What is Intelligence?
Cyber Threat Intelligence provides organisations with evidence-based insights about potential cyber threats, equipping them with the knowledge they need to proactively strengthen their defences and make informed security decisions.
Why is Cyber Threat Intelligence Important?
Cyber threat intelligence (CTI) is important as it helps you take a proactive approach to cyber security – keeping your organisation ahead of potential attackers by informing you which threat actors are likely to target you, their motivations for doing so, and the tools, tactics and procedures (TTPs) they’re likely to use.
Some of the key benefits of CTI include:
- Informed Decision-Making: Prioritise resources and response capabilities through actionable insight.
- Proactive Defence: Anticipate and prepare for potential threats, improving response times in the event a security breach does occur.
- Prioritise Vulnerability Management: Security teams can identify and address vulnerabilities before they’re exploited by potential attackers and improve overall cyber security posture.
- Reduced Downtime: By successfully preventing cyber attacks, businesses save on the time and costs associated with downtime and repairs.
- Incident Response: In the event of a breach, CTI provides additional context about threats, their attack flows, TTPs, victimology, and infrastructure. This promotes quicker and more accurate response tactics.
- Threat Hunting: Informing or executing threat hunts to identify active or historic threats/attacks that have infiltrated your networks.
- Security Testing and Control Validation: Providing detailed information of adversary procedures that can be used to emulate real world attacks.
Types of Cyber Threat Intelligence
There are several types of cyber threat intelligence:
- Strategic Intelligence: What are the key threats to our business? Which business units and are most at risk? Have our security investments positively reduced the risk of threats we are tracking?
- Operational Intelligence: What campaigns, or intrusion sets are active in our industry? If APT41 compromised our organisation, what assets would it target?
- Tactical Intelligence: What are the prioritised TTPs used by our top threats. What indicators are available to search for the threat actor behind an active incident.
- Technical Intelligence: Often structured threat information such as STIX 2.1 or indicators of compromise (IOCs) such as IPs, domains, hashes being provided for machine to machine communication. Usually relating to the use of a threat intelligence platform (TIP).
Cyber Threat Intelligence Stakeholders
CTI requires a collaborative and coordinates effort across various business units and teams. Below are some examples of stakeholder roles that can benefit from a CTI program rollout:
| Profession | CTI Use Cases |
| Security Analyst | Enriches alerts and associated entities from SIEM to reduce false positives and speed up triage and investigation workflows. |
| Security Operations Centre (SOC) Team | Prioritises incidents based on impact and risk. They often have a priority focus on critical threats that could affect the organisation. |
| Computer Security Incident Response (CSIRT) Team | Speed up investigations by providing additional information about the incident, indicators, adversary, and associated TTPs. |
| Intelligence Analyst | Improve tracking of threat actors and gain additional insights into their tactics, techniques or operating patterns. |
| Supply Chain Management | Identify compromised suppliers and customer accounts. |
| Mergers and Acquisitions | Evaluate prospects to understand possible risks relating to acquisition. |
| Red / Purple Team | Provides adversary attacks flows and procedural information to allow operators to emulate real world attacks. |
| Security Culture and Awareness | Analyse real world intrusions to bring security awareness program and training to life. |
Cyber Threat Intelligence Lifecycle
The cyber threat intelligence lifecycle provides a structured approach to collecting, analysing and applying gathered data.
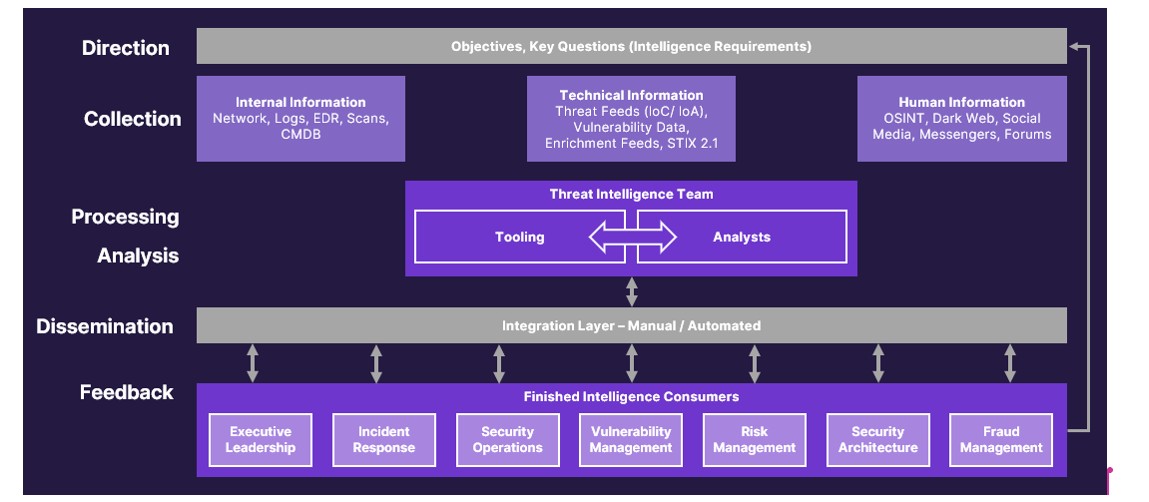
Listed below are the key stages of a cyber threat intelligence framework:
- Planning and Direction: Stakeholders work with threat intelligence team to define key questions and refine to refine them into intelligence requirements. Requests for Intelligence (RFIs) are another starting point to trigger moving into the collection phase.
