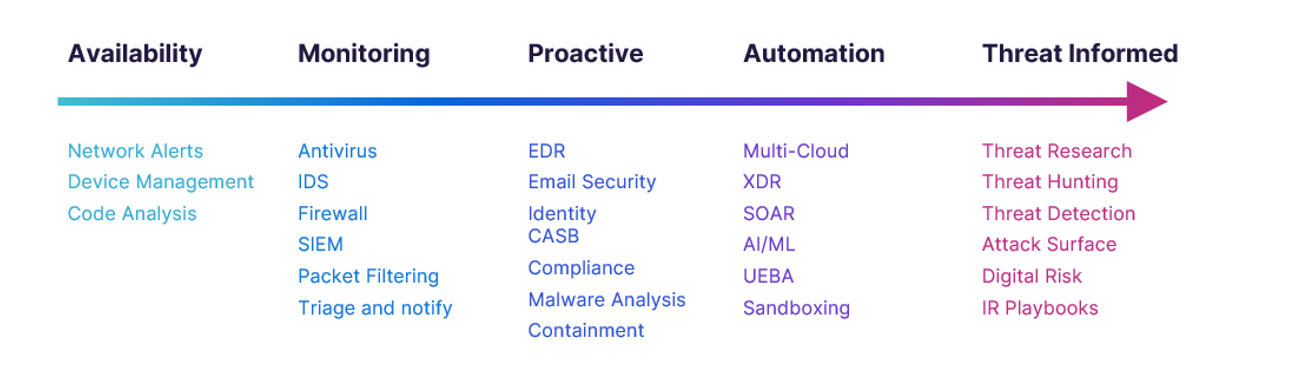
However, despite these reported improvements, we still see many organisations failing to meaningfully integrate threat intelligence capabilities. It is all too common to see organisations that collect threat intelligence without incorporating it into their strategy. It is also common for organisations to buy ‘off-the-shelf’ threat intelligence that provides outdated and publicly available information or insights that aren’t relevant to their sector or geography. Organisations that aren’t investing in the right type of threat intelligence and making practical use of it are moving in the right direction but won’t realise the benefits of a threat informed defence.
What Are the Benefits of Threat Informed Defence?
By systematically applying a deep understanding of adversary tradecraft and technology and viewing the enterprise through the lens of an adversary, including the analysis of the campaigns actively impacting your organisation, threat informed defence helps a security team gains critical insights on how to prioritise security operations and investments. This shift in perspective helps the team clearly see how adversaries could, and are, trying to exploit their organisation’s assets.
Understanding the Threat Landscape
By taking the approach of adversarial and security research, we gain a real understanding of who the relevant threat actors are, how they operate and how we can identify them within our environment. We can, for example, observe if they are leveraging available tooling such as CobaltStrike or Mimikatz or if they are leveraging CVE’s for remote access or simply living off the land with their use of Windows binaries.
Continuous Improvement
Better understanding the threat landscape allows us to test what our security operations can and can't do right now and evaluate what we need to be able to do in the future. The key is emulation and testing. We can emulate a specific adversary, of which we’re trying to improve and demonstrate resilience from, so that we can test our capabilities, which allows us to drive improvements. This leads to a cycle of continuous improvements across people, technology and process and moves our capabilities forward.
Demonstrate Value to the Board
We can also use threat intelligence to inform the key risks to our organisation and then present them to the board to encourage focused investment. By being able to demonstrate that we’ve tested our capabilities, and provide evidence that our operations aren’t currently able to do A and B against those adversaries, we can implement the changes and influence budgets and planning to protect our organisation from these newly discovered threats or clearly articulated risks.
How to Build a Threat Informed Defence
As I’ve highlighted above, building a threat informed defence isn’t simply buying a threat intelligence product. It requires various investments in cyber security involving people, processes, and technology that can be effectively incorporated into security plans. It is worth remembering that implementing this can be done via a phased approach, as shown in our Mazars webinar.
This webinar provides a more detailed view on how to take this phased approach. However, for a quick overview, here is a summary of each of the three stages.
Crawl
For organisation coming from a less mature position, they should focus on where they can rapidly build early maturity. They should focus on quick wins that deliver a fast return on investment, leveraging open source intelligence, such as MITRE Engenuity’s Top Att&ck techniques to guide activities and budgets for security products and consider partnering to achieving 24/7 managed detection and response.
Walk
From here, they can look to how they can expand and customise their security operations. This includes the onboarding of custom third-party technologies, performing threat hunts, and creating customised automations and incident response playbooks. They will also benefit from intelligence integration focusing on observables.
Run
With these baselines established, the organisation is now ready to continually validate and optimise. This is the time for them to focus on: prevention, control mapping, targeted intelligence, continual research, proactive content, validation, and continual improvement.
Above all, a threat informed defence must be built on good foundations. It is not something you can merely go out to buy, deploy and run instantly. It's something that has to be achieved over time.





