‘Risk owners’ are responsible for managing assessments. They may rely on IT risk assessment frameworks such as NIST Cybersecurity Framework (CSF) or ISO/IEC 27005.
What is Risk?
Risk, in the context of IT, refers to the potential for loss or disruption that could affect information systems or processes. These risks can stem from various factors, including cyber attacks, technical failures, human errors or natural disasters.
A risk is a combination of a vulnerability and a threat resulting in an impact. For example, an operating system that is out of date (a vulnerability) could be exploited by an automated bot (a threat) to gain access to sensitive data on a system.
It is also worth distinguishing between inherent risk residual risk. Inherent risk is the amount of risk before risk reductions are made, and residual risk is the amount of risk following these reductions.
How is Risk Measured?
Risk is measured as a combination of likelihood and impact. After identifying a risk, the next steps are to either accept the risk, transfer the risk, or implement mitigations to reduce it. The purpose of these mitigations is to lower the residual risk (the risk that remains after mitigations have been applied) to an acceptable level.
It is extremely uncommon and often far too costly for a risk to be completely eliminated so some residual risk will always persist. The goal is to minimise this residual risk to an acceptable level, which is defined by the organisation and referred to as ‘risk appetite’.
Risk appetite is going to look different for every organisation and defining risk appetite allows organisations to understand where actions need to be taken. For example, if an organisation's success revolves around proprietary information, they will have less appetite for risks resulting in data loss. The definition of risk appetite must factor in business risk and operations, and must be evaluated regularly.
Who is Responsible for Managing Risk?
There are different individuals and groups in play when it comes to managing IT risk. There should always be a risk owner or risk owners. These are individuals or groups assigned responsibility for identifying, assessing, and addressing specific risks within their domain.
The duties of a risk owner include evaluating the level of risk, defining and actioning appropriate mitigation strategies, and ensuring the level risk sits within the organisations risk appetite. Other individuals include:
- Risk identifier (raiser)
- Risk action owner
- Risk Owner
For oversight, situational awareness and visibility, a Responsible, Accountable, Consulted & Informed (RACI) model / matrix can be developed.
- R = Responsible (does the work)
- A = Accountable (ultimate ownership – usually the Risk Owner)
- C = Consulted (provides input / another perspective)
- I = Informed (kept in the loop)
Why are IT Risk Assessments Important?
In the context of IT risk, it is often easy to lose sight of the bigger picture. Understanding the relationship between IT risk and business risk is a key contextual consideration when evaluating levels of risk and selecting appropriate mitigations.
IT risks have real impacts on business and can materialise risks to the core business. For example, if customer data is leaked, the organisation loses reputation and therefore future customers. The link between reducing the risk of data leaks and reducing the risk of reputational damage is an example of how IT risk and business risk are intrinsically linked.
How to Conduct IT Security Assessments
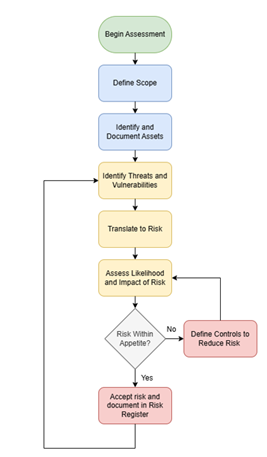
Conducting an IT security assessment involves several steps:
- Define the Scope of the Assessment: Defining the scope of an assessment is essential to ensure clarity, focus, and alignment with the objectives of the risk evaluation. It sets the boundaries for what will and won’t be included in the assessment. By defining the scope, the risk assessment becomes a targeted and efficient process that yields actionable insights.
- Identify and Document the Assets: Understanding and having visibility of your assets is the first real step to understanding your risk profile. An asset may be something physical, like an office space or data centre, something digital like a proprietary algorithm, or even something human.
- Identify Threats and Vulnerabilities: For each of the identified assets, consider the threats and vulnerabilities associated with it. A threat is a potential external event that could damage an asset, whereas a vulnerability is a weakness or flaw that could be exploited by a threat.
- Translate to Risks: Once the assets are defined and the threats and vulnerabilities identified, defining the relevant risks at a high level is the next step in the process.
- Assess the Likelihood and Impact of the Risks: To be able to assess the risks, we must understand the level of them. We can measure this by looking at both their likelihood of occurring and the potential impact they would have on your business. This process should be pre-defined and can be subjective, or objective based on a defined set of metrics. Each risk should have a defined risk level.
- Compare the Level of Risk to Risk Appetite: To understand how to address a risk, an organisation must first understand if it sits within their risk appetite or not. This could be a decision from the risk owner or determined by following a predefined set of rules.
- Define Controls to Reduce the Risk: If a risk falls outside of your organisation’s risk appetite, the risk will either need to be transferred or reduced to an acceptable level. This could be done through implementing controls. Once defined or implemented, the level of risk must be assessed again to see if it now falls inside your organisation’s risk appetite.
- Accept and Track the Risk: Once the level of inherent or residual risk is deemed to be within the organisation’s risk appetite, your organisation can now accept this risk. However, it must be documented so it can be tracked and revisited as appropriate. This is often performed in a risk register, which is a large collection of risks. It is vital that this risk register is revisited on a periodic basis to ensure the residual risks don’t fall outside of the organisation’s risk appetite.
IT Risk Assessment Frameworks
Organisations can draw on a wealth of international and sector-specific standards to guide their approach to risk management. Rather than relying on a rigid, step-by-step process, many organisations find value in adopting frameworks that offer both structure and flexibility. Some of the most widely used frameworks include:
- NIST Cybersecurity Framework (CSF)
- ISO/IEC 27005
- COBIT (Control Objectives for Information and Related Technologies)
These frameworks help ensure you meet best practices and regulatory requirements, all while leaving room for a tailored risk assessment strategy.
Bridewell’s Cyber Security Audit Team
Effective IT risk assessment is essential for managing and mitigating risks within any organisation. Bridewell stands ready to assist, offering the expertise and support needed to help you navigate the complexities of IT risk assessment with confidence.


.tmb-6_col_resi.jpg?sfvrsn=7fe77a4a_3)