- Collection: Raw data is collected from different sources, like internal logs and threat feeds, to gain a large base of threat information to work from.
- Processing: Data is processed, transformed, and filtered into useful information that can be analysed by CTI analysts.
- Analysis: Information is analysed to identify any patterns, trends or actionable insights. This includes both a qualitative and quantitative analysis. Processes such as structured analytic techniques (SATs) can be used to remove bias, fill gaps, and satisfy intelligence requirements defined in the Planning and Direction phase. Intelligence assessments and products are produced for consumption by stakeholders.
- Dissemination: Intelligence assessments and products are shared with relevant stakeholders, usually security teams and executives, in a concise, clear and actionable format to aid decision making.
- Feedback: Feedback from stakeholders and KPI’s associated with technical threat intelligence integration are used to continually improve intelligence outputs. Regular feedback establishes systems for regular improvement. This includes updating intelligence based on threats, incidents and organisational changes.
Cyber Threat Intelligence Feeds
‘Feeds’ are real-time data streams that provide organisations with information about potential threats and vulnerabilities.
Some of the different cyber threat intelligence feeds – and the data they provide – include:
| Source/Types | Types | Description |
| Types of Feeds | Indicators of Compromise | These are data points that can signify a potential breach. Includes IP addresses or domain names related to any malicious activity. |
| Tactics, Techniques, Procedures (TTPs) | Key information about threat actors and how they operate. This includes both tools and methods. | |
| Vulnerability Exploitation Data | Any information about known exploitable vulnerabilities in systems and software. Includes information on threat actors leveraging specific vulnerabilities, their severity ratings, prioritisation, and steps for remediation. | |
| Sources of Feeds | Commercial Providers | Any organisation that offers threat intelligence feeds for a subscription fee. |
| Open-Source Feeds | Free, open-source resources that are available to the public and are often community-driven. | |
| Internal Feeds | Any data generated by an organisation’s community monitoring, including logs and incident reports. | |
| Special Interest Groups | Information sharing communities such as ISACs or industry peer groups. |
Cyber Threat Intelligence: The Tooling and Service Conundrum
Acquiring the right tools for a cyber threat intelligence (CTI) programme is only half the battle. While an in-house approach offers control, it also presents significant management and talent challenges. Tools can simplify collection but if they are not providing finished intelligence or “Fintel” then humans are needed to analyse their outputs and produce actionable threat intelligence products for stakeholders.
Cyber Threat Intelligence Tools
Effective CTI relies on a combination of tools to collect, process, and contextualise threat data. These commonly include:
- Threat Intelligence Platforms (TIPs): Automate the collection and analysis of threat data, consolidating it into a single platform.
- Security Information and Event Management (SIEM): Collects and analyses internal data like logs and event information to identify threats within an organisation's network.
- Threat Intelligence Feeds: Provides real-time streams of data on current threats, often focused on specific indicators of compromise (IOCs).
- Sandboxing Tools: Create isolated, secure environments to analyse potentially malicious files, and provide malware reports, and artefacts for ongoing tracking.
- Open-Source Intelligence (OSINT) Tools: Gathers and analyses publicly available data to provide early warnings and track adversary infrastructure.
- Intrusion Detection/Prevention Systems (IDS/IPS): Identifies and provides intelligence on network traffic anomalies and attack patterns.
- Cloud Detection and Response (CDR): Detects and provides real-time intelligence for threats within cloud environments.
