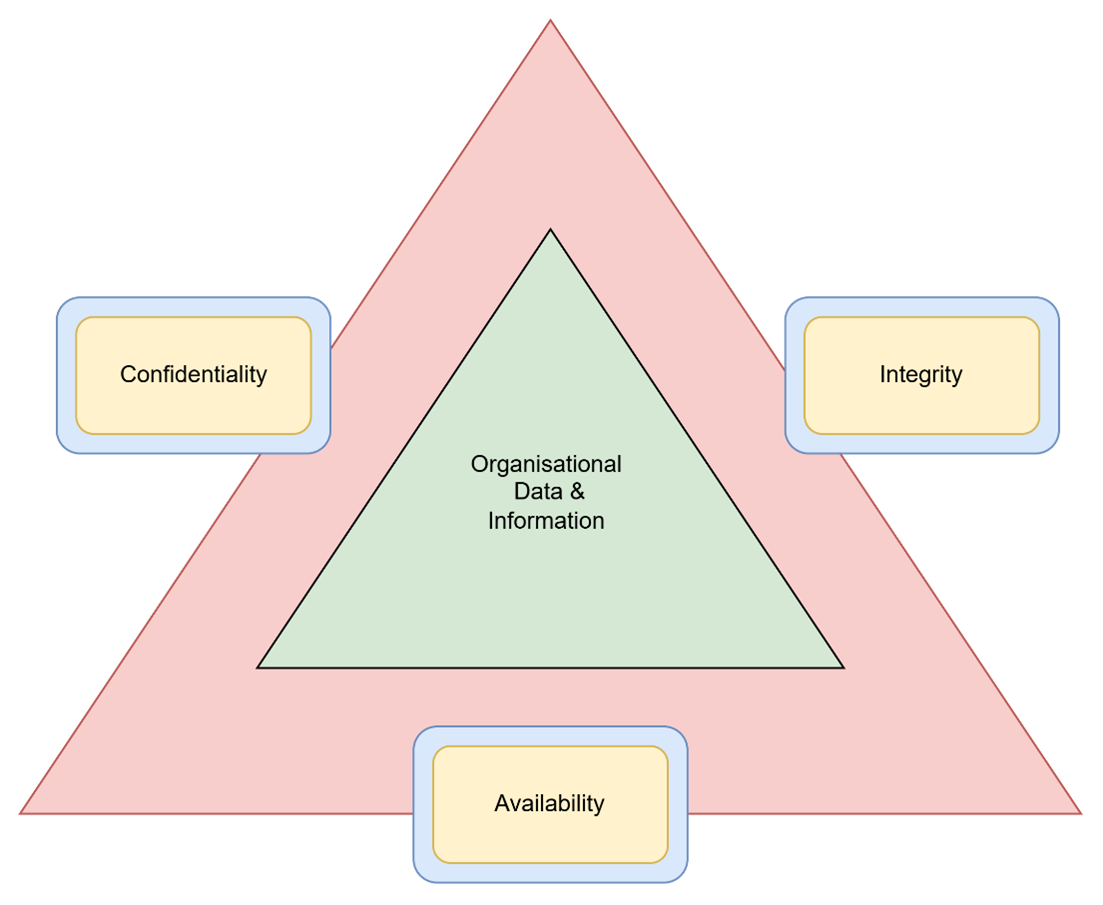
Components of the CIA Triad
Confidentiality
Identification, authentication and authorisation support maintaining confidentiality of information by strengthening the principle of least privilege. When only providing authorised personnel, processes, systems or solutions access pertinent to their role, confidentiality is protected. This is further bolstered by succinct classification of information. When cross referencing classification, with roles defined by the principle of least privilege, organisations can best assess the applicability of access to it. Another example control that helps improve the confidentiality of information is encryption, which limits the usability of information in the event of it being accessed by an unauthorised source.
Integrity
To safeguard information from unauthorised, accidental or intentional modification, there is the principle of integrity. Controls are put in place to best ensure information is only modified by known, approved and accountable (auditable) sources. By ensuring integrity of information, organisations can be confident in the knowledge their solutions provide accuracy to support decision making. Example controls include segregation (or separation) of duties, embedded approval mechanisms, and implementation of testing procedures aimed at validating integrity.
Availability
This is the principle that ensures information is readily available to those that need it whenever they need it. Whether it be through malicious action or loss of service outside of human factors, if users (or systems) can’t access the information required, the ability to conduct operations degrades quickly. If there’s a lack of controls aimed at safeguarding availability, the risk and impact of extended downtime increases. Sample controls include scoped, routinely tested and up-to-date disaster recovery and business continuity procedures. This will help ensure that organisational functions have alternatives when there’s technological outage or unplanned loss of access.
How Does the CIA Triad Work?
The CIA triad works by anchoring decisions on technologies, management processes, applications, systems, solutions, architecture, or any other element that impacts the security of information, to three pillars of information security. Equal consideration is given to authorised access (confidentiality), maintaining accuracy (integrity) and aiming to guarantee access (availability).
When consistently applying the CIA triad principles, organisations can better anticipate and manage risks to their information assets in phases:
- Design – Technologies, processes and systems engineered with confidentiality, integrity, and availability in mind from the outset and preferably as requirements themselves.
- Implementation – Controls and safeguards that were designed to address confidentiality, integrity, and availability during design are deployed and tested appropriately.
- Managing the Lifecycle – Applications, solutions, architectures are routinely revalidated, so the security controls designed and implemented to support confidentiality, integrity, and availability remain fit-for-purpose.
Why is it so Important and What Value Can it Add?
The importance of the CIA triad lies in providing a clear, simple, structured approach for organisations to protect their data, information and systems in an ever-evolving threat landscape.
It can form the foundation principle for organisational cyber security, underpinning existing information security-centric frameworks (such as ISO 27001 and NIST CSF). It also supports adjacent regulatory requirements (such as the EU GDPR) or compliance with a Quality Management System (such as ISO 9001).
With consistent, repeated application of the CIA triad, organisations can better anticipate and mitigate risks, subsequently reducing the likelihood and impact of incidents. The CIA triad can also demonstrate proactive organisational commitment to protecting both information assets and reputation – whether that be to regulators, investors or customers.
The Role of the CIA Triad in Cyber Security and Emerging Threats
The CIA triad can also be utilised to re-evaluate existing security posture and controls. Taking three of the most significant threats organisations face today, we can see how the CIA triad plays its part:
- Ransomware attacks target availability by encrypting data and demanding payment. Organisations counter this by maintaining secure backups and robust recovery procedures.
- Supply chain attacks can compromise integrity by introducing malicious code into trusted software. Code signing, vulnerability management, and continuous monitoring help detect and prevent tampering.
- Insider threats challenge confidentiality and integrity. Behavioural analytics and least privilege policies help detect unusual access patterns and prevent unauthorised actions.
In Summary
Ultimately, value comes from the fact the CIA triad doesn’t have to be a theoretical model. It offers a simple, practical baselining tool to build out a robust information security posture. This in turn:
- Safeguards sensitive information from unauthorised access (Confidentiality), ensuring that only those with a legitimate need can view or use critical data.
- Maintains trustworthiness and accuracy of information (Integrity), so that business decisions are based on reliable, unaltered data.
- Guarantees reliable access to systems and information (Availability), supporting business continuity even in the face of disruptions or attacks.
This can subsequently aid decision making around the applicability and robustness of controls, as well as prioritisation of cyber security and technology investment.
.tmb-6_col_resi.jpg?sfvrsn=34e97148_3)