The Challenges of an In-House Approach
Building an internal CTI program can be a challenge to stand-up and manage without a mature cybersecurity program in place. Beyond the initial purchase of tools, organisations face key challenges:
- Technical Burden: Acquiring the right tools is complex, but the real difficulty lies in integrating disparate systems and ensuring they are configured and producing good outputs. This requires technical expertise to ensure threat intelligence platforms and outputs are creating expected return on investment (ROI).
- The Talent Gap: Tools are only as effective as the analysts who use them. Finding and retaining talent with specialised skills in threat intelligence, threat hunting, malware analysis is a significant, and often expensive, challenge.
- Information Overload: CTI tools and feeds can generate a massive volume of data. Without the right expertise and processes, this can lead to analyst burnout and slow response times, making it difficult to turn raw data into actionable intelligence products.
CTI Services: An Alternative Model
Instead of building an in-house programme, some organisations opt for a managed CTI service. This model provides access to a dedicated team of experts and their specialised tools.
A CTI service can be a more predictable and cost-effective option for many organisations. It shifts the burden of tool management and talent acquisition to a third party. This allows an organisation to benefit from curated, actionable intelligence while minimising the operational and financial challenges of a self-built programme. It is a trade-off between the direct control of an internal team and the efficiency and broad threat visibility offered by a dedicated service.
Consuming a service can help organisations avoid the mistakes and pitfalls of rolling your own threat intelligence program and provides experienced threat intelligence professionals who can tailor the program and service to an individual companies requirements.
Bridewell’s Cyber Threat Intelligence Team
At Bridewell, we offer a managed Cyber Threat Intelligence service, spearheaded by a team of experienced cyber security professionals.
At Bridewell we take a research driven approach to cyber threat intelligence, producing actionable intelligence products and services that empower our clients with the knowledge required to build a threat informed defence.
We can provide the necessary expertise to implement, operate, manage, and continually improve our clients CTI programs. Or alternatively we can work as an extension of the team augmenting specialist roles or delivering capabilities that may be inaccessible or cost prohibitive to run internally.
Our team specialises in the following areas:
Cyber Threat Intelligence
- Malicious Infrastructure Threat Feed
- CTI Analyst as a Service
- Intrusion Analysis and Threat Hunting
- Requests for Intelligence (RFIs)
- Threat Landscape Assessment
- Threat Model
- Threat Advisories
Digital Risk Protection
- Compromised Credentials
- Information Stealers
Database Leaks
- Domain Impersonation
- Dark Web Investigations
Attack Surface Assessment
- Continuous Asset Discovery and Inventory
- Asset Risk Identification and Assessment
- Network Security
- DNS and Domains
- Certificate and SSL/TLS Security
Protect your organisation against credible threats – so, your people can focus on doing what they do best
Frequently Asked Questions
Q: What is cyber threat intelligence?
A: Cyber threat intelligence is the collection and analysis of information regarding potential or existing cyber threats that satisfies a requirement. It helps organisations understand threat actors, their tactics and any potential security vulnerabilities they are leveraging, to prevent attacks and limit damage.
Q: What does a CTI team do?
A: A cyber threat intelligence (CTI) team works with organisational stakeholders to understand and define their intelligence requirements. CTI teams then collect and process data, before analysing the resulting information to produce threat intelligence that can be shared with stakeholders to satisfy their intelligence requirements.
CTI teams can operate at strategic, operational, and tactical levels to ensure stakeholders intelligence requirements are met.
Threat intelligence produced by the CTI team should be timely, relevant, and accurate.
Q: What are threats and why do I need to know about them?
A: Threats are agents that have the capability, opportunity, and intent to do harm to your organisation and underlying assets.
Organisations need to understand themselves and the threats that are interested in them to effectively collect and use threat intelligence.
Q: What is the purpose of CTI?
A: The purpose of cyber threat intelligence is to provide timely and relevant threat intelligence to decision makers, enabling them to take action that positively impacts the cyber security posture of an organisation.
Q: How do I ensure my threat intelligence is effective?
A: Effective threat intelligence requires you to work with stakeholders to define intelligence requirements. Intelligence requirements are effectively requests from the business to satisfy a knowledge gap or concern, regarding a threat or the organisations defensive posture.
Once these are established the threat intelligence team can work to collect, process, and analyse relevant data to satisfy these knowledge gaps in a timely manner.
This will also often include defining the cadence and format in which stakeholder intelligence requirements are met often referred to as the dissemination of intelligence products.
Finally feedback from the outputs of the intelligence process are critical to ensure the process continually improves and that intelligence requirements are met in a satisfactory manner.


-(2).tmb-6_col_resi.jpg?sfvrsn=47051177_2)


